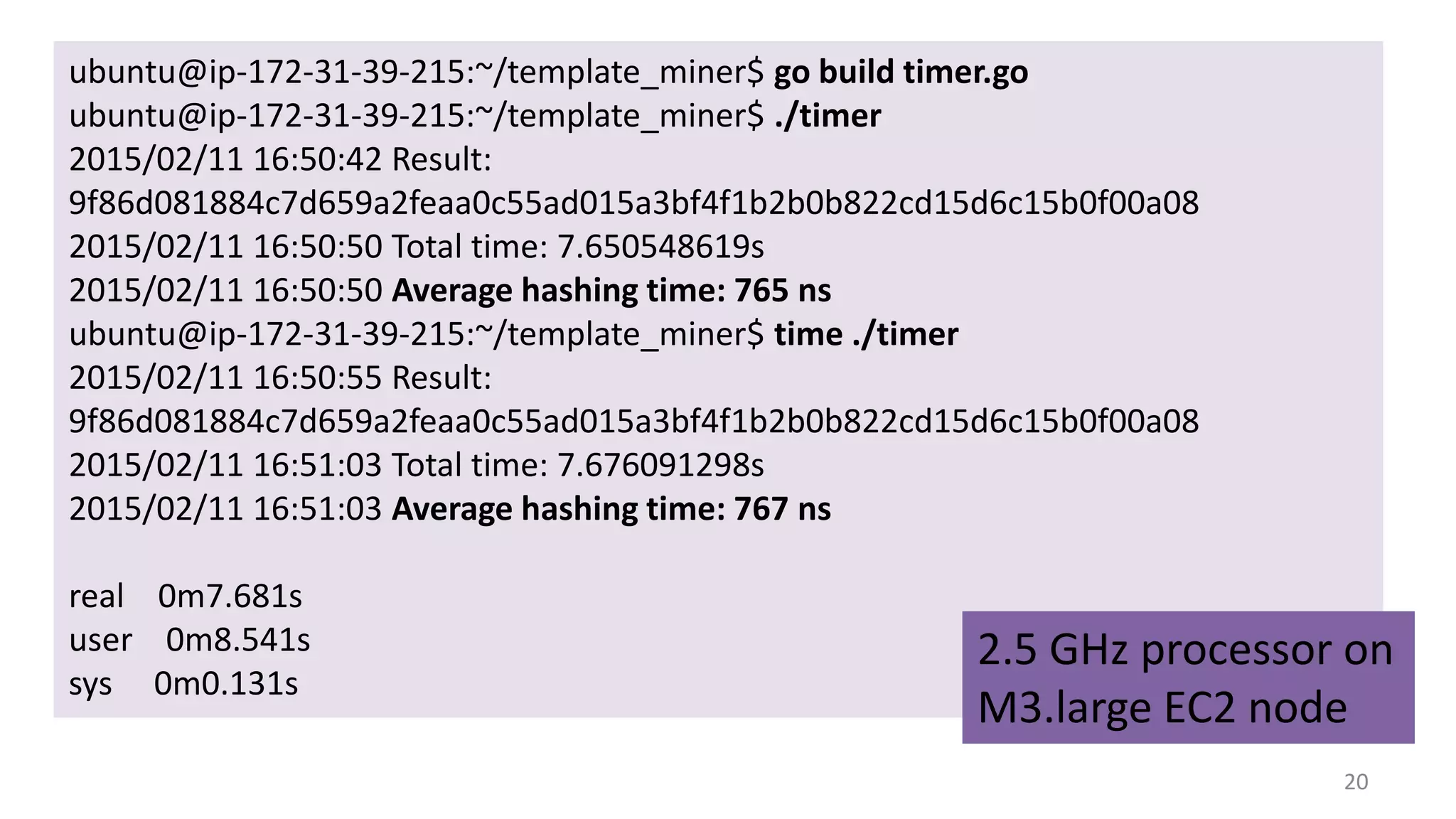
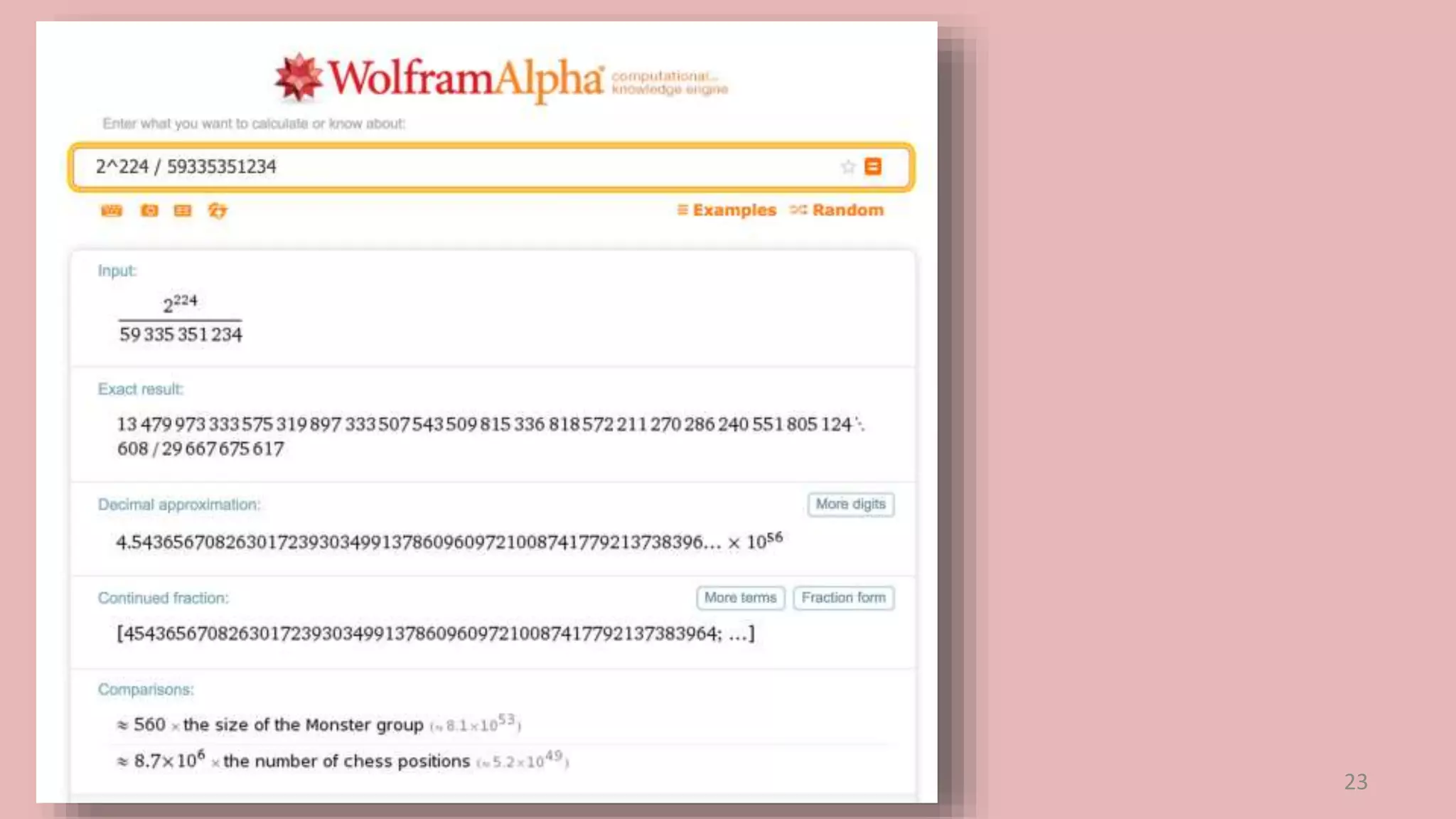
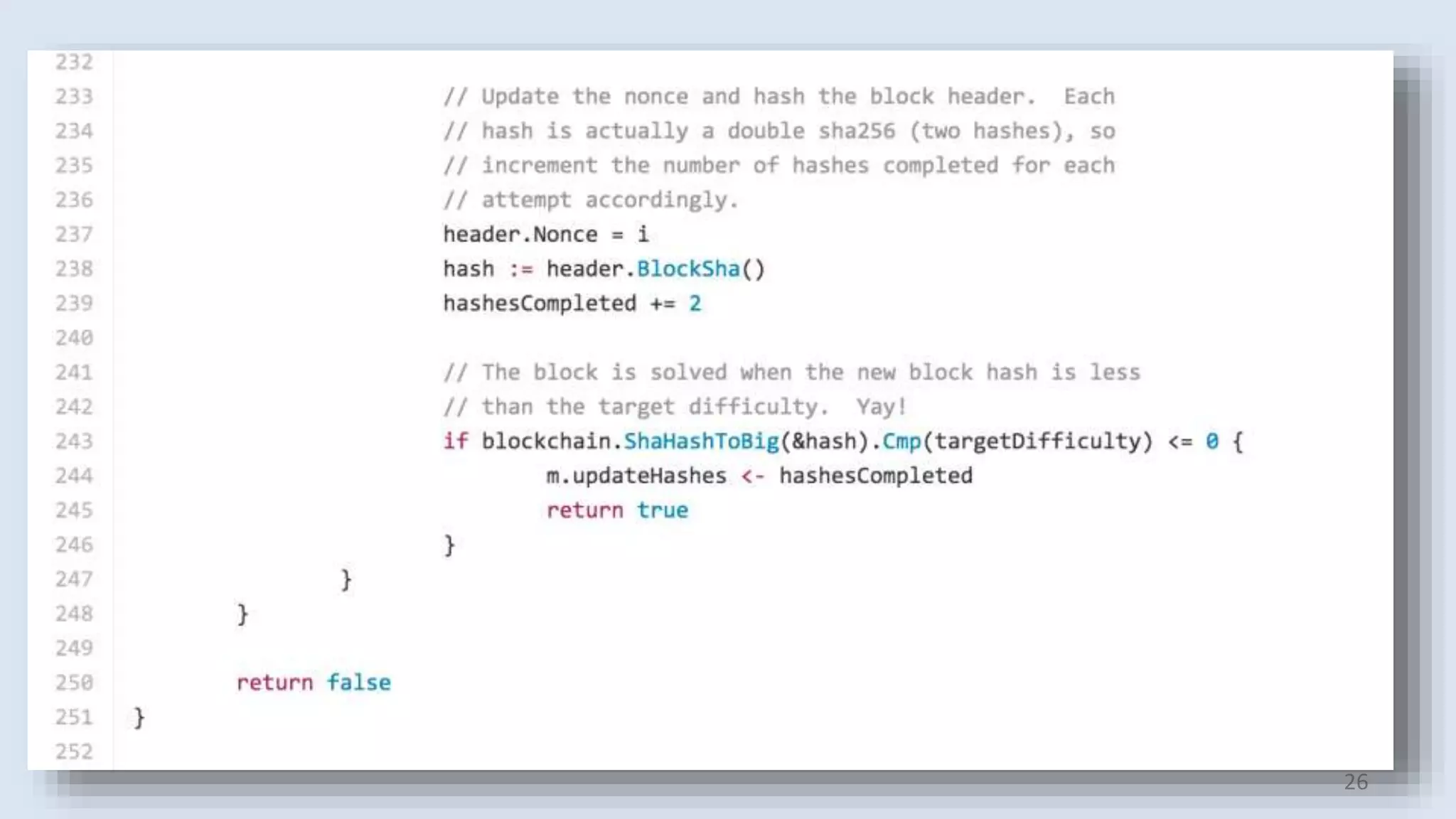
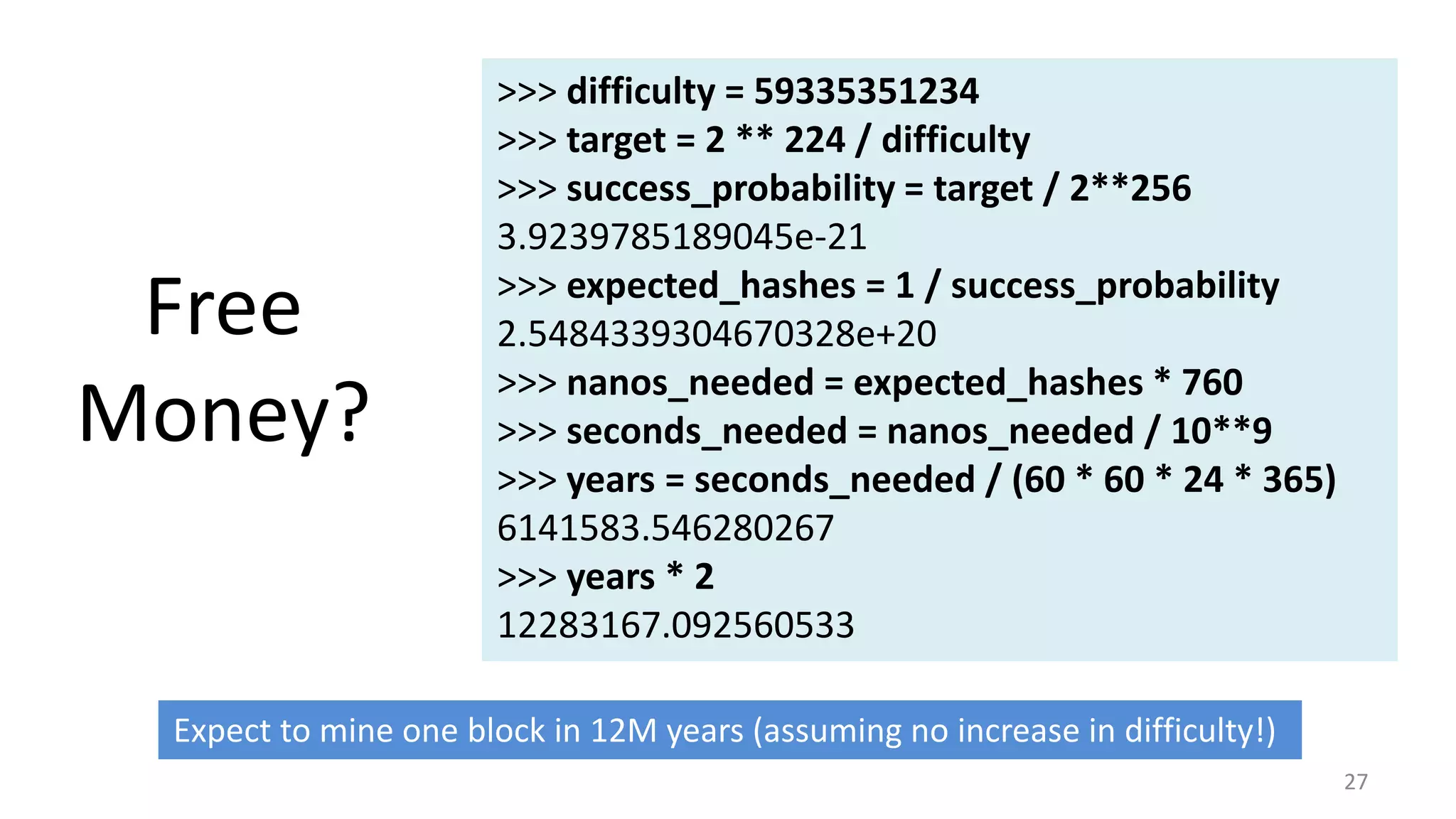
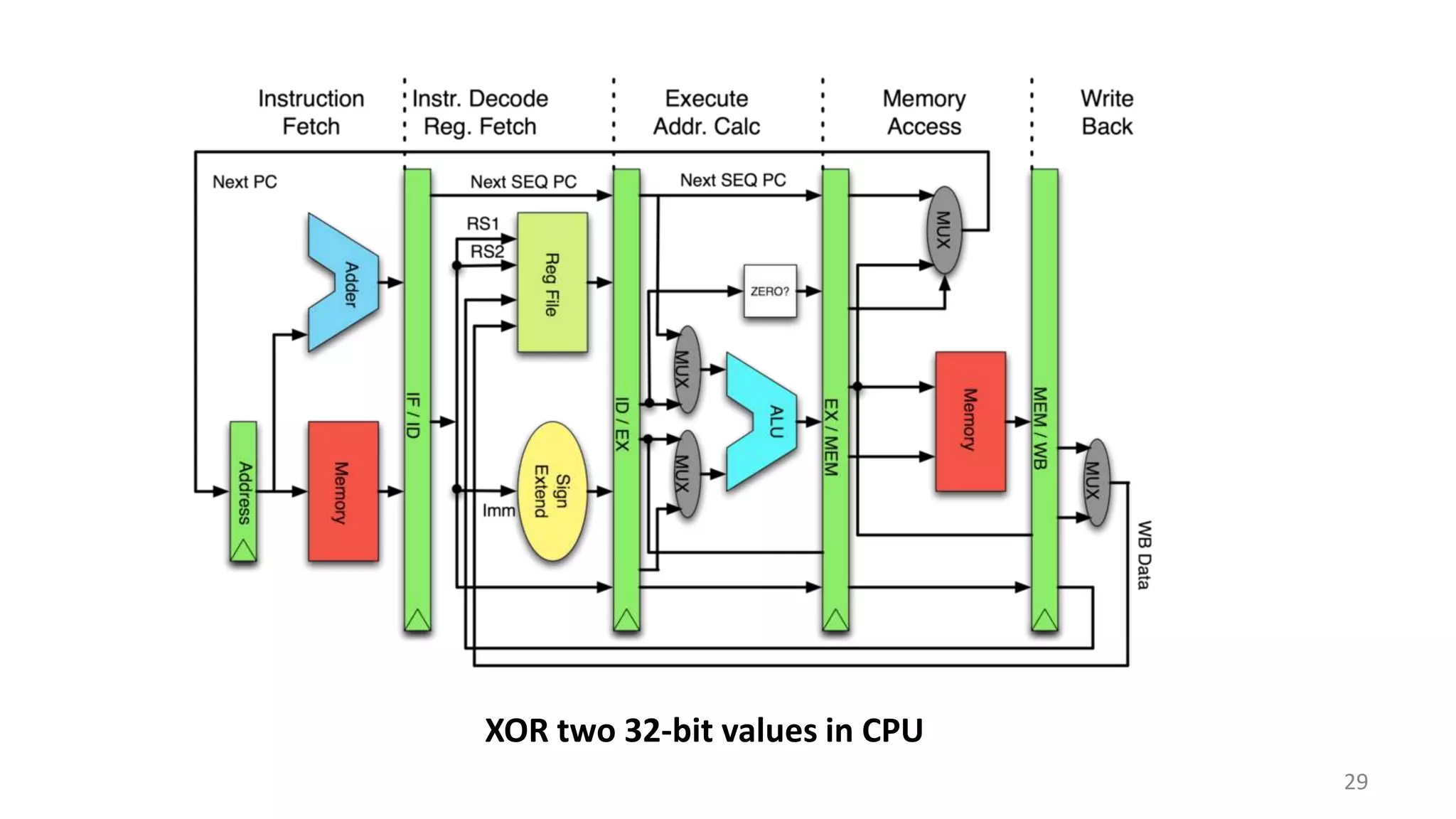
