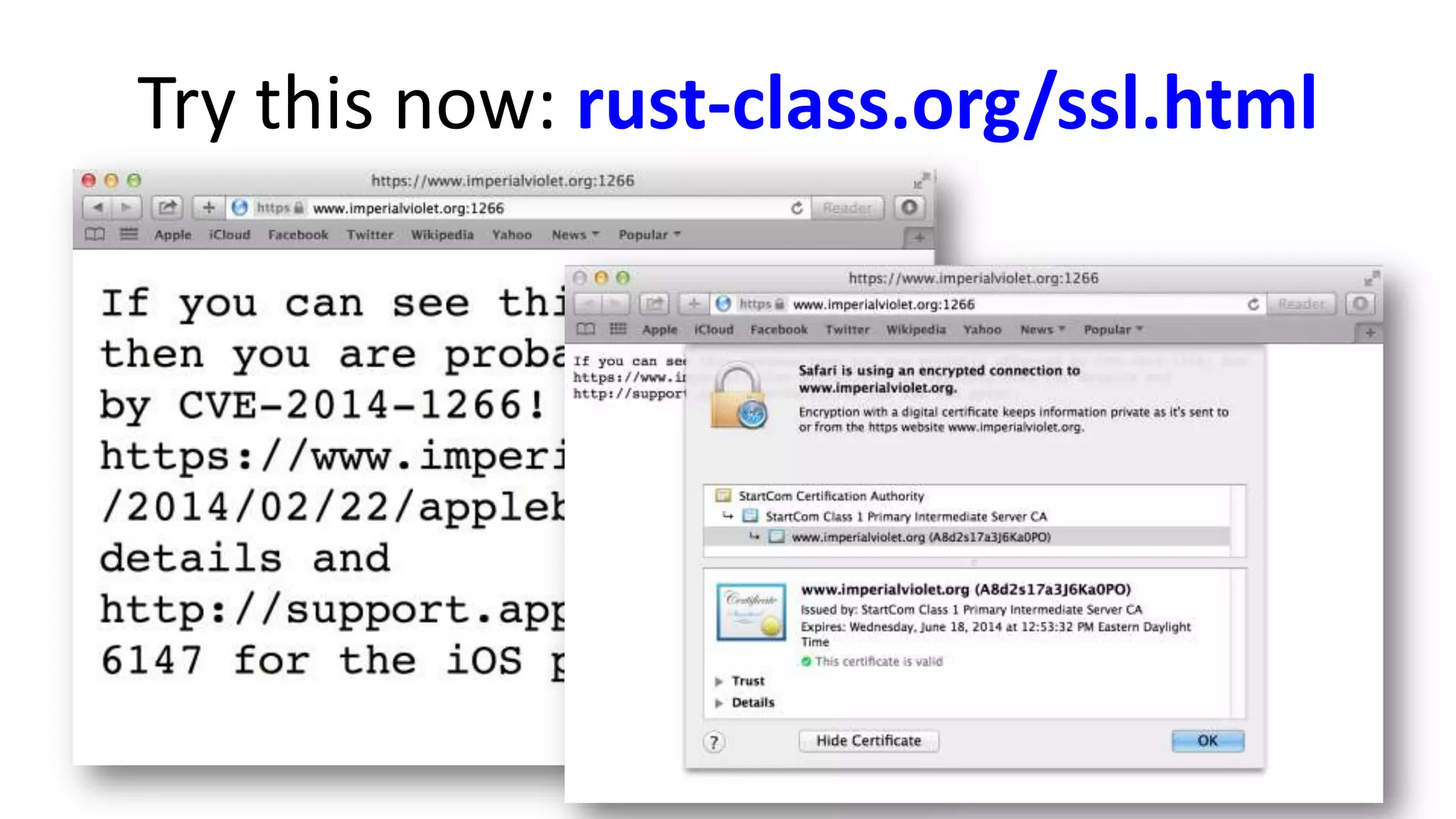
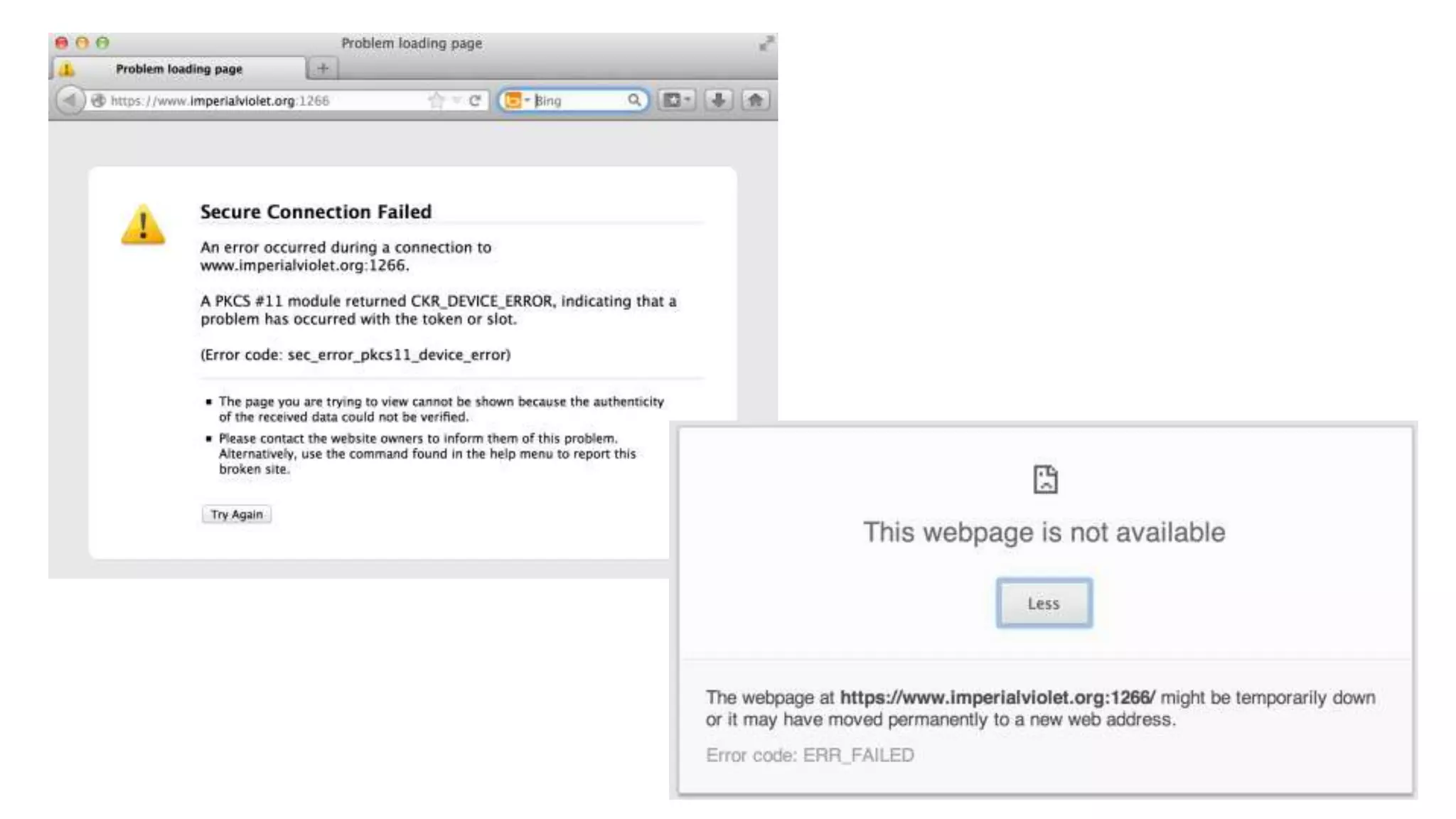
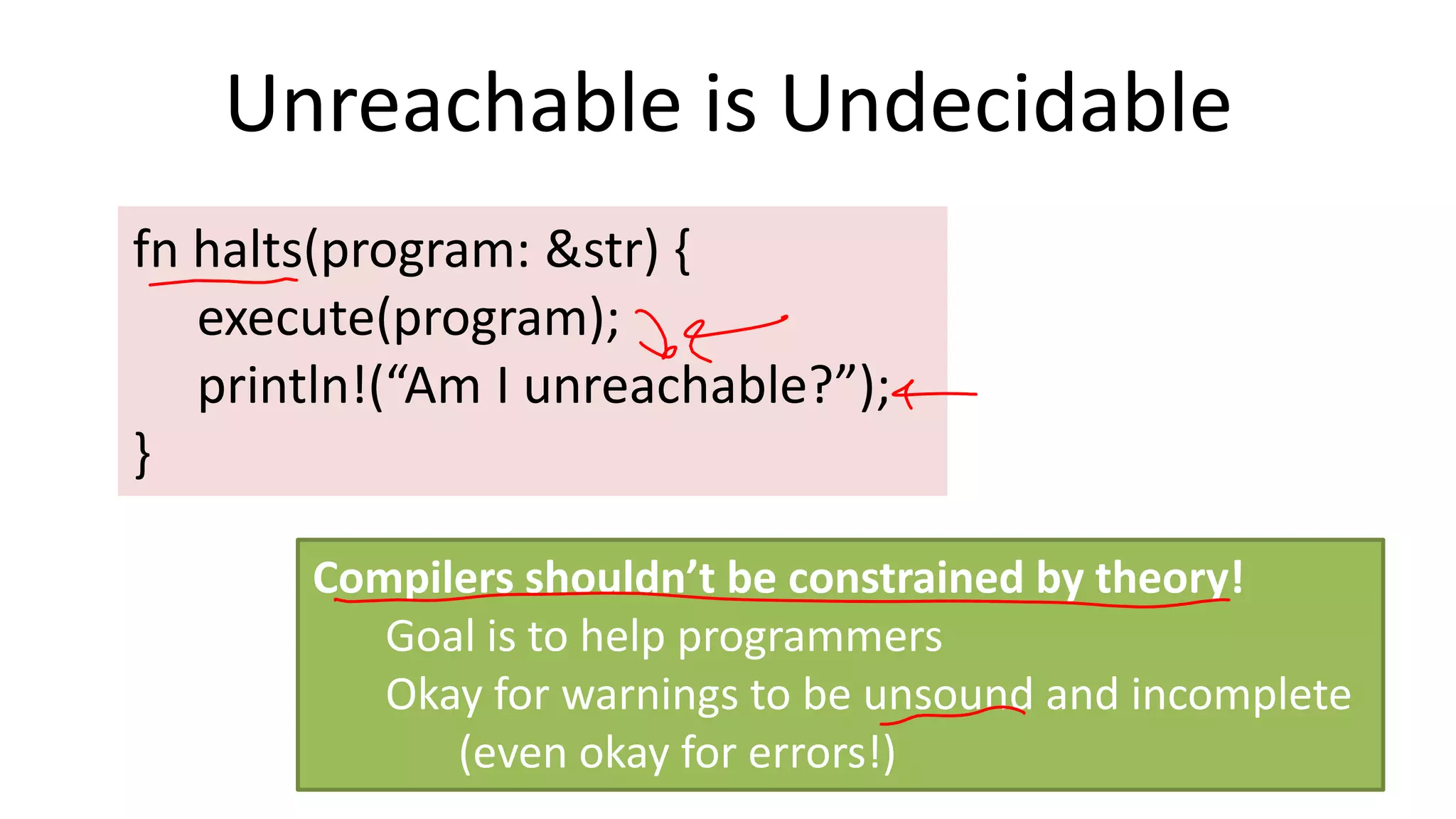
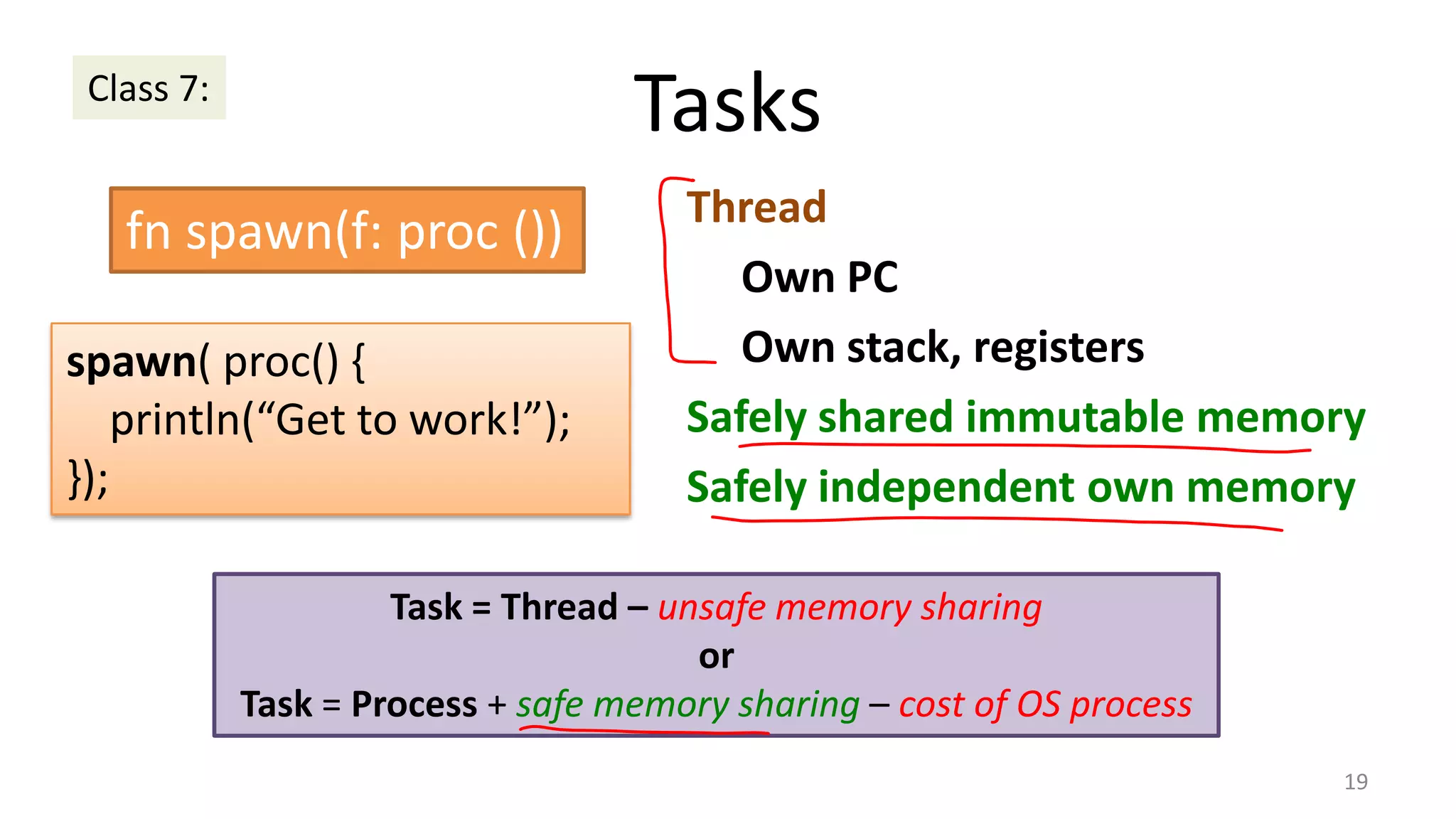
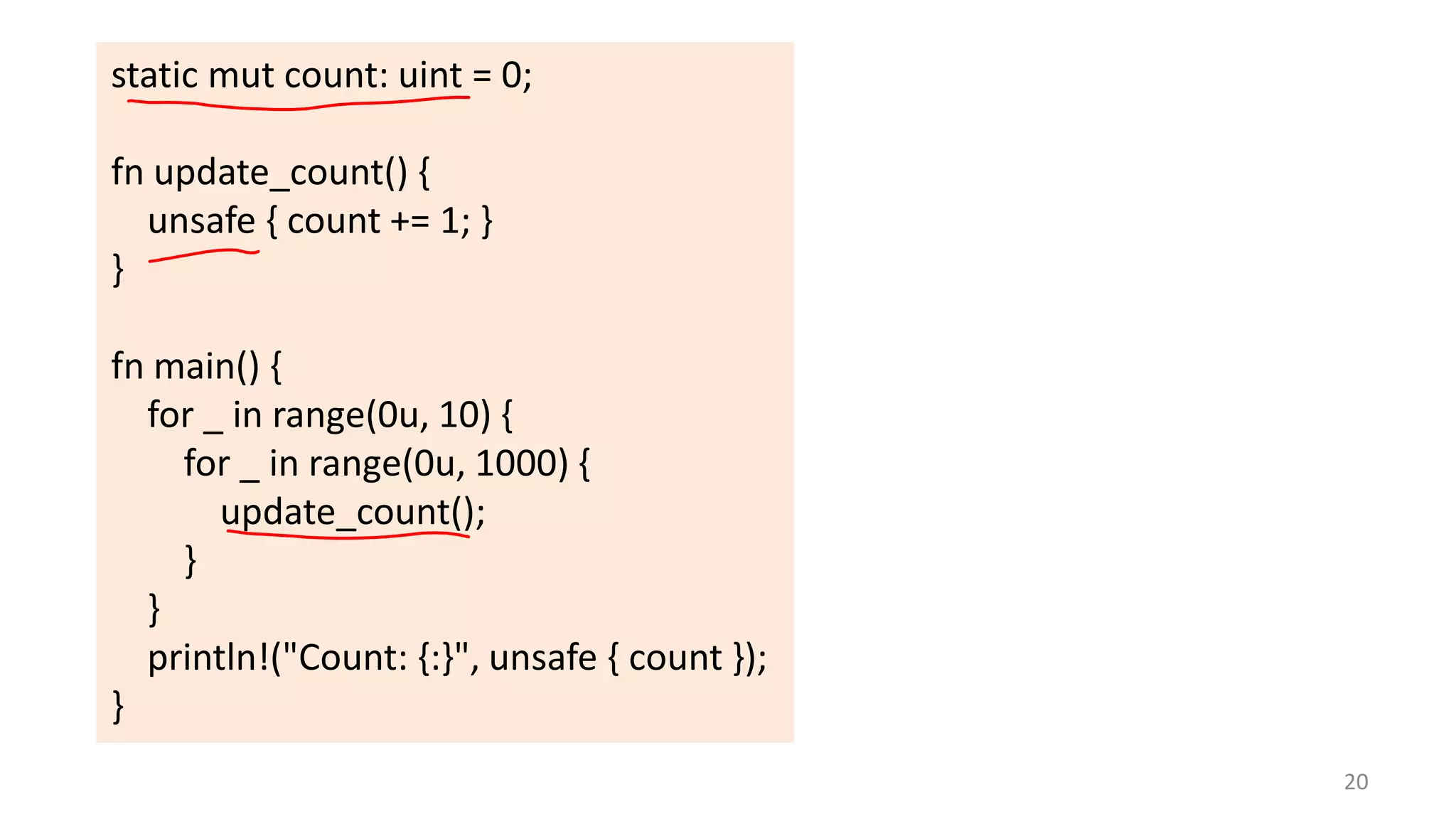
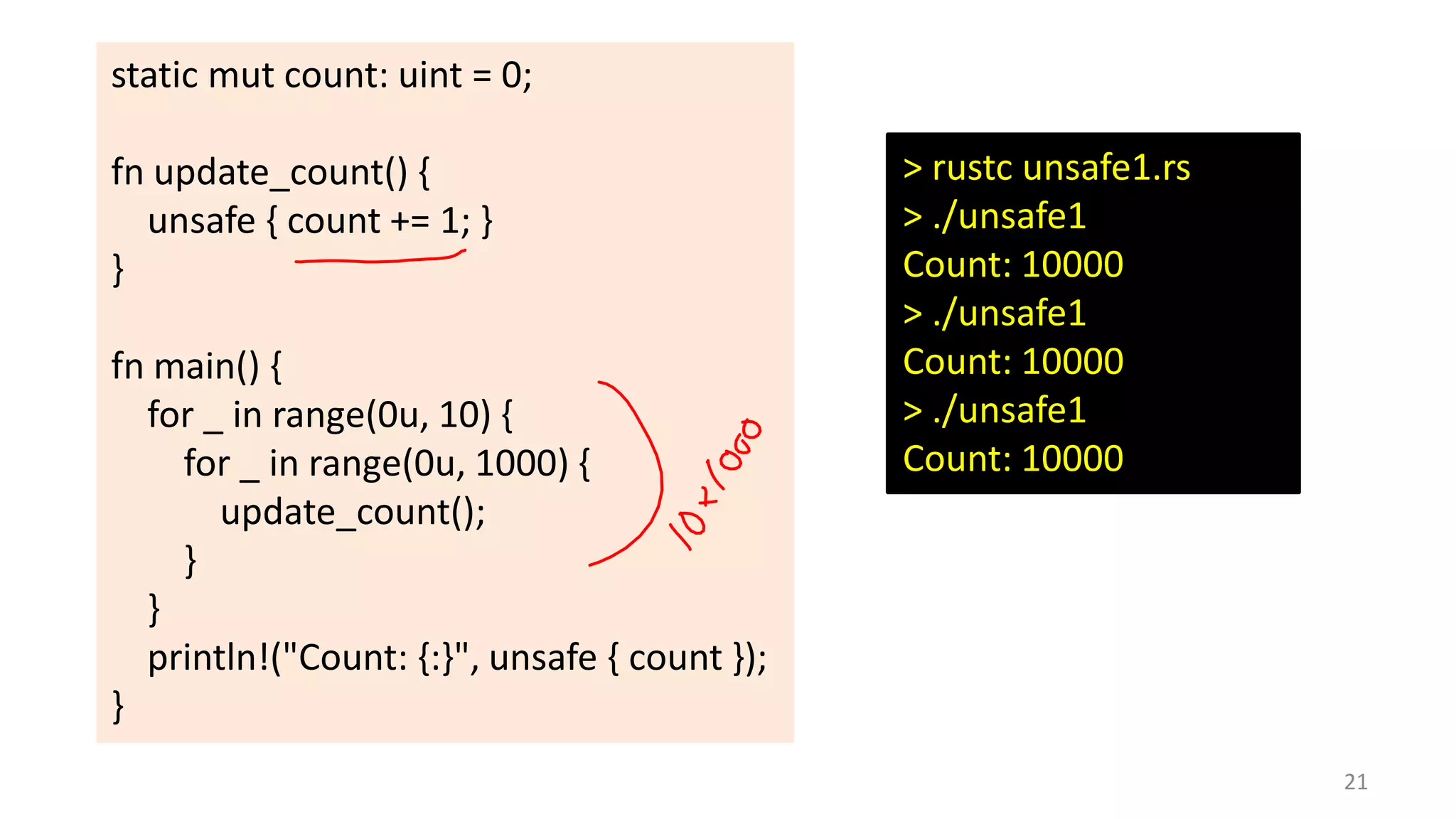
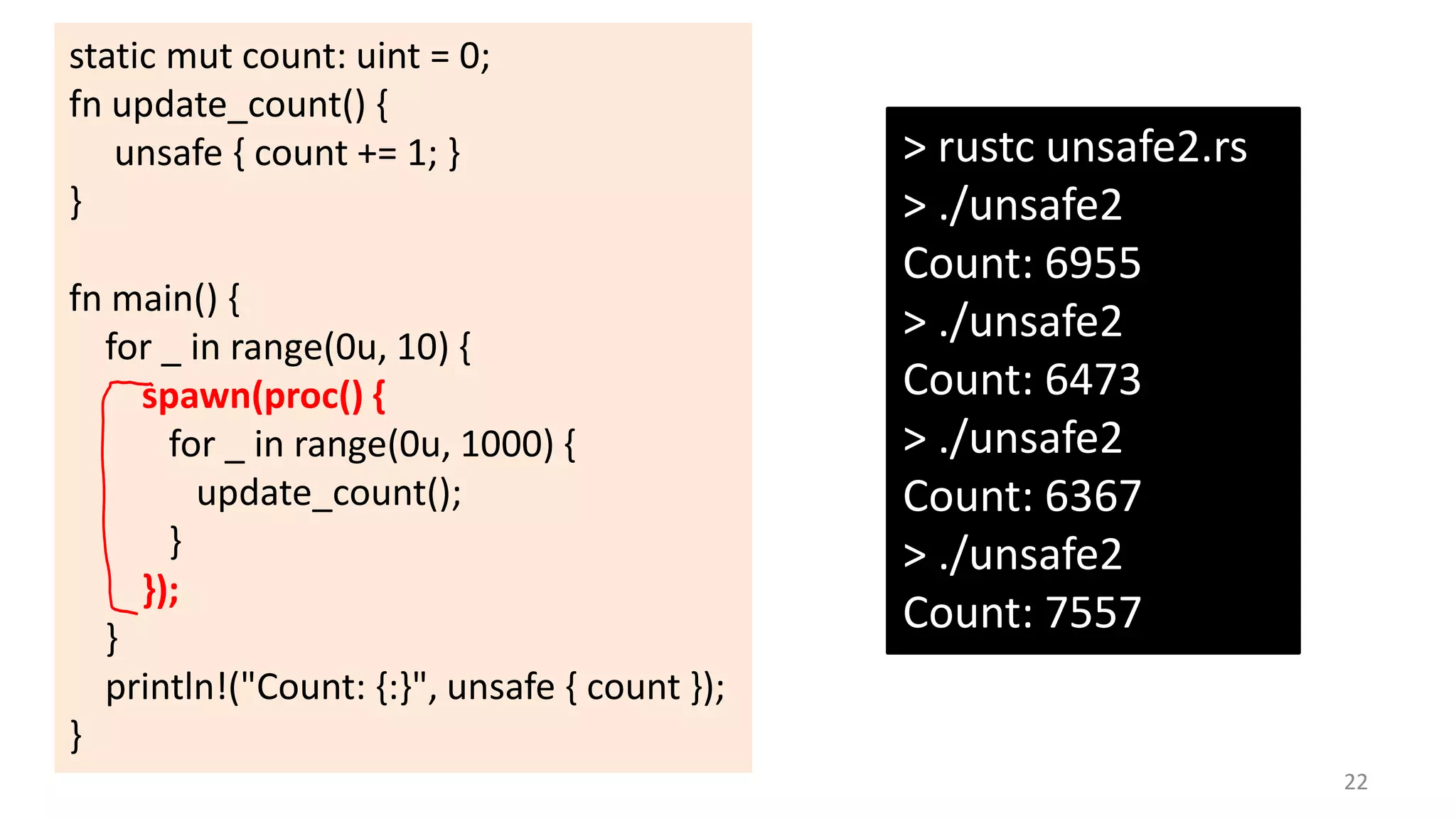
