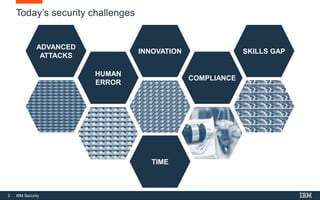
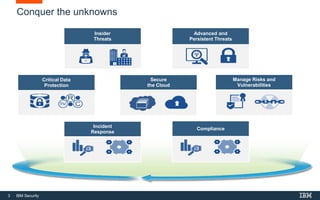
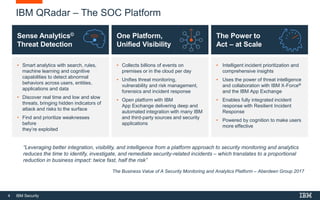
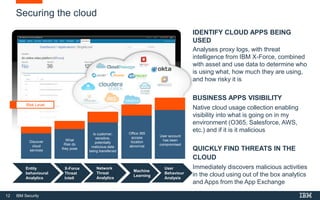
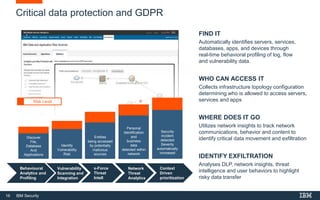
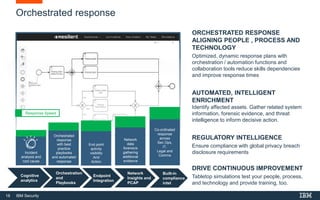
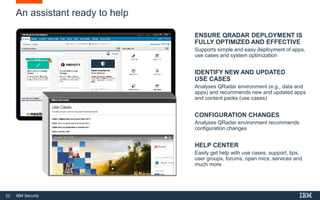
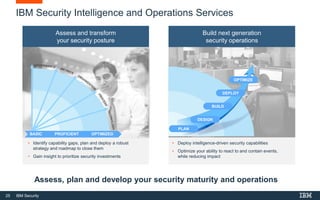
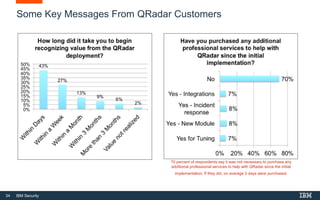
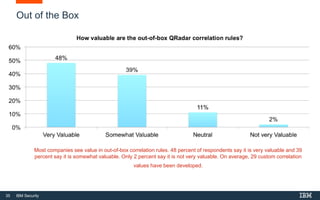
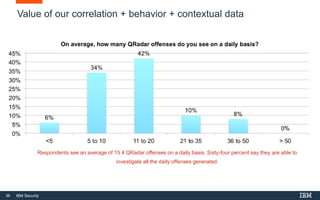
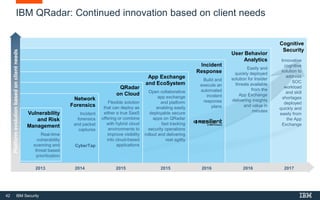
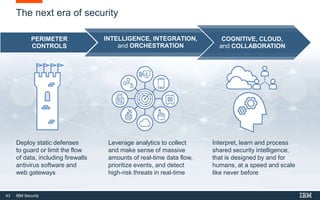
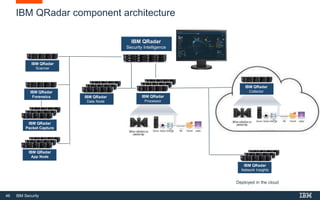
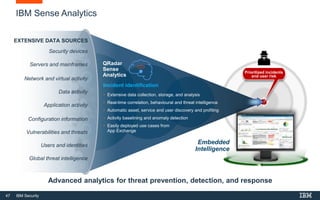
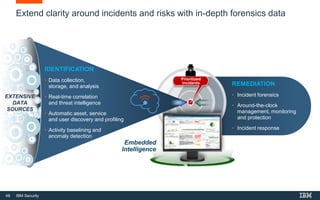
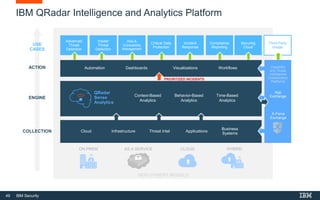
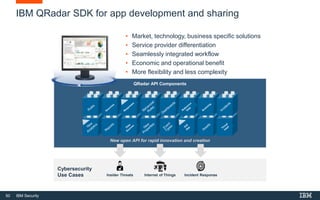
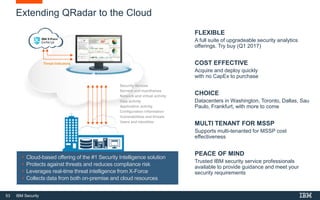
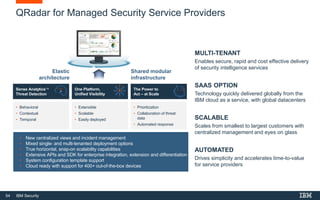
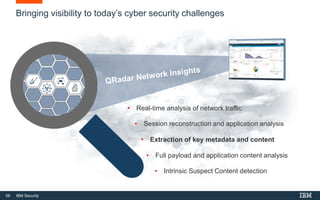
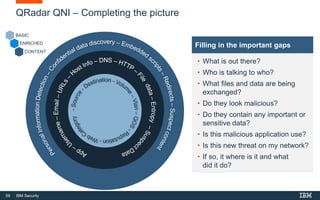
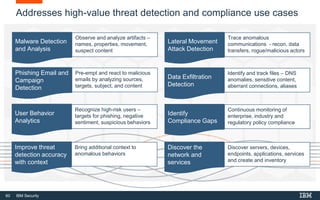
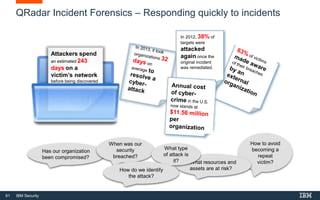
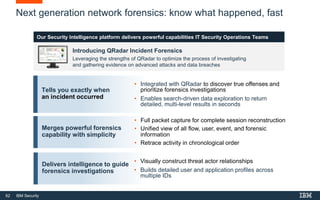
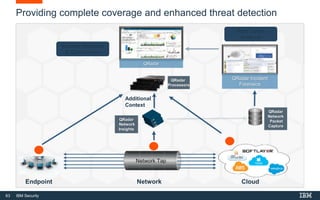
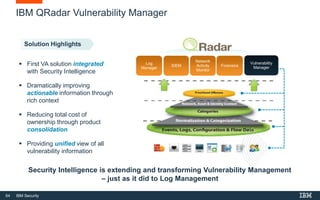
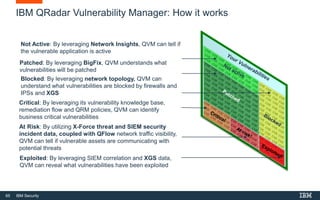
This document discusses IBM QRadar, a security intelligence platform. It addresses common security challenges faced by organizations like compliance issues, human error, skills gaps, and advanced attacks. The platform provides threat detection, incident response, and vulnerability management capabilities. It collects data from various sources and uses analytics, machine learning, and cognitive capabilities to detect threats. The document promotes QRadar's abilities to provide unified visibility, quickly identify issues, and enable automated and orchestrated responses. It also highlights QRadar's ecosystem of applications, services, and partners to help customers achieve security.