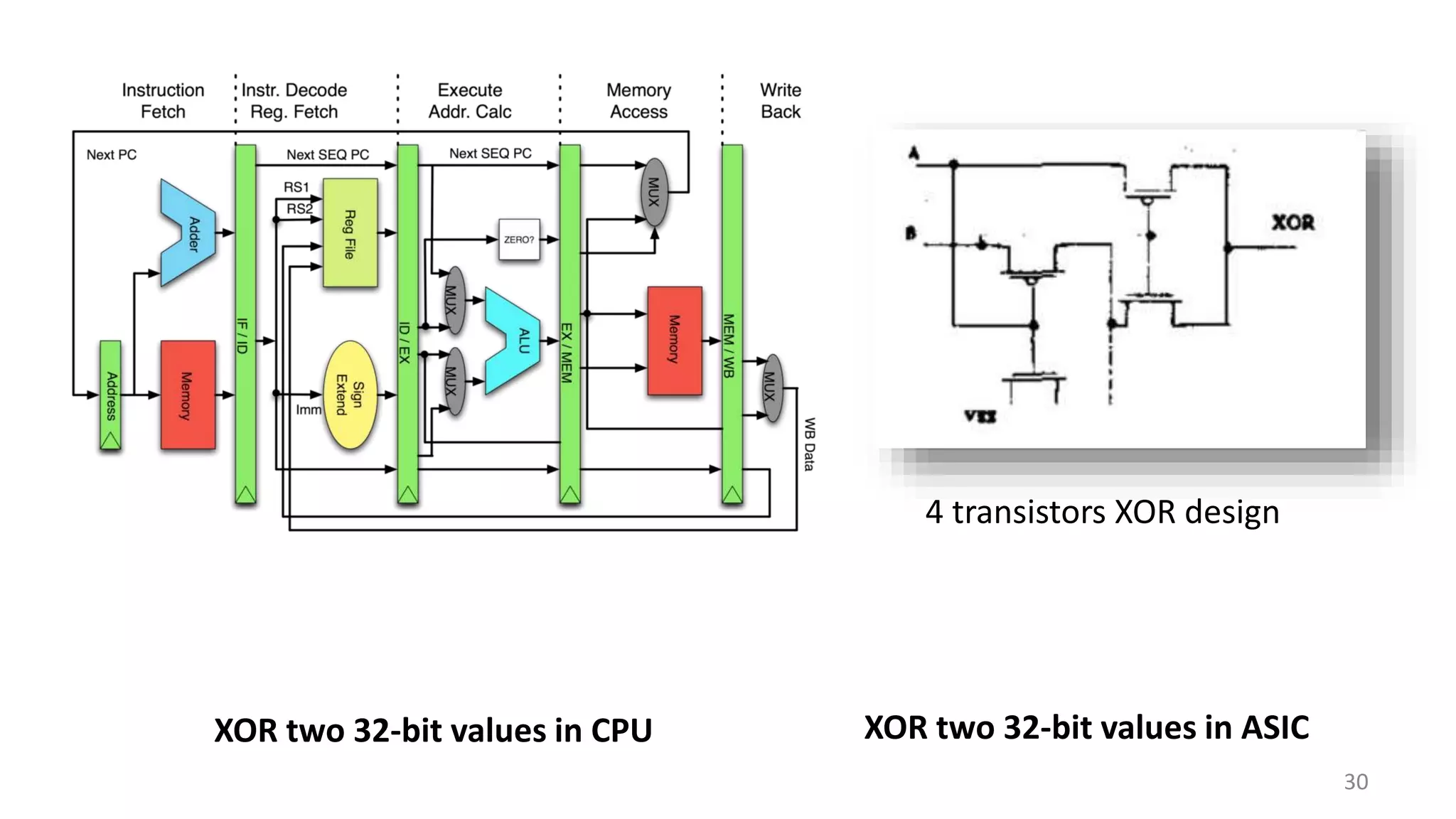
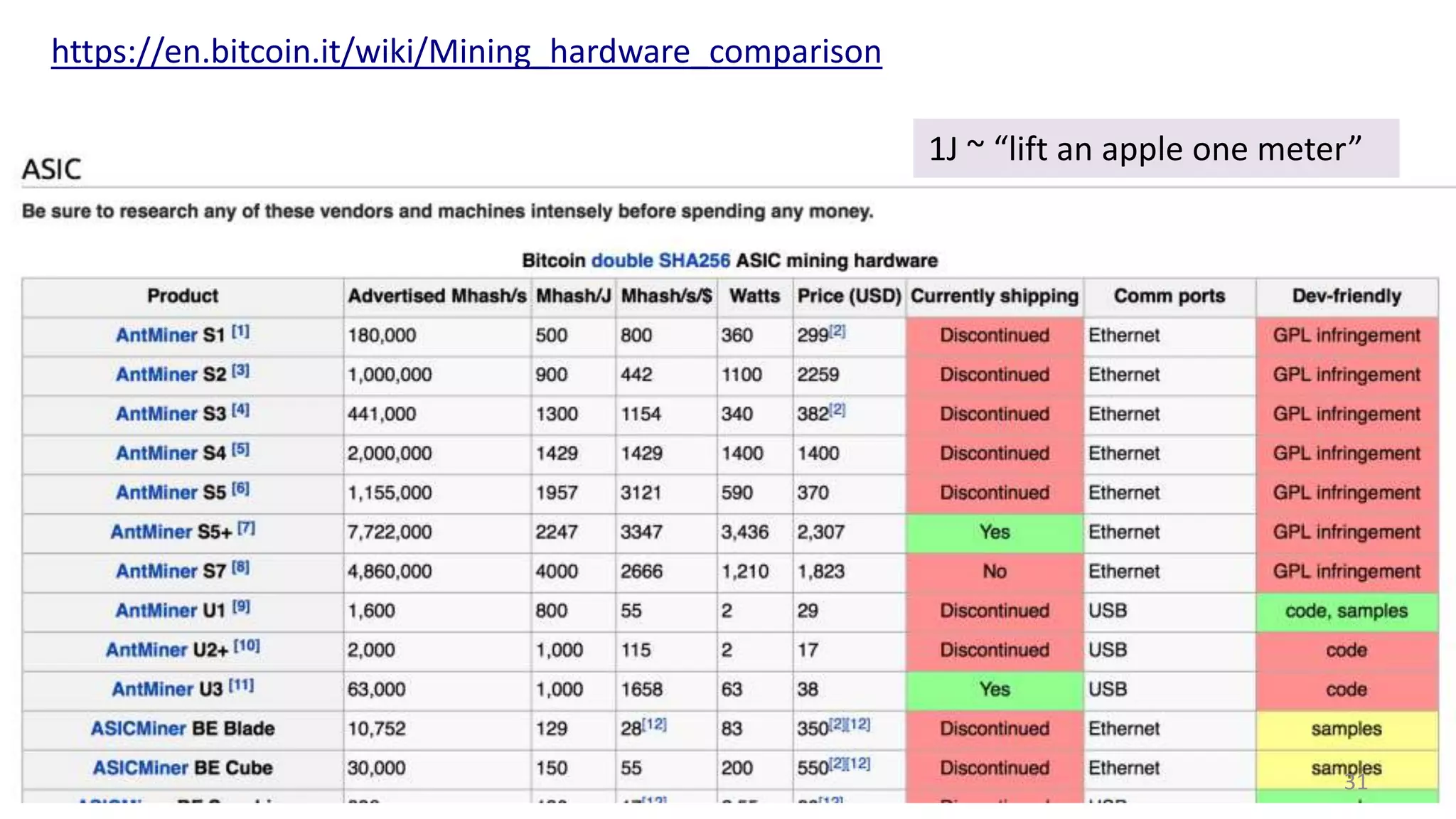
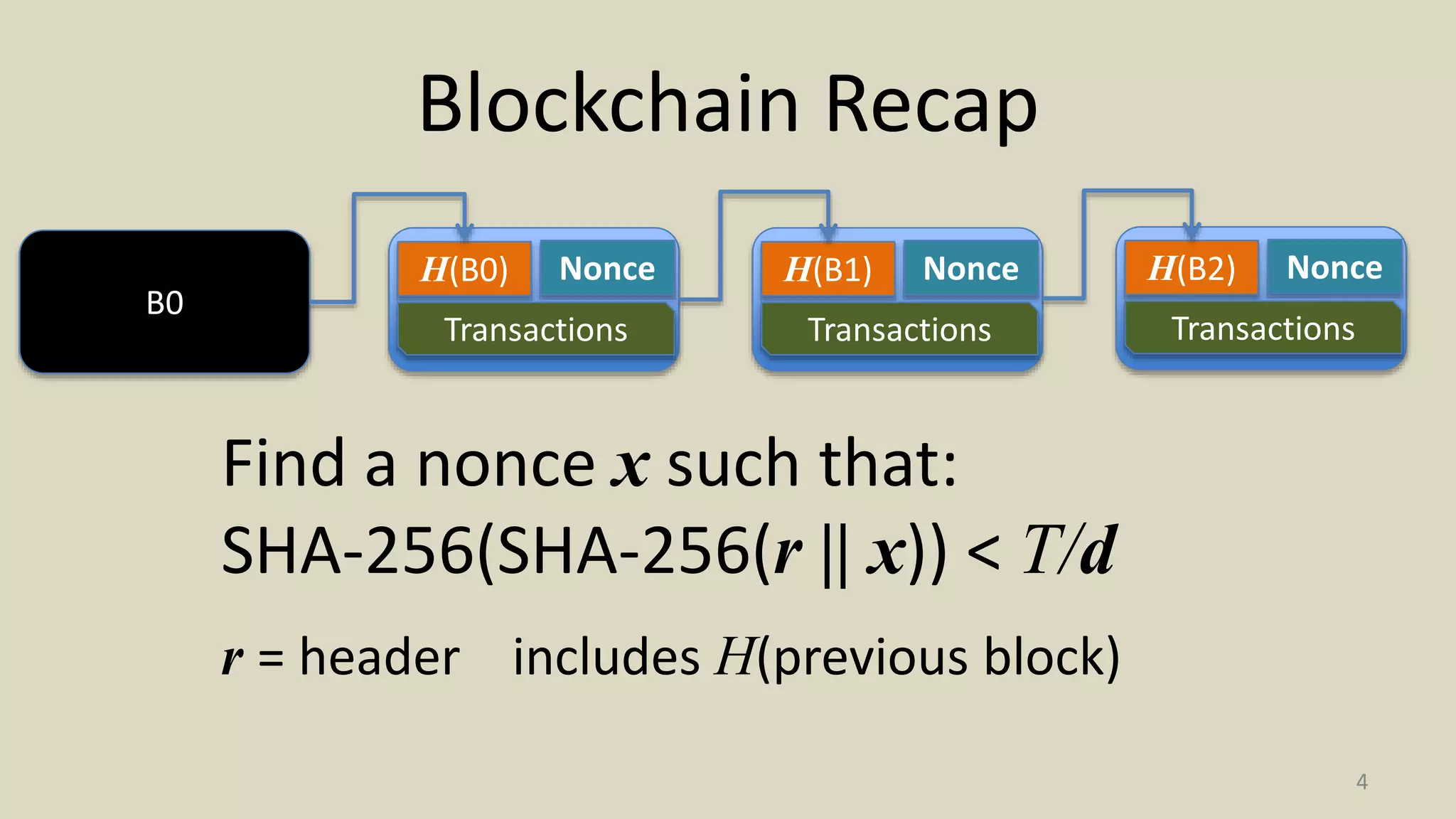
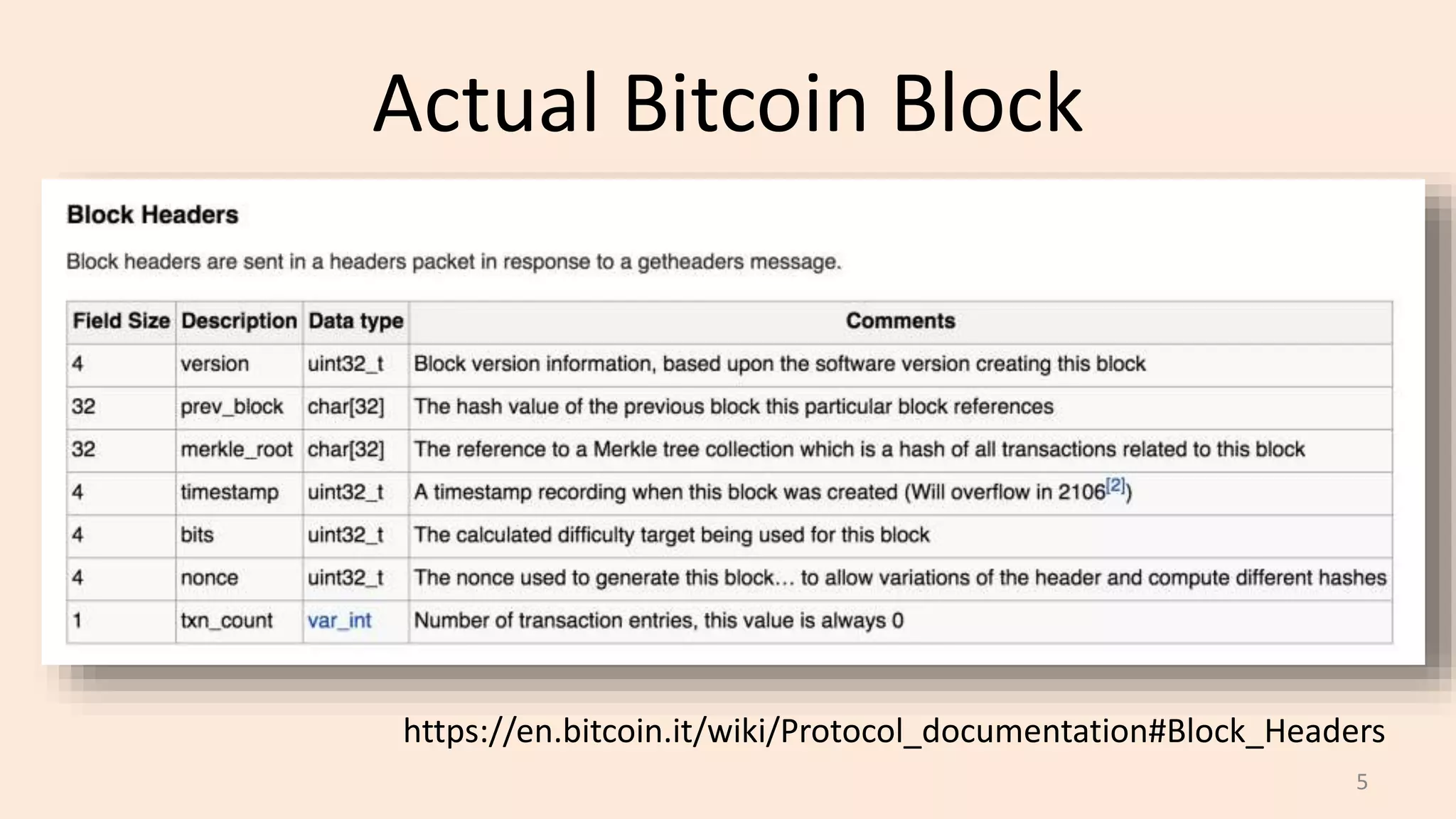
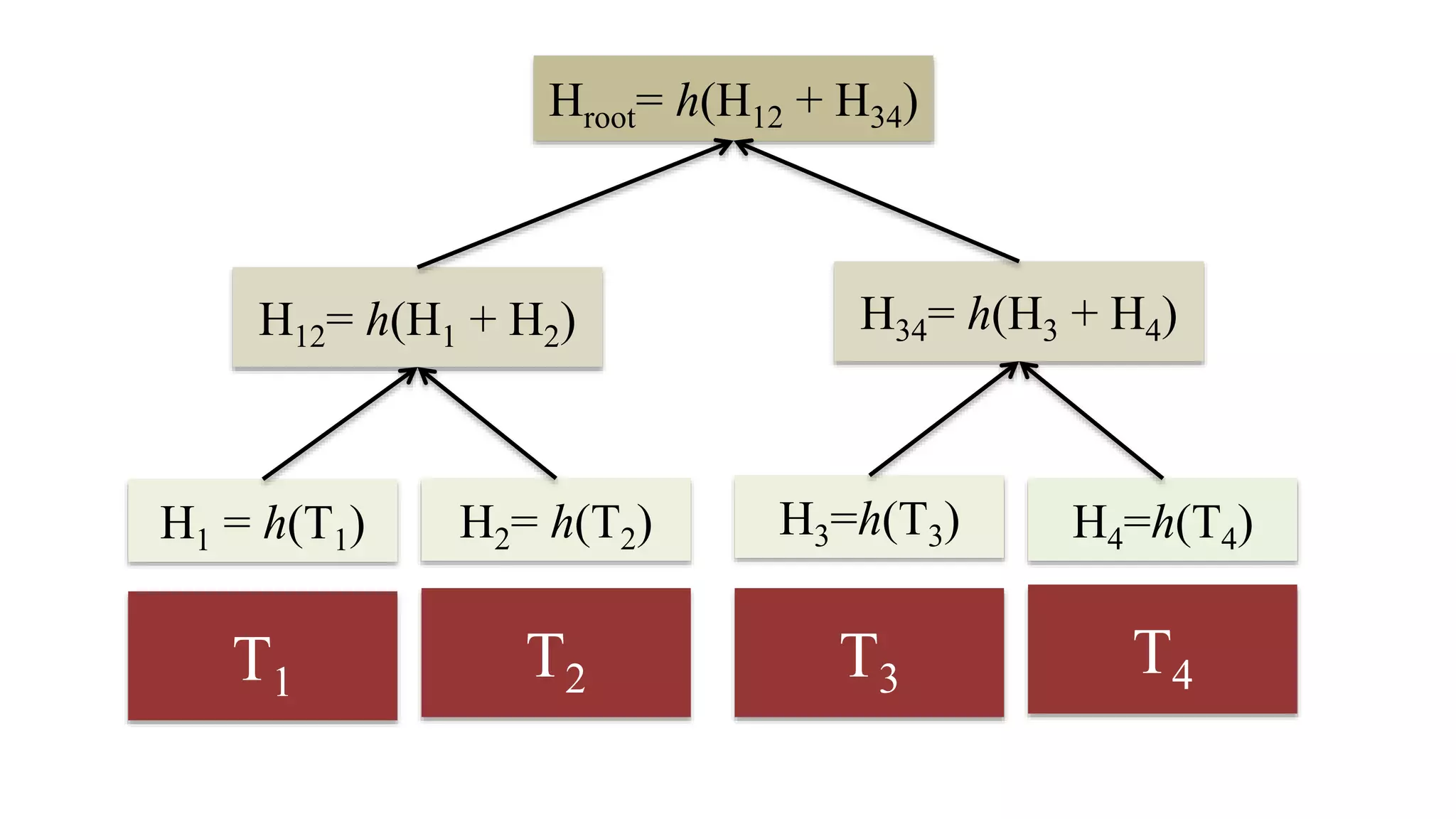
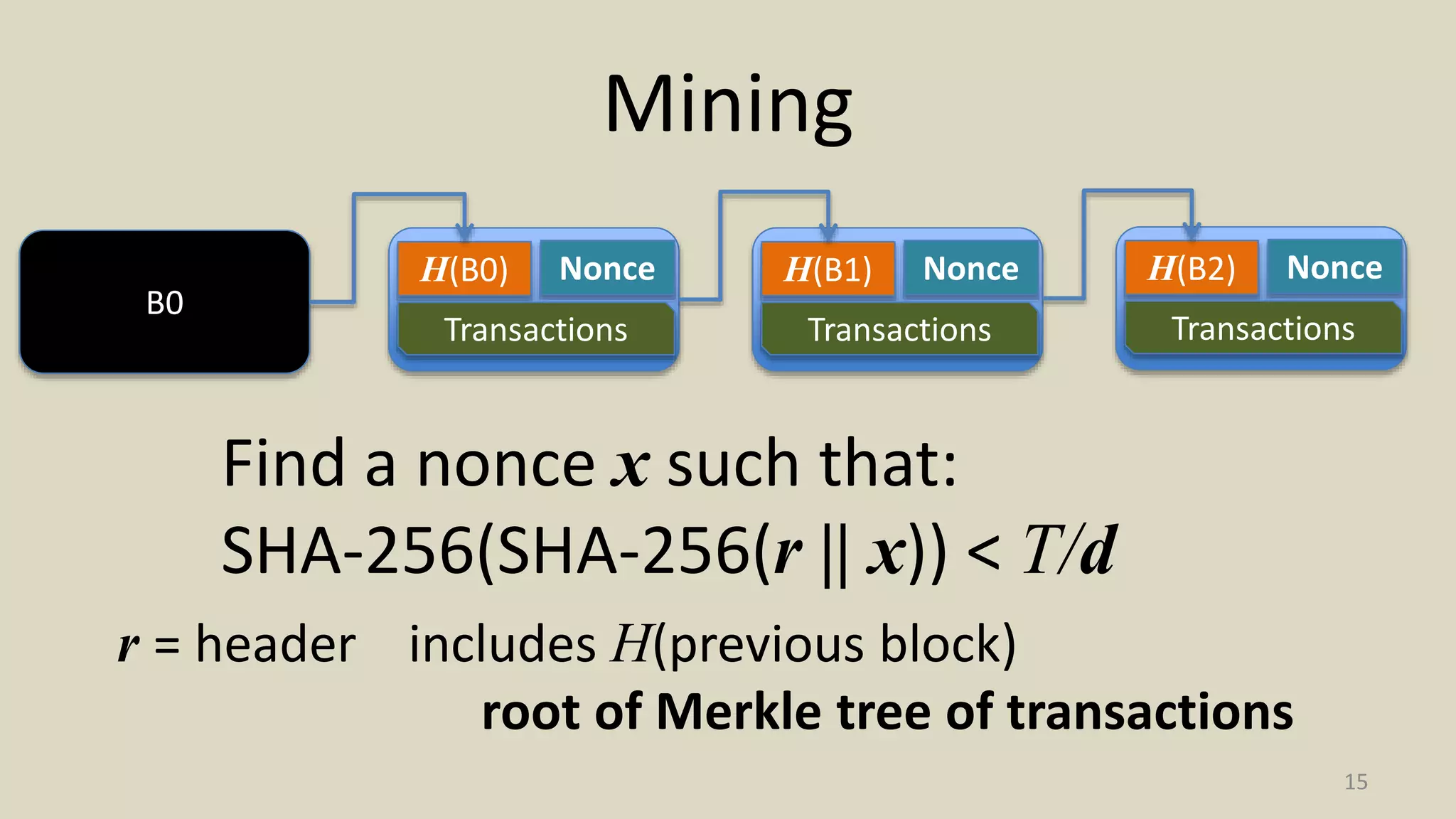
