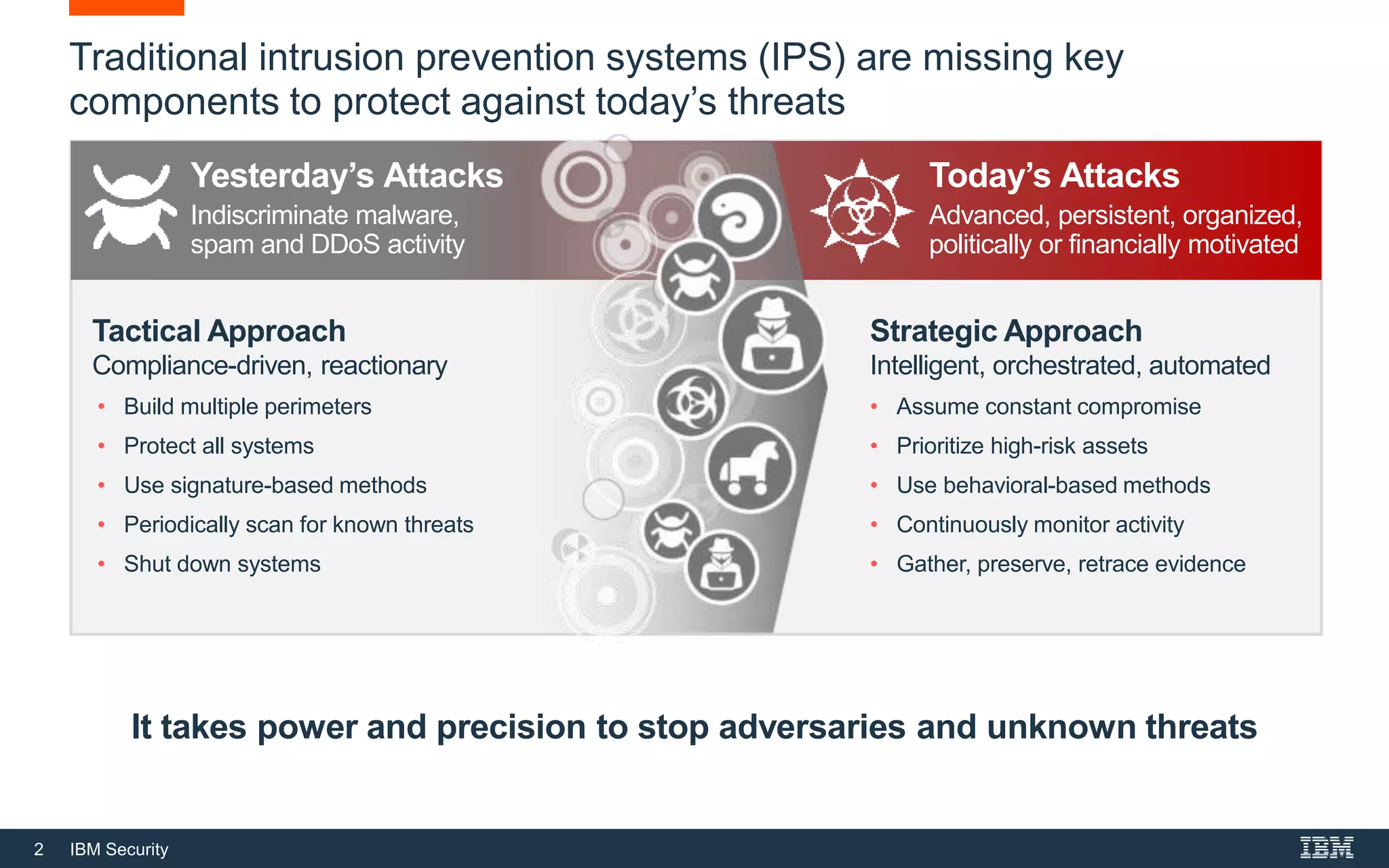
