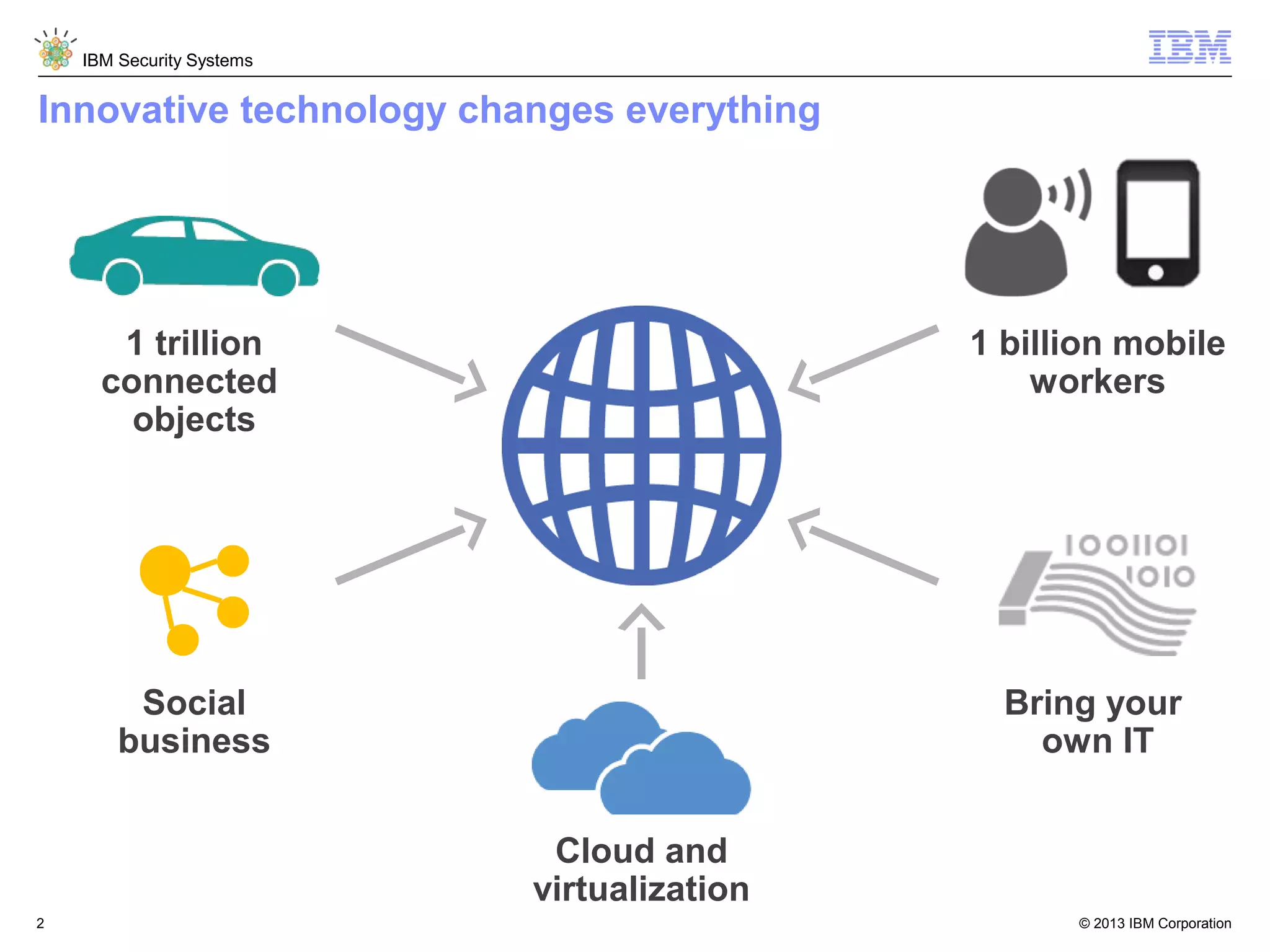
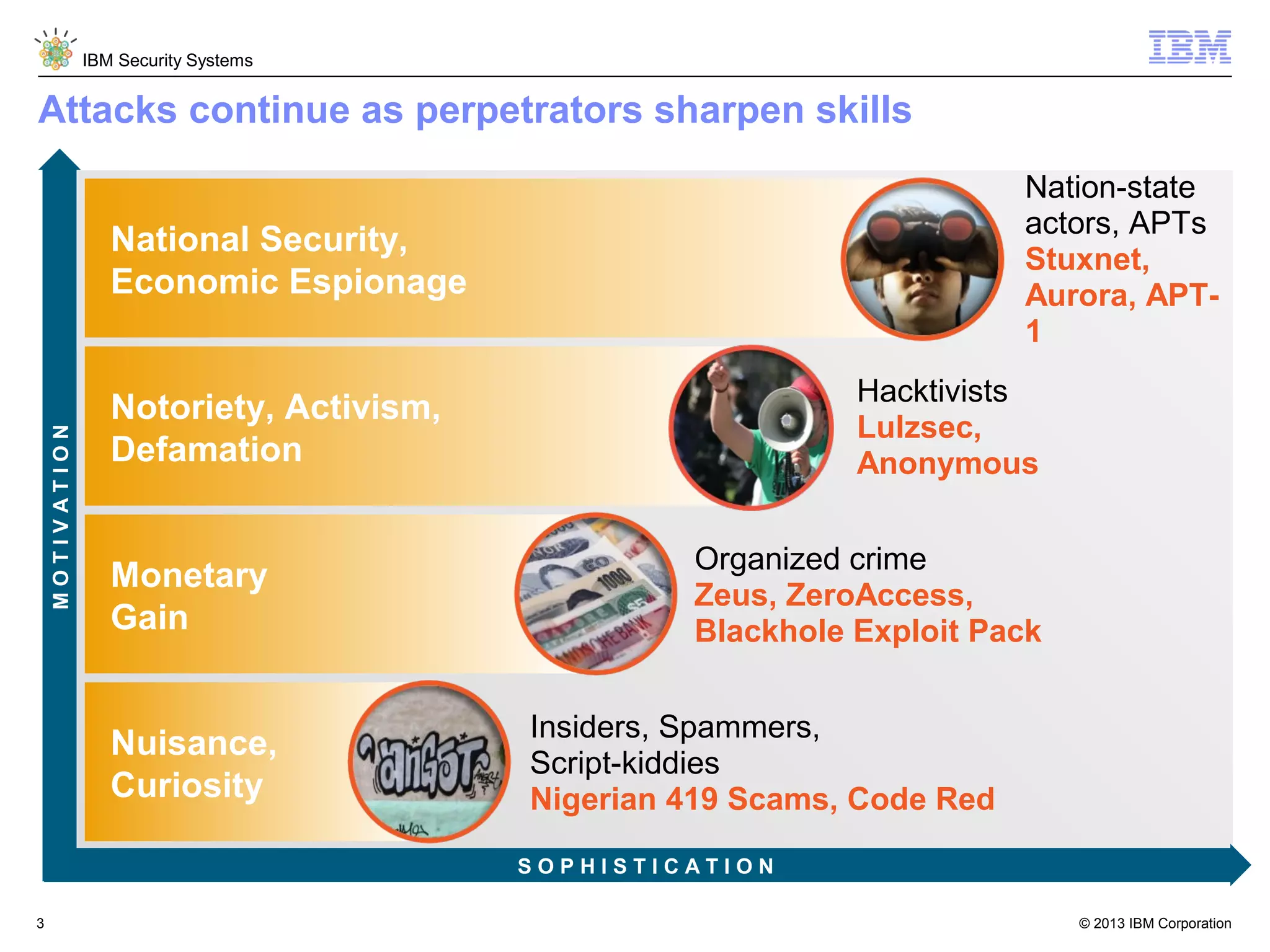
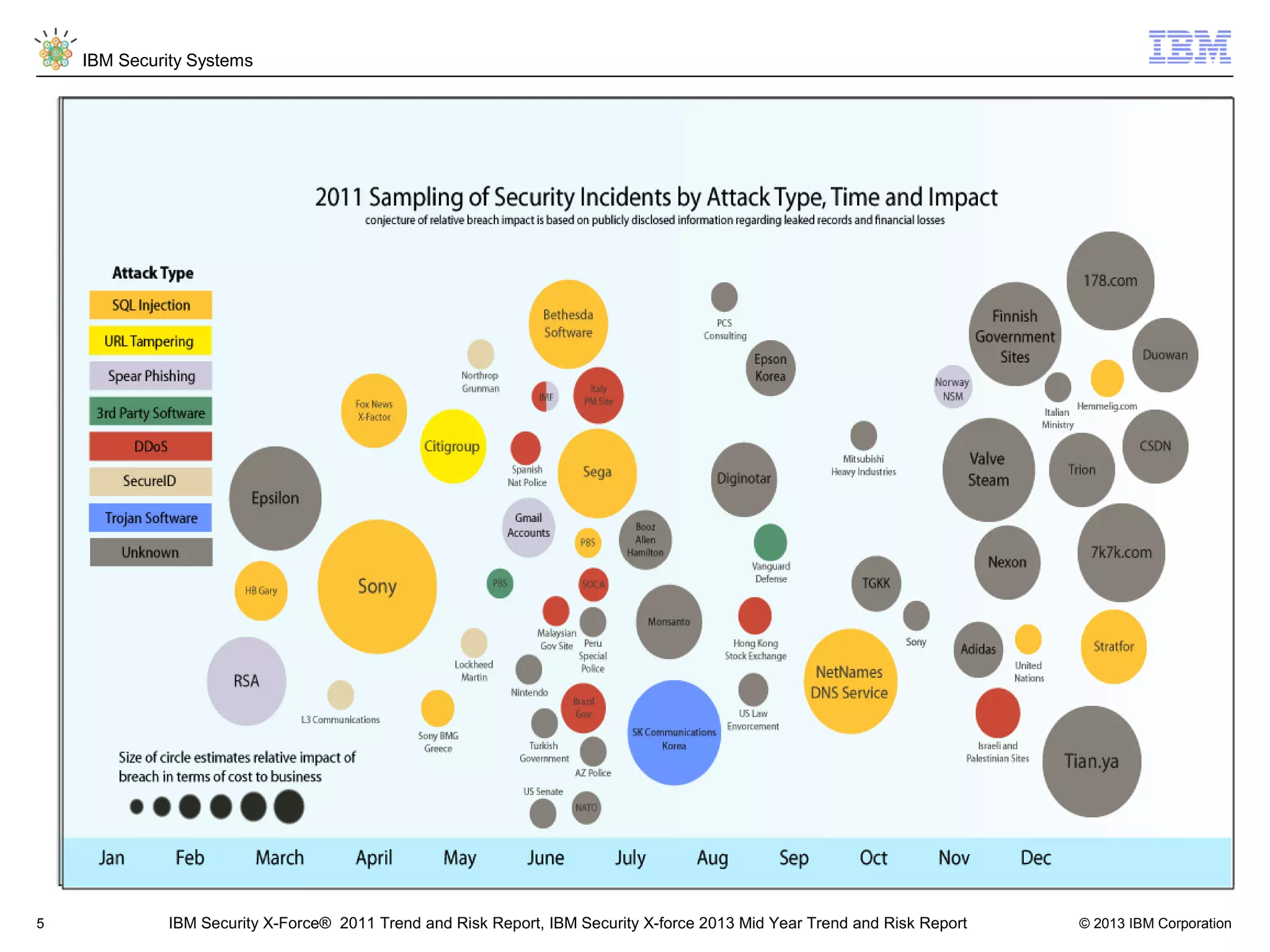
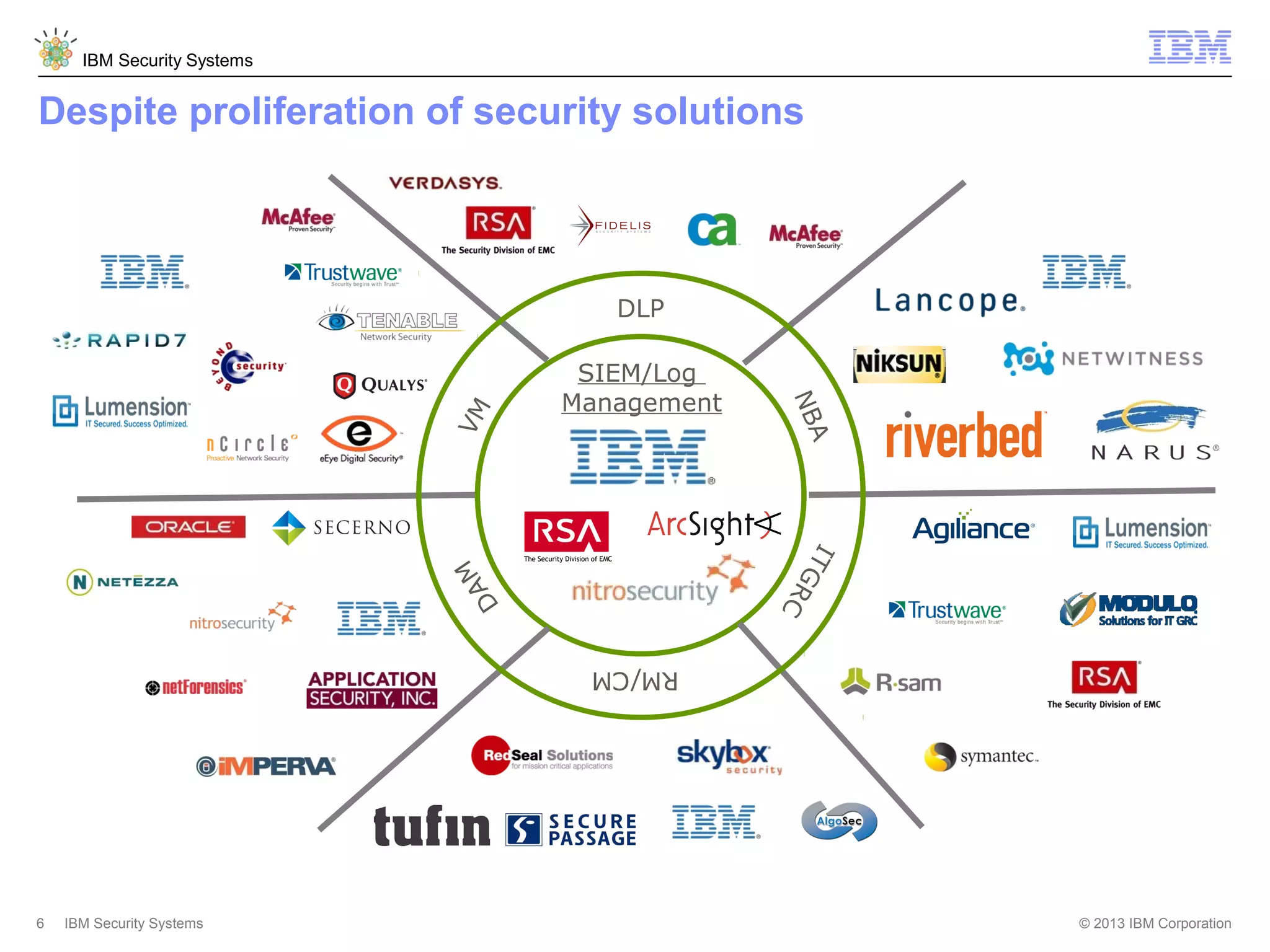
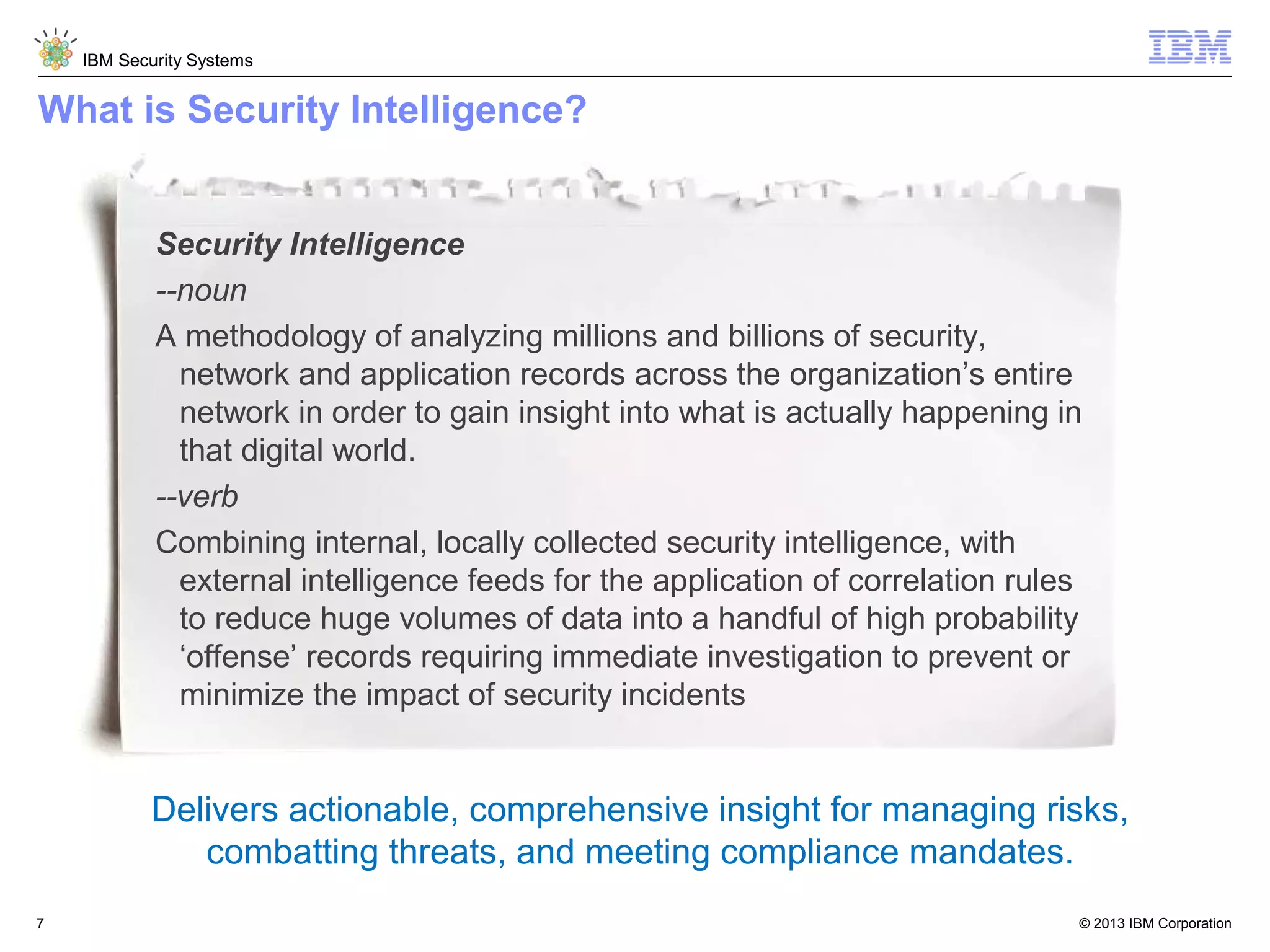
