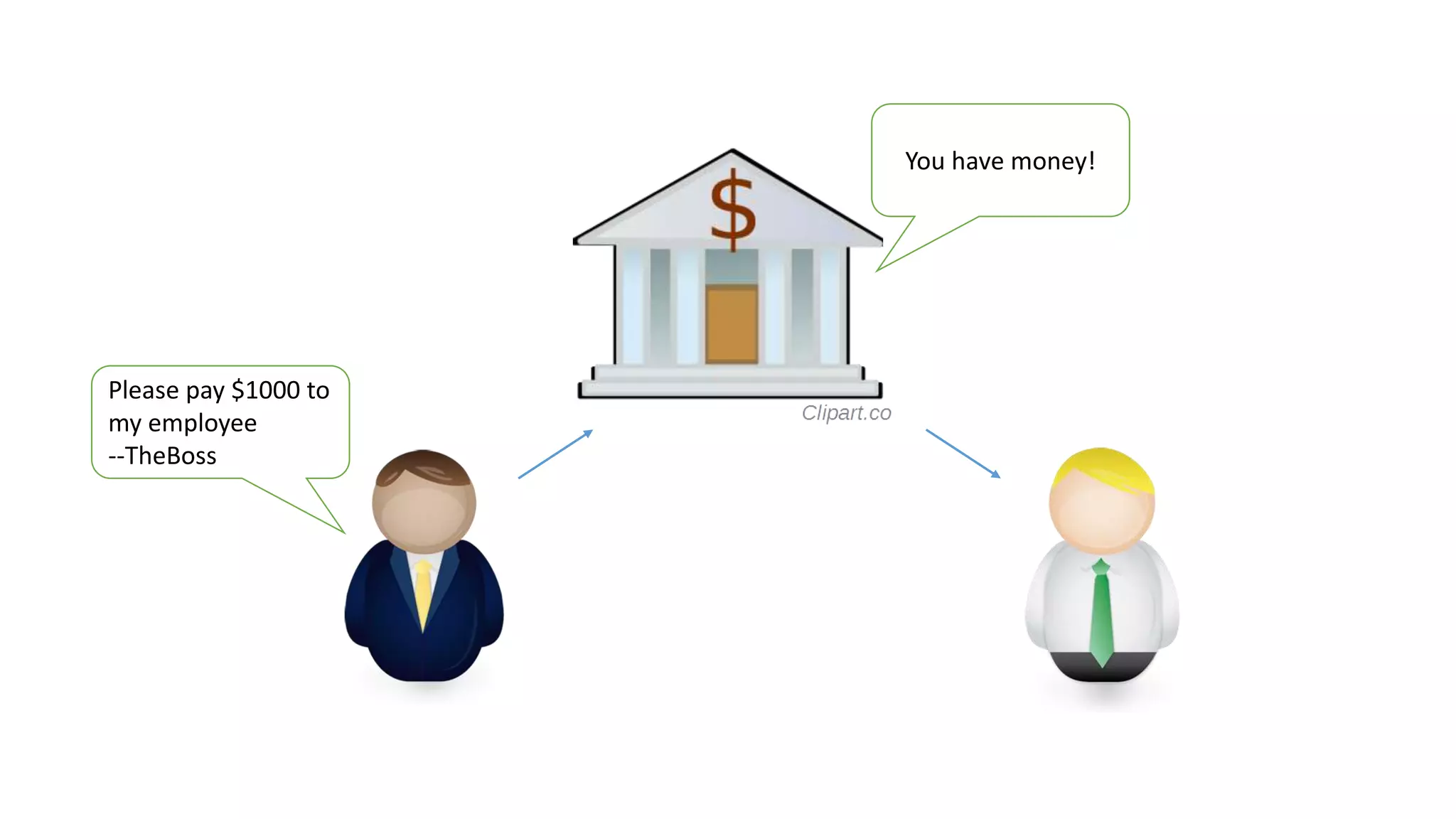
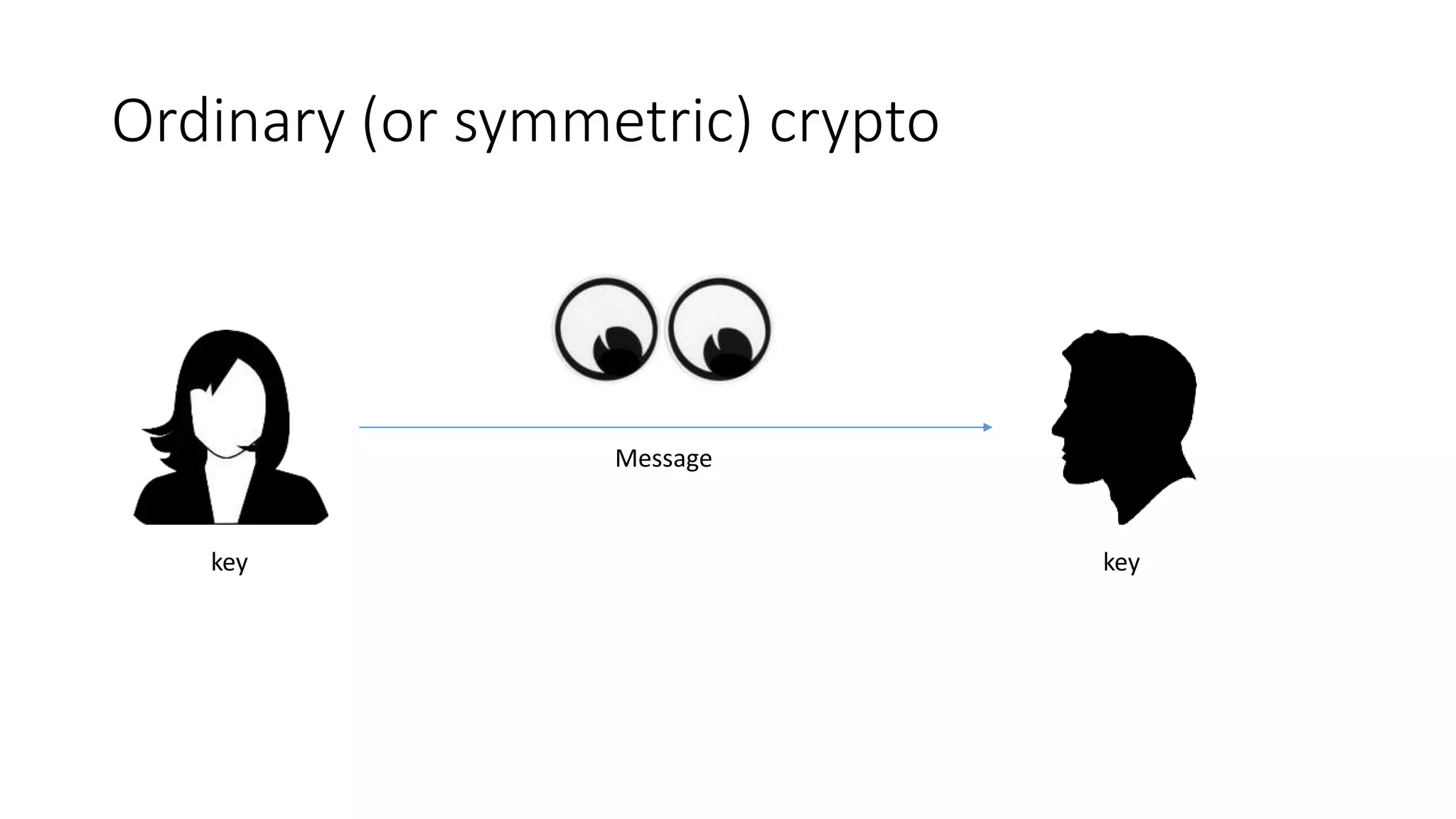
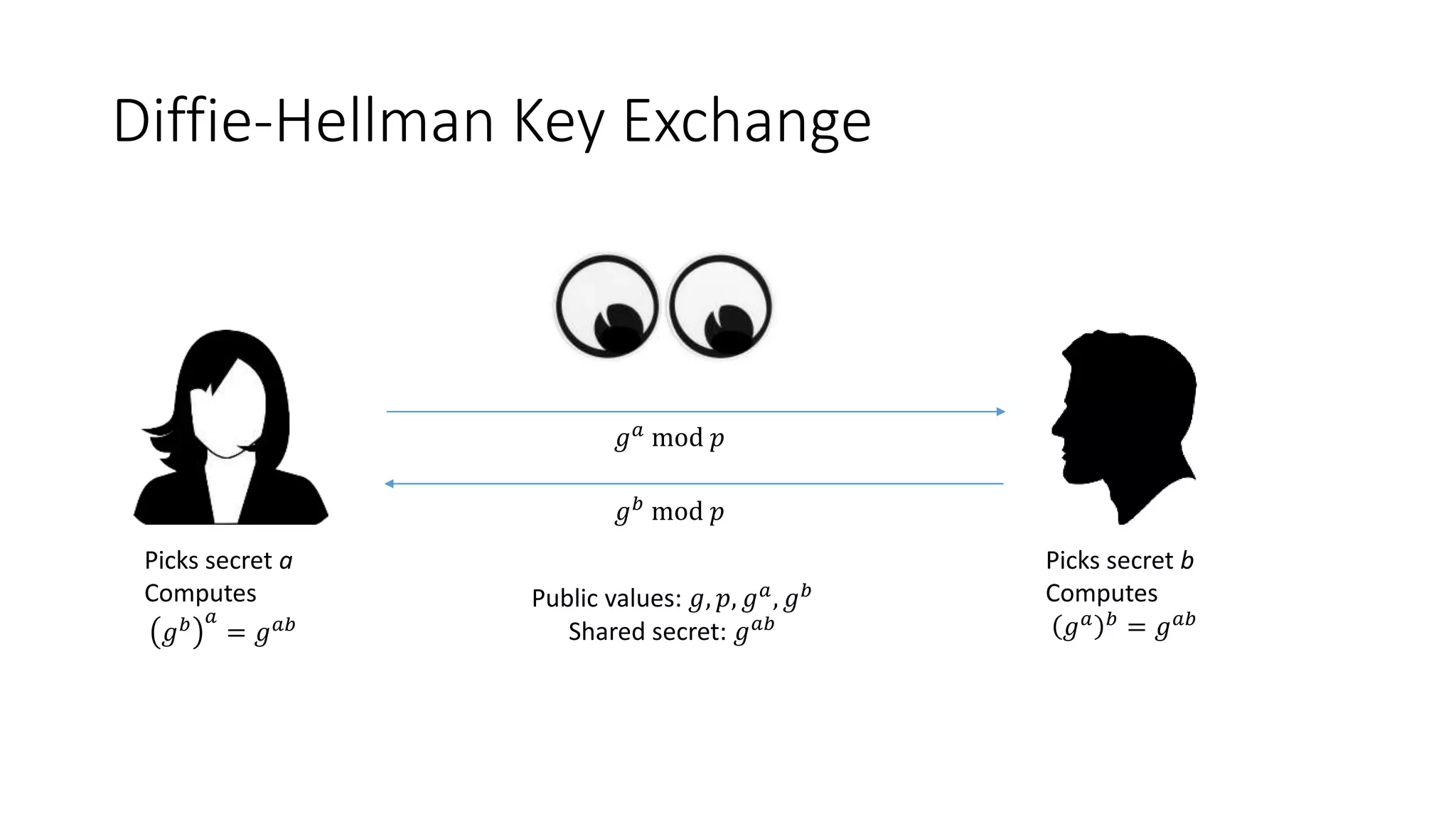
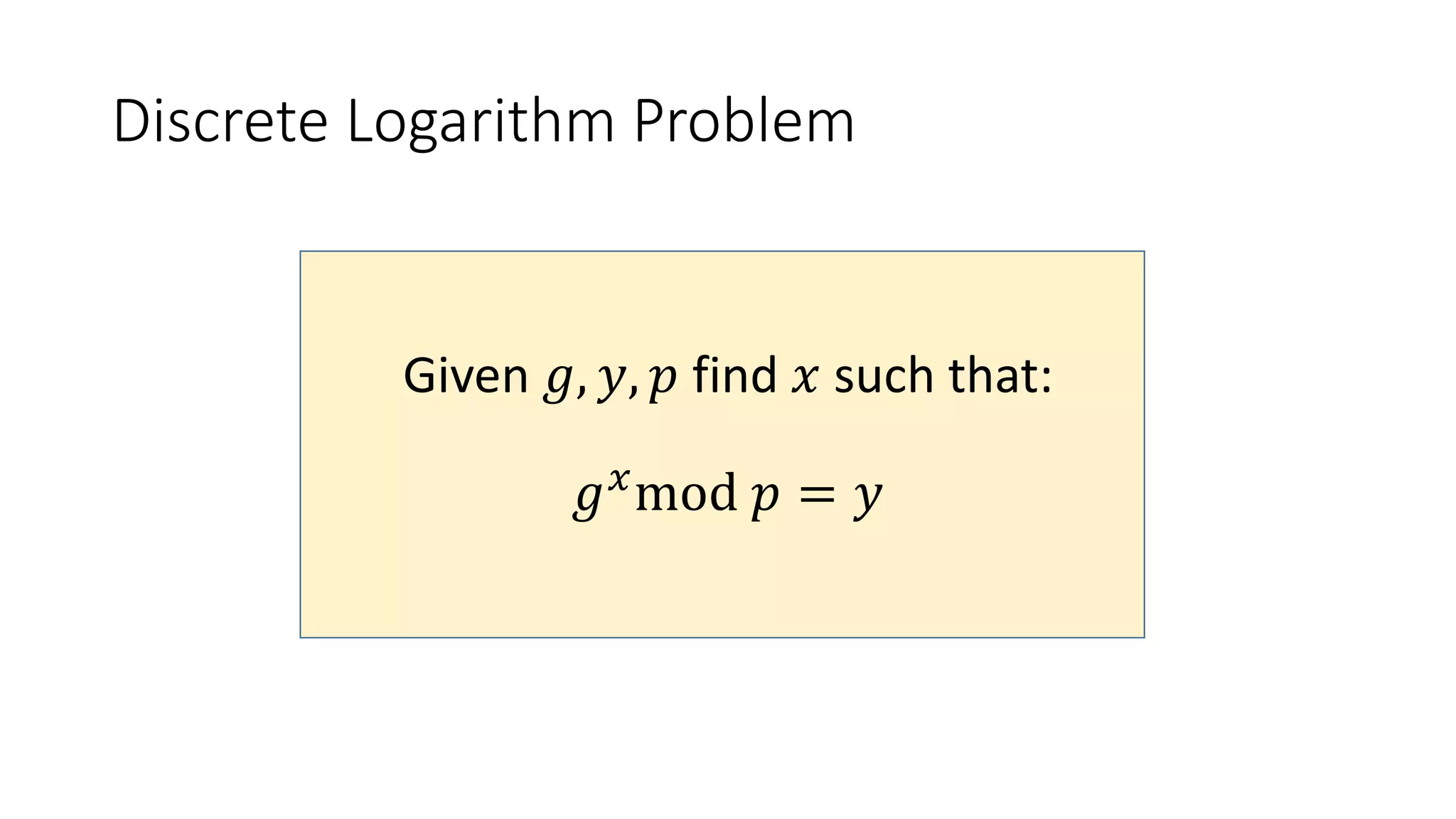