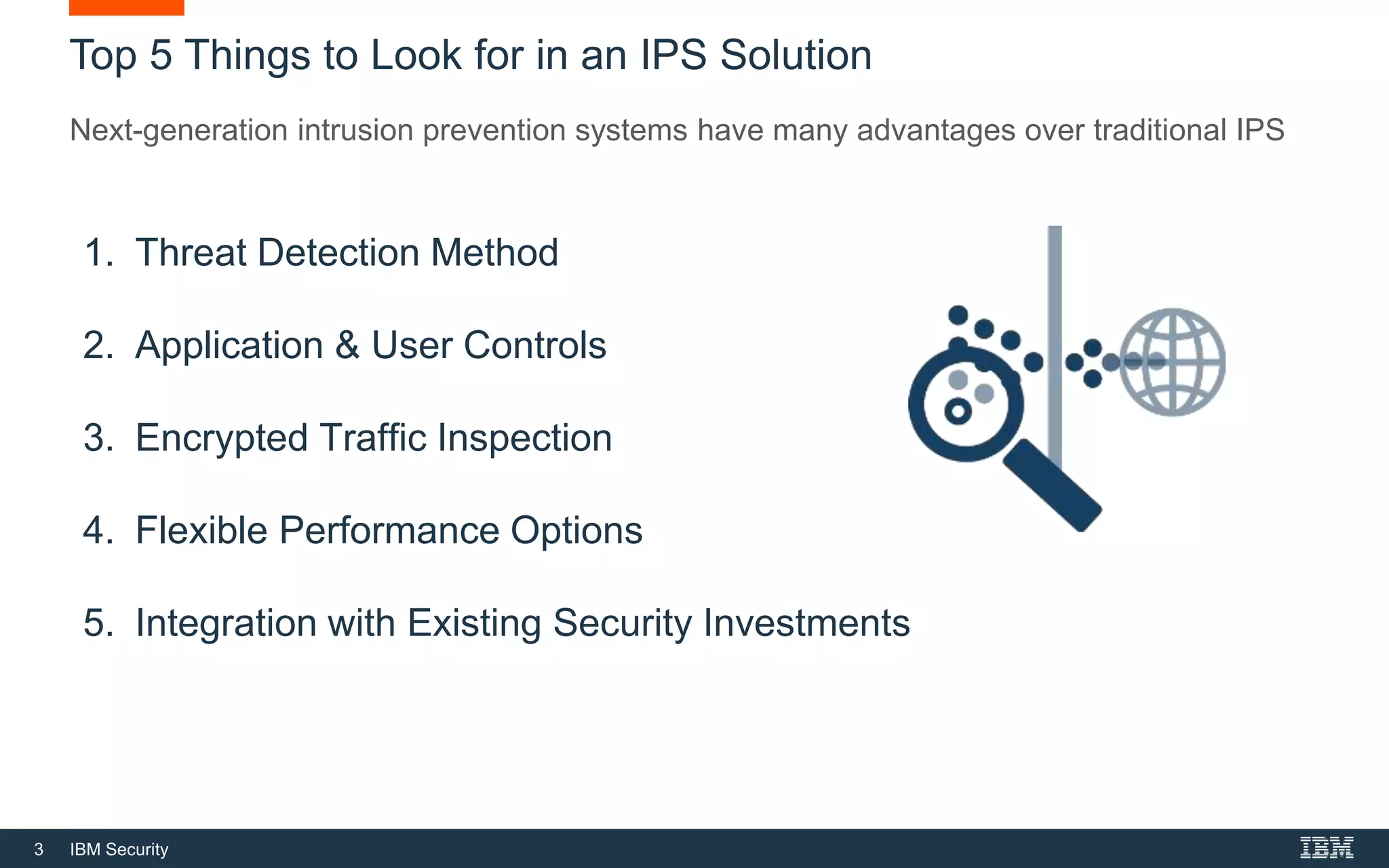
