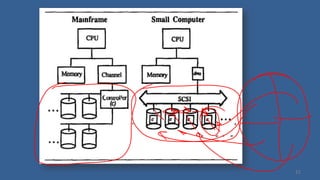
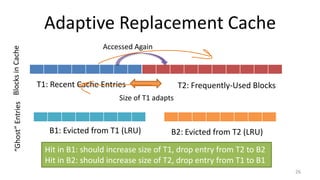
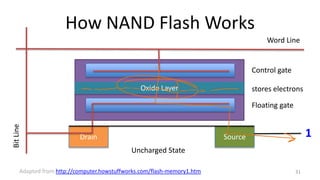
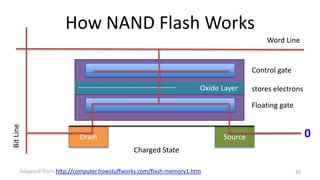
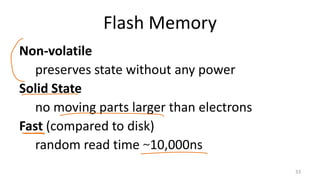
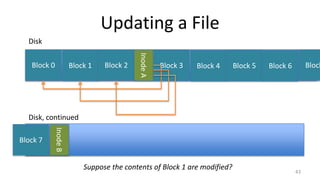
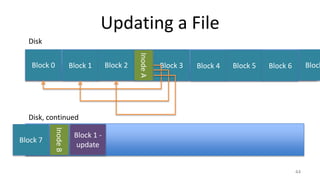
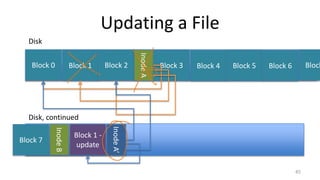
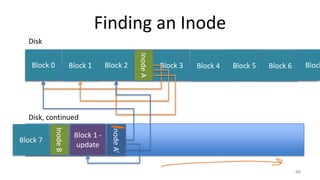
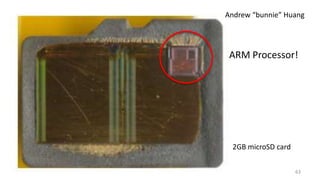
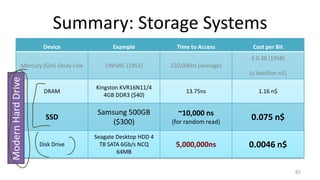
This document provides an overview of file systems and storage technologies, including Unix System 5, log-structured file systems, ZFS, RAID, flash memory, and garbage collection. It discusses how files are represented and accessed in different systems. The key aspects covered are:
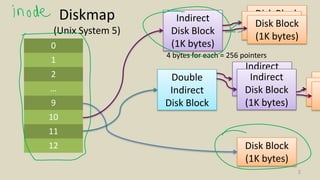
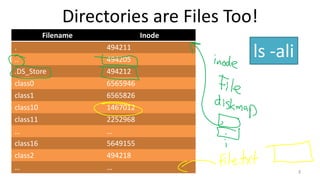
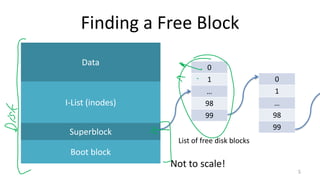
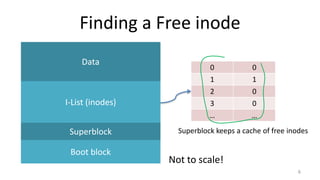
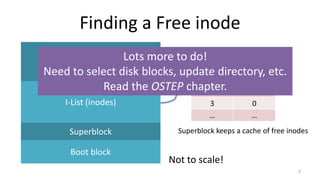
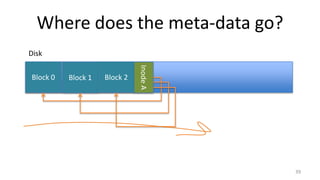
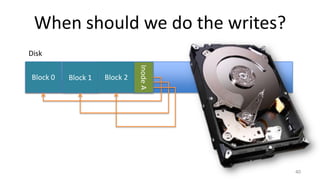
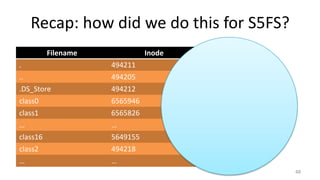
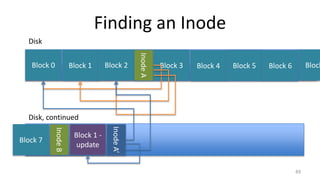
- How Unix System 5 represents files using inodes and disk blocks
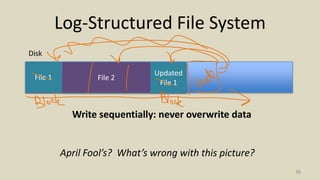