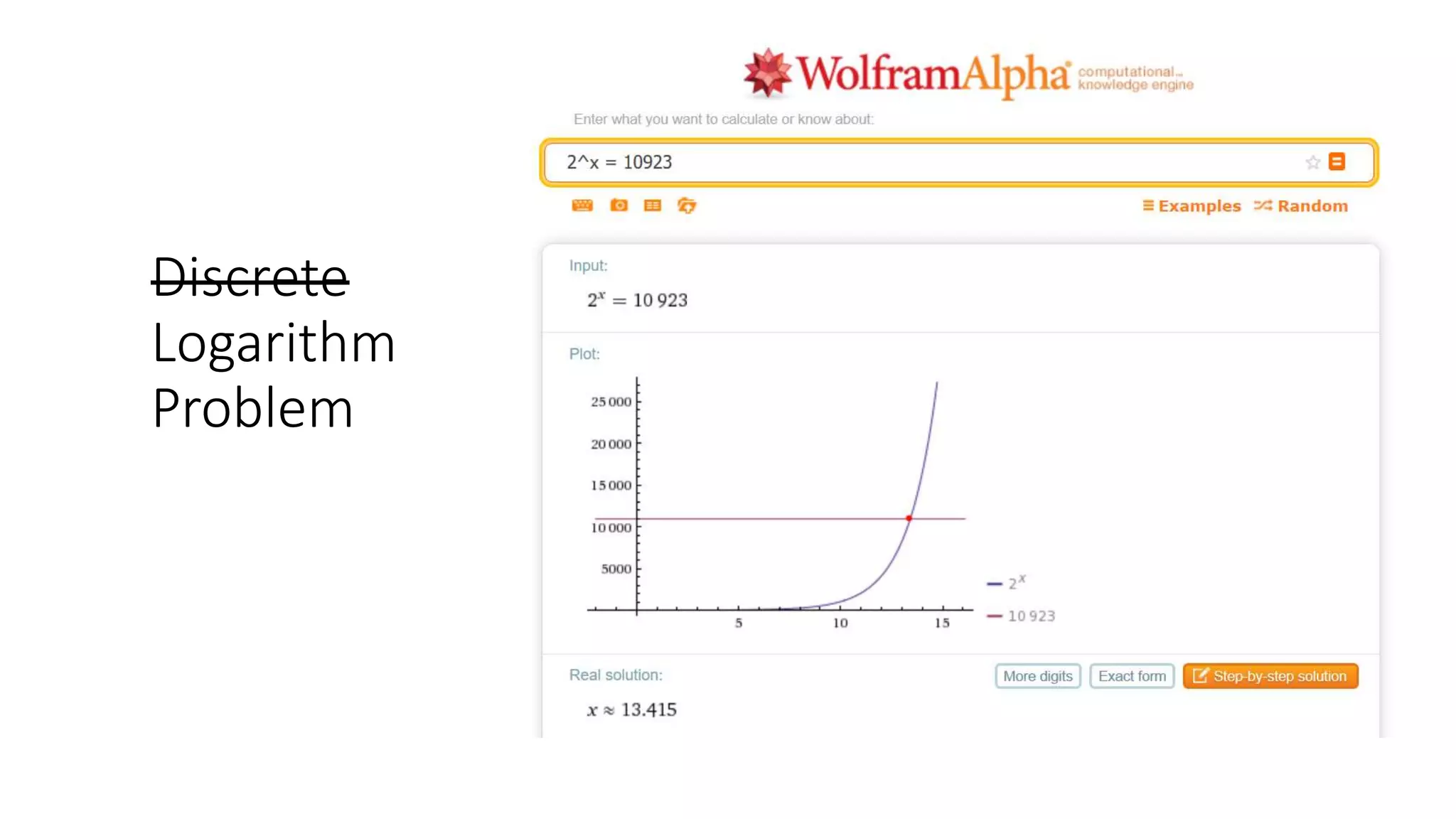
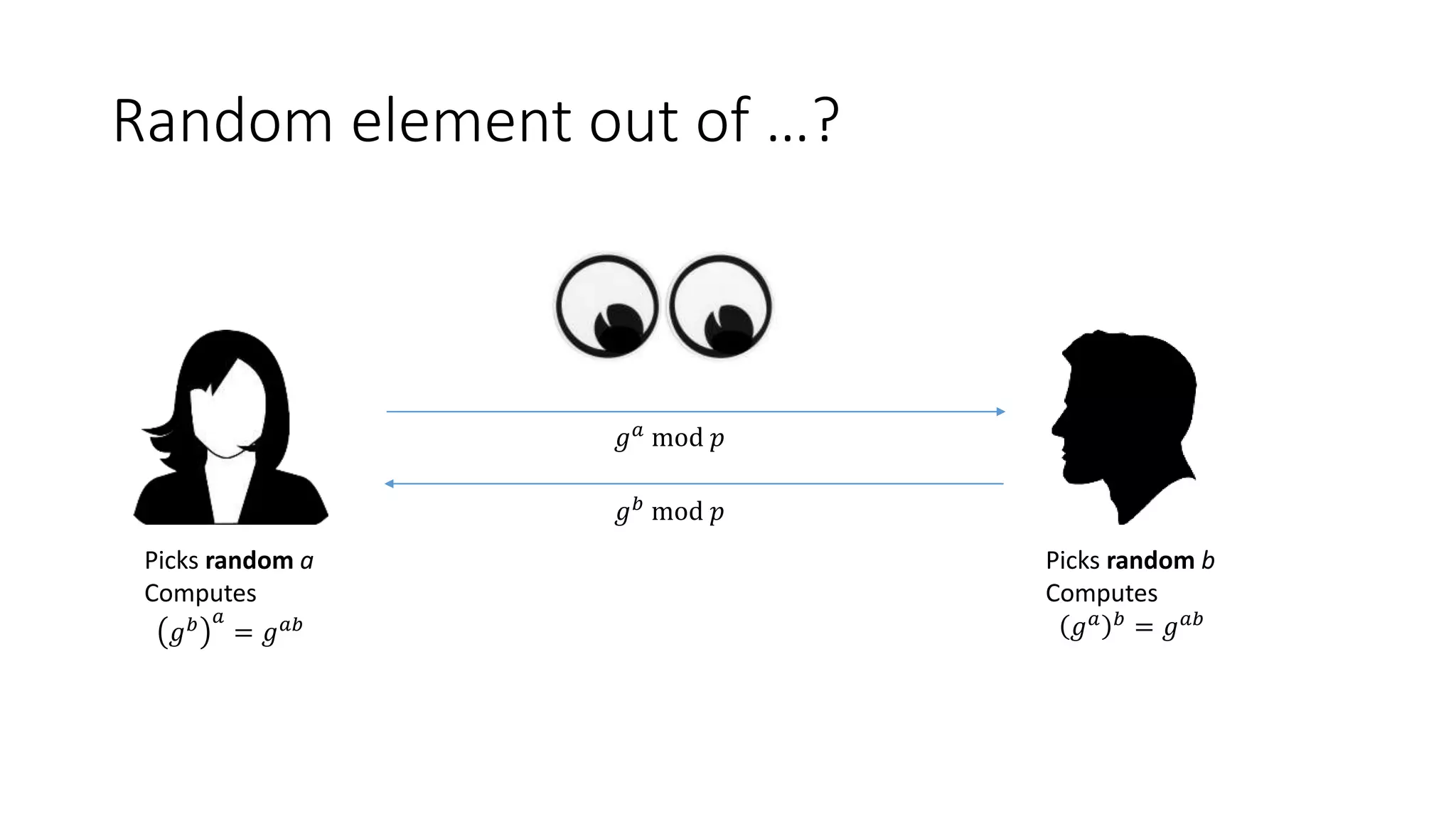
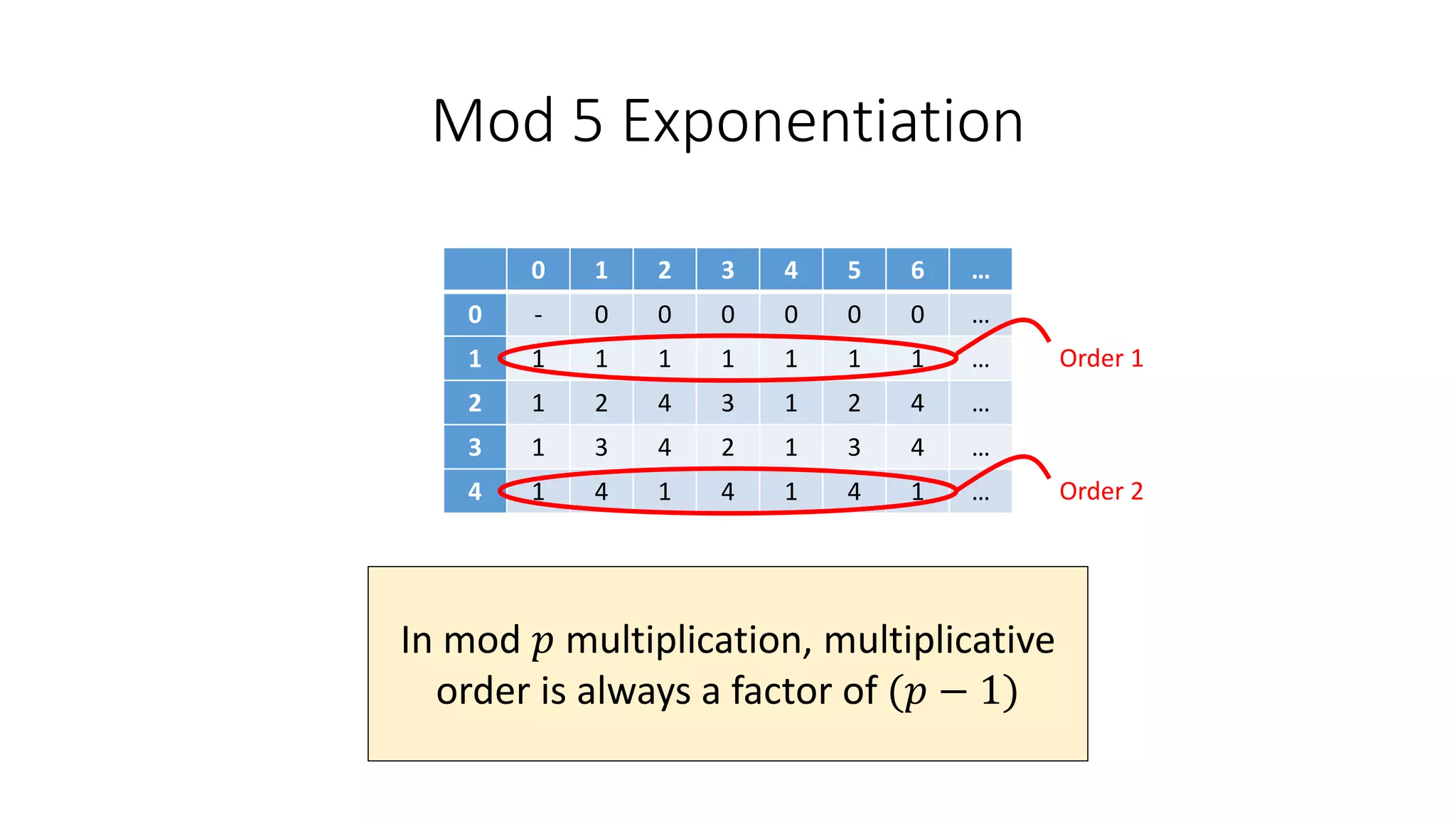
