Embed presentation
Downloaded 50 times

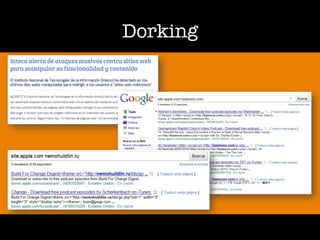
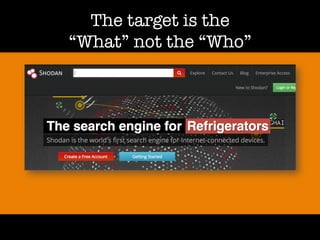


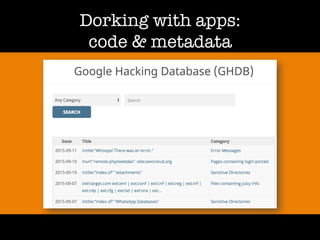
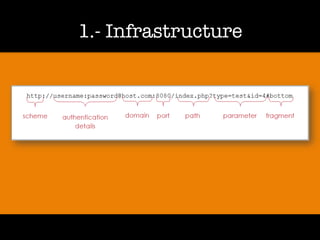


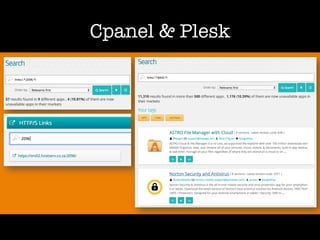
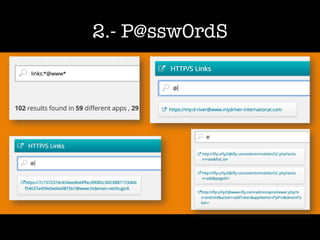
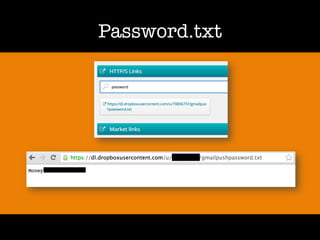

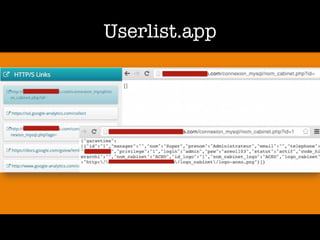

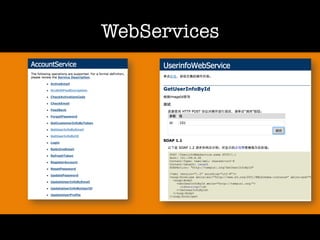

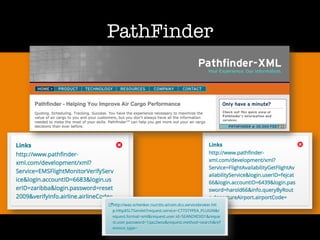

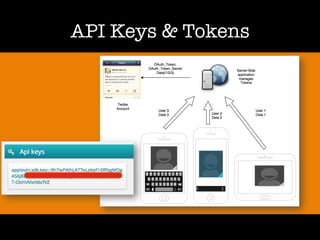

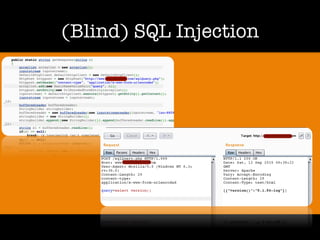

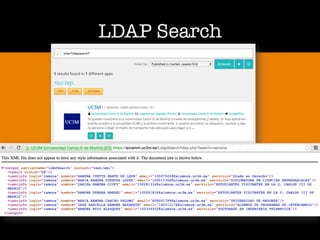




The document discusses 'dorking' and pentesting, emphasizing the focus on code rather than individuals. It introduces 'tacyt' and outlines various methods and tools for uncovering vulnerabilities in applications, including password lists, third-party credentials, and common injection attacks. The author, Chema Alonso, invites questions and credits Eleven Paths for the development of the tacyt service.


























