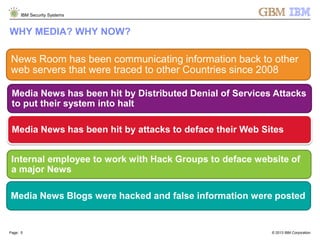
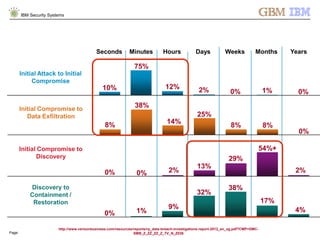
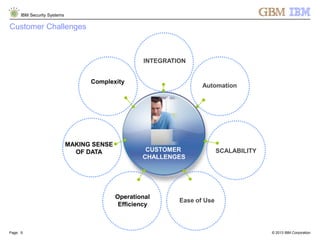
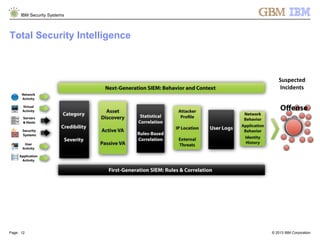
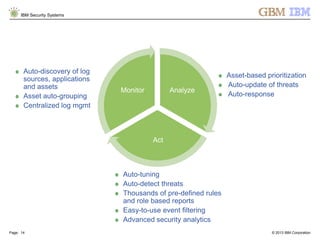
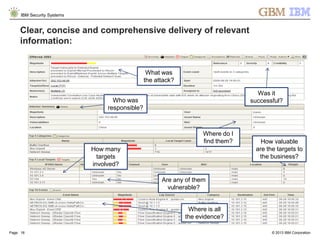
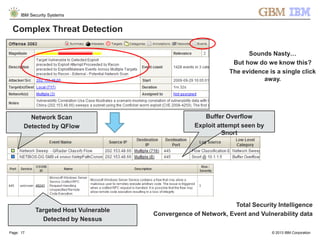
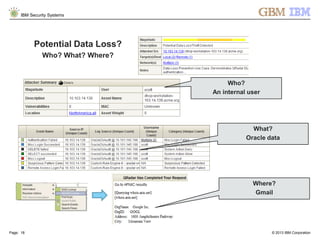
The document is a presentation by Ahmed El Nahas from IBM about IBM's security intelligence products and services. It discusses challenges customers face around making sense of large amounts of security data, the need for integration and automation. It provides examples of how IBM security intelligence solutions can help detect threats across the network, identify vulnerabilities and risk of data loss. Analytics and visualization tools are demonstrated to provide clear evidence and answers to common security questions.