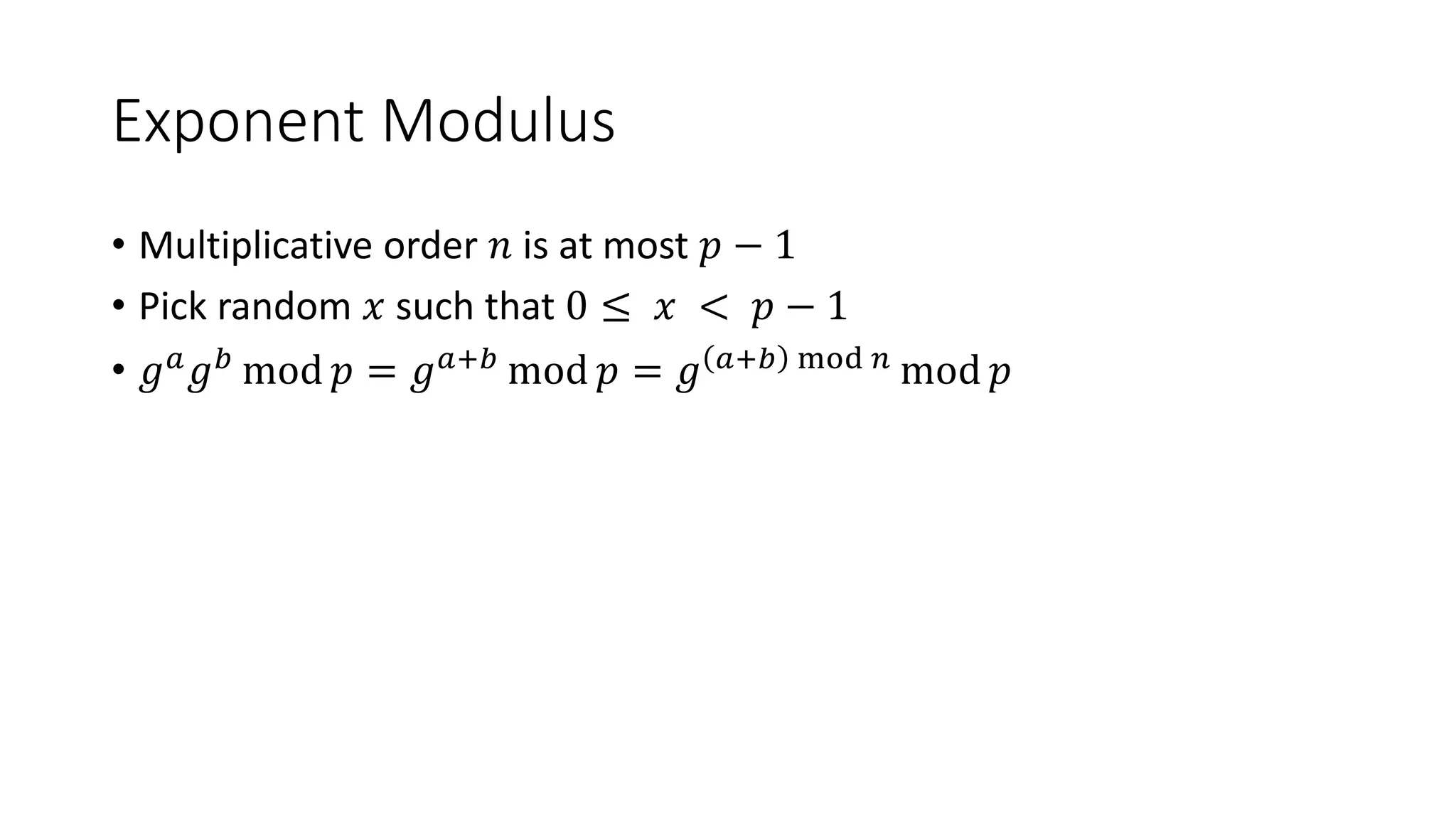
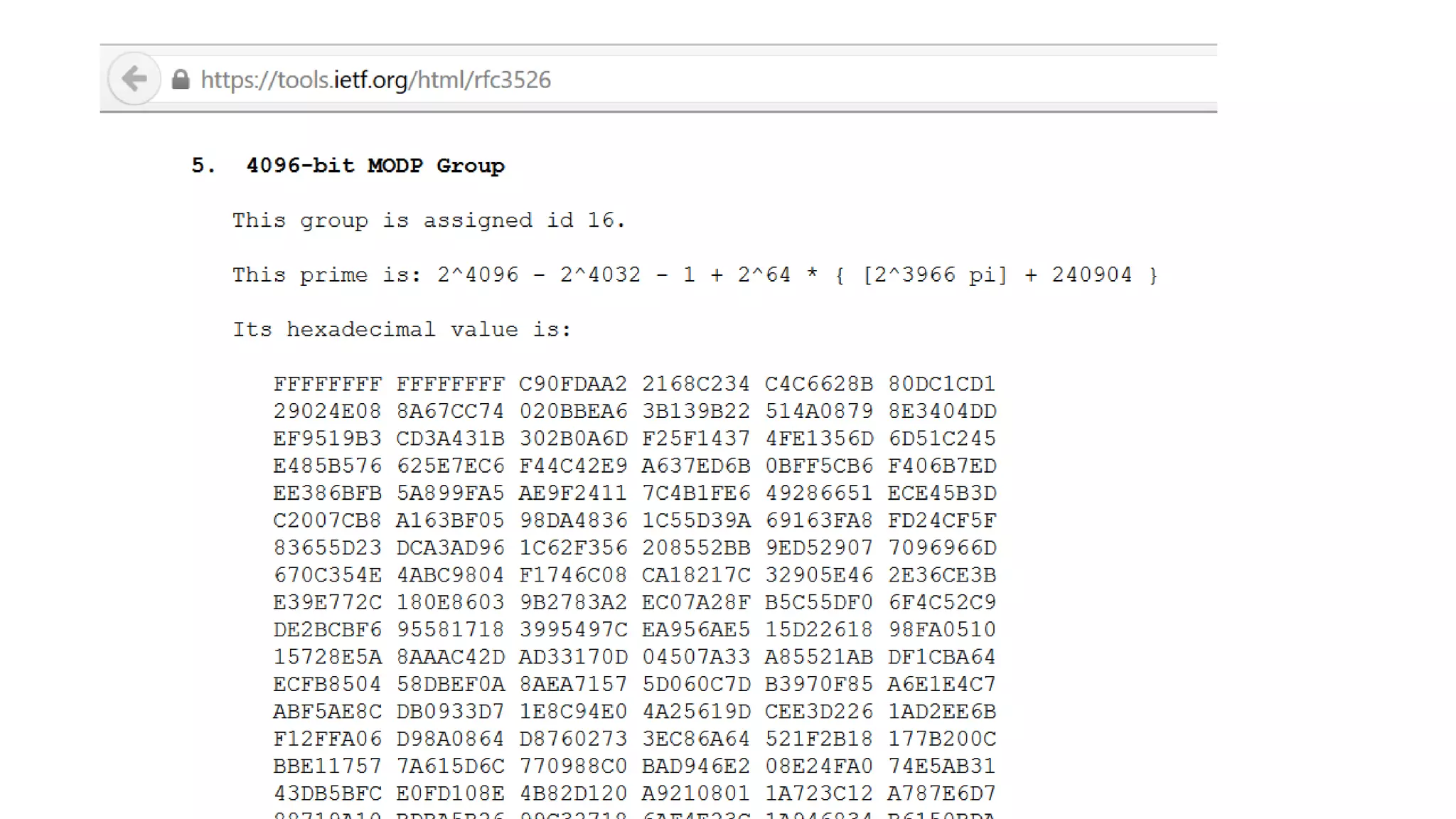
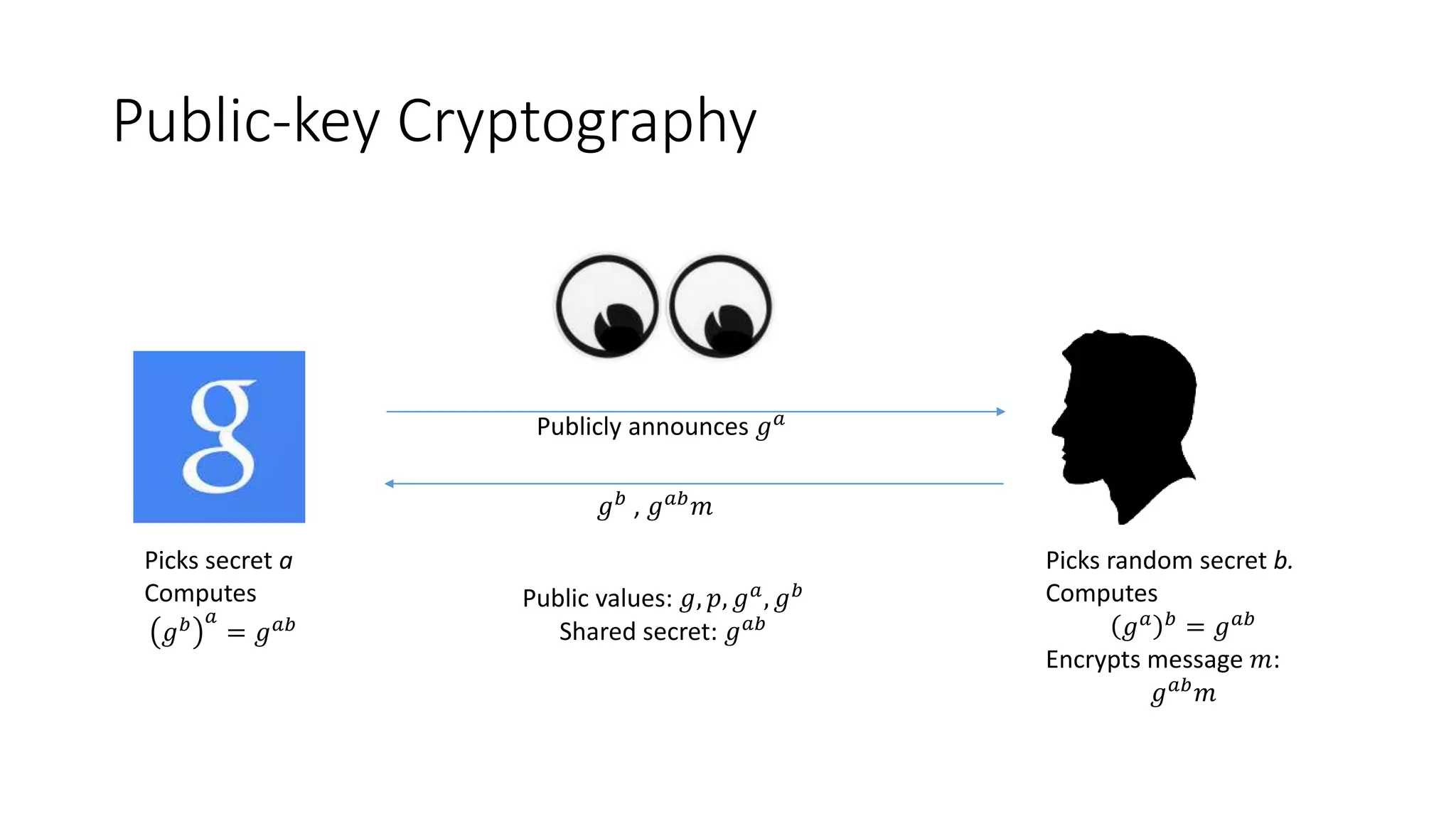
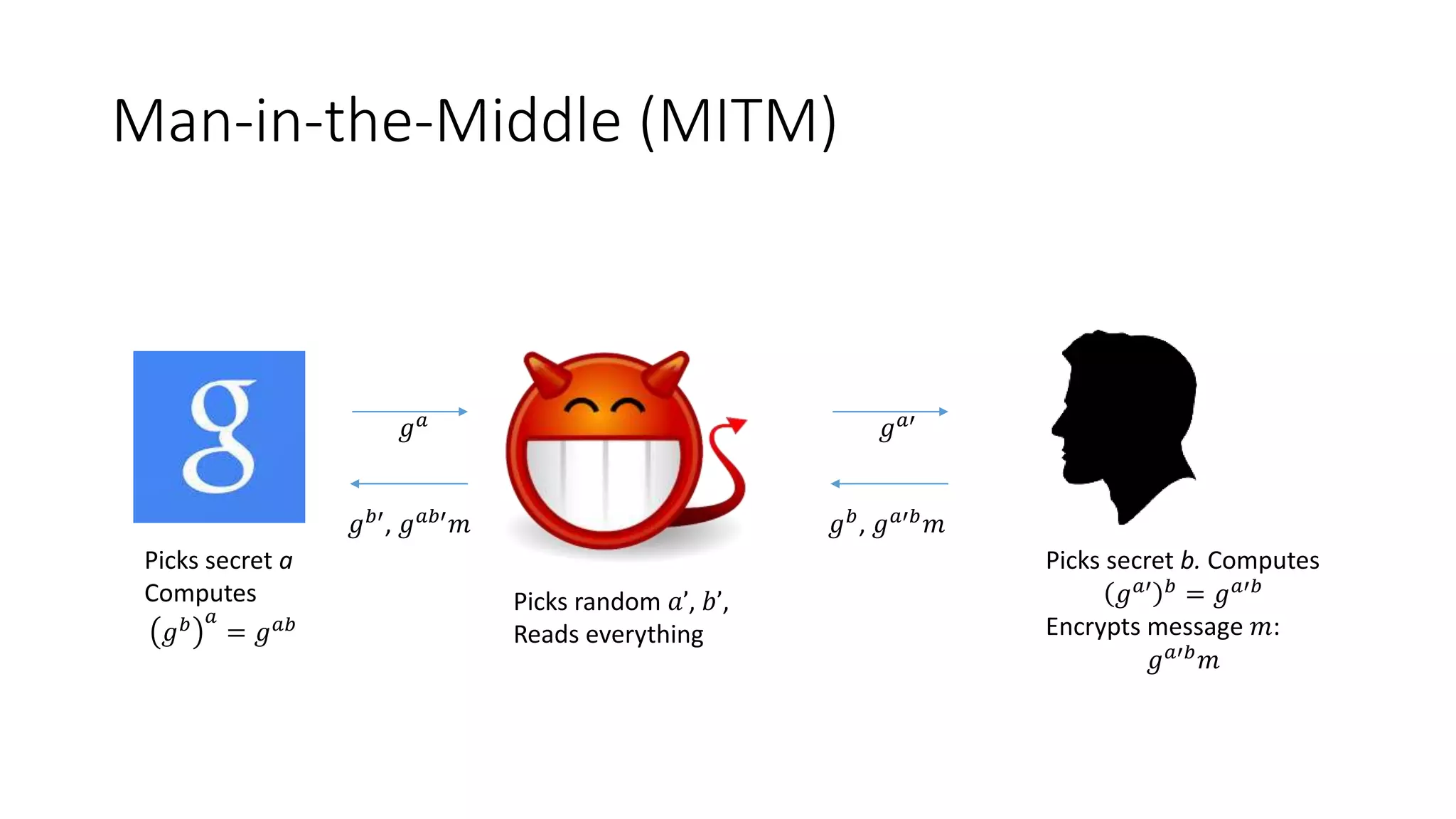