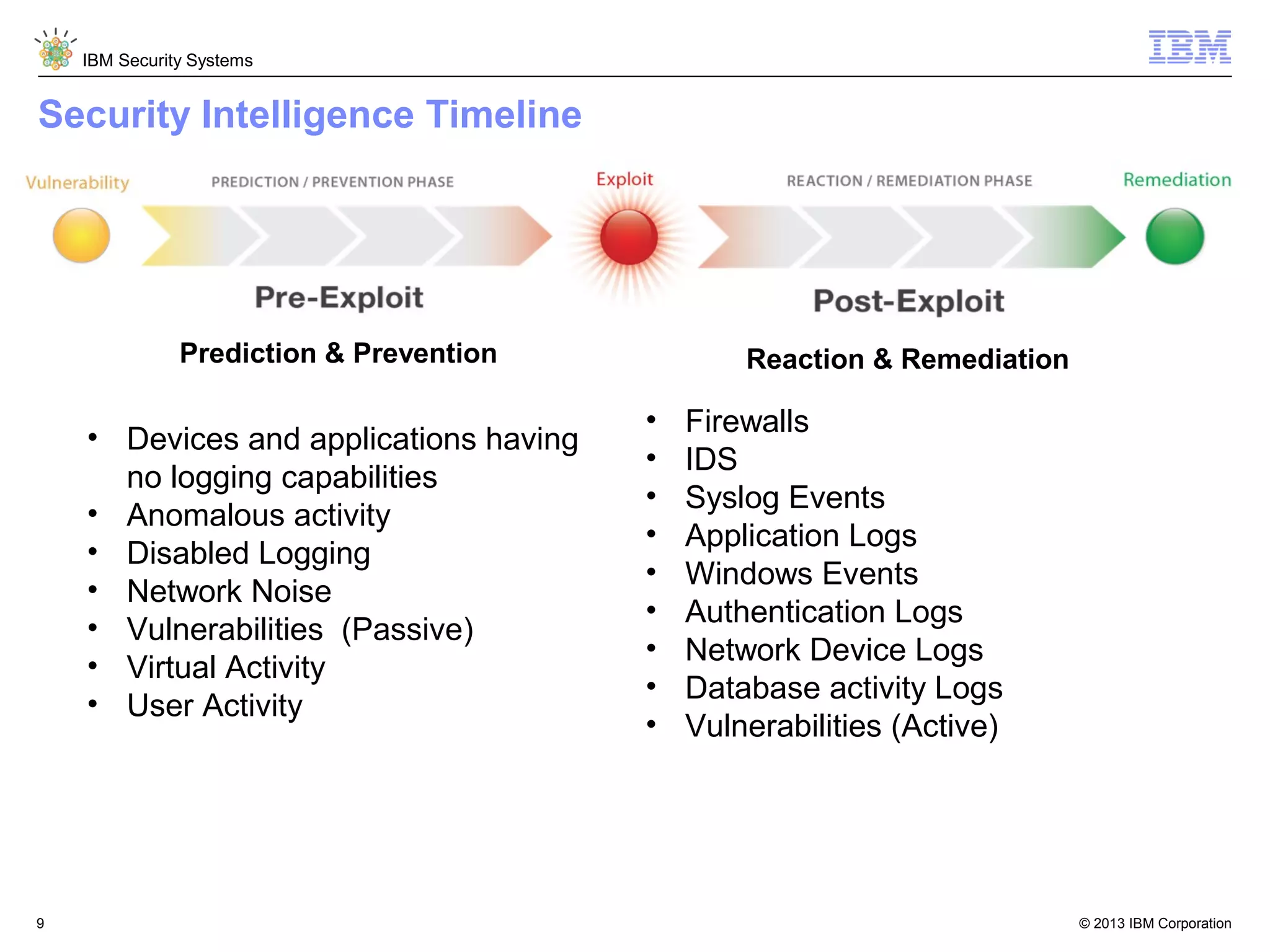
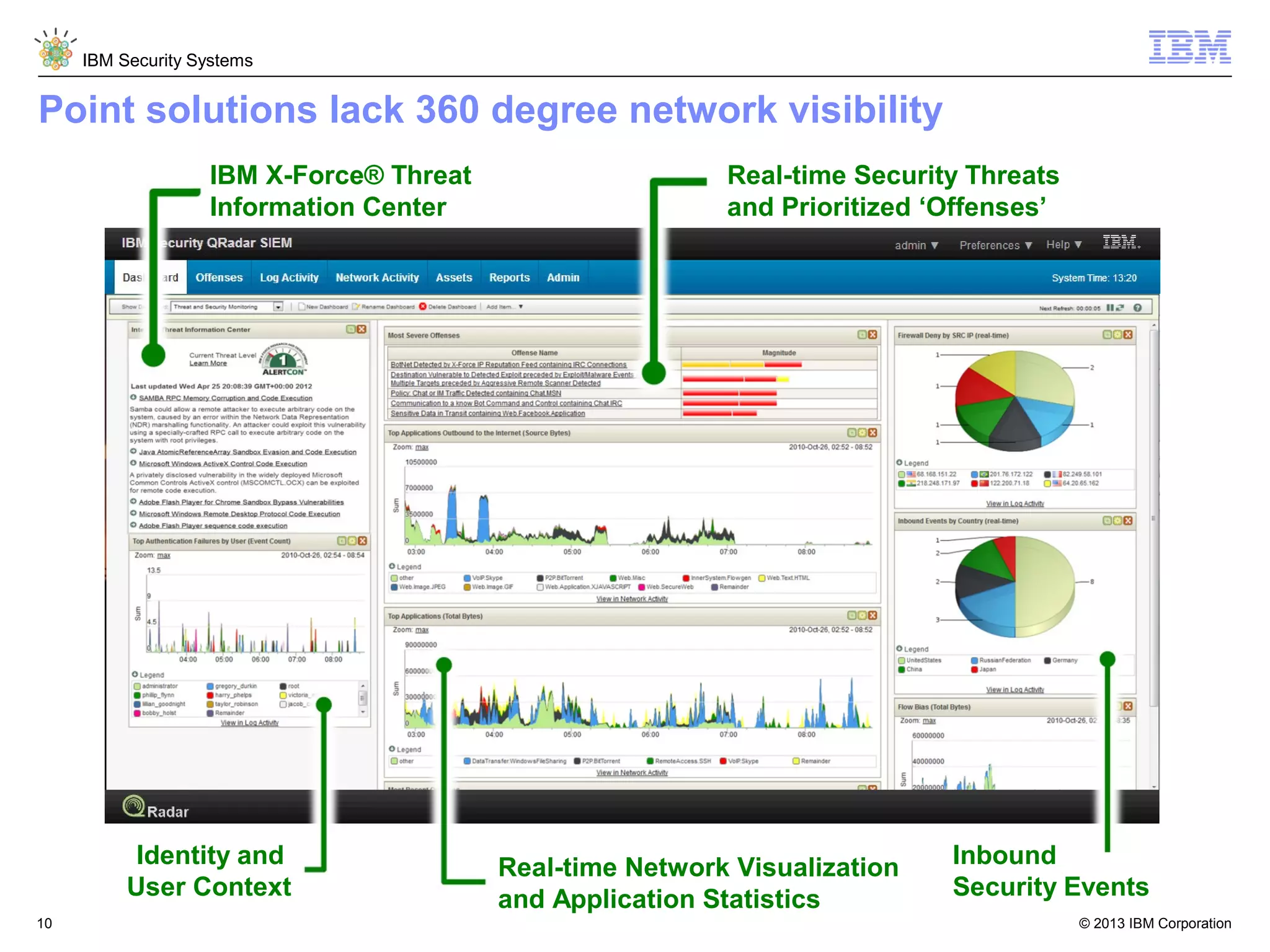
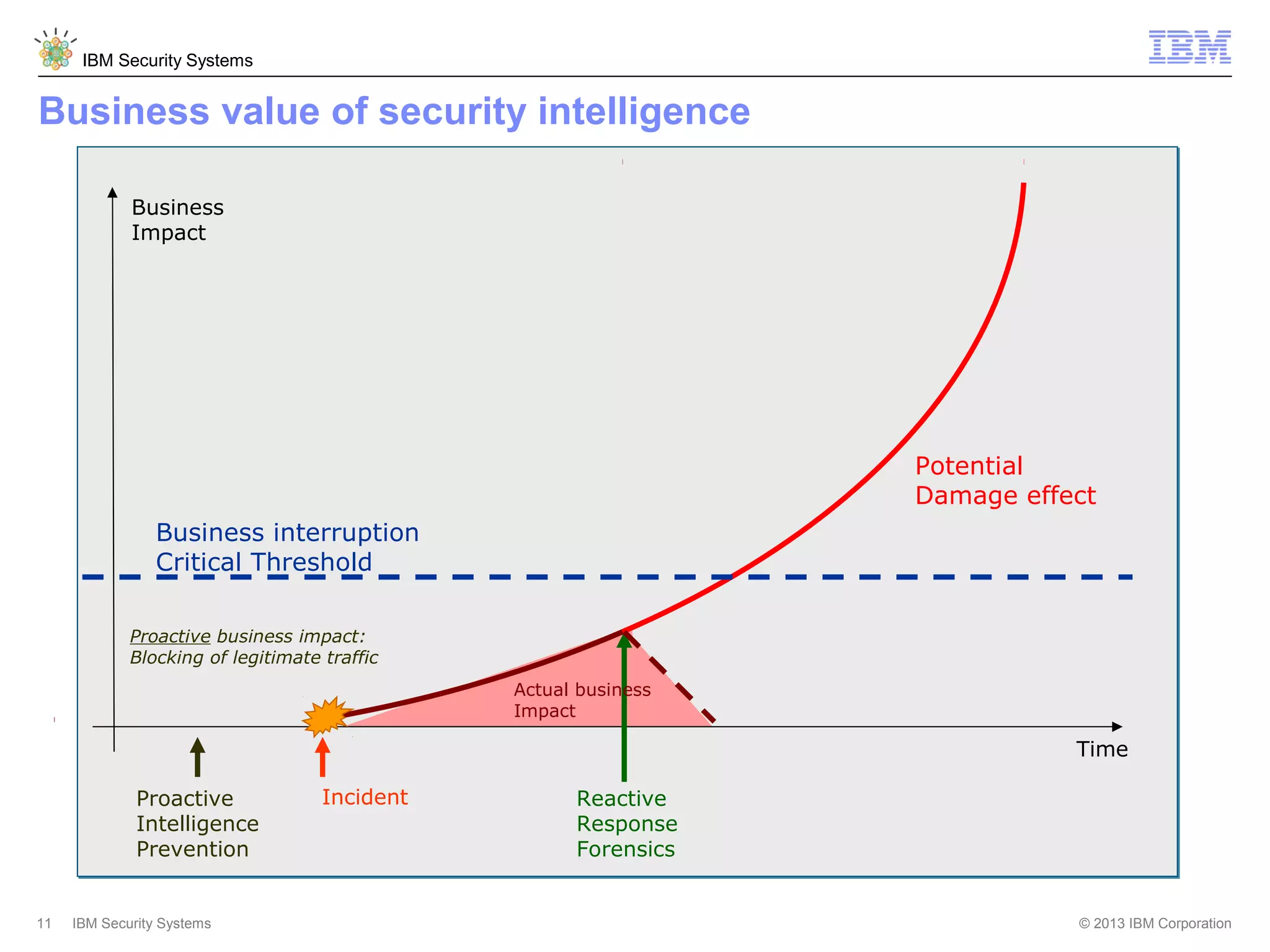
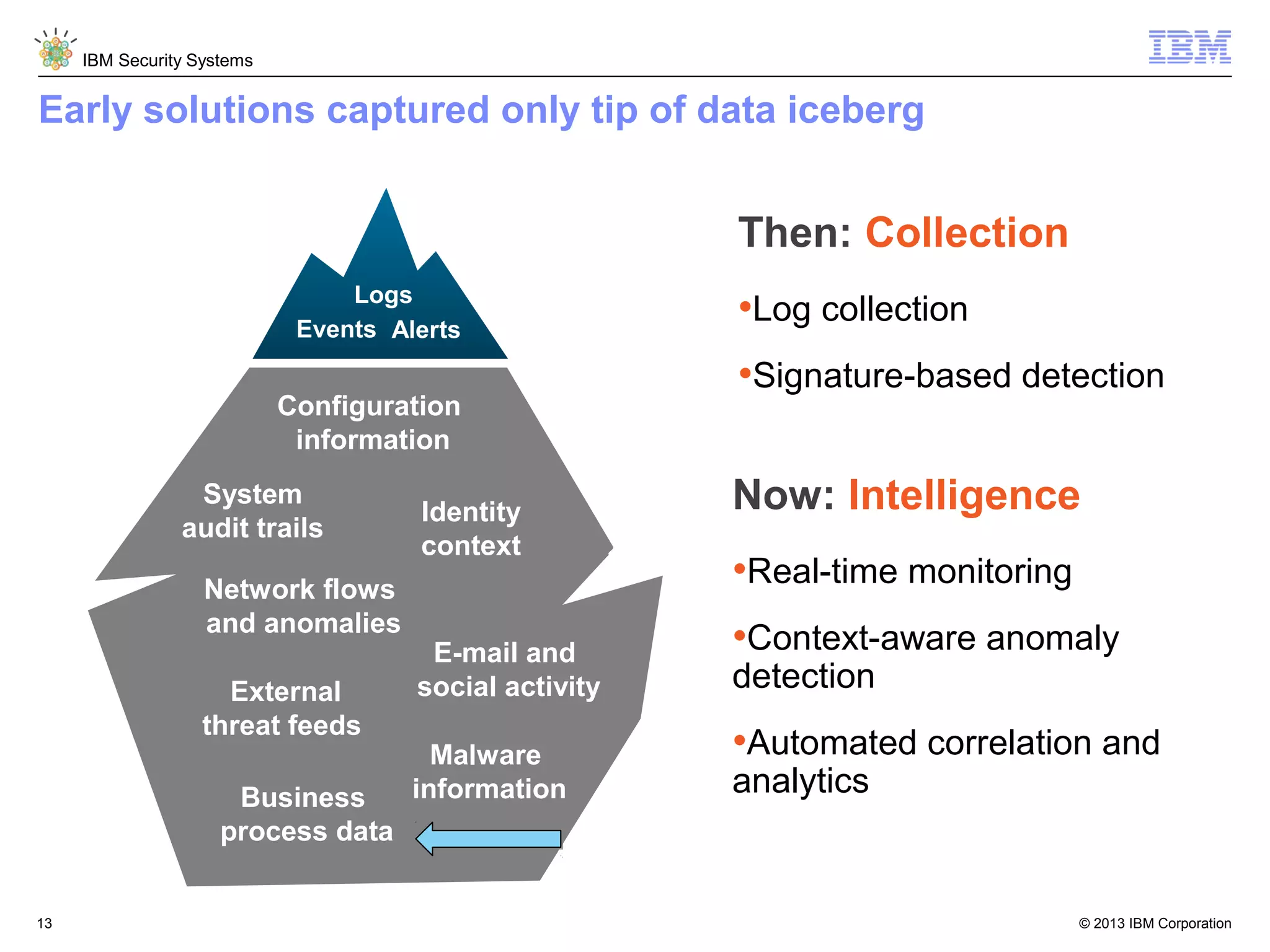
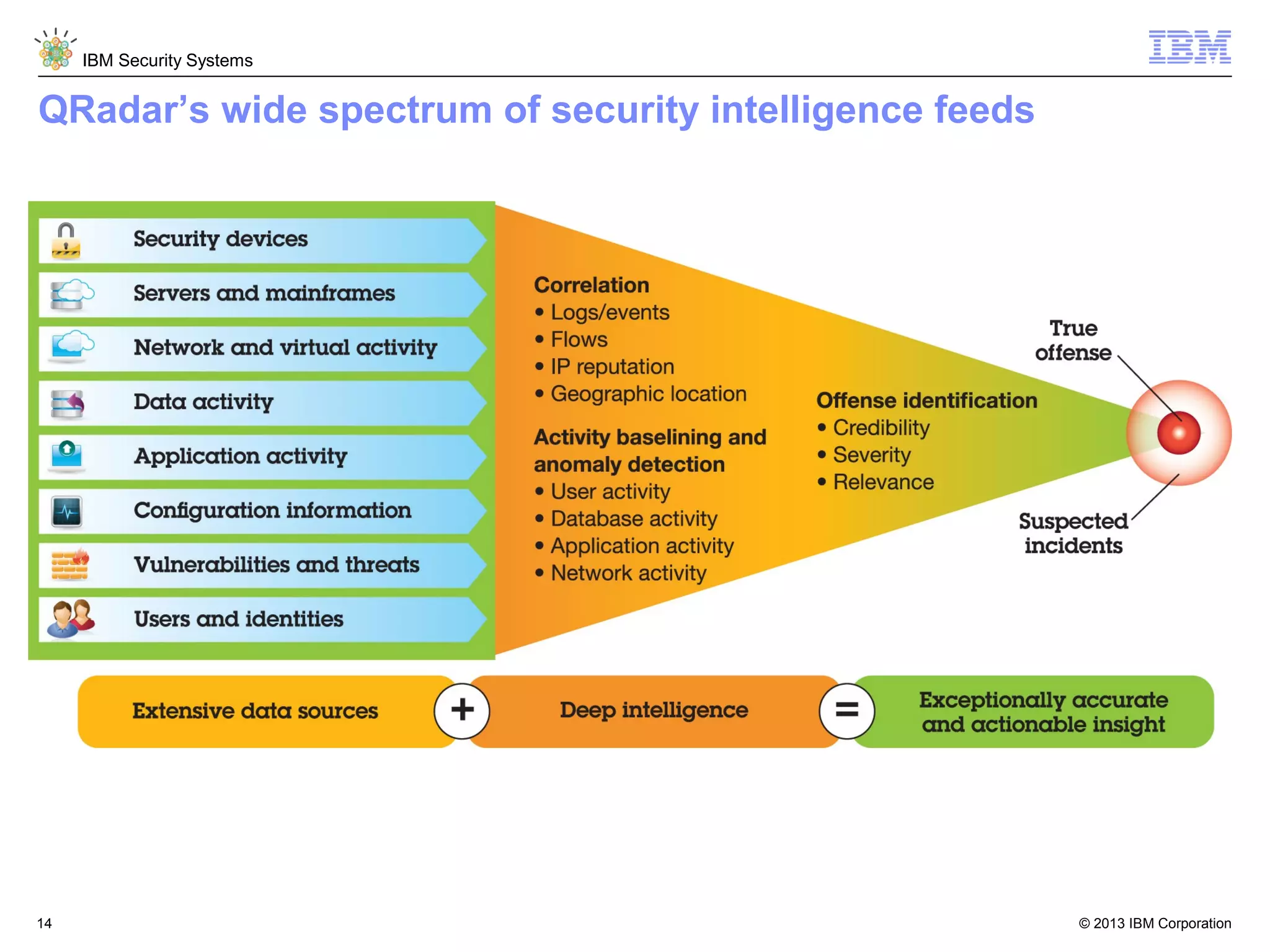
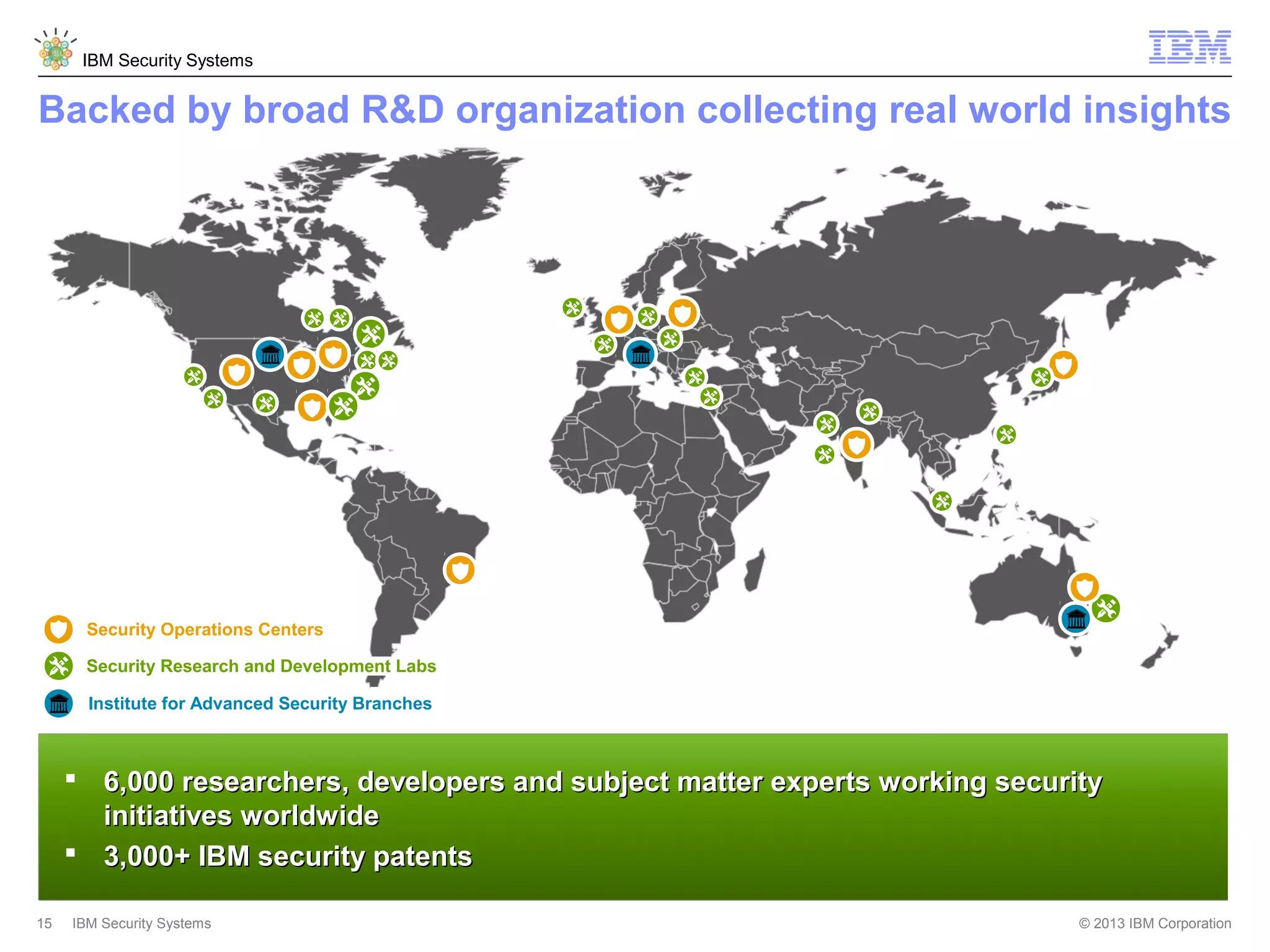