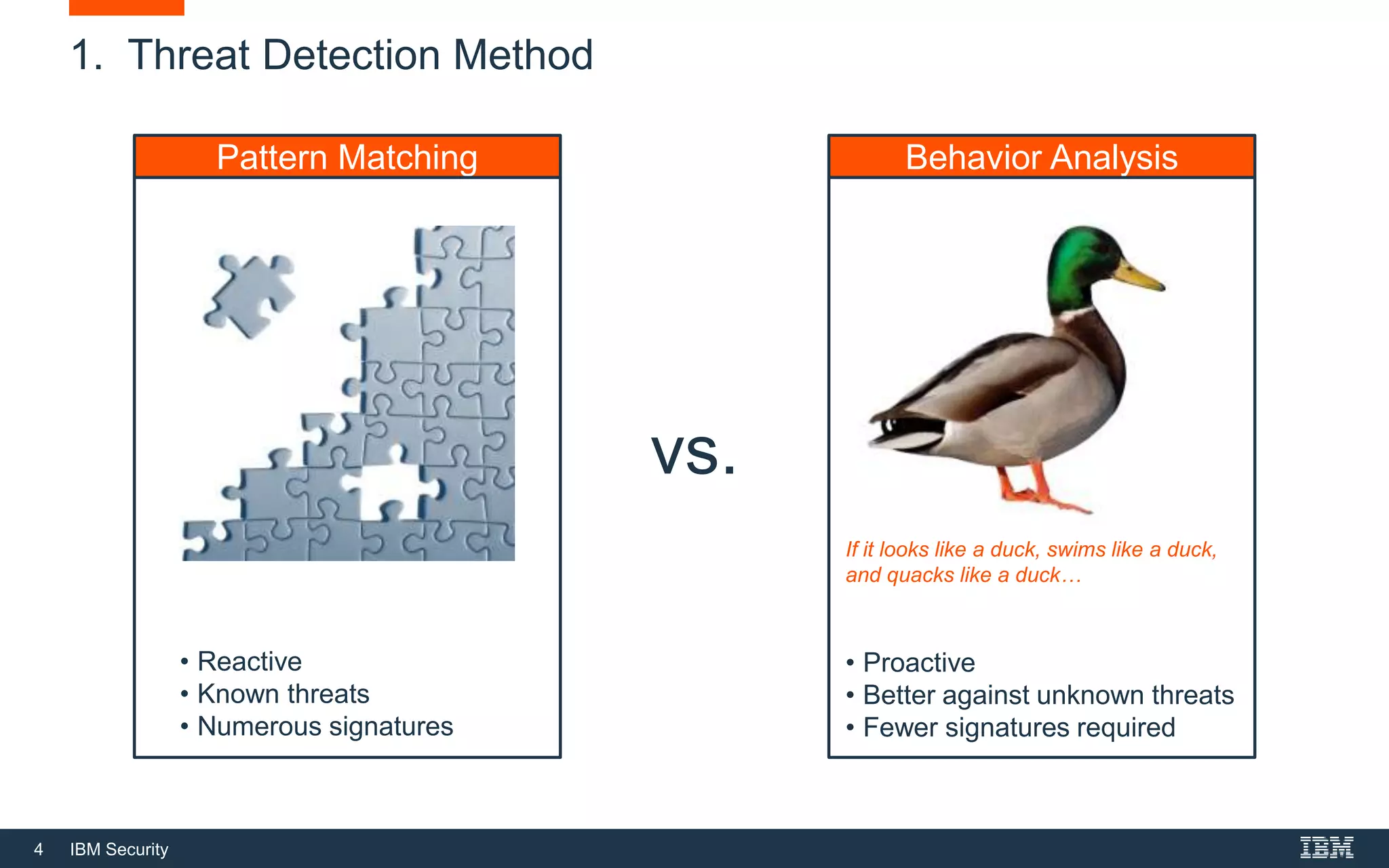