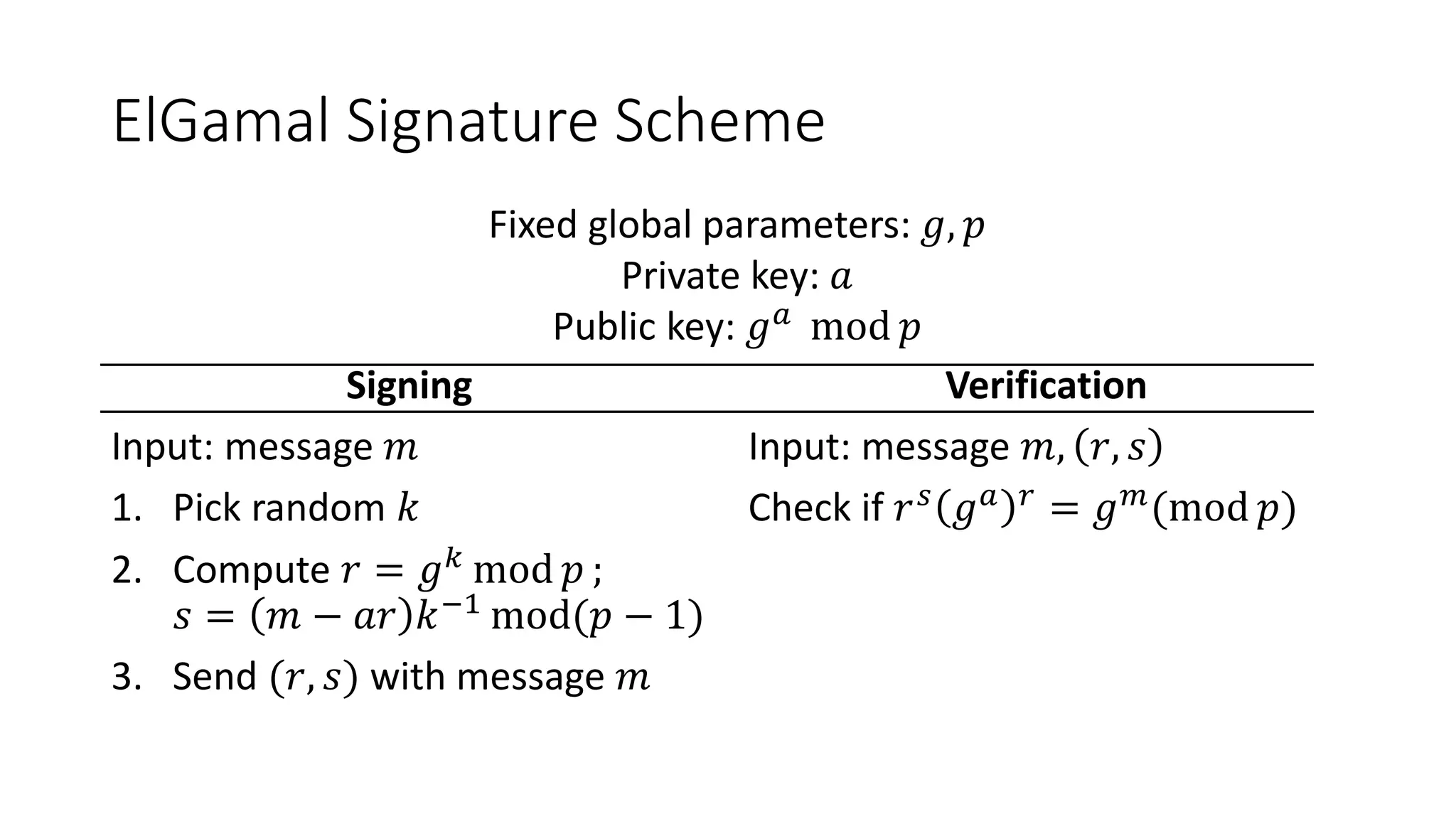
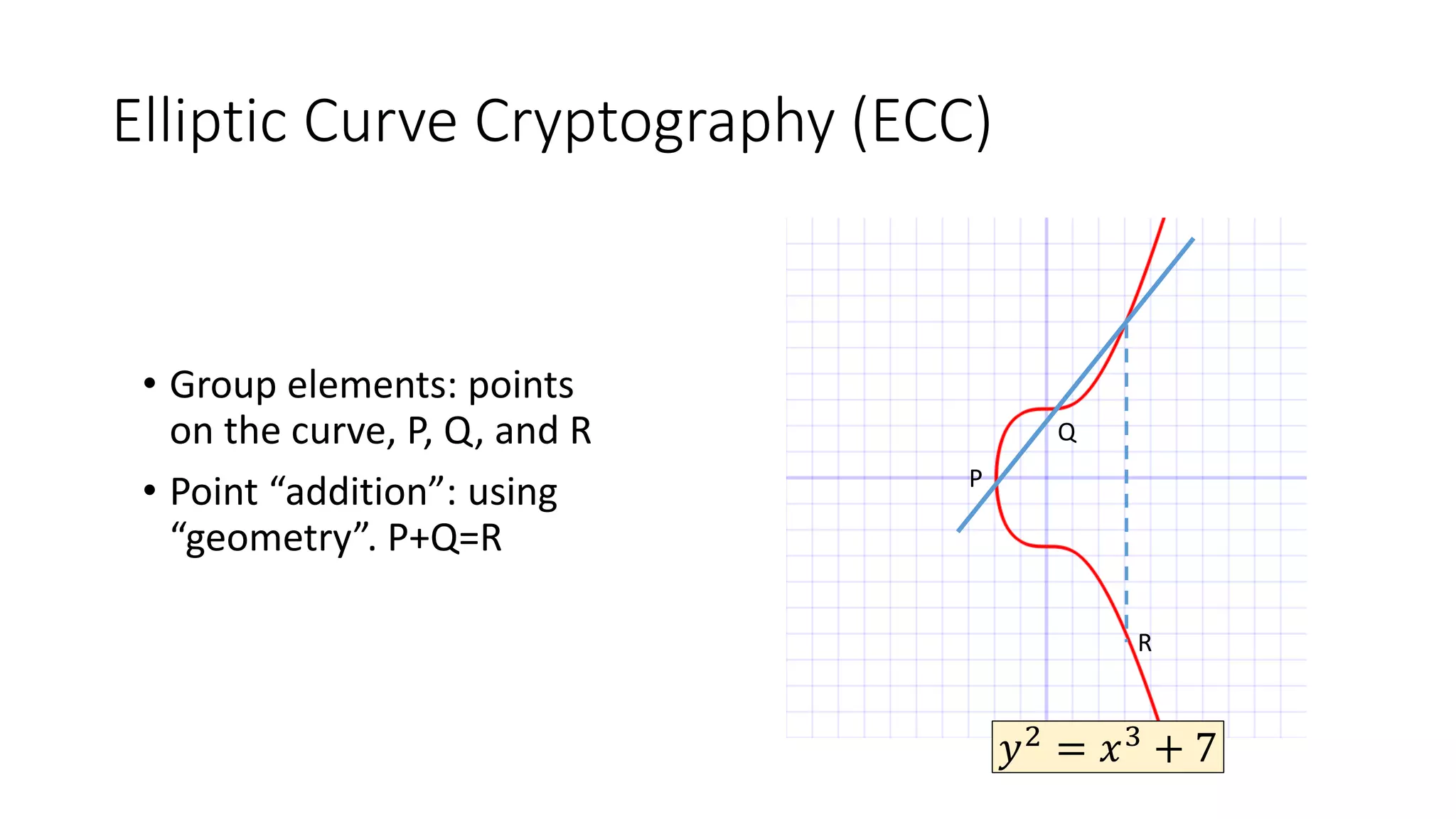
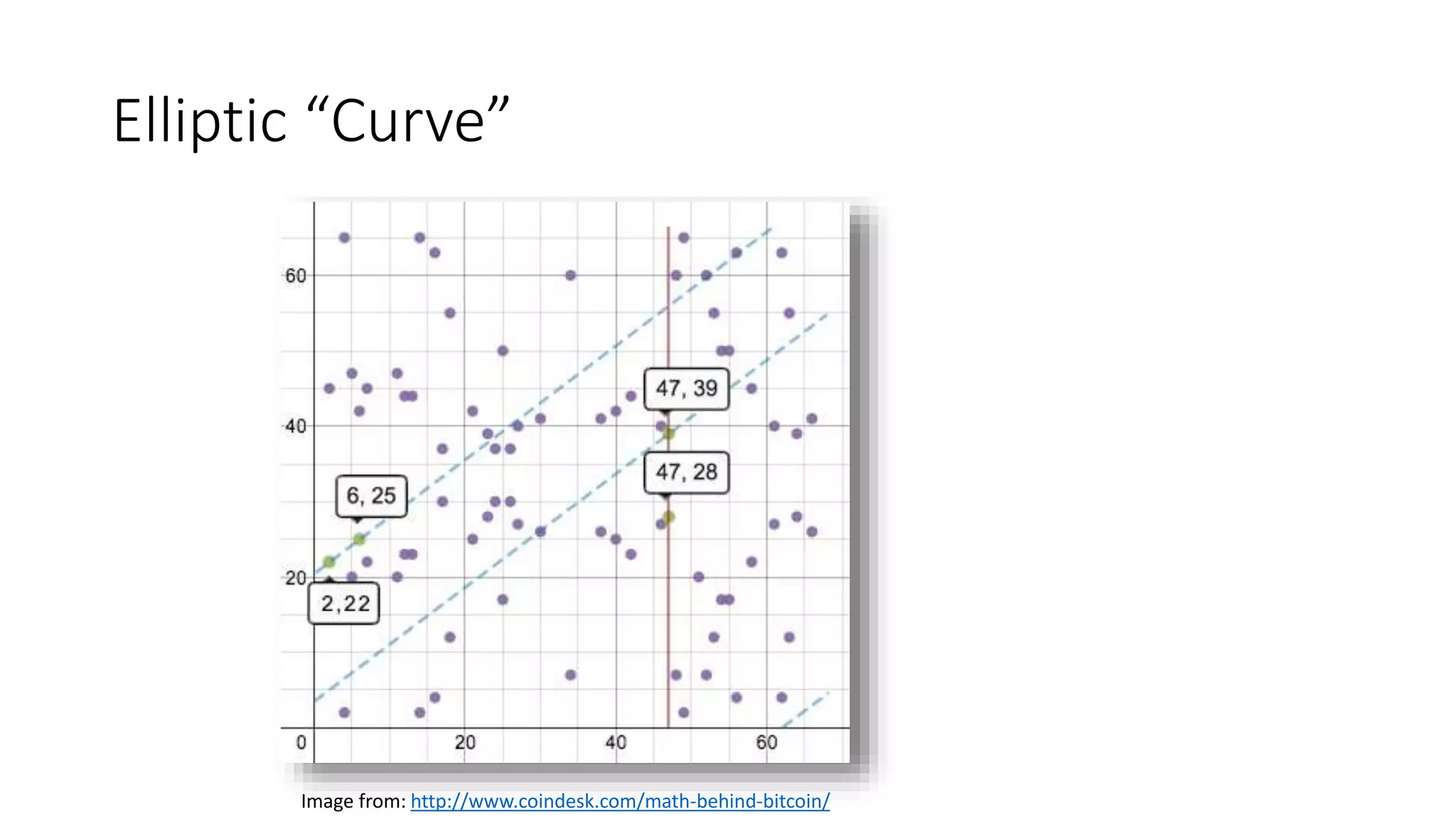
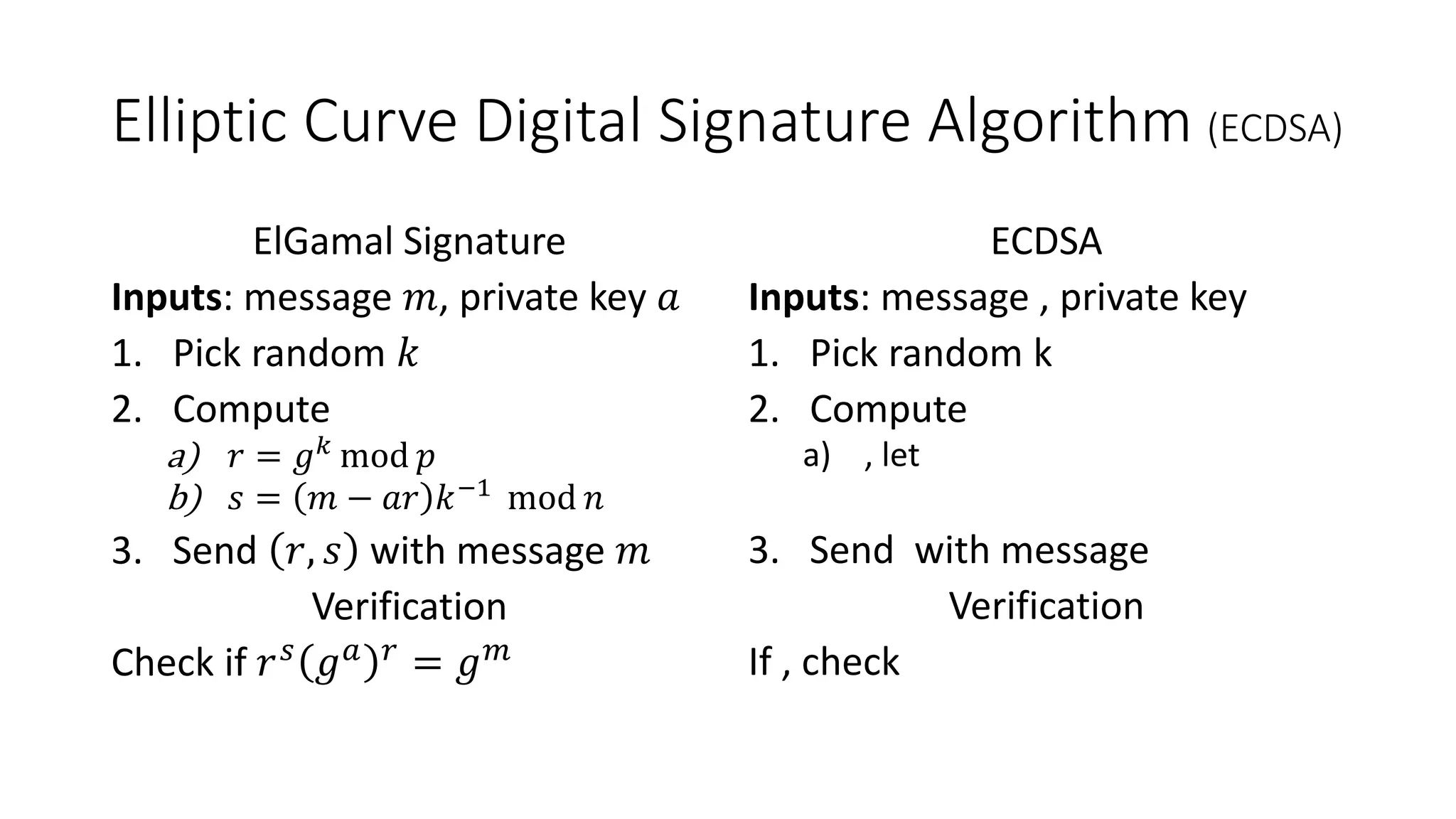