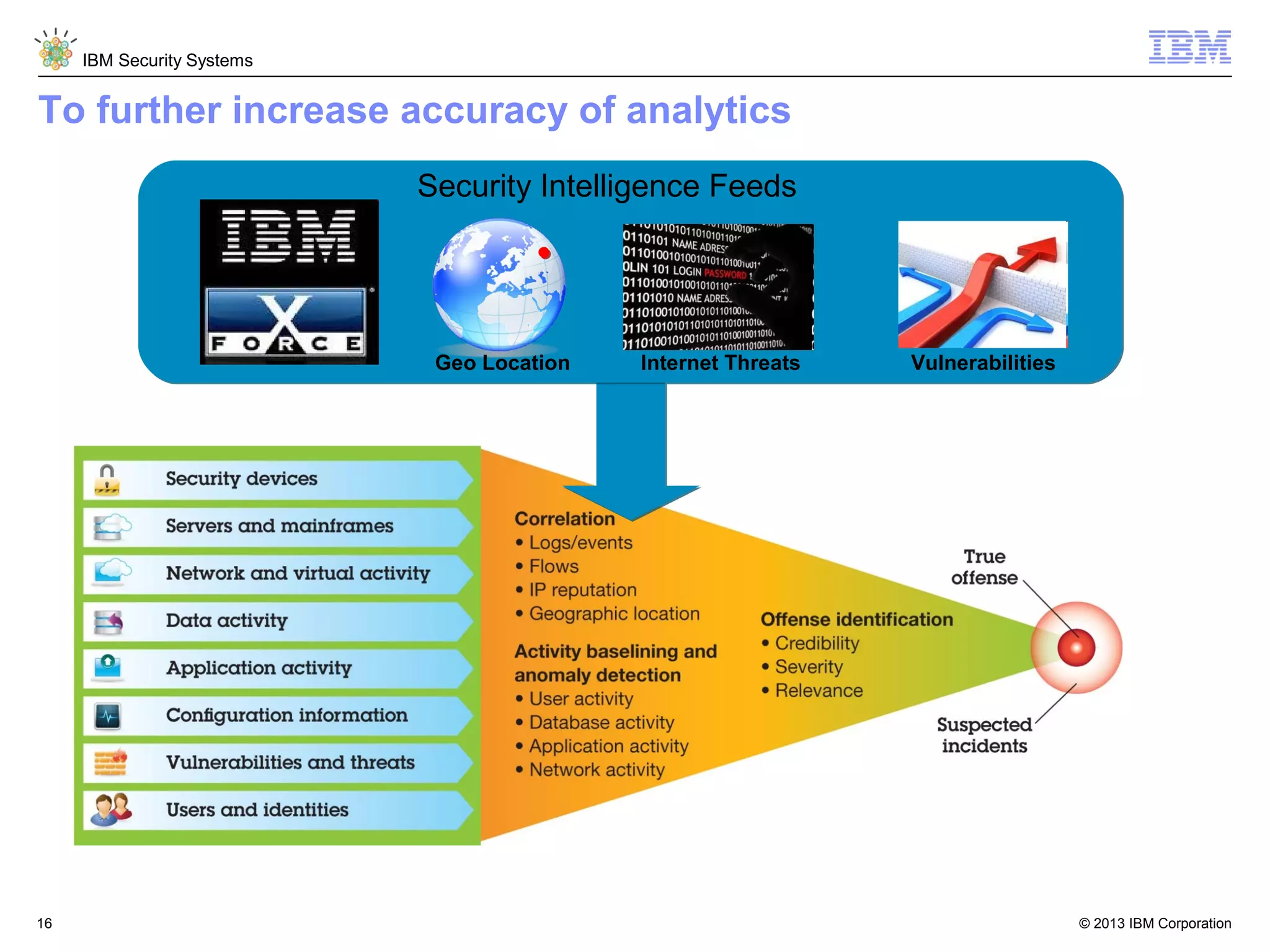
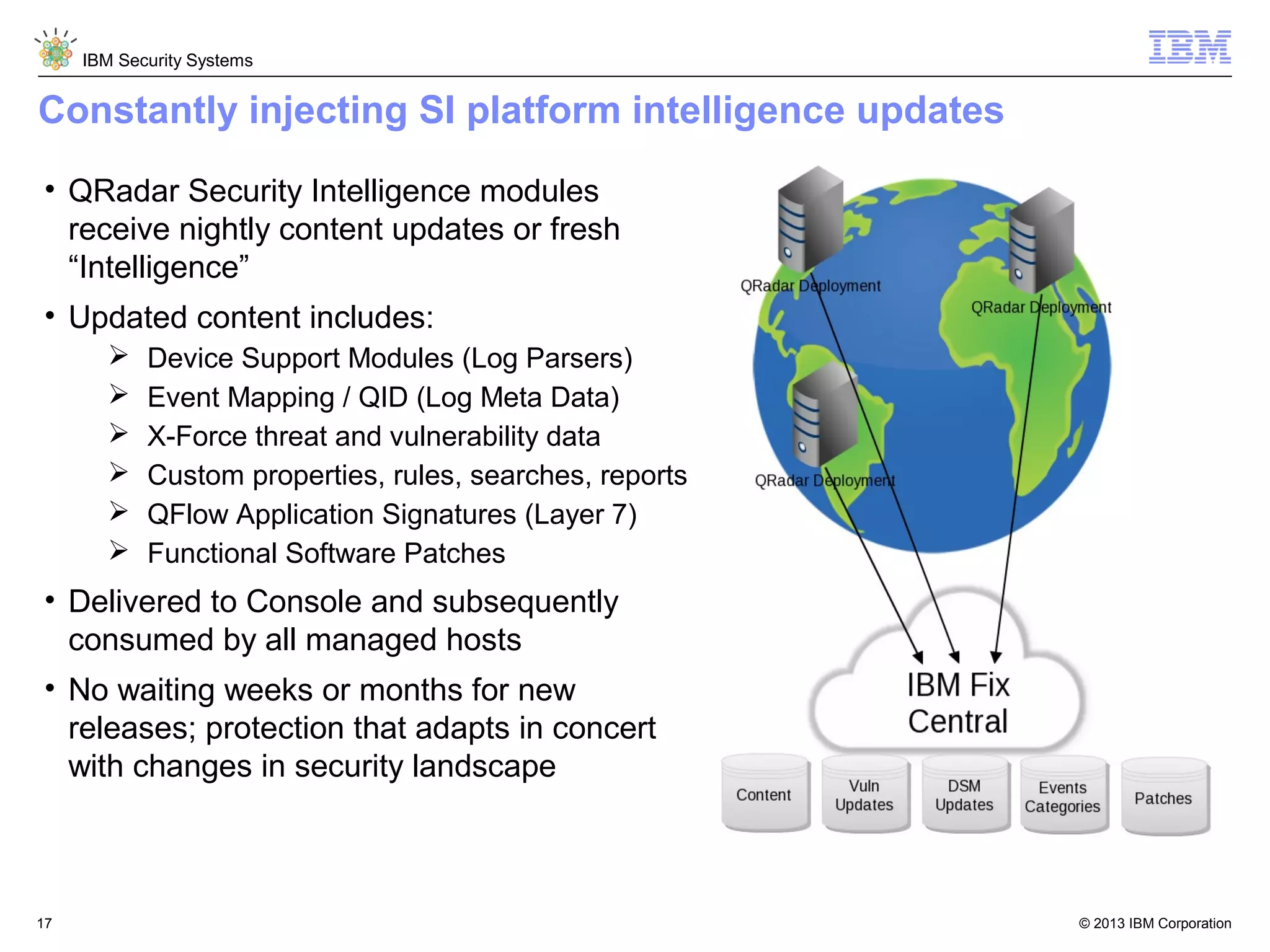
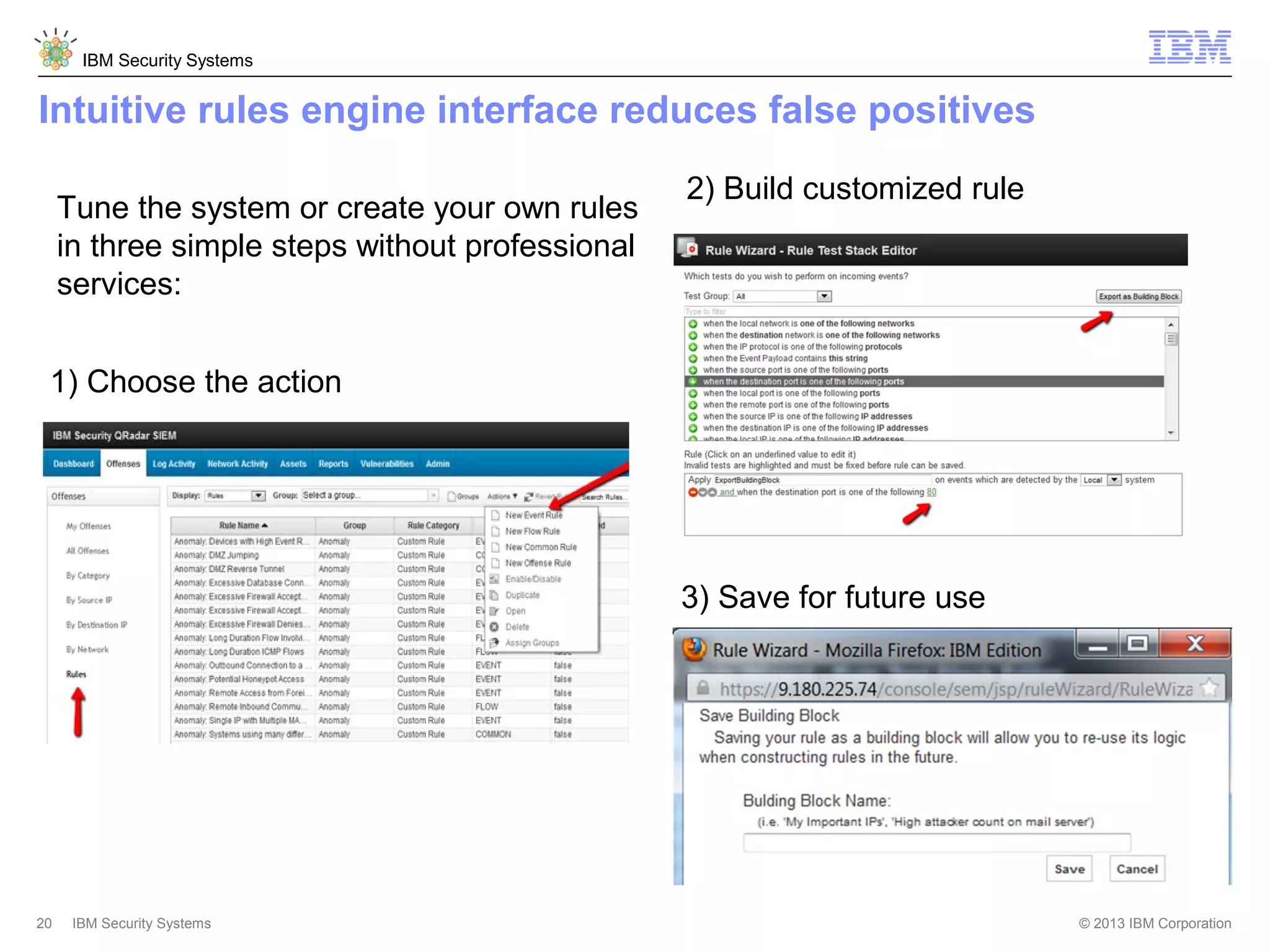
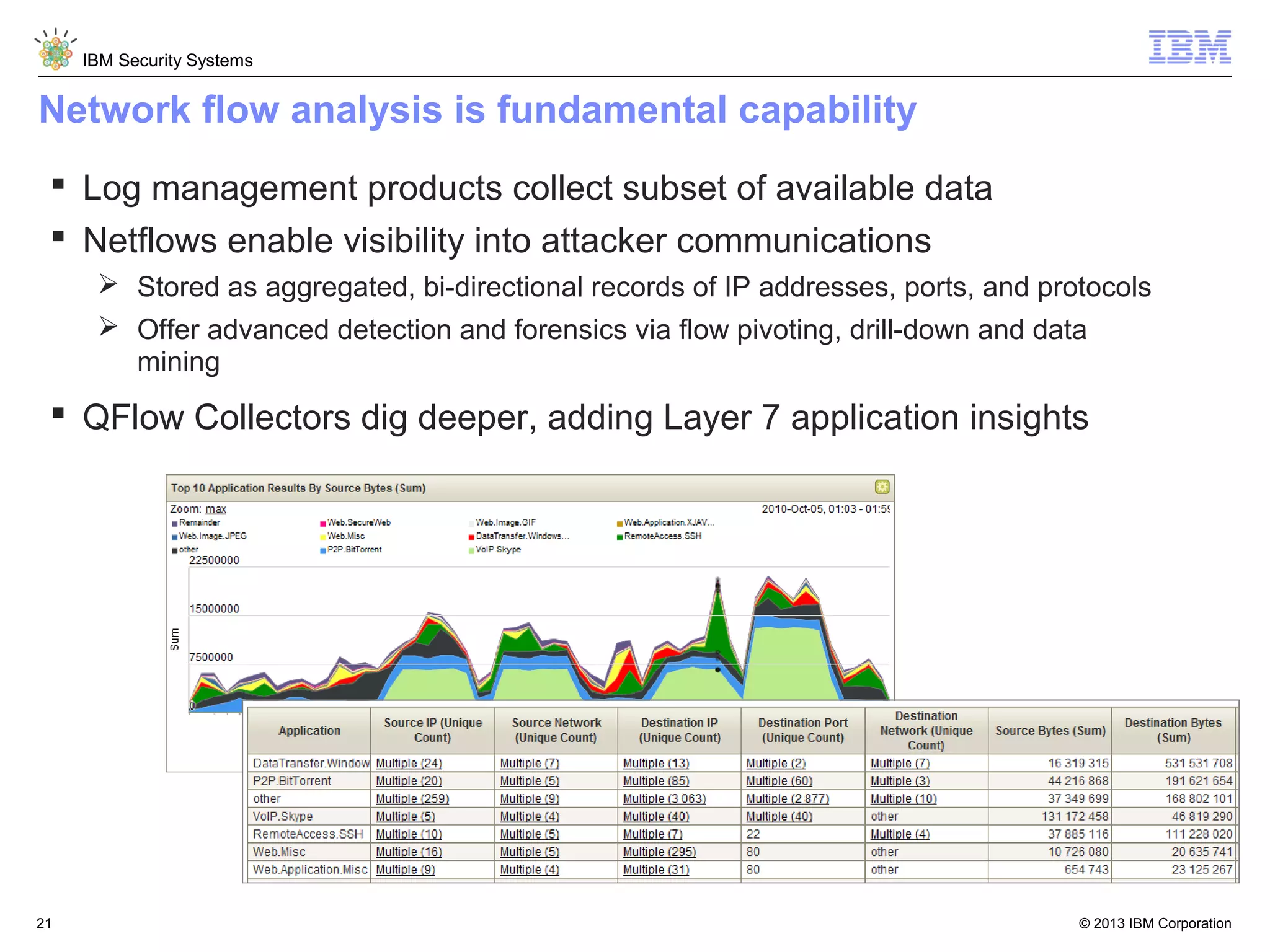
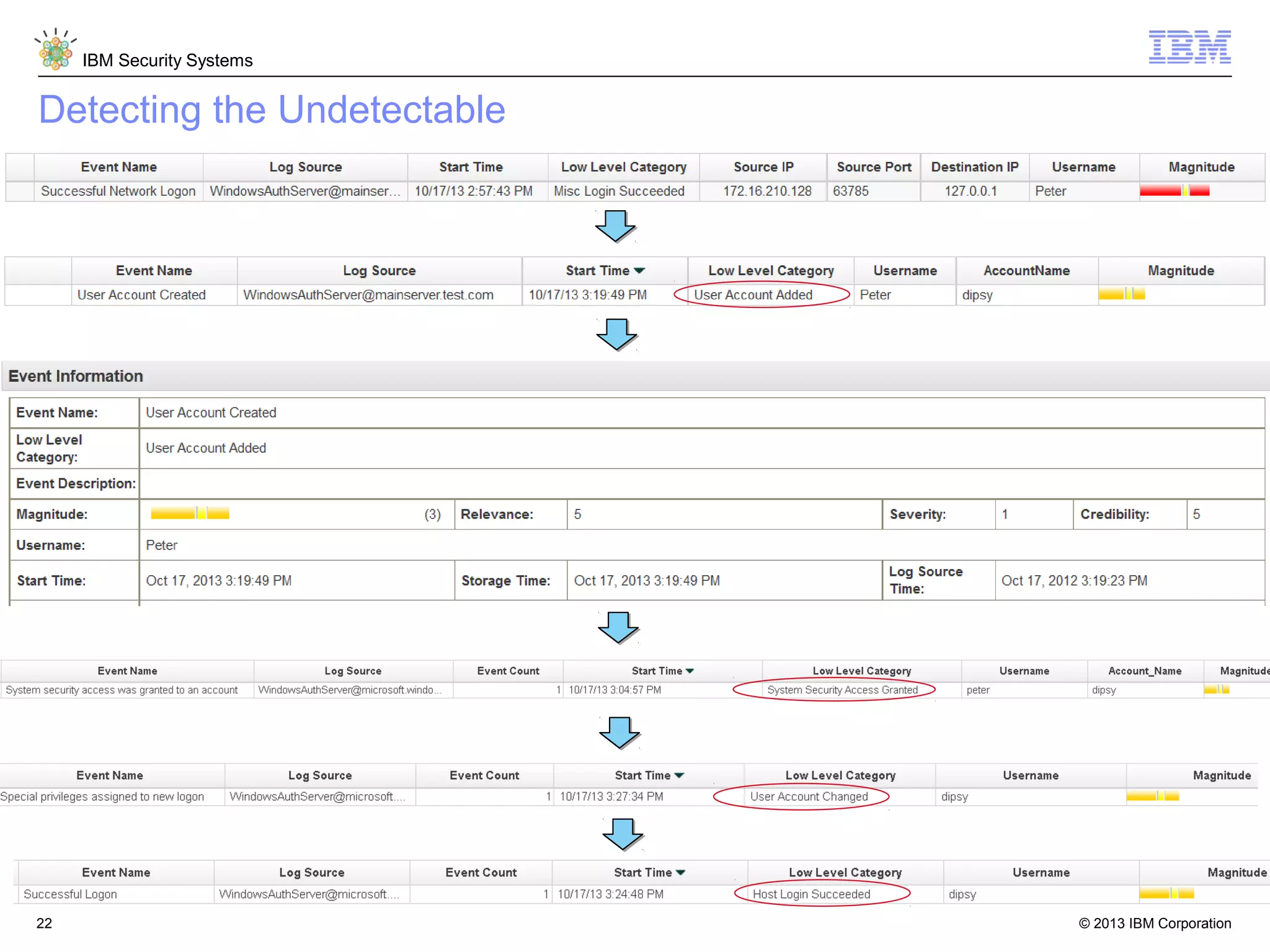