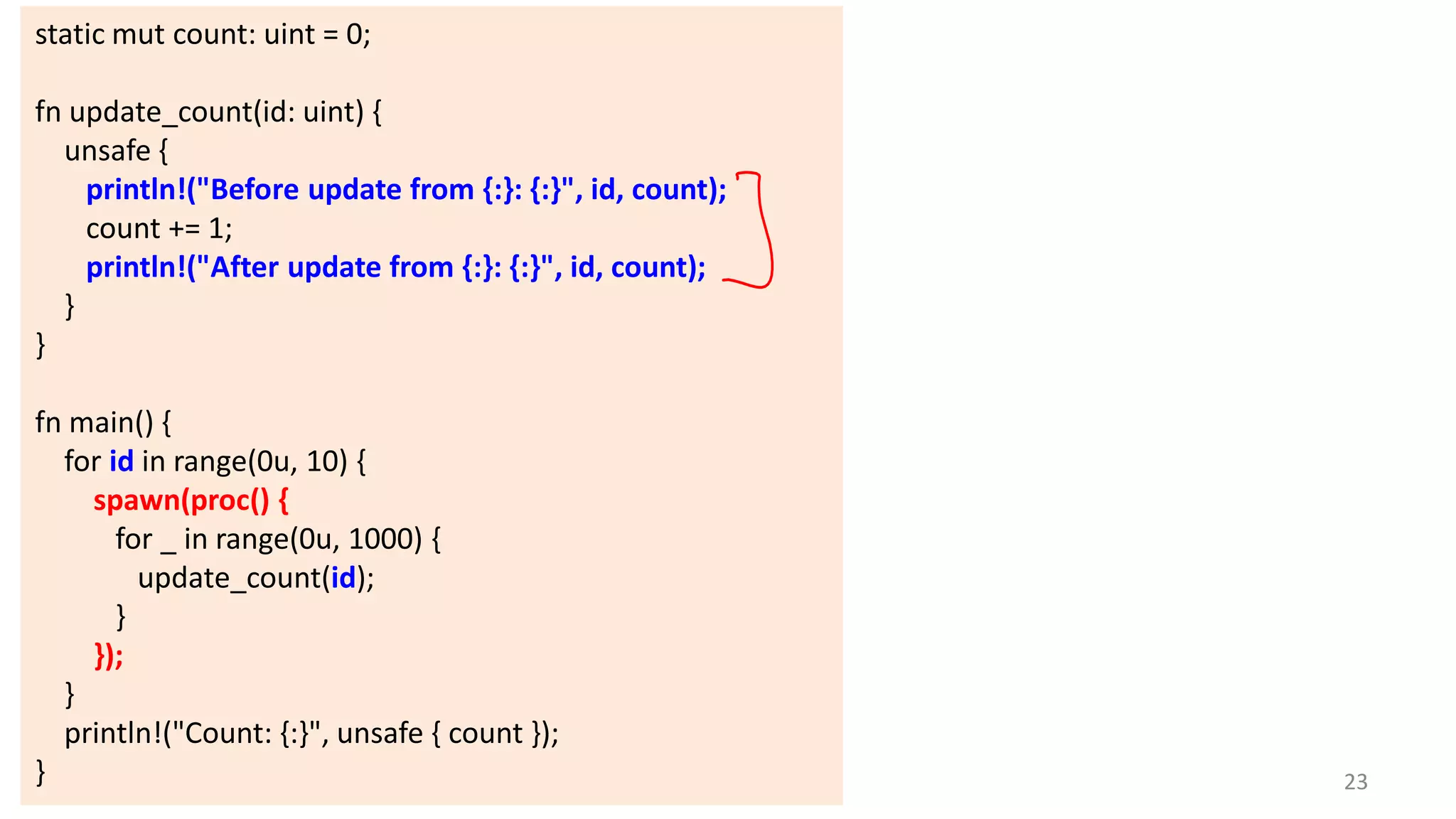
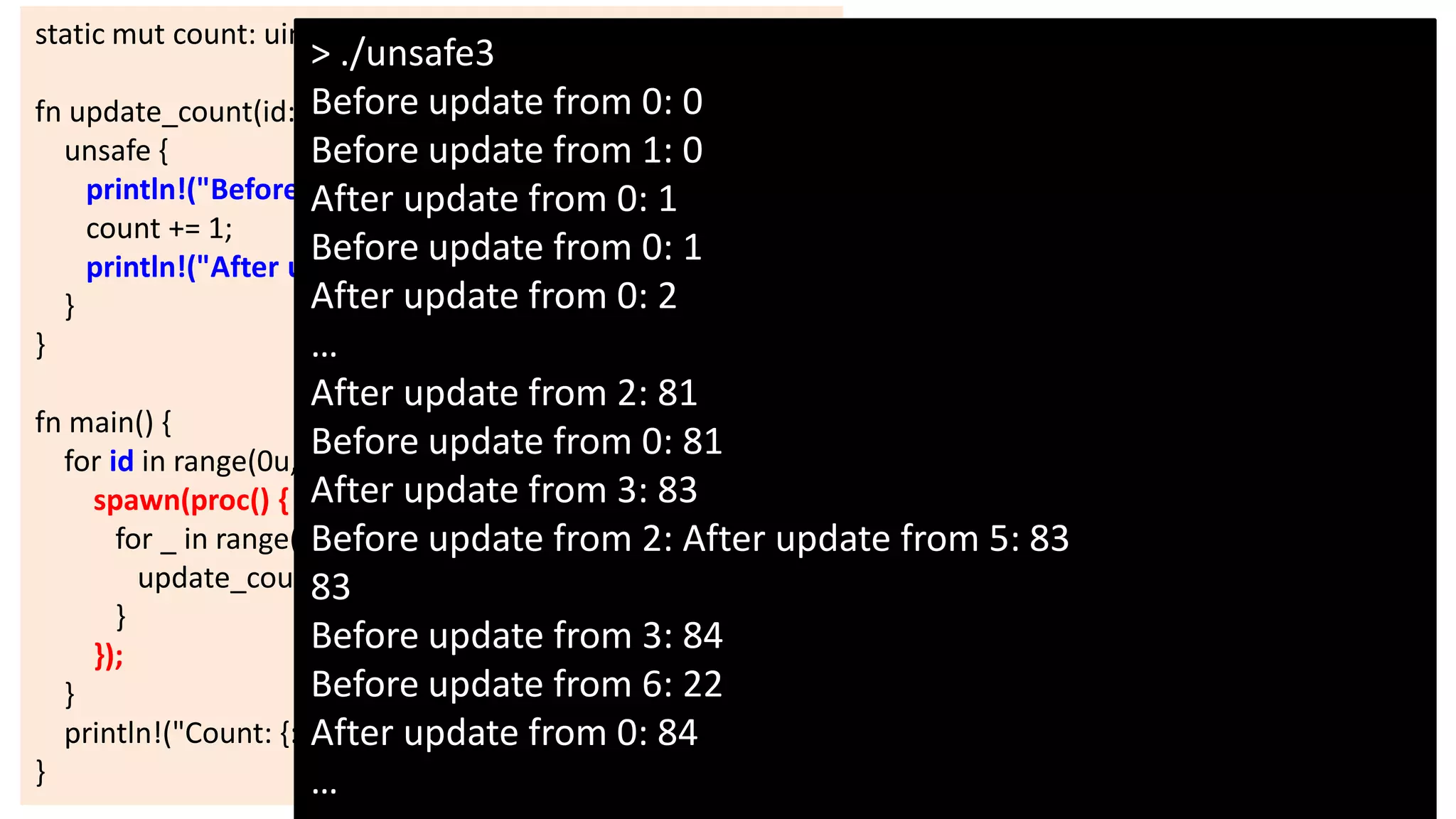
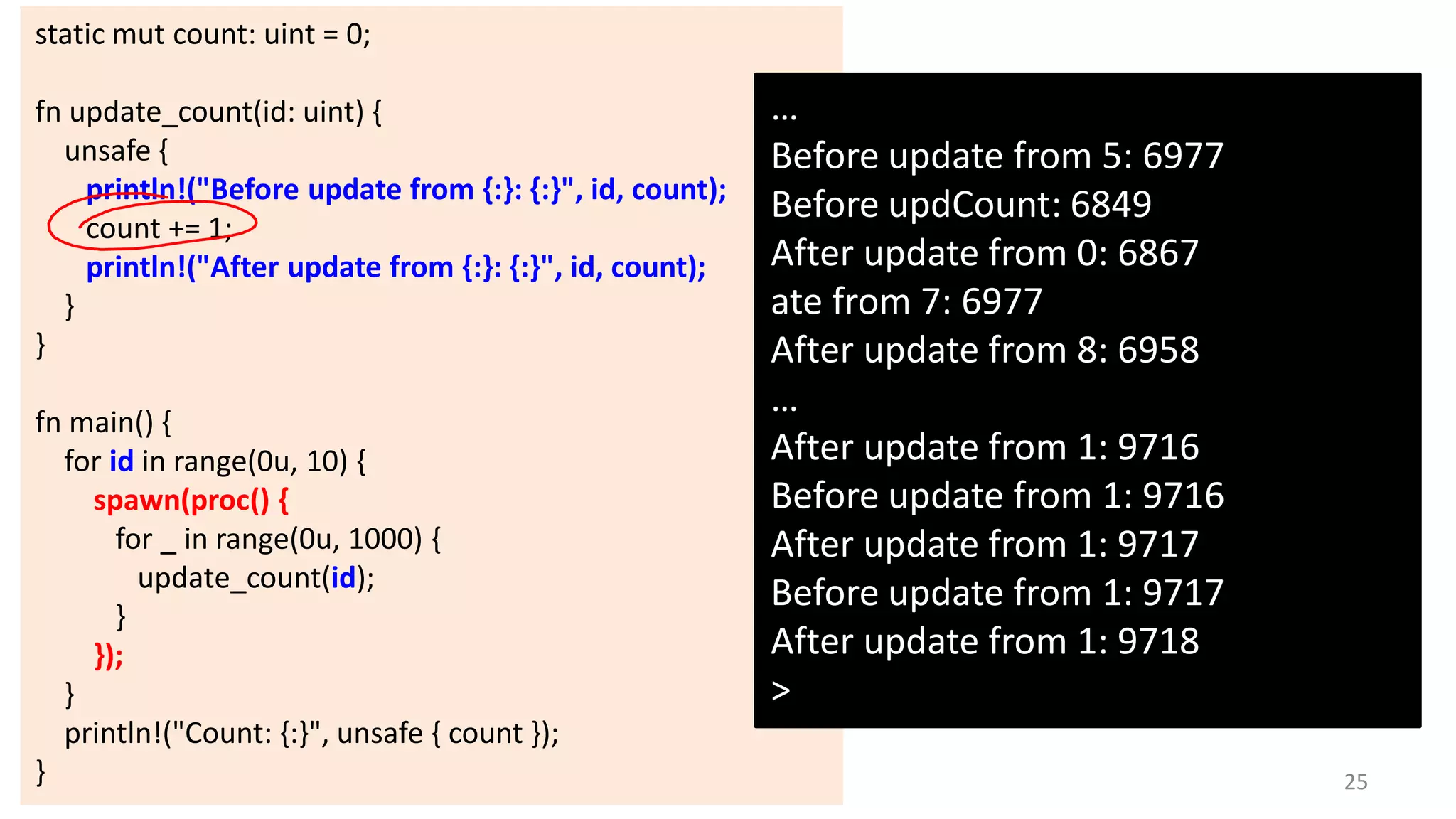
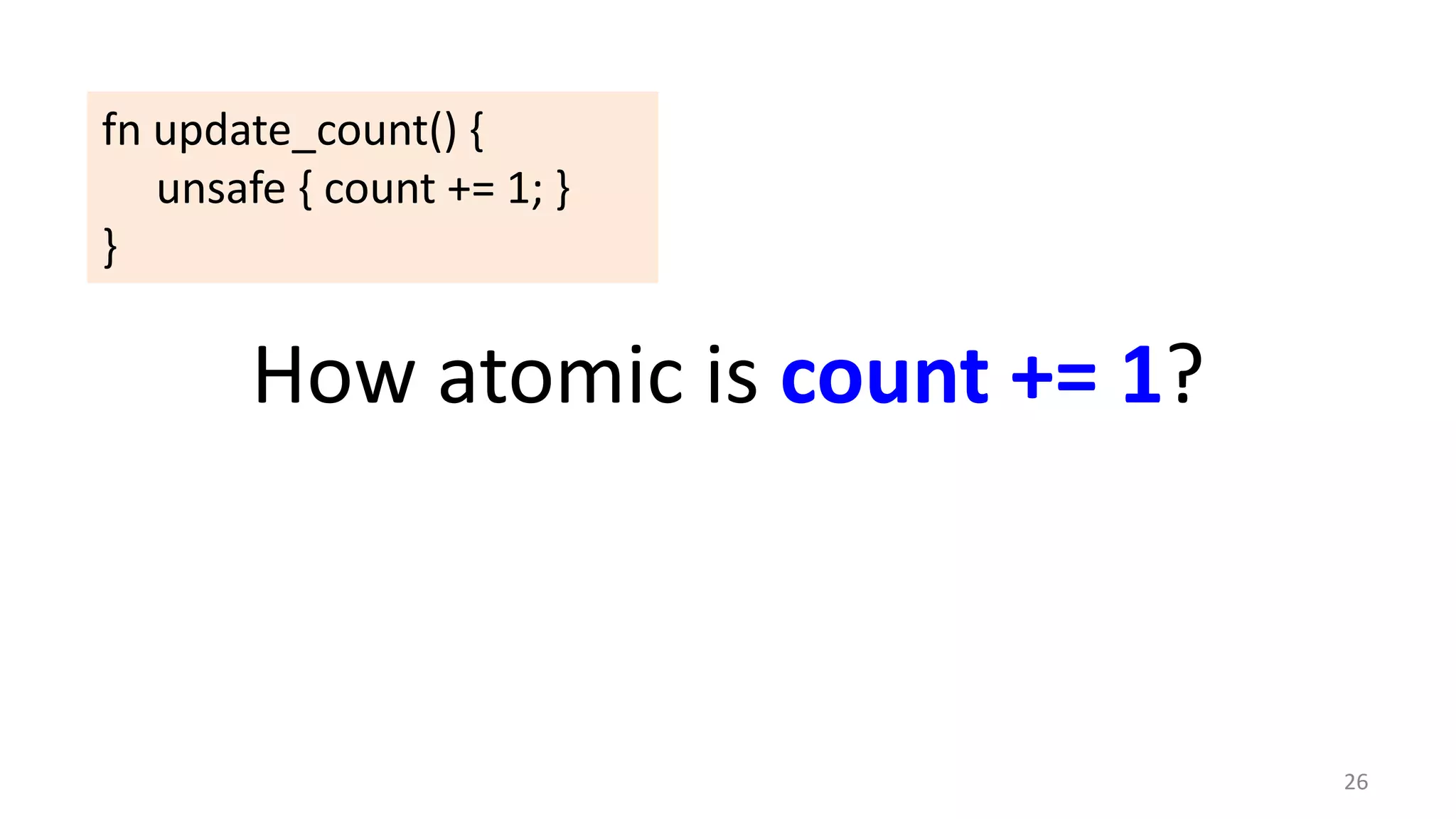
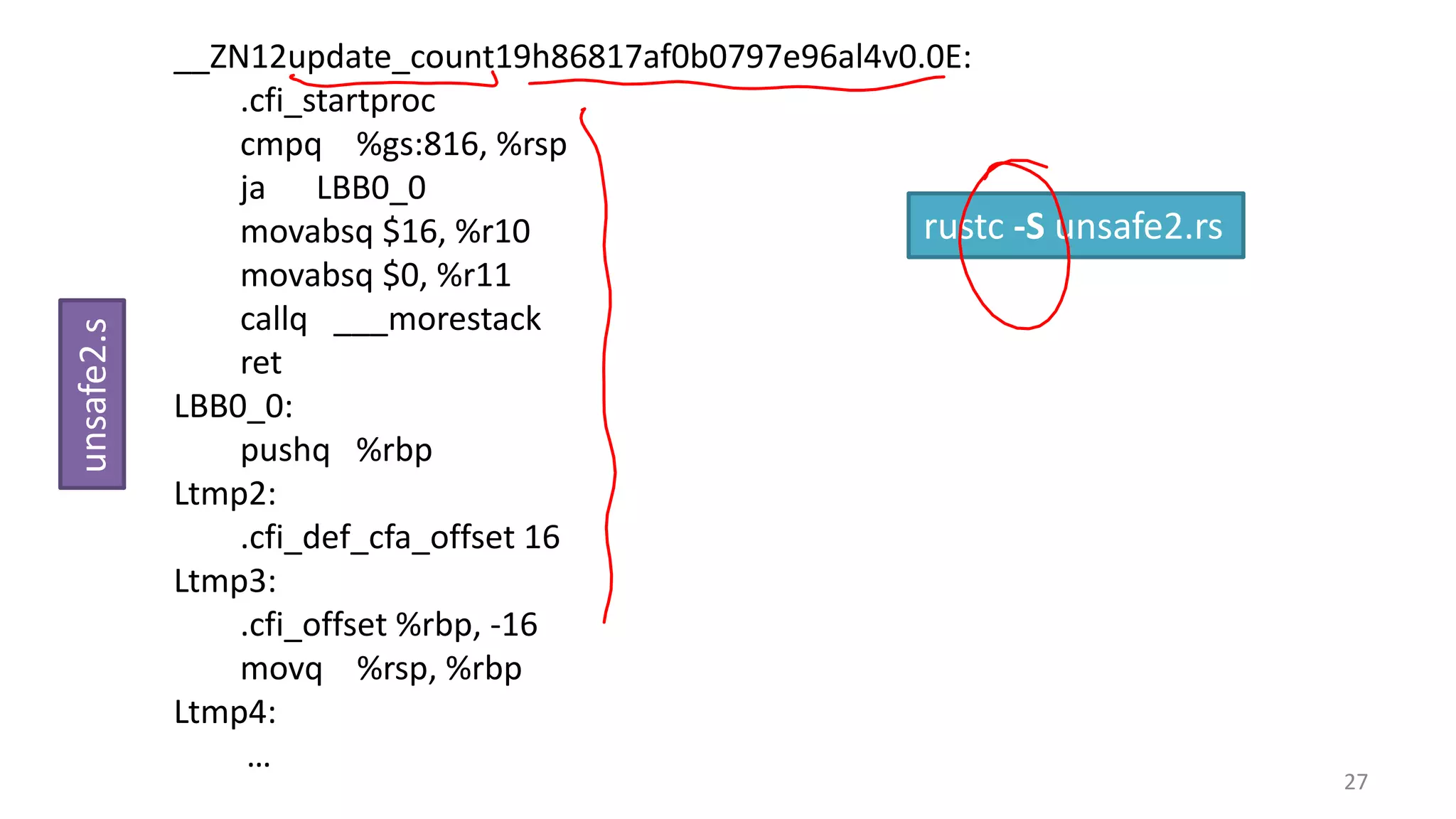
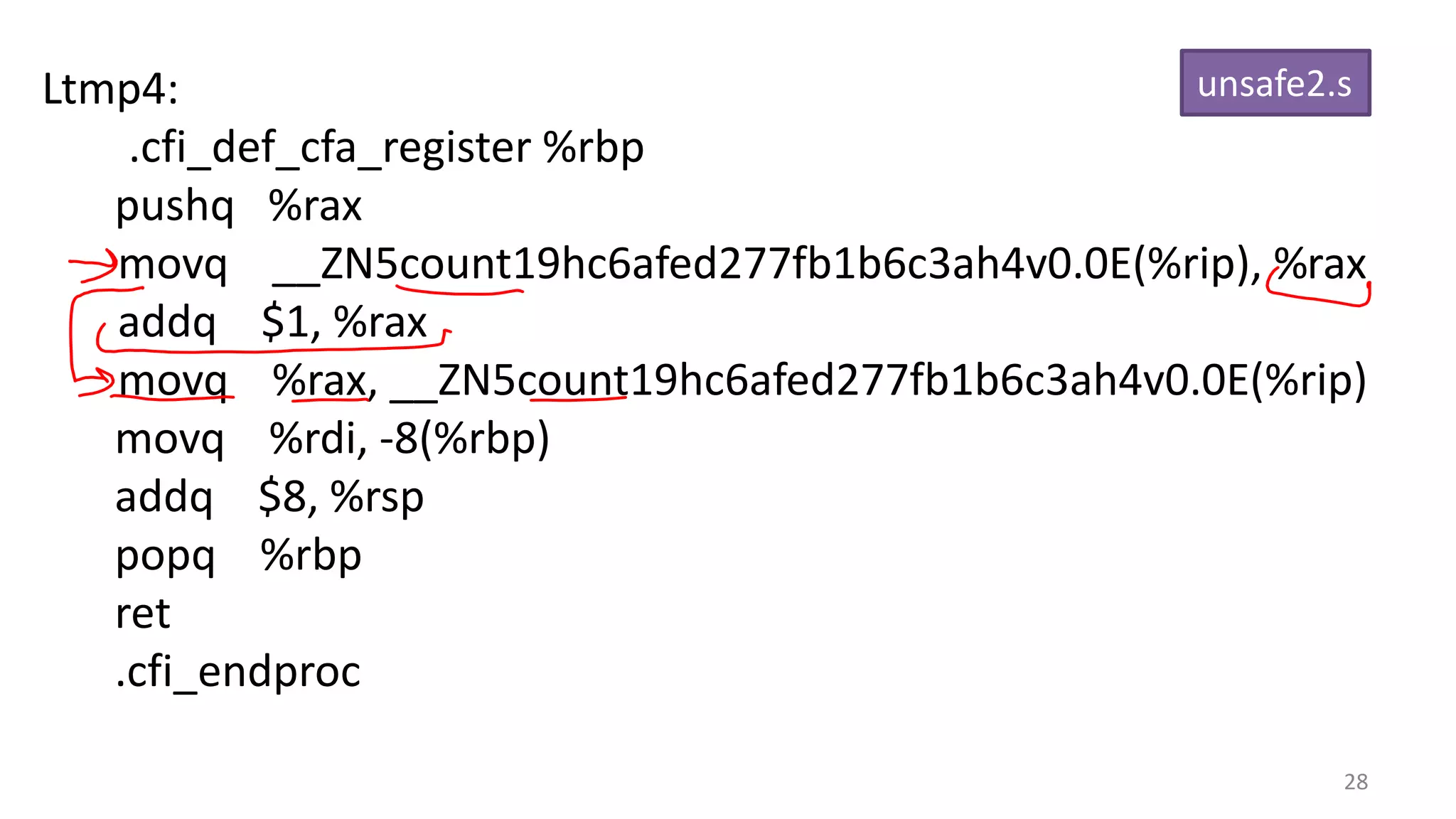
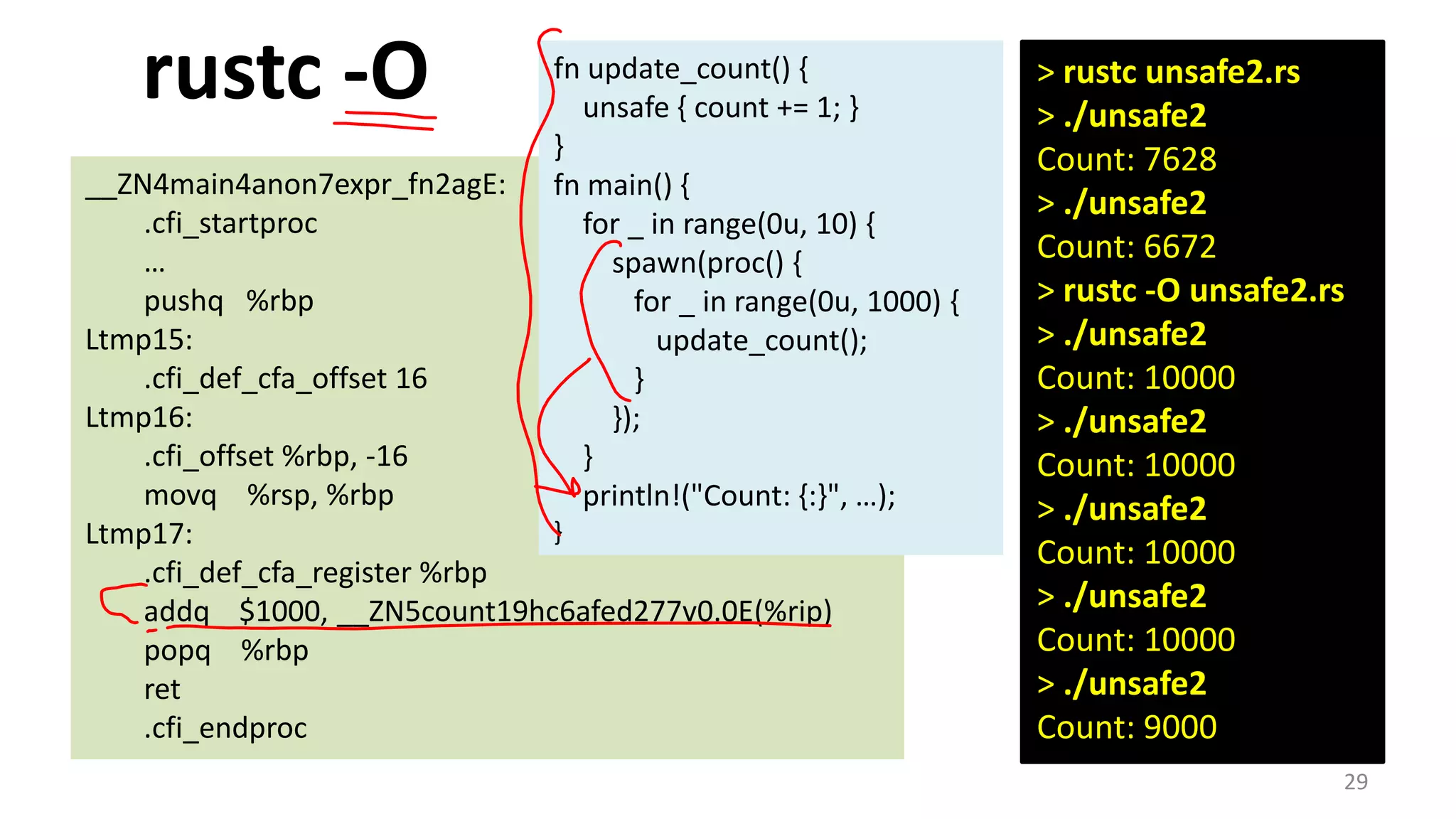