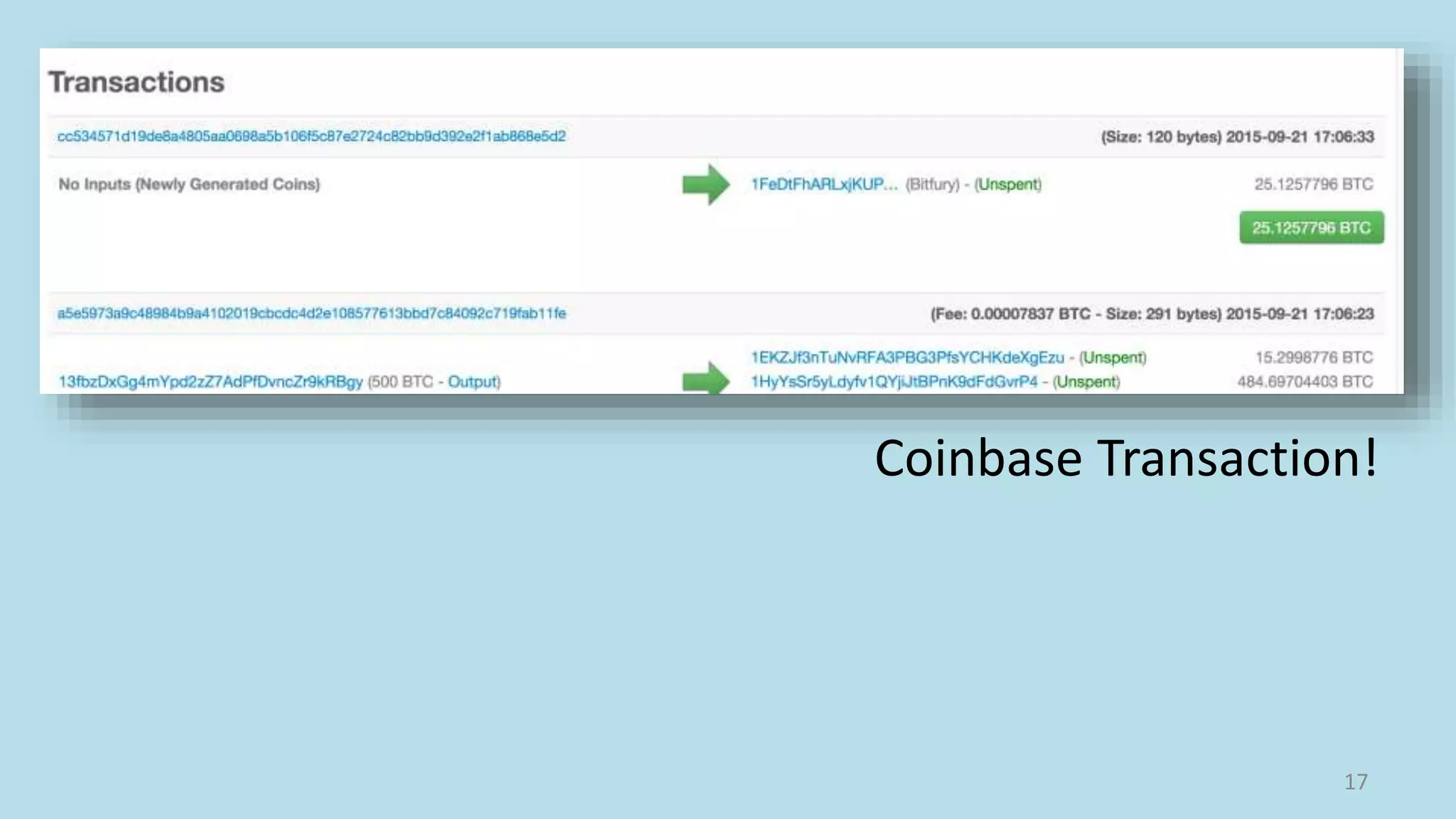
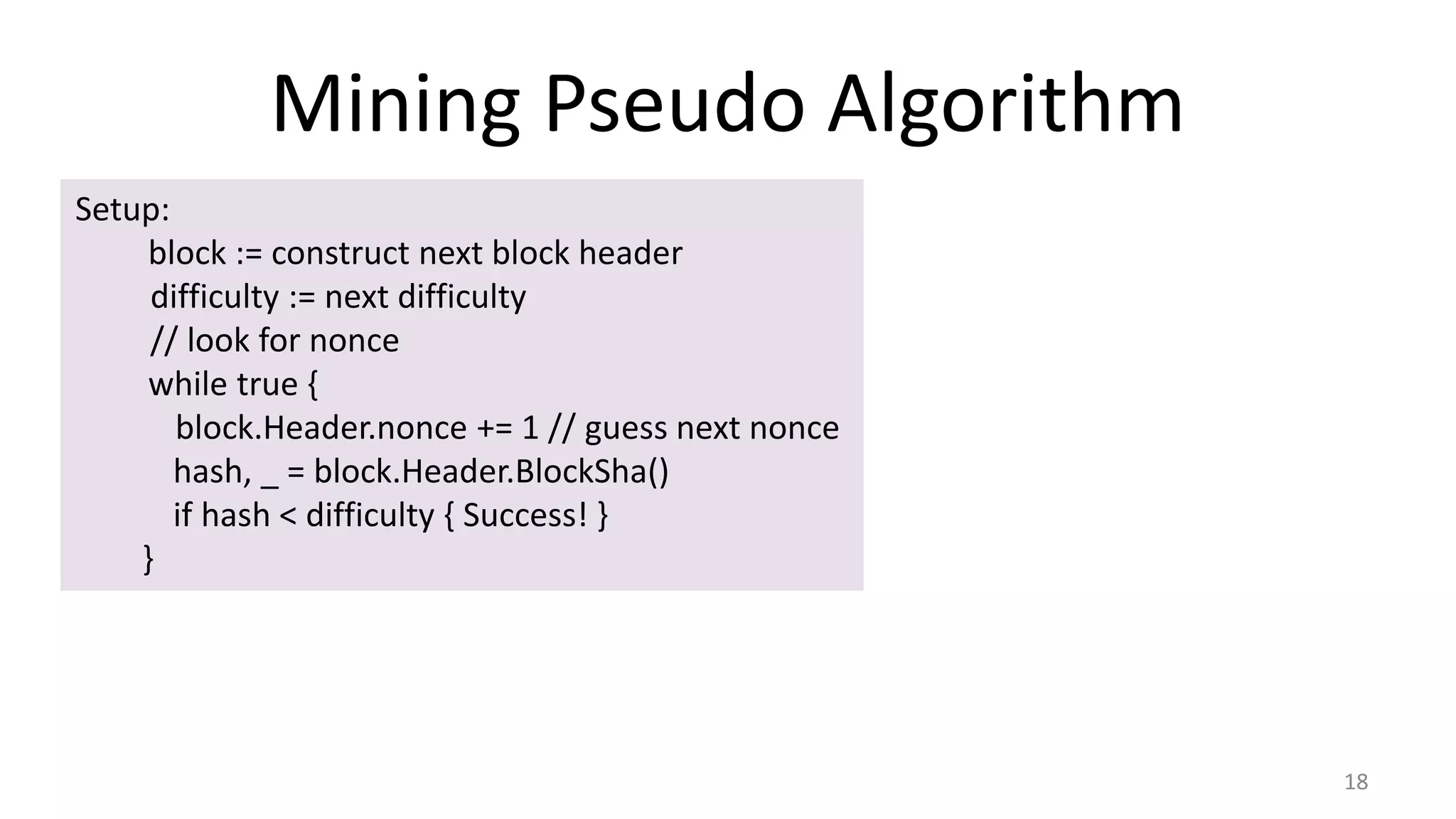
This document summarizes a class lecture on cryptocurrency mining. It discusses the mining process, which involves finding a nonce value that satisfies the mining difficulty target for a block. Miners include transactions and solve cryptographic puzzles to validate blocks and earn rewards. The document explains Merkle trees, which improve transaction verification scalability. It also discusses the high computational costs and energy requirements of mining, noting specialized mining hardware can solve puzzles thousands of times faster than CPUs. The goal of mining is to process and validate transactions in a decentralized manner to maintain blockchain integrity.











![19
package main
import "github.com/PointCoin/fastsha256"
import "log"
import "time"
func main() {
msg := "test"
hasher := fastsha256.New()
hasher.Write([]byte (msg))
starttime := time.Now()
num := 10000000
for i := 0; i < num; i++ {
hasher.Sum(nil) // ignore result
}
elapsed := time.Since(starttime)
log.Printf("Total time: %s", elapsed)
log.Printf("Average hashing time: %d ns", elapsed.Nanoseconds() / int64(num))
}](https://image.slidesharecdn.com/class8-post-150921193723-lva1-app6891/75/Mining-20-2048.jpg)