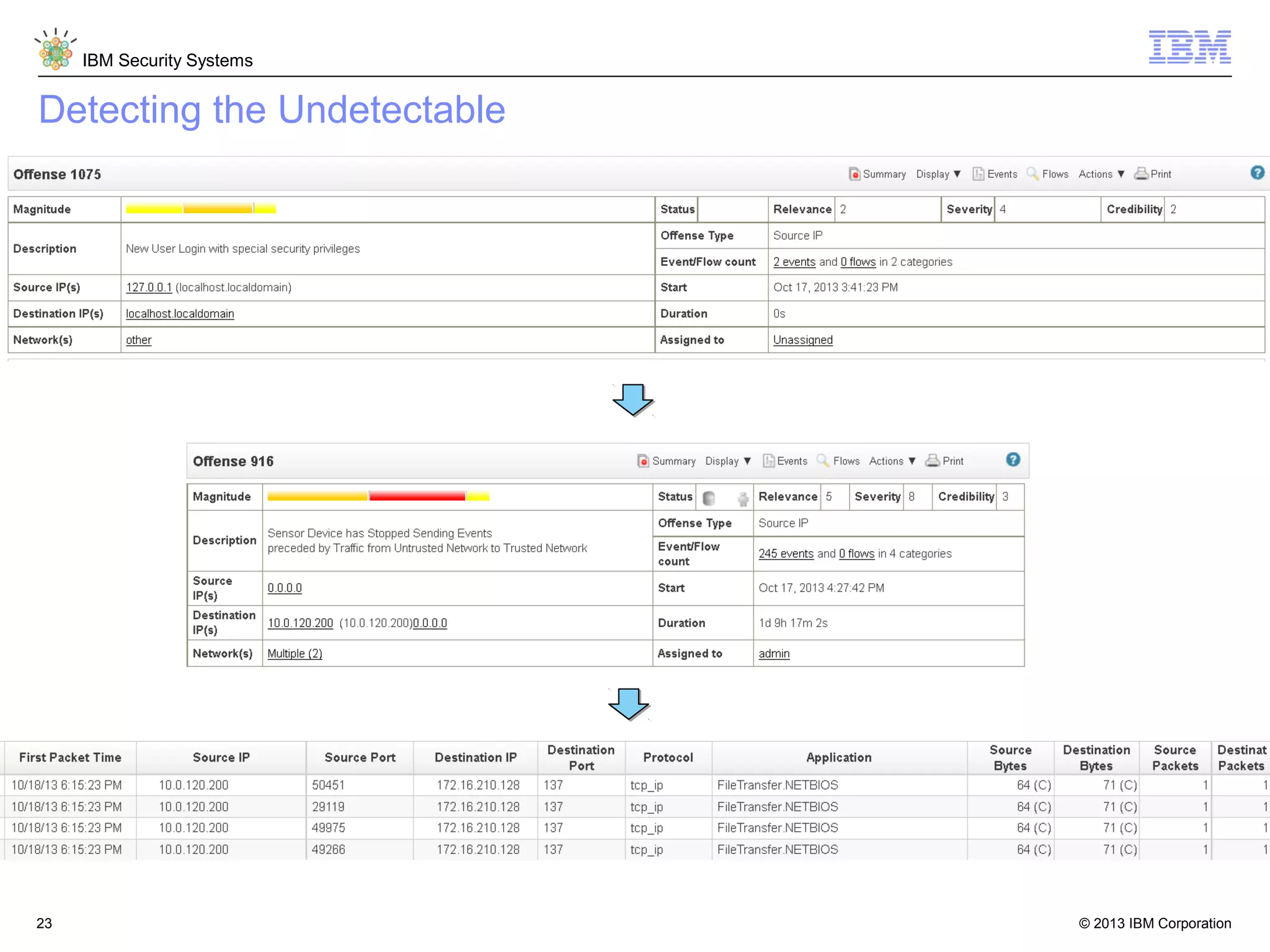
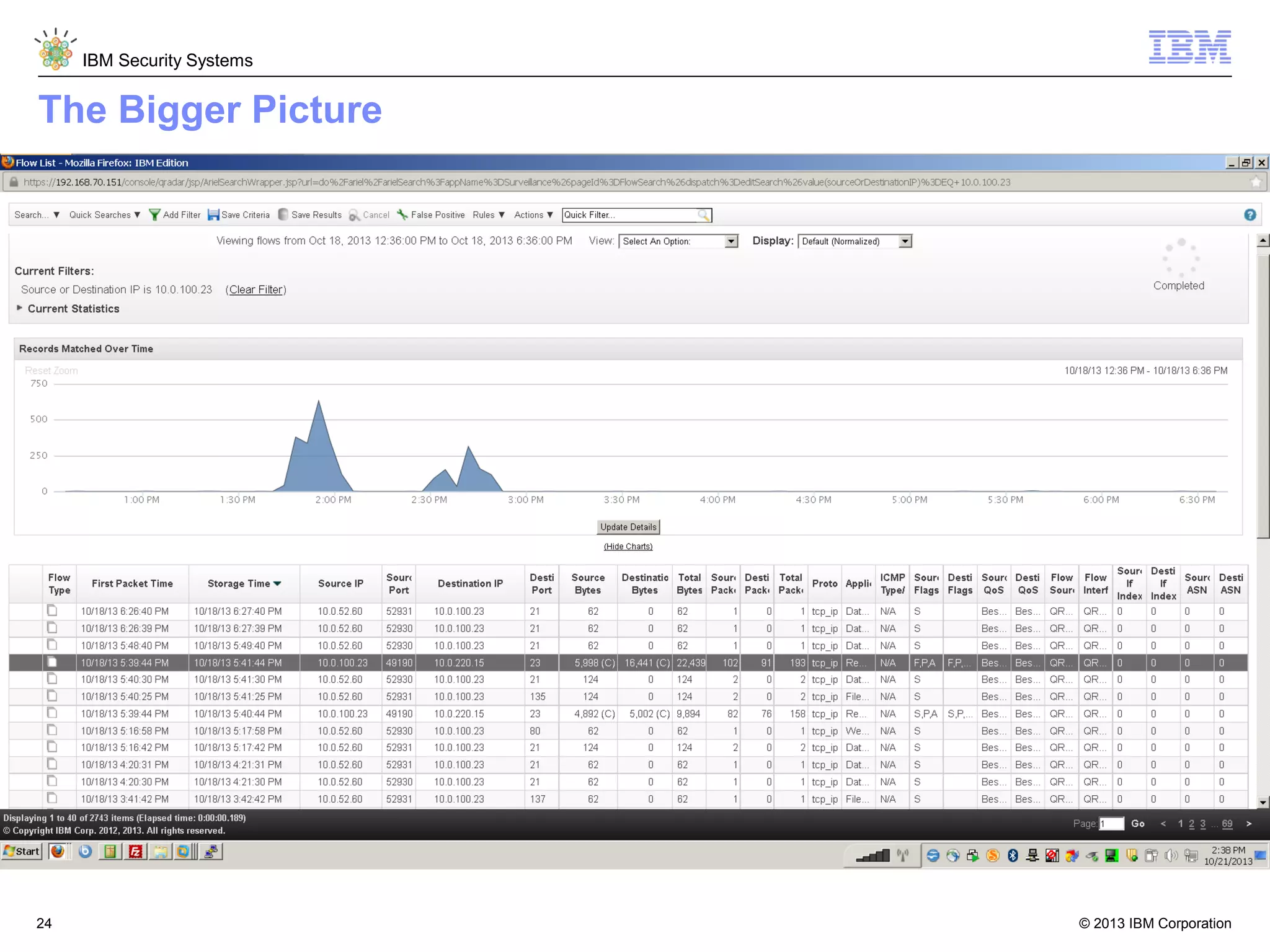
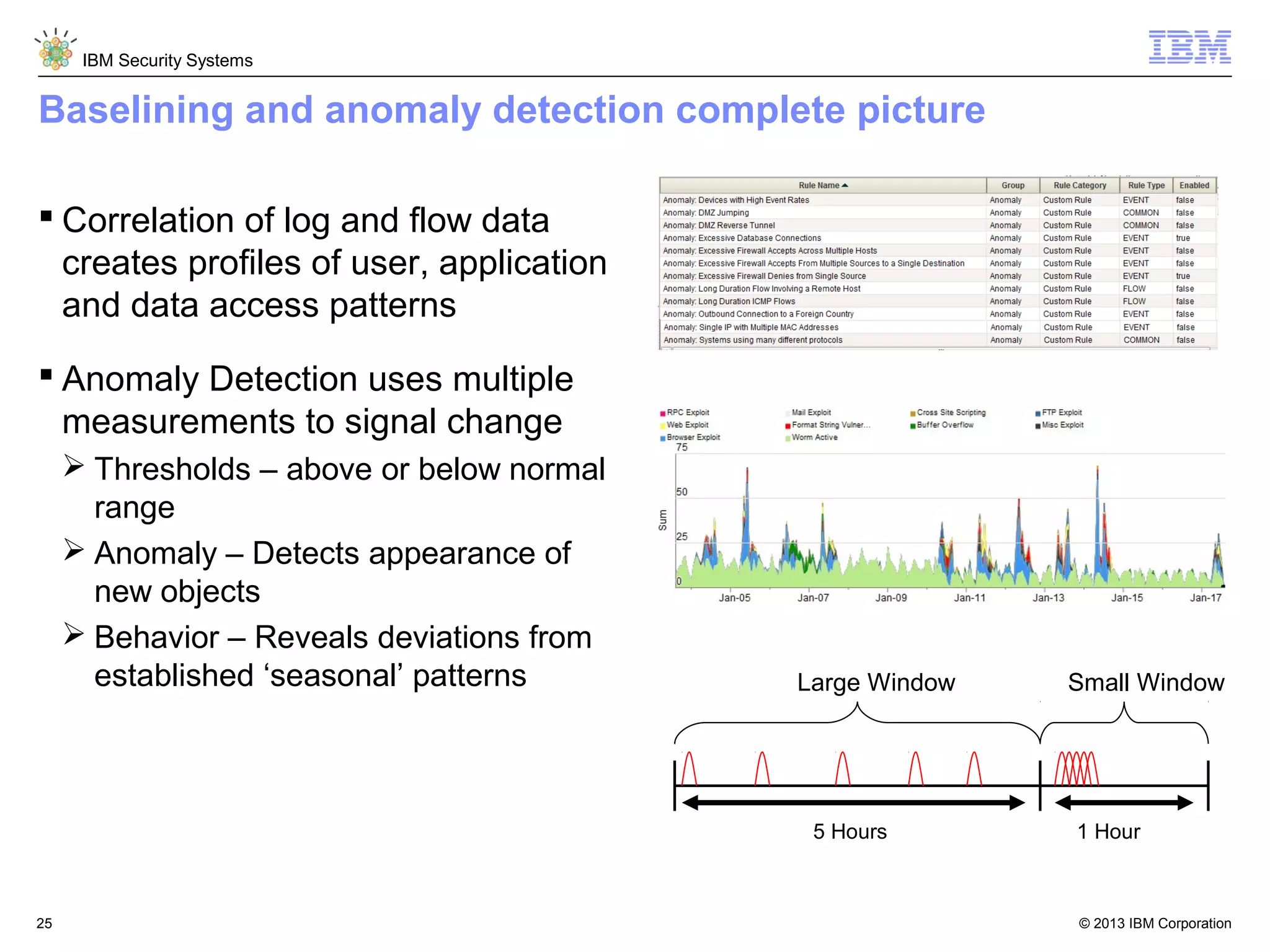
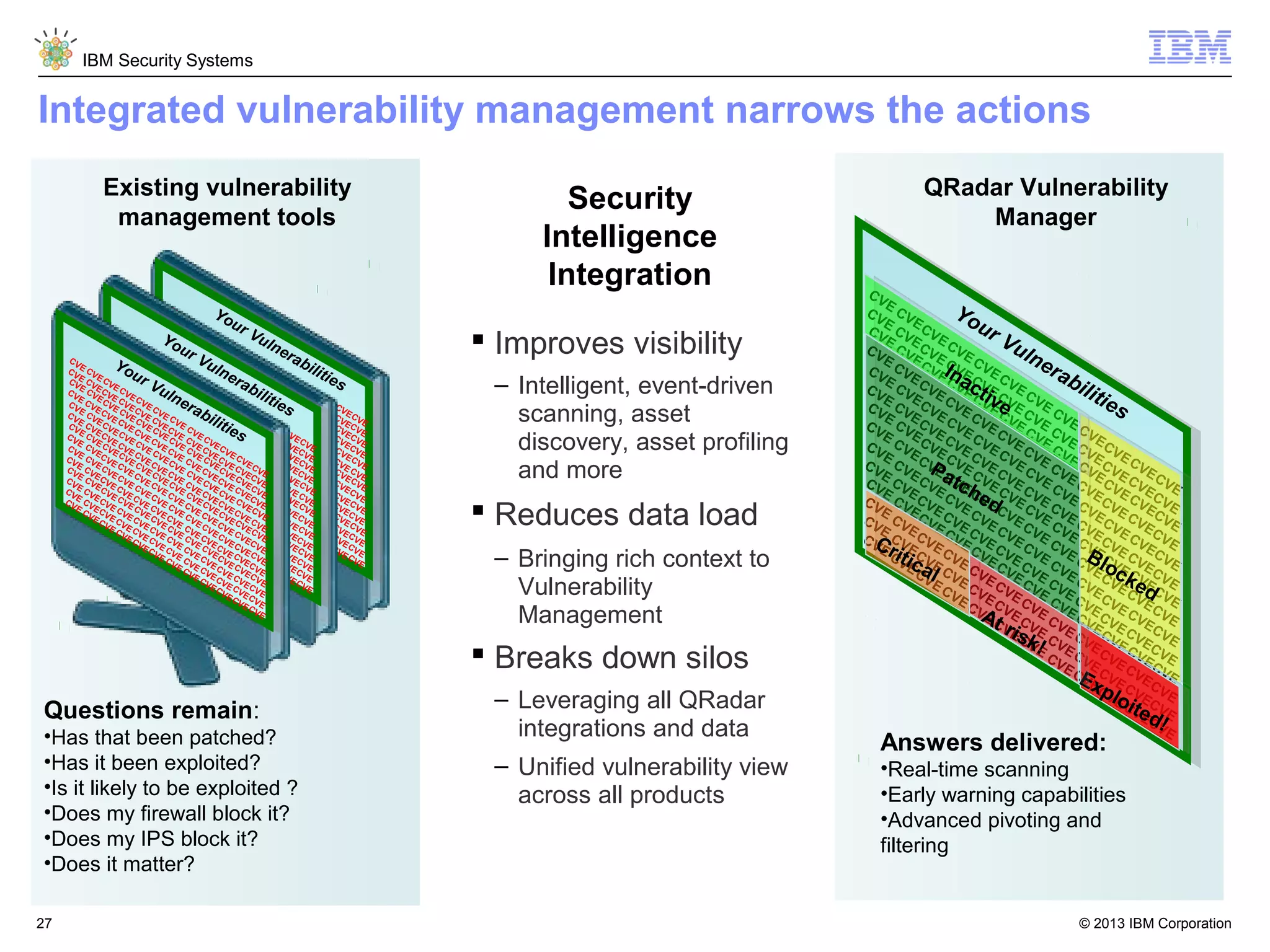
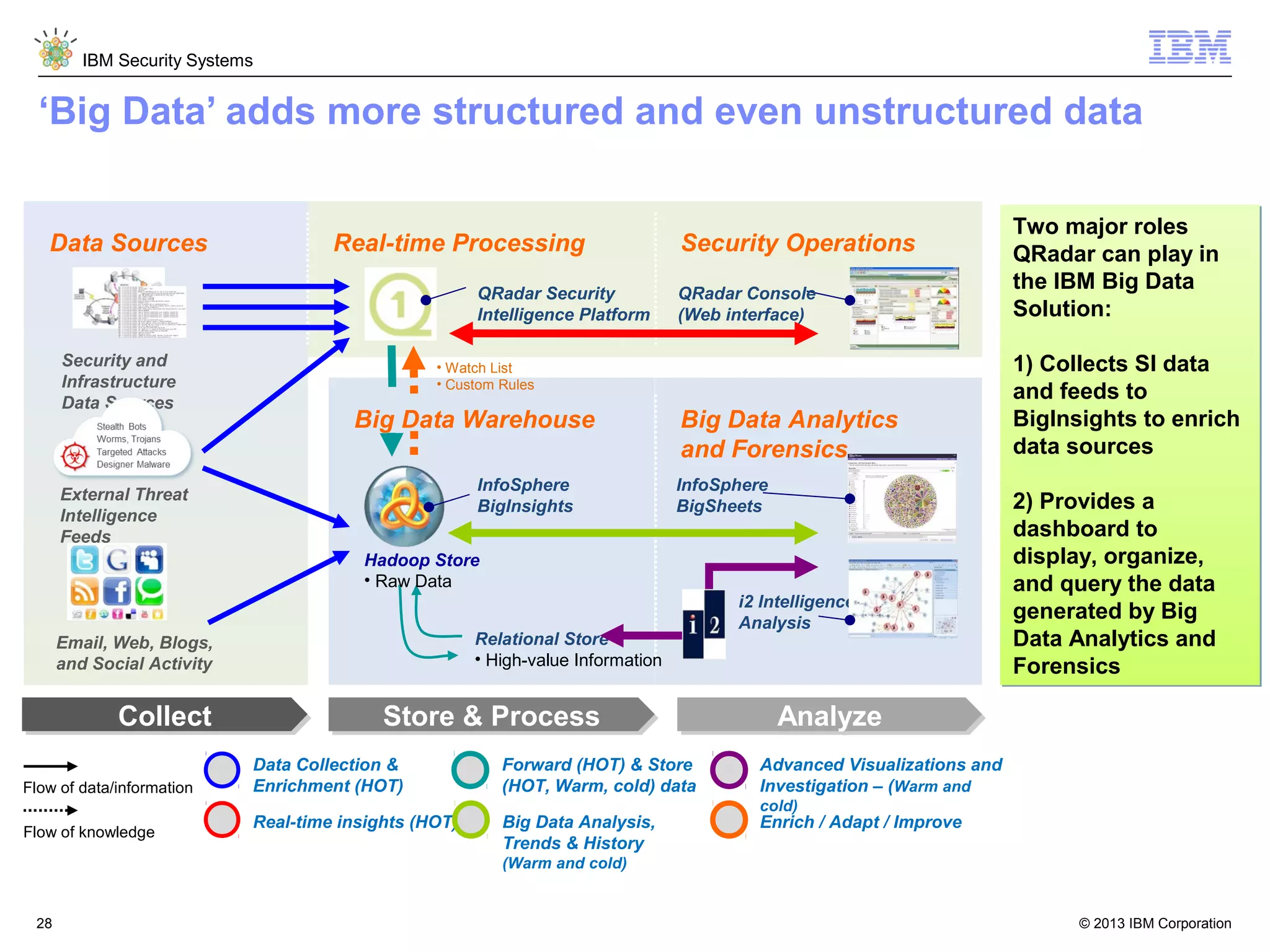
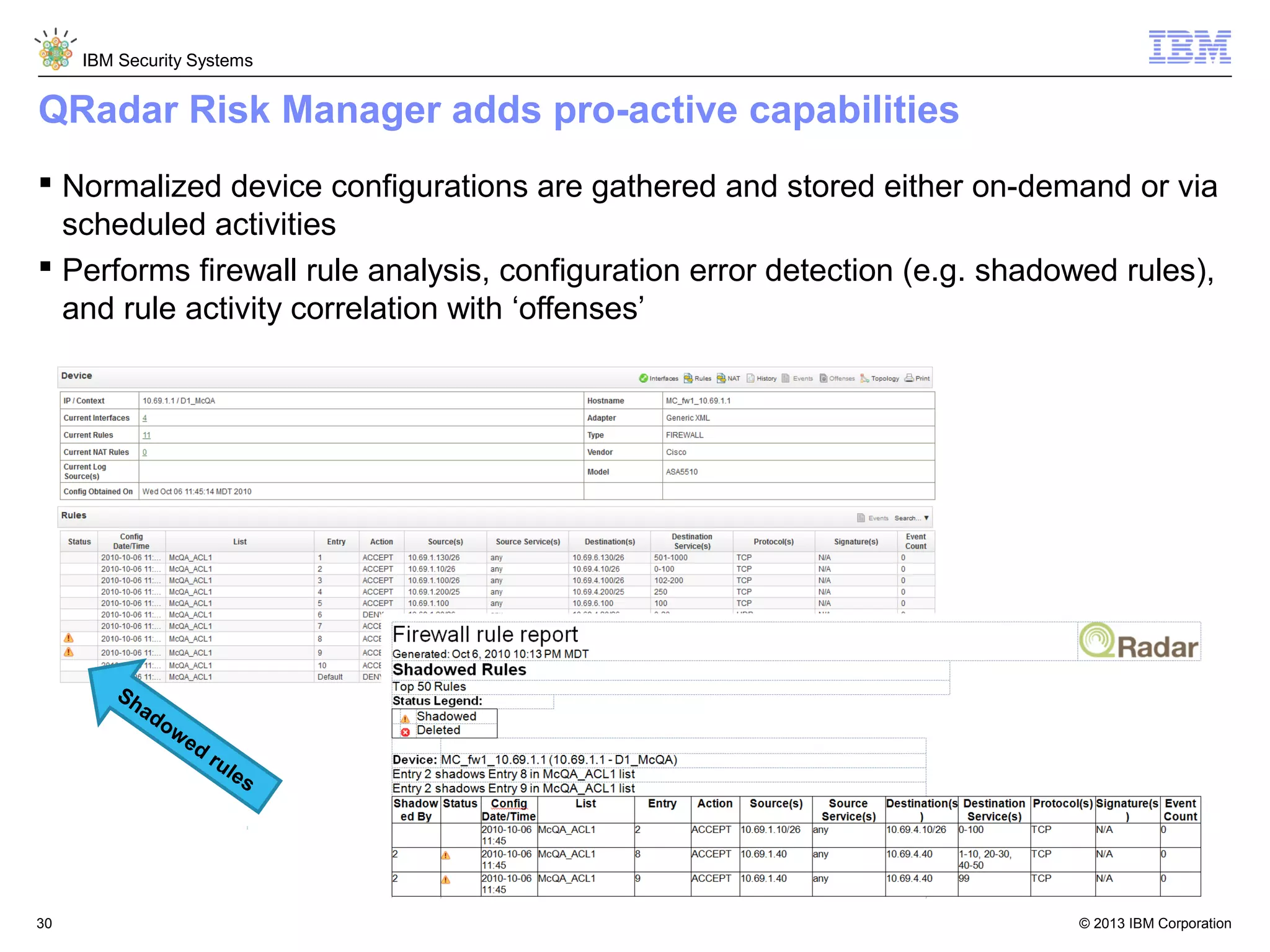