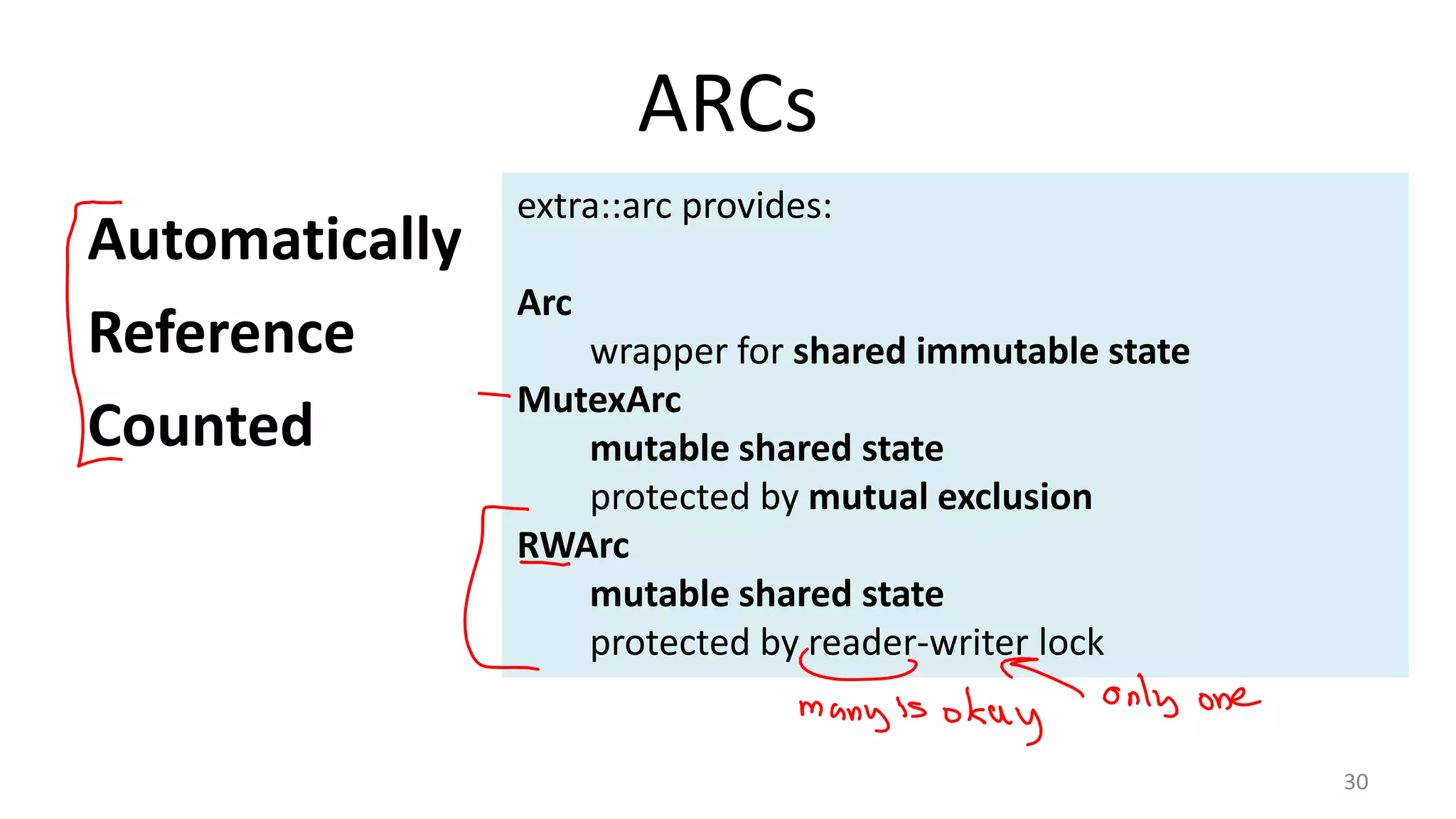
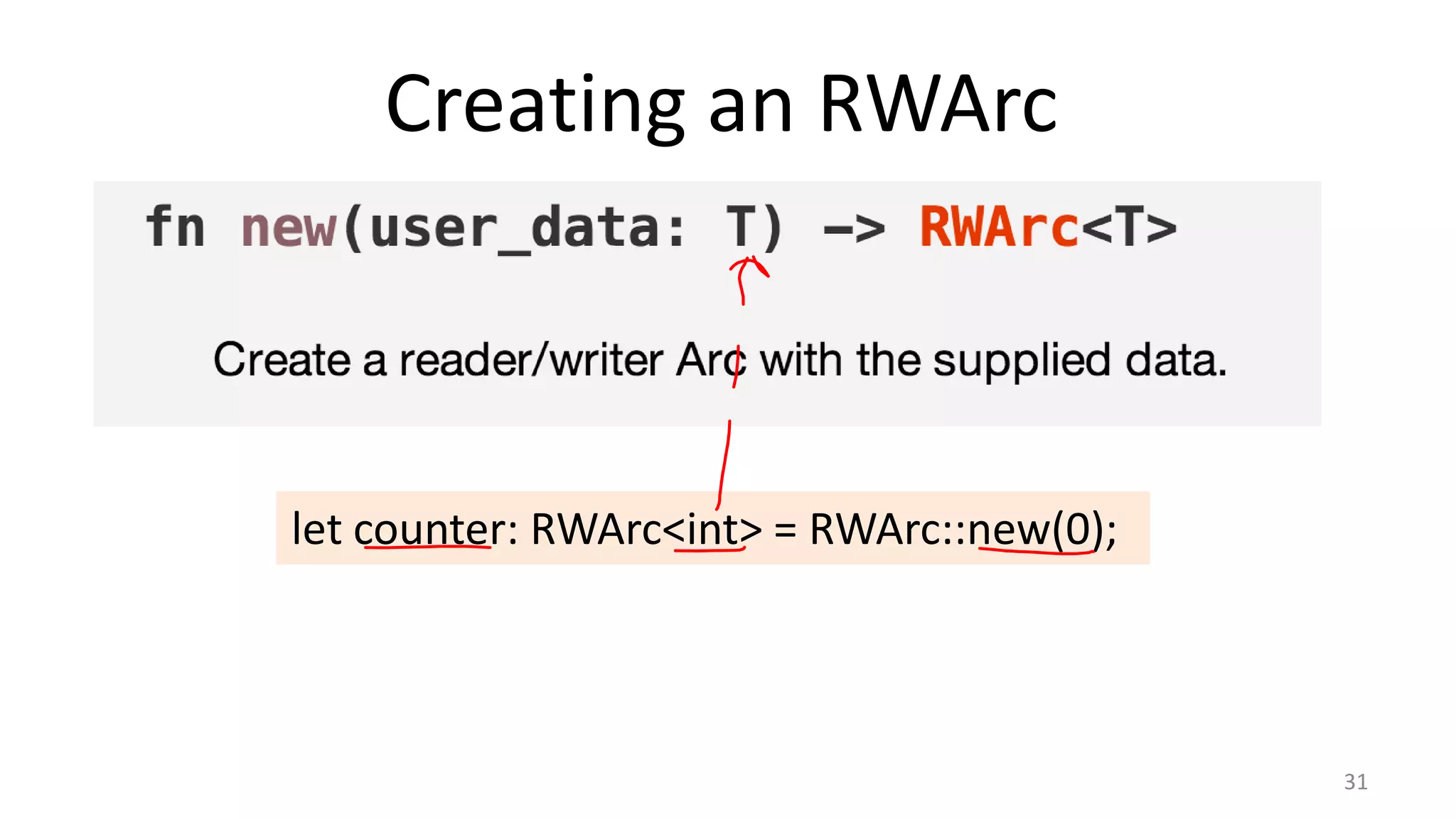
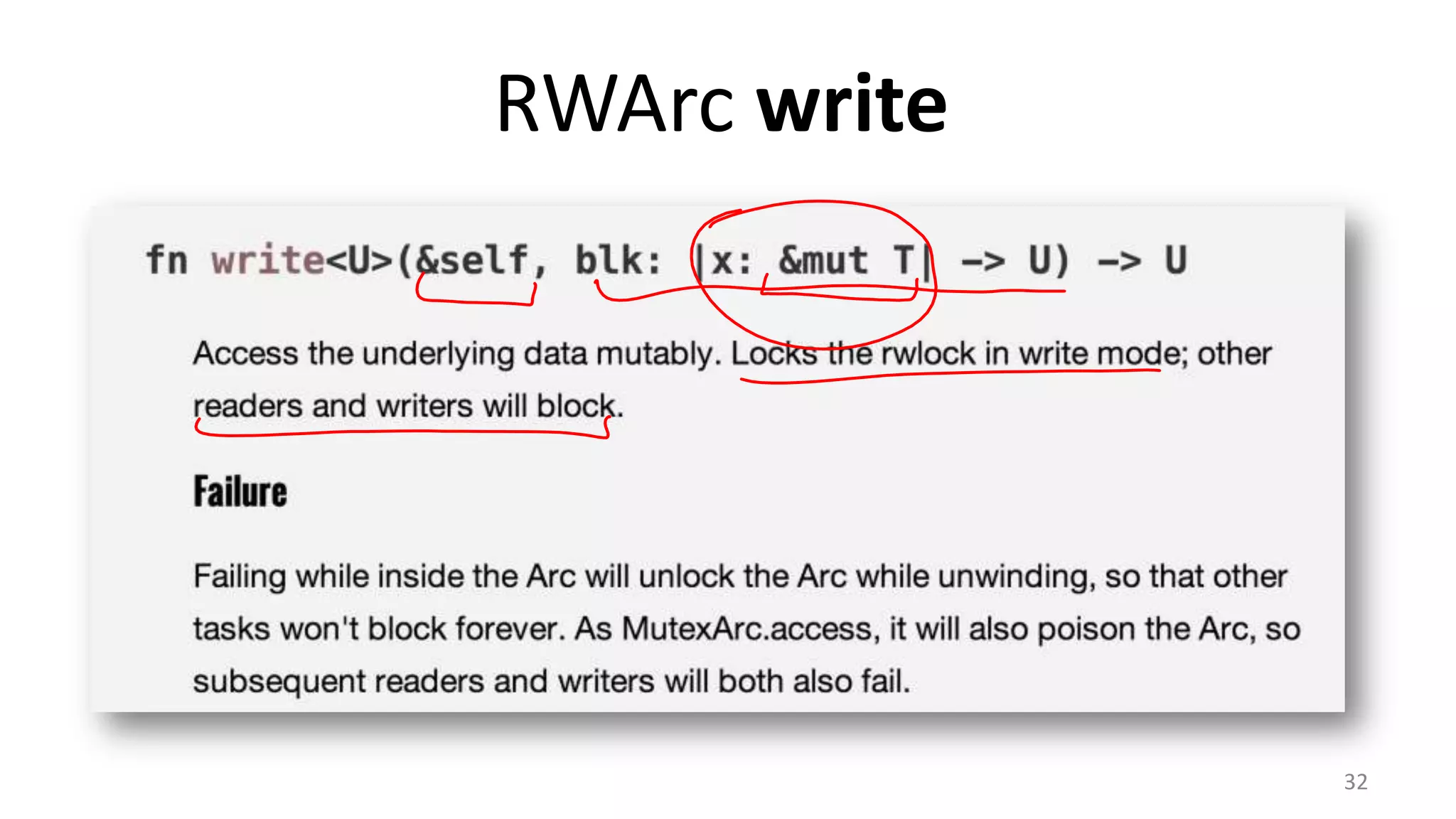
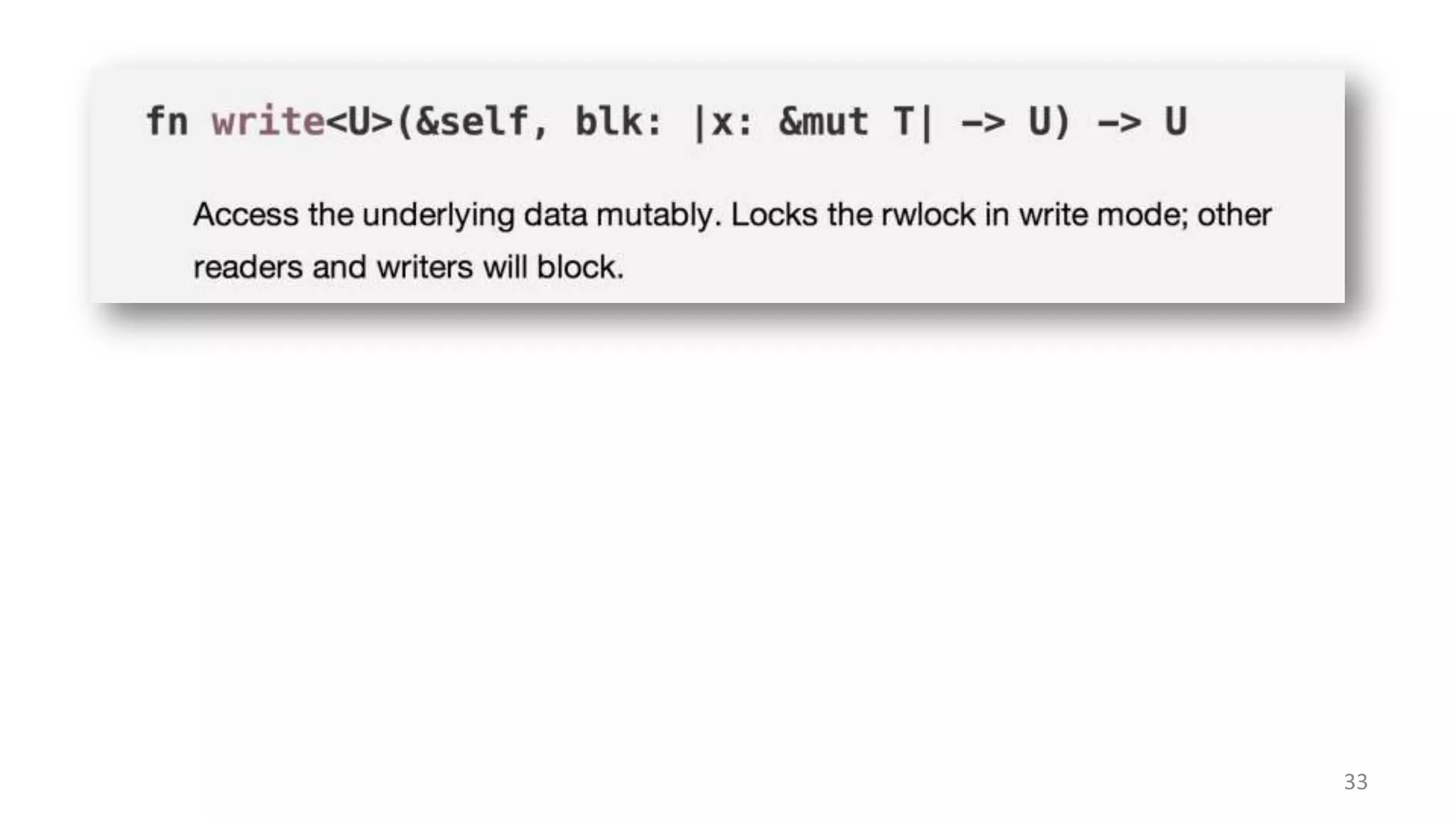
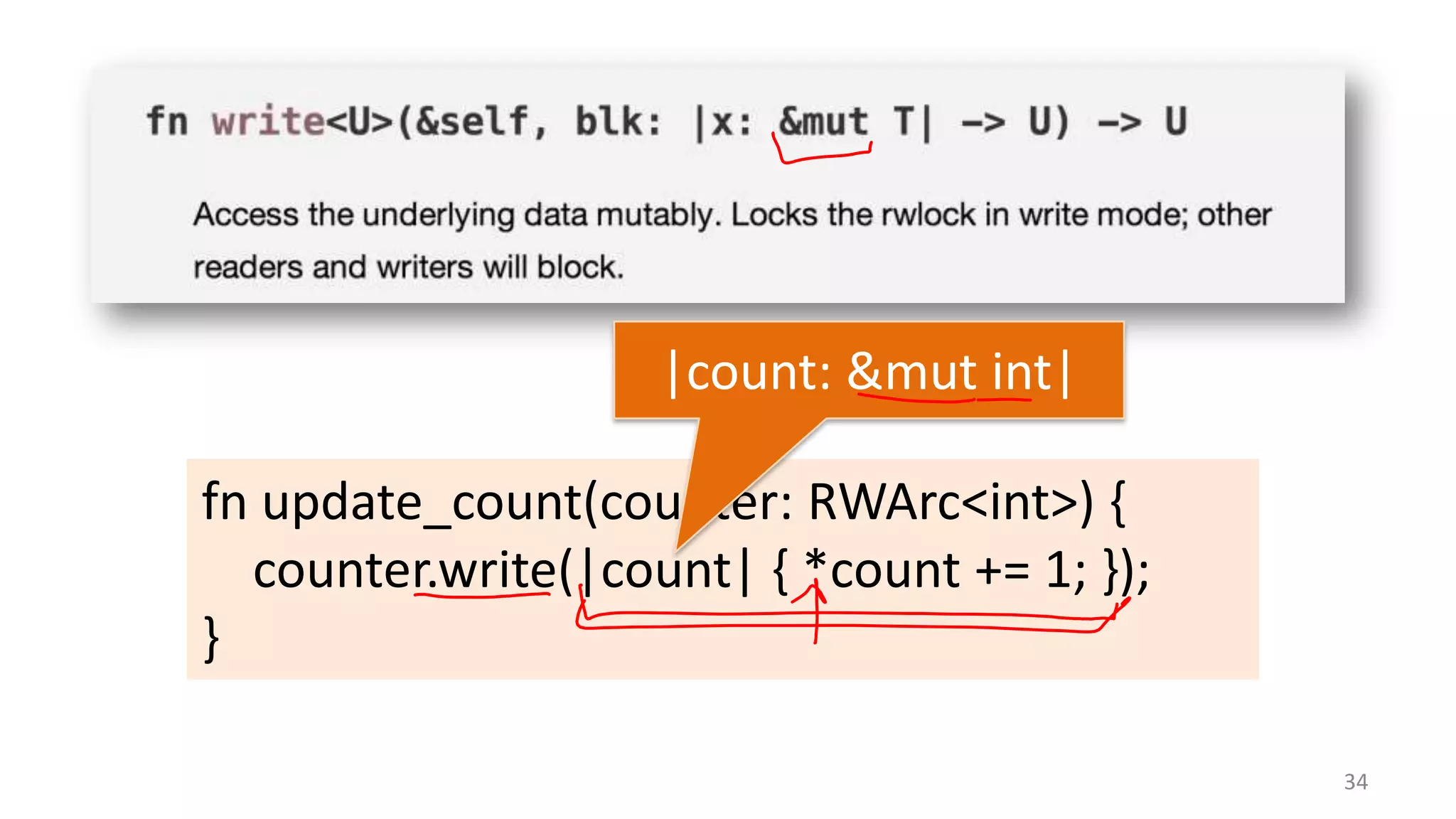
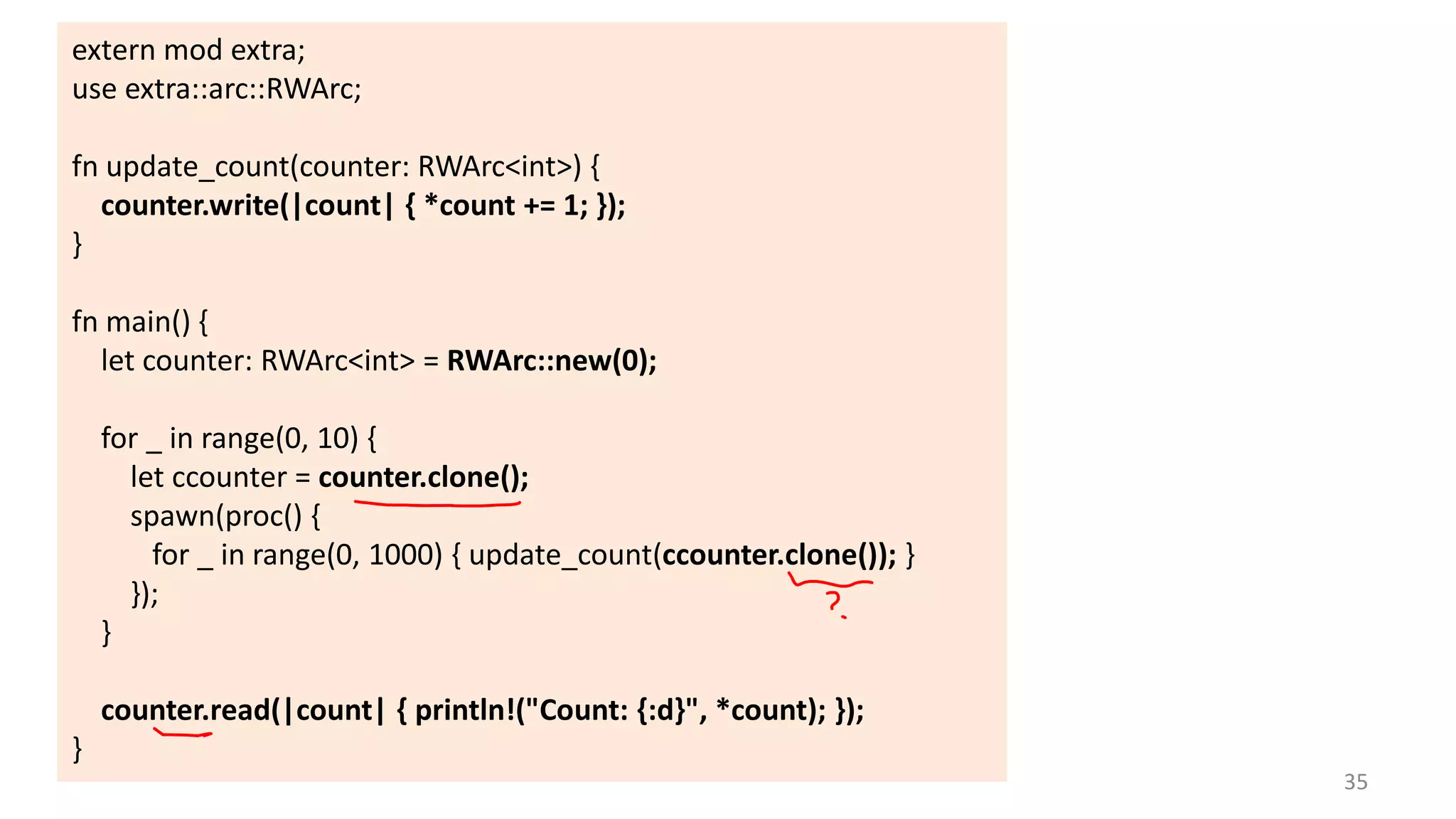
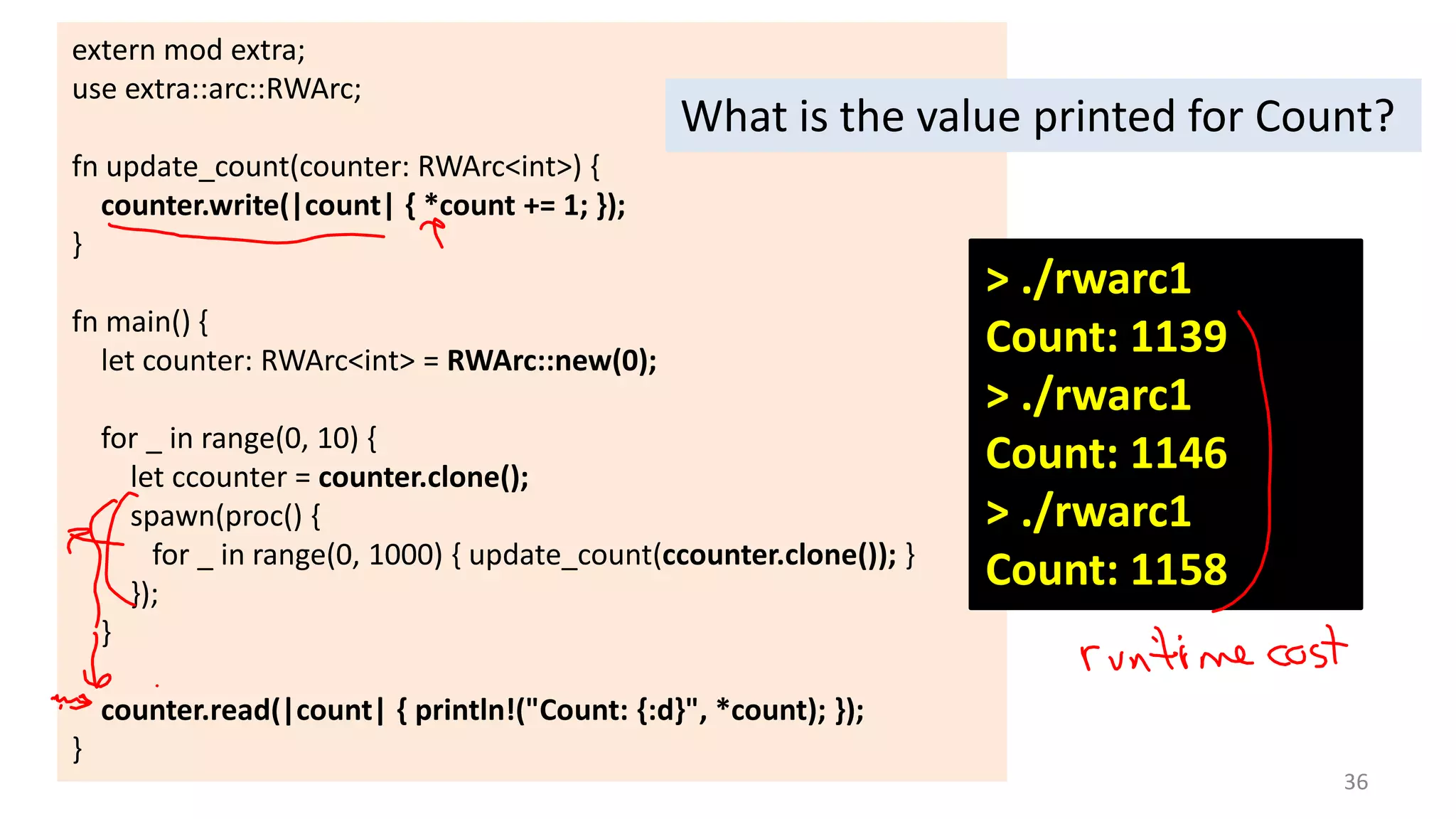