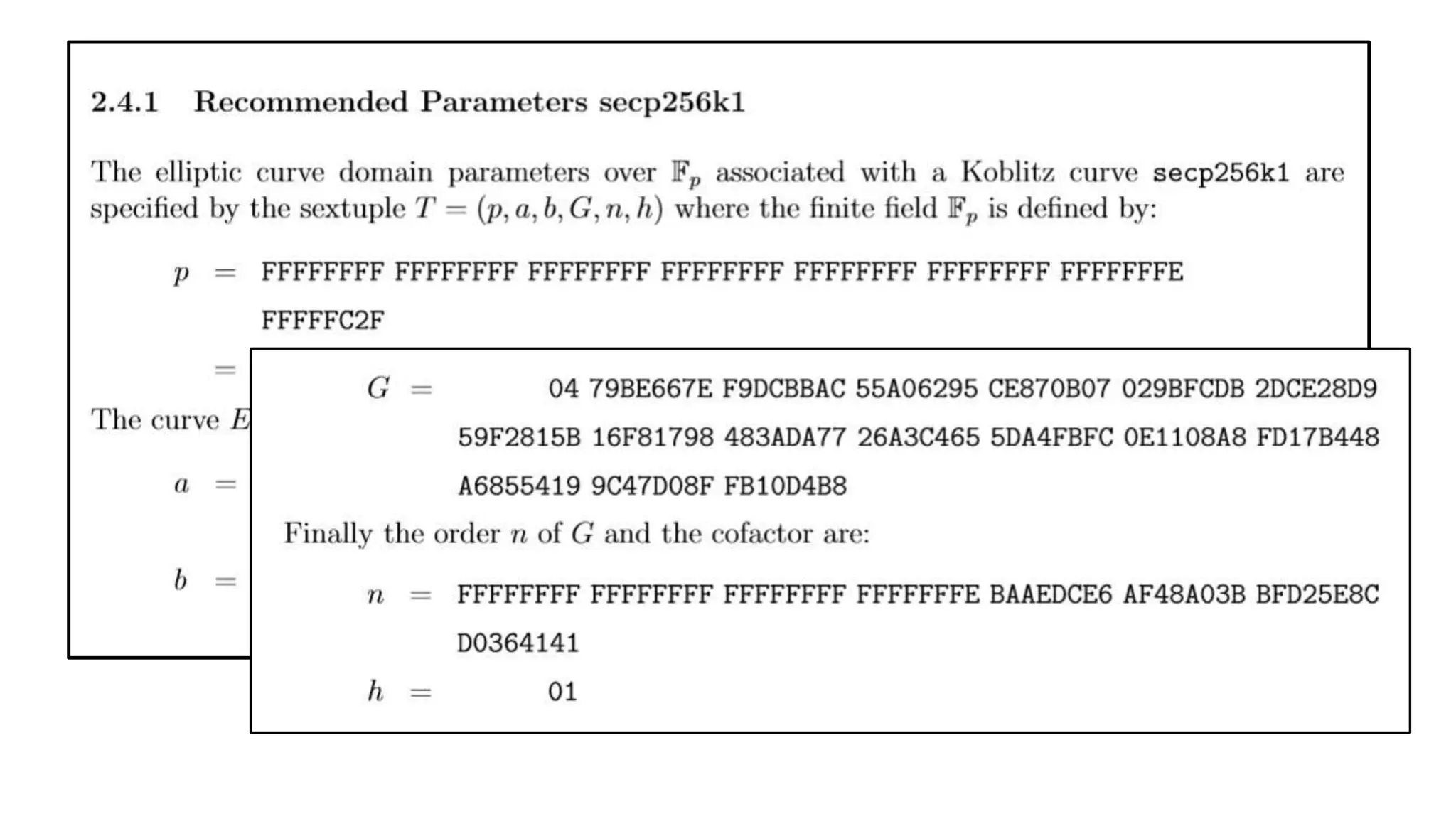
The document covers asymmetric key signatures and cryptographic principles, emphasizing the ease of verification and difficulty of forgery in both digital and ordinary signatures. It describes key concepts such as discrete logarithm problems, public-key cryptography, and elliptic curve cryptography, which are essential for secure digital communications like Bitcoin transactions. The document also touches on specific signature schemes, including ElGamal and ECDSA, illustrating how these cryptographic methods ensure message integrity.