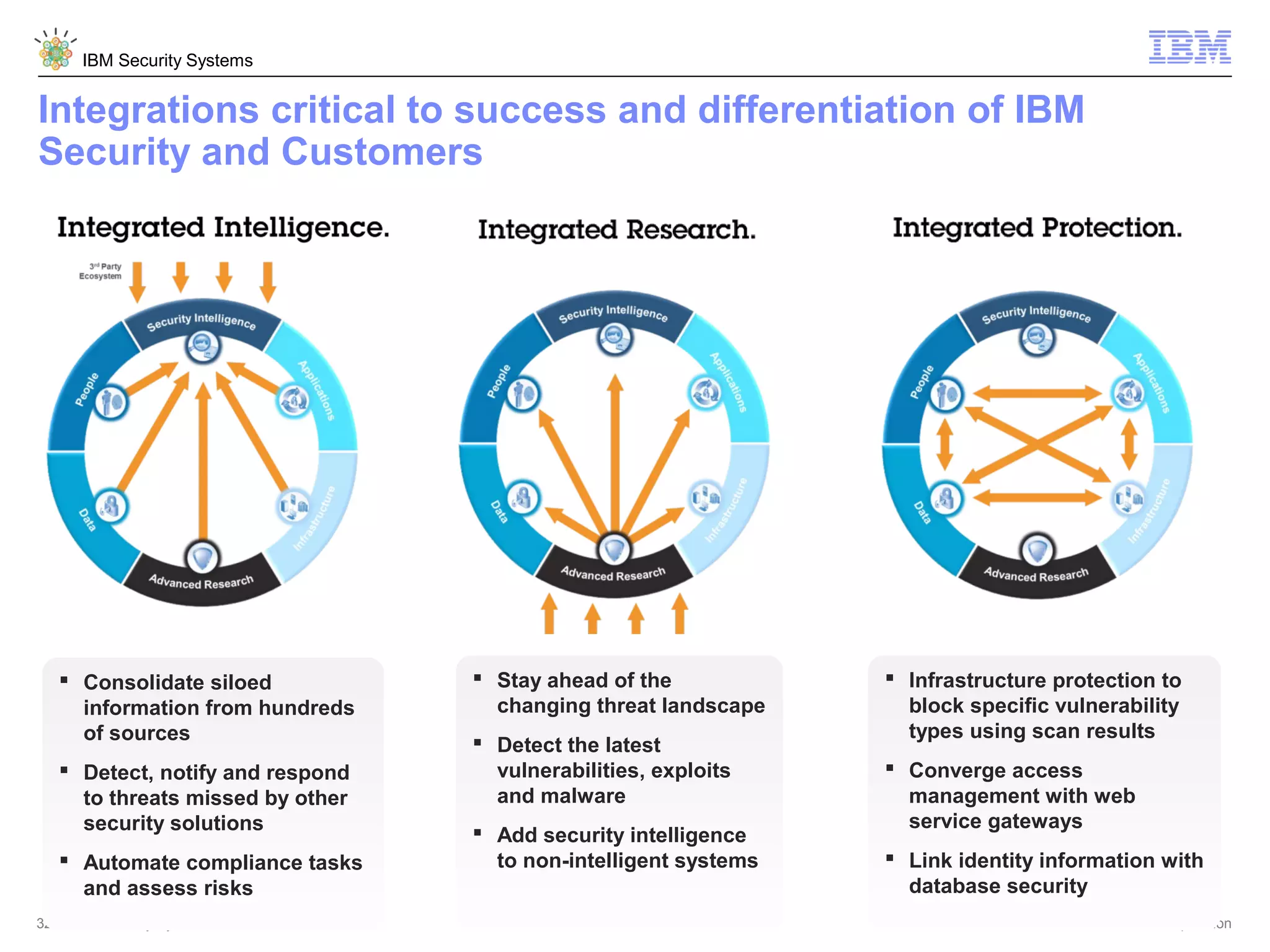
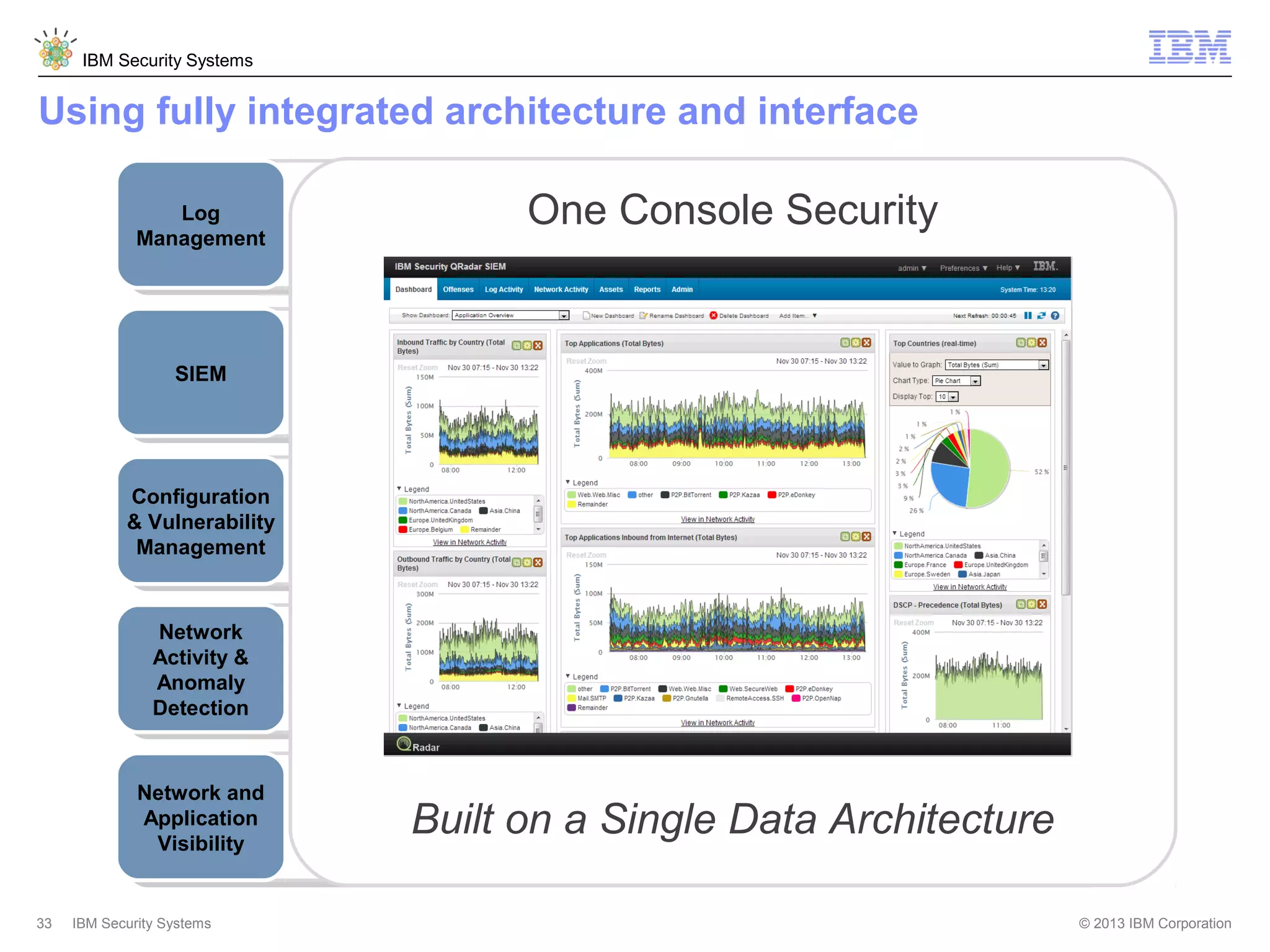
This document discusses five critical conditions for maximizing security intelligence investments. It begins by noting the proliferation of innovative technologies and connected devices that have changed the threat landscape. It then discusses how attacks continue to evolve in sophistication. The document emphasizes that targeted attacks remain a top concern and lists several high-profile attacks. It notes that security solutions alone are not enough and that security intelligence is needed. The document provides five key points: 1) what you don't know can hurt you, 2) force multipliers are key to winning the battle, 3) reduce incident investigations with more available data, 4) further reduce blind spots using non-traditional event sources, and 5) 'big data' adds more structured and unstructured data