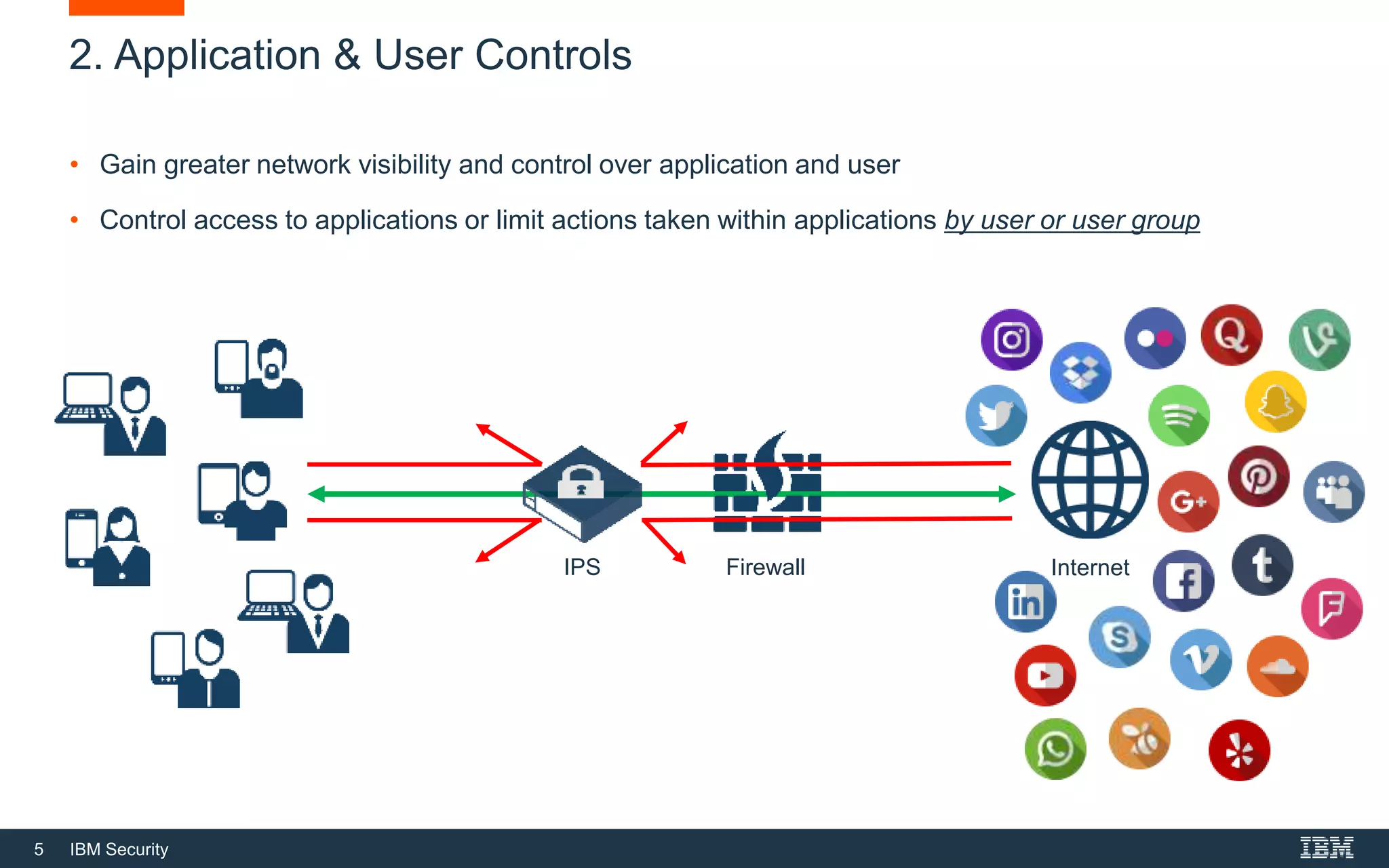