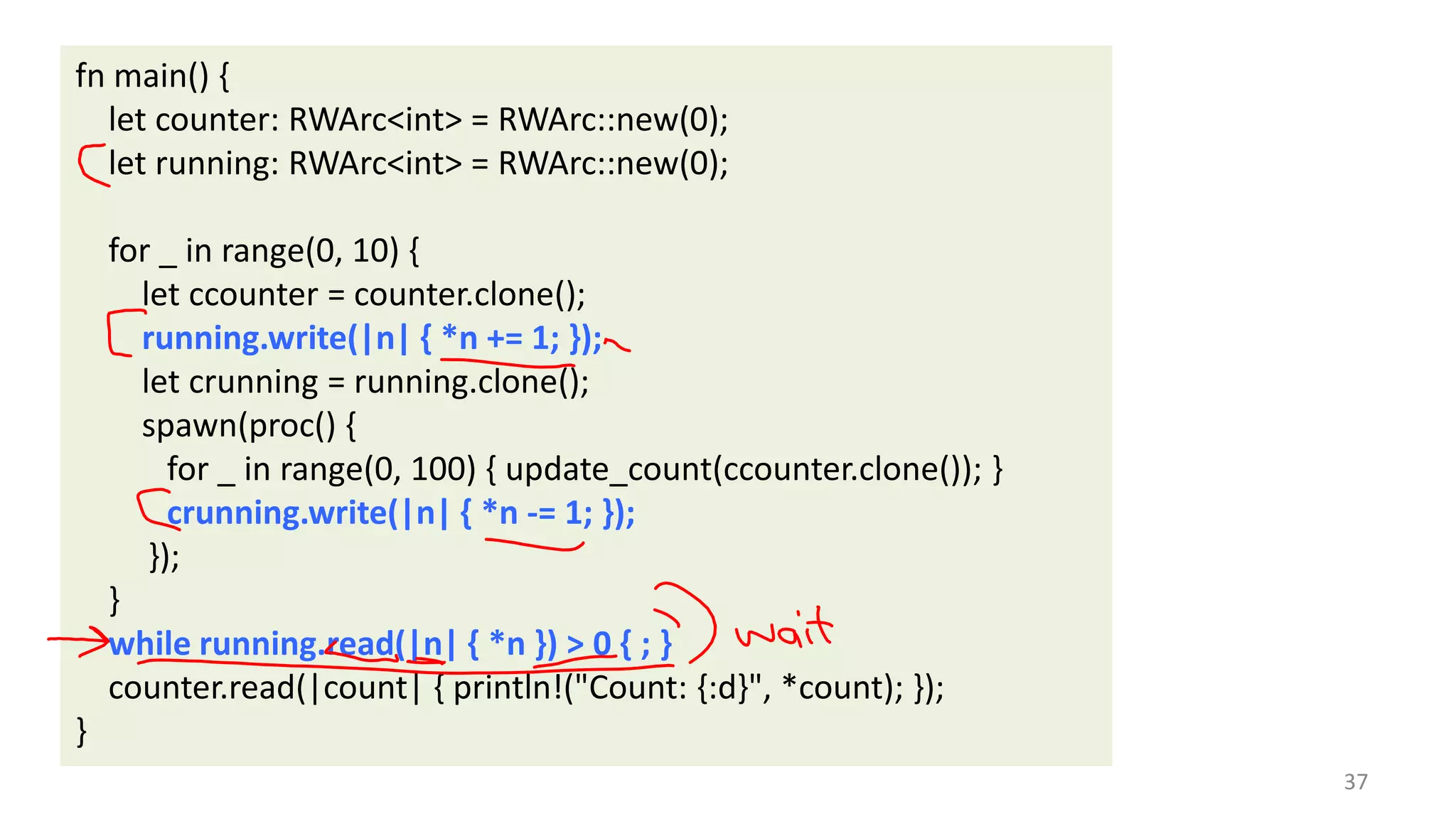
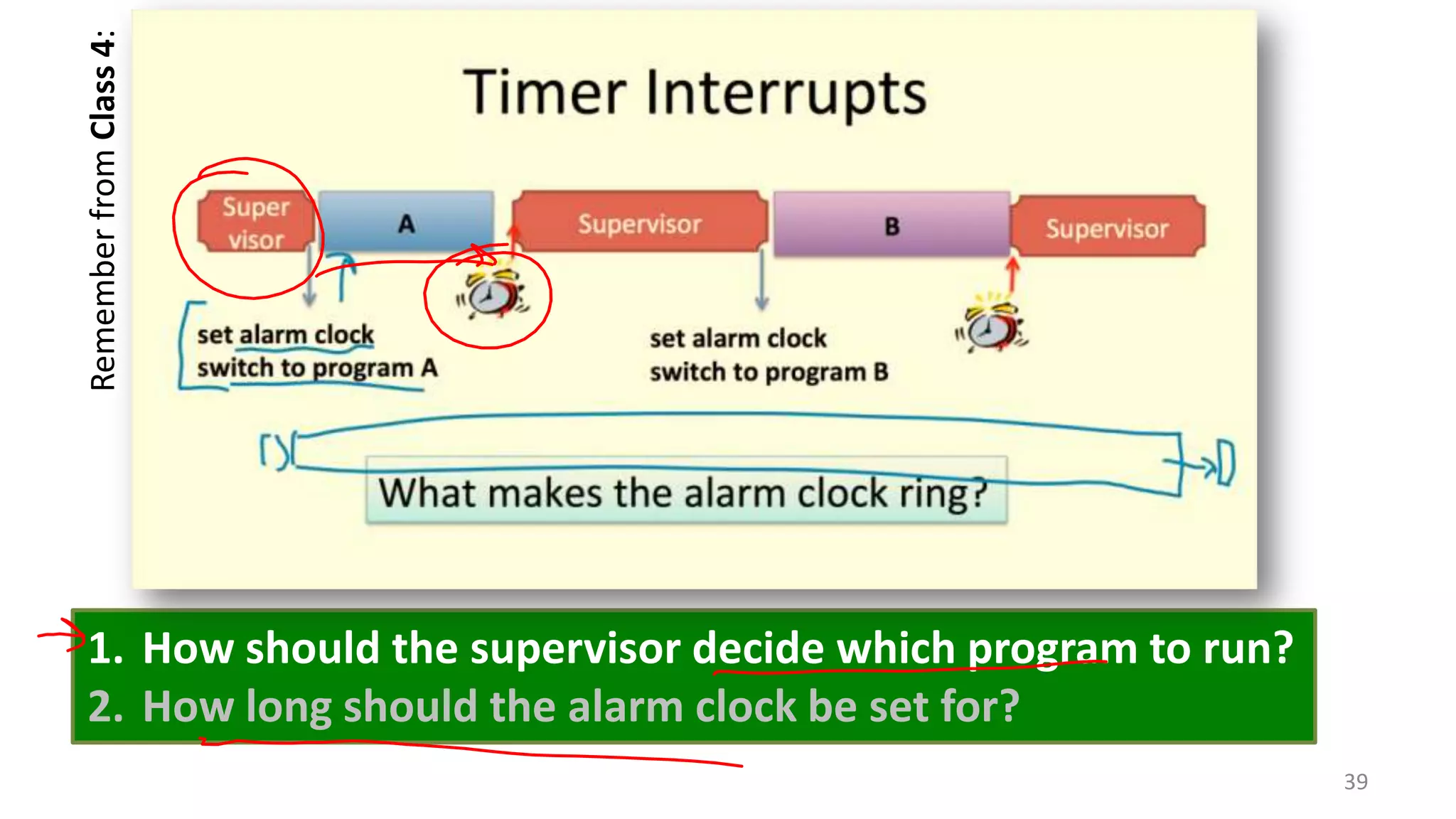
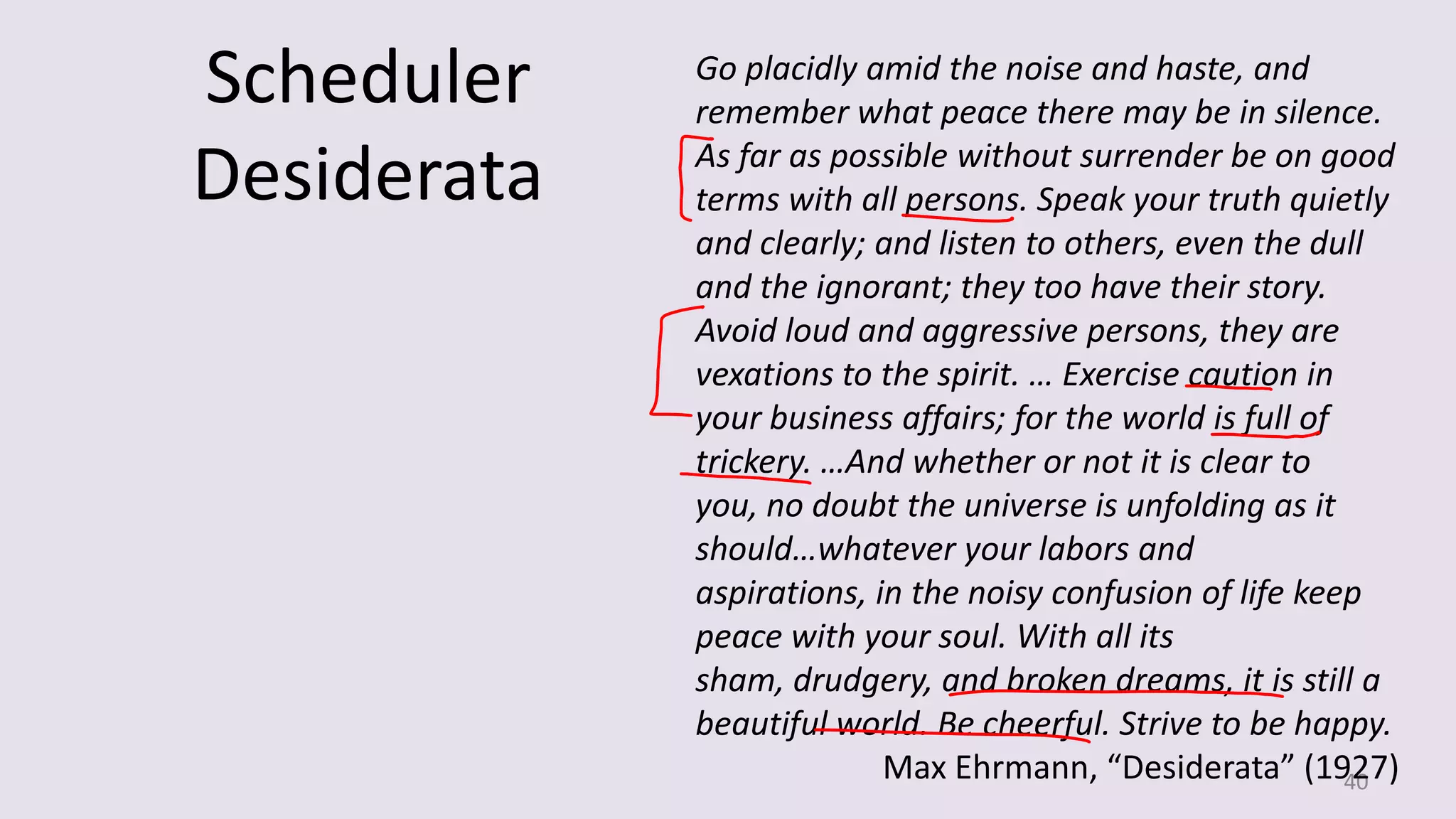
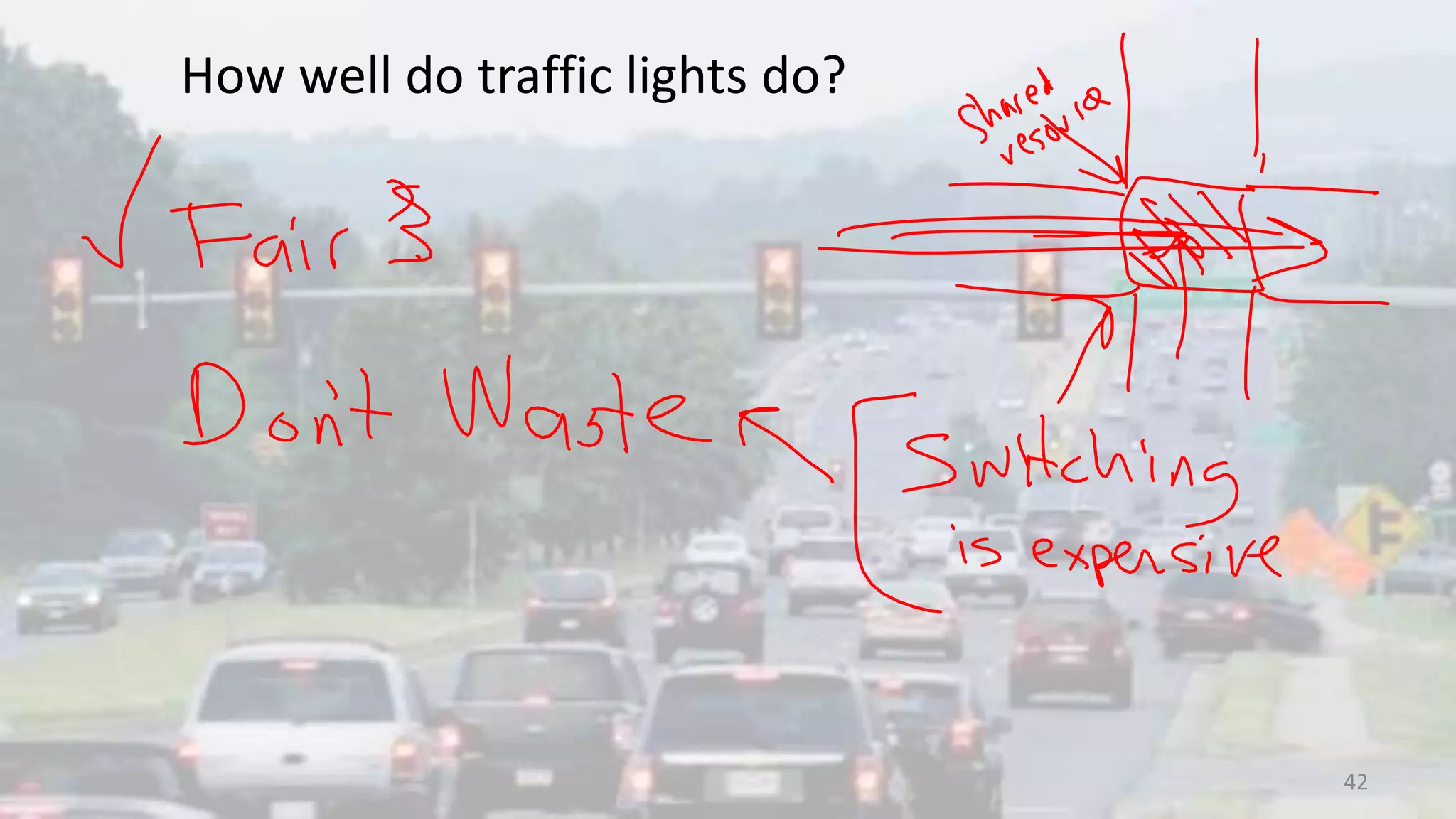
The document discusses the SSL/TLS handshake protocol, detailing the process involved in securing a channel and verifying server identities, as well as the potential implementation challenges. It also explores memory sharing in Rust programming through examples of unsafe code and threading, demonstrating how shared mutable state can lead to data races. Additionally, the document reflects on scheduling issues and includes various programming insights and thoughts on computer science concepts.
![SSL/TLS Handshake Protocol
Client
Verify Certificate
using KUCA
Hello
Server
KRCA[Server Identity, KUS]
Check identity
matches URL
Generate
random K
EKUS (K)
Secure channel using K
Decrypt
using
KRS
4](https://image.slidesharecdn.com/class10-inked-140227105904-phpapp02/75/SSL-Failing-Sharing-and-Scheduling-5-2048.jpg)
![SSL/TLS Handshake Protocol
Client
Verify Certificate
using KUCA
Check identity
matches URL
Generate
random K
Hello
Server
KRCA[Server Identity, KUS]
How did client get KUCA?