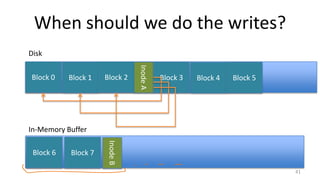
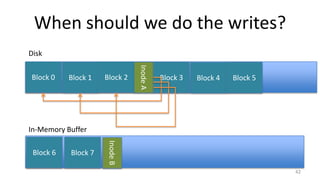
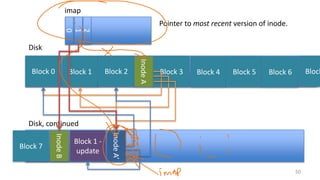
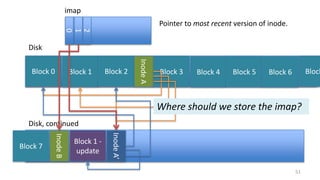
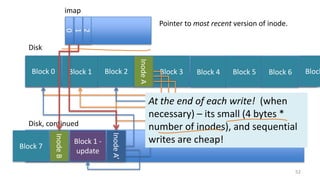
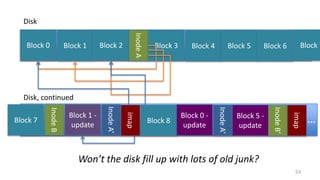
- How log-structured file systems write files sequentially to avoid overwriting and better suit flash memory
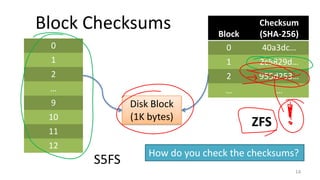
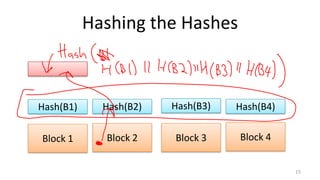
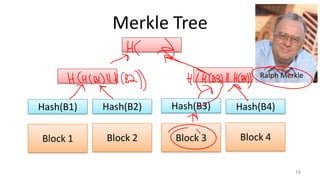
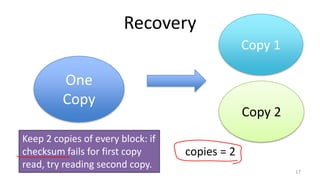
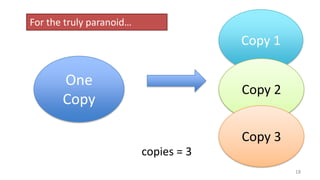
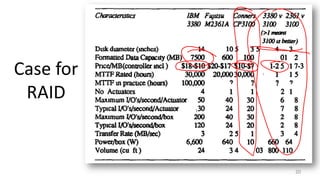
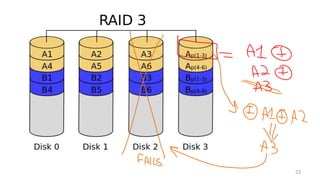
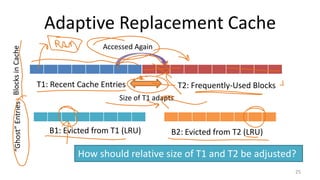
- Techniques used in modern file systems like ZFS to provide redundancy, detect errors, and improve performance
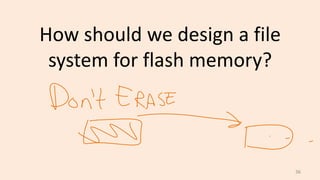
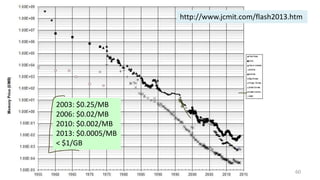
- Challenges of flash memory like limited write cycles and how file systems address these
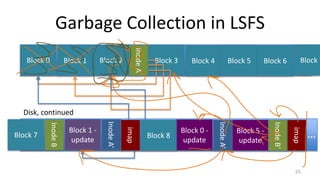
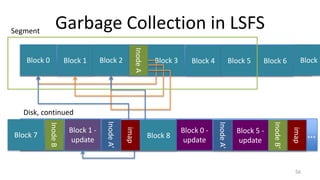
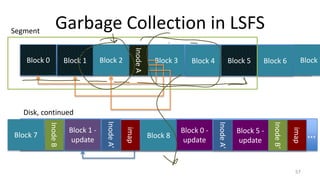
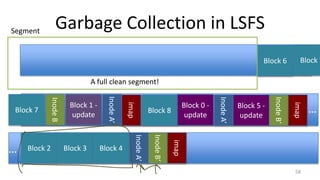
- Garbage collection methods used in log-structured file systems to reclaim