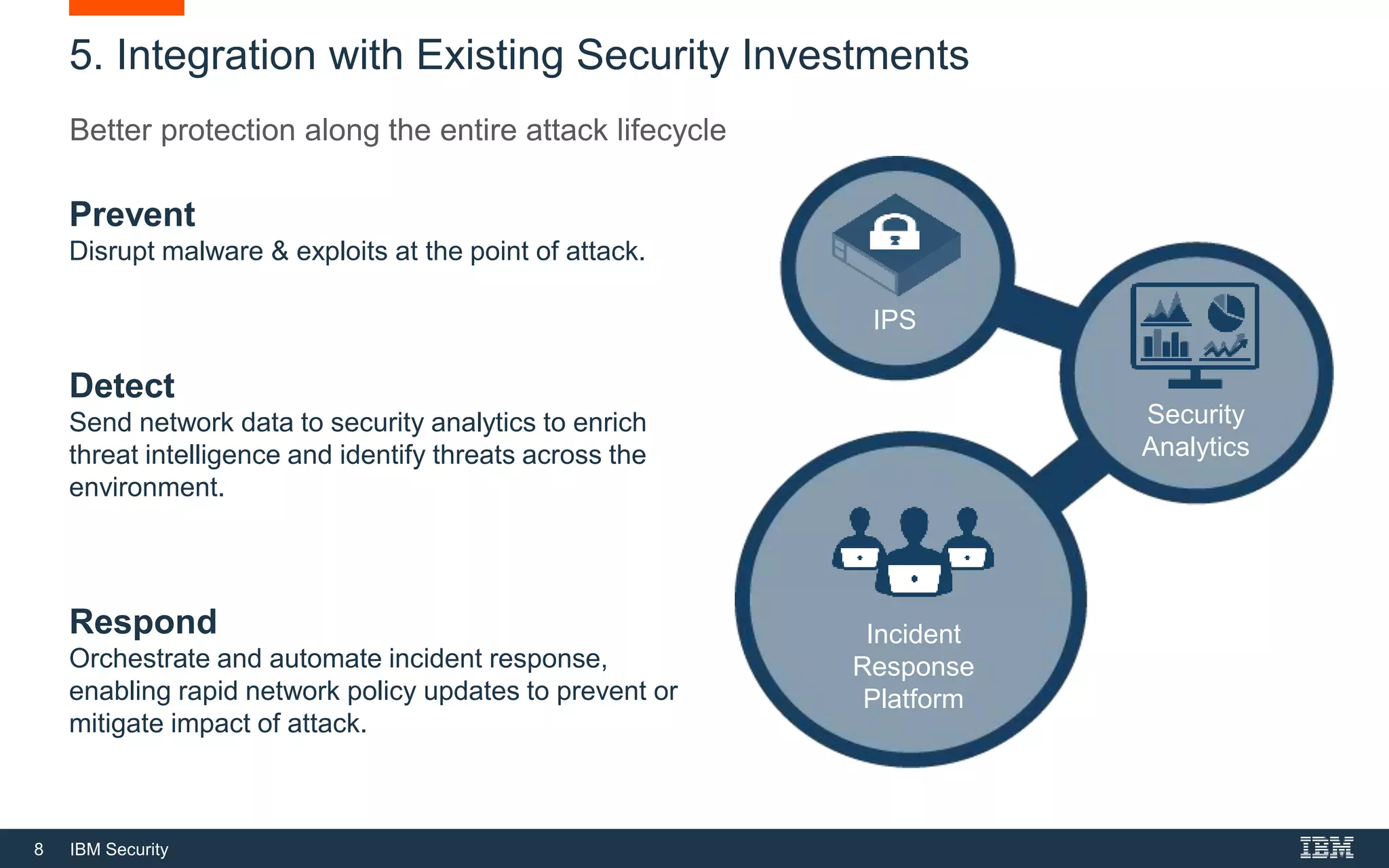