EKUS (K)
Secure channel using K
Decrypt
using
KRS
5](https://image.slidesharecdn.com/class10-inked-140227105904-phpapp02/75/SSL-Failing-Sharing-and-Scheduling-6-2048.jpg)
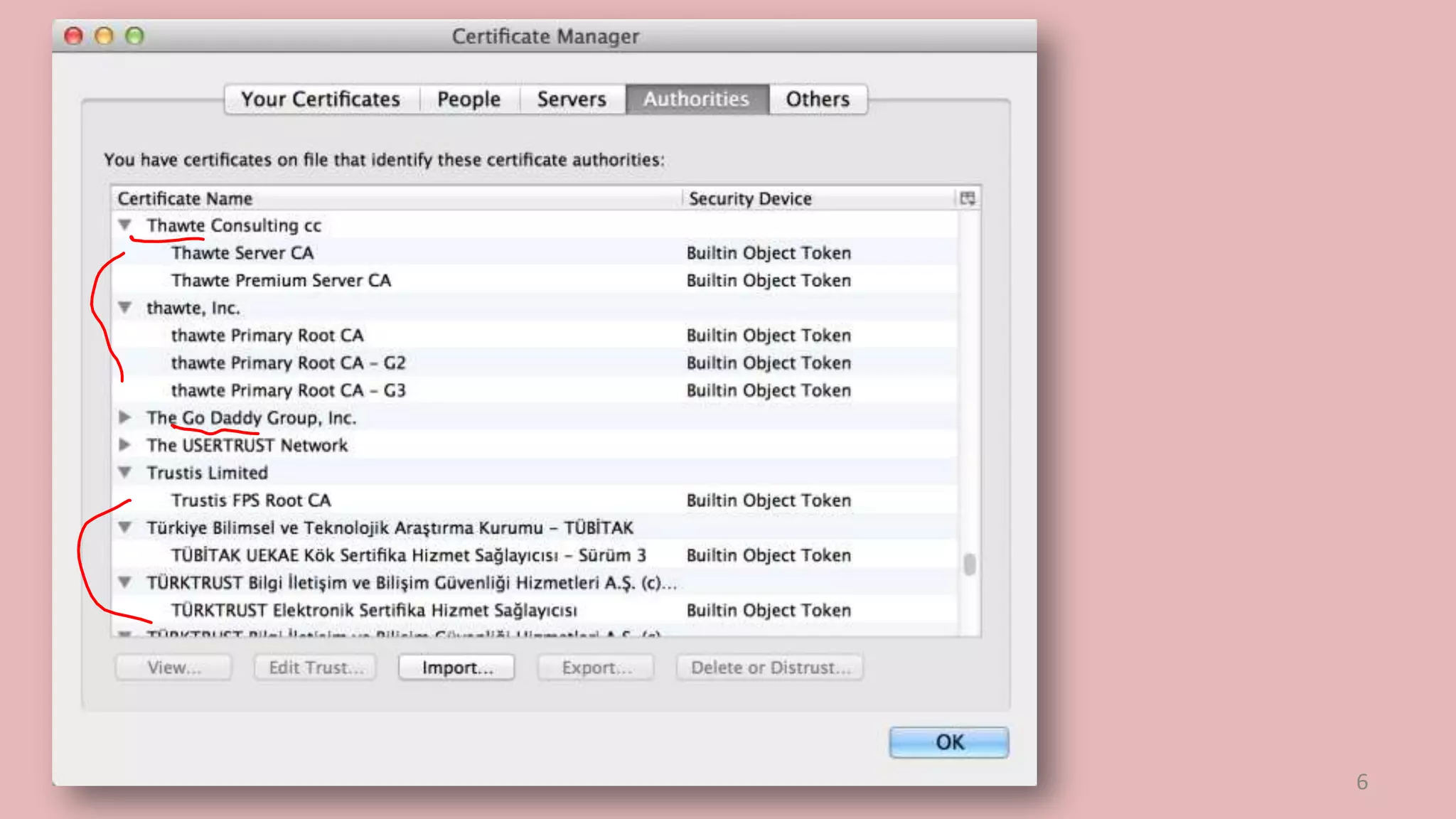
![SSL/TLS Handshake Protocol
Client
Verify Certificate
using KUCA
Hello
Server
KRCA[Server Identity, KUS]
Check identity
matches URL
Generate
random K
EKUS (K)
Secure channel using K
Decrypt
using
KRS
7](https://image.slidesharecdn.com/class10-inked-140227105904-phpapp02/75/SSL-Failing-Sharing-and-Scheduling-8-2048.jpg)
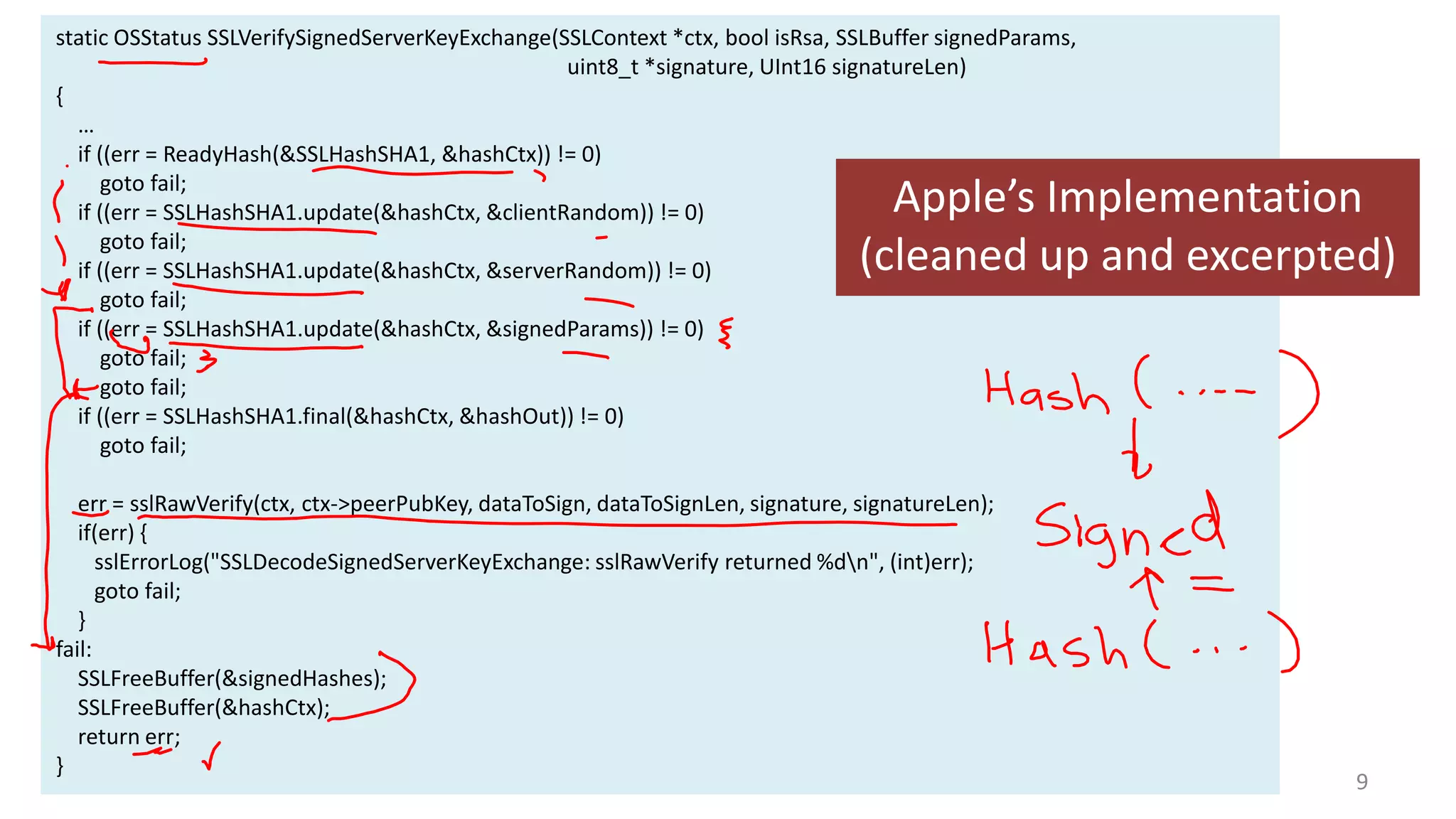
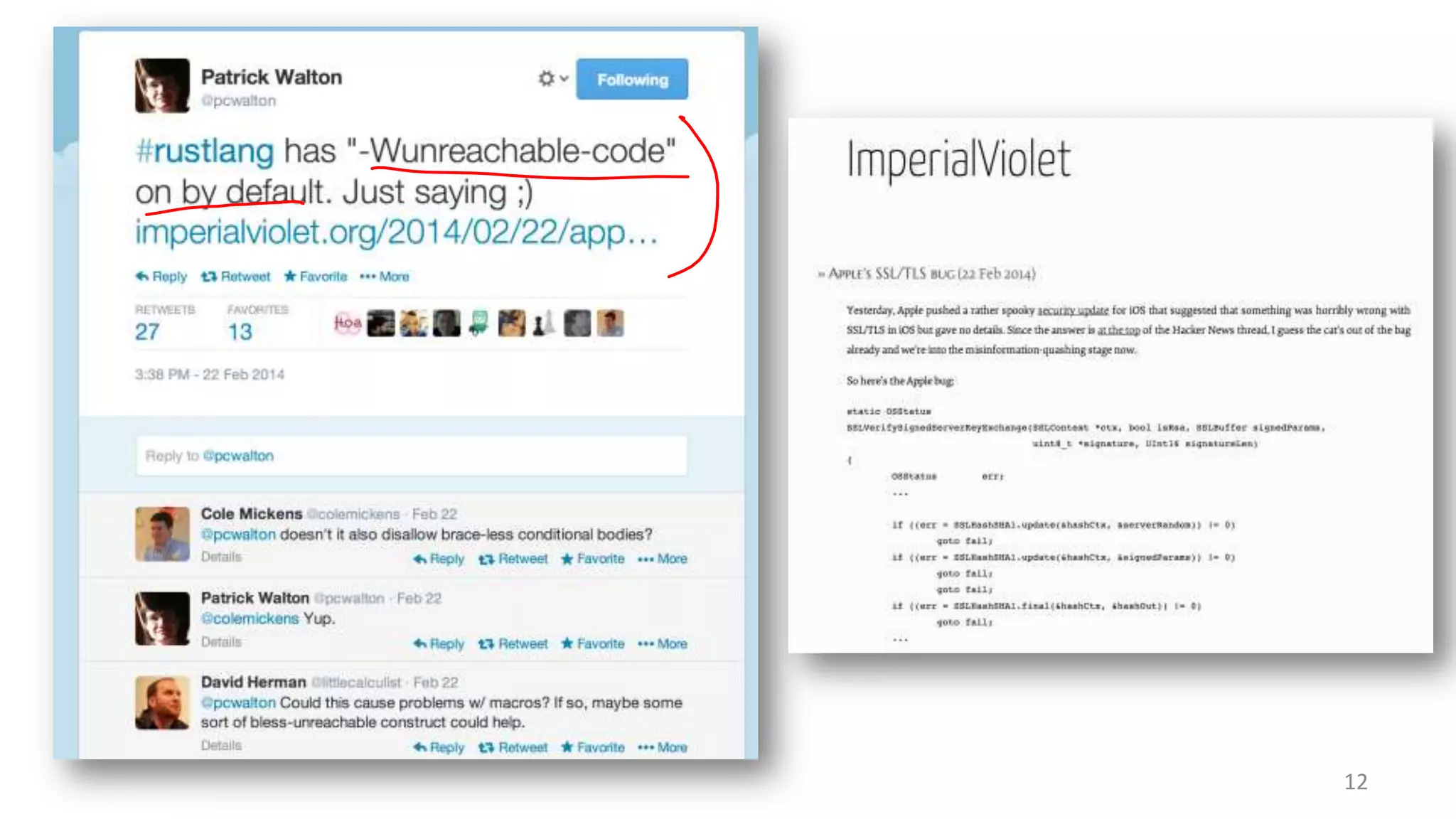
![static OSStatus
SSLVerifySignedServerKeyExchange(SSLContext *ctx, bool isRsa, SSLBuffer signedParams,
uint8_t *signature, UInt16 signatureLen)
{
OSStatus
err;
SSLBuffer
hashOut, hashCtx, clientRandom, serverRandom;
uint8_t
hashes[SSL_SHA1_DIGEST_LEN + SSL_MD5_DIGEST_LEN];
SSLBuffer
signedHashes;
uint8_t
*dataToSign;
size_t
dataToSignLen;
signedHashes.data = 0;
hashCtx.data = 0;
Apple’s
Implementation
clientRandom.data = ctx->clientRandom;
clientRandom.length = SSL_CLIENT_SRVR_RAND_SIZE;
serverRandom.data = ctx->serverRandom;
serverRandom.length = SSL_CLIENT_SRVR_RAND_SIZE;
…
hashOut.data = hashes + SSL_MD5_DIGEST_LEN;
hashOut.length = SSL_SHA1_DIGEST_LEN;
if ((err = SSLFreeBuffer(&hashCtx)) != 0)
goto fail;
[Link]
8](https://image.slidesharecdn.com/class10-inked-140227105904-phpapp02/75/SSL-Failing-Sharing-and-Scheduling-9-2048.jpg)








![dori-mic.org
“If only I had this book when I was
a young student, I might have
done something useful with my
life like discover a new complexity
class instead of dropping out and
wasting my life flipping
pancakes, playing with basic
blocks, and eradicating polo.”
Gill Bates,
Founder of Mic-Soft Corporation
MiniLEGO [FJNNO 2013]](https://image.slidesharecdn.com/class10-inked-140227105904-phpapp02/75/SSL-Failing-Sharing-and-Scheduling-44-2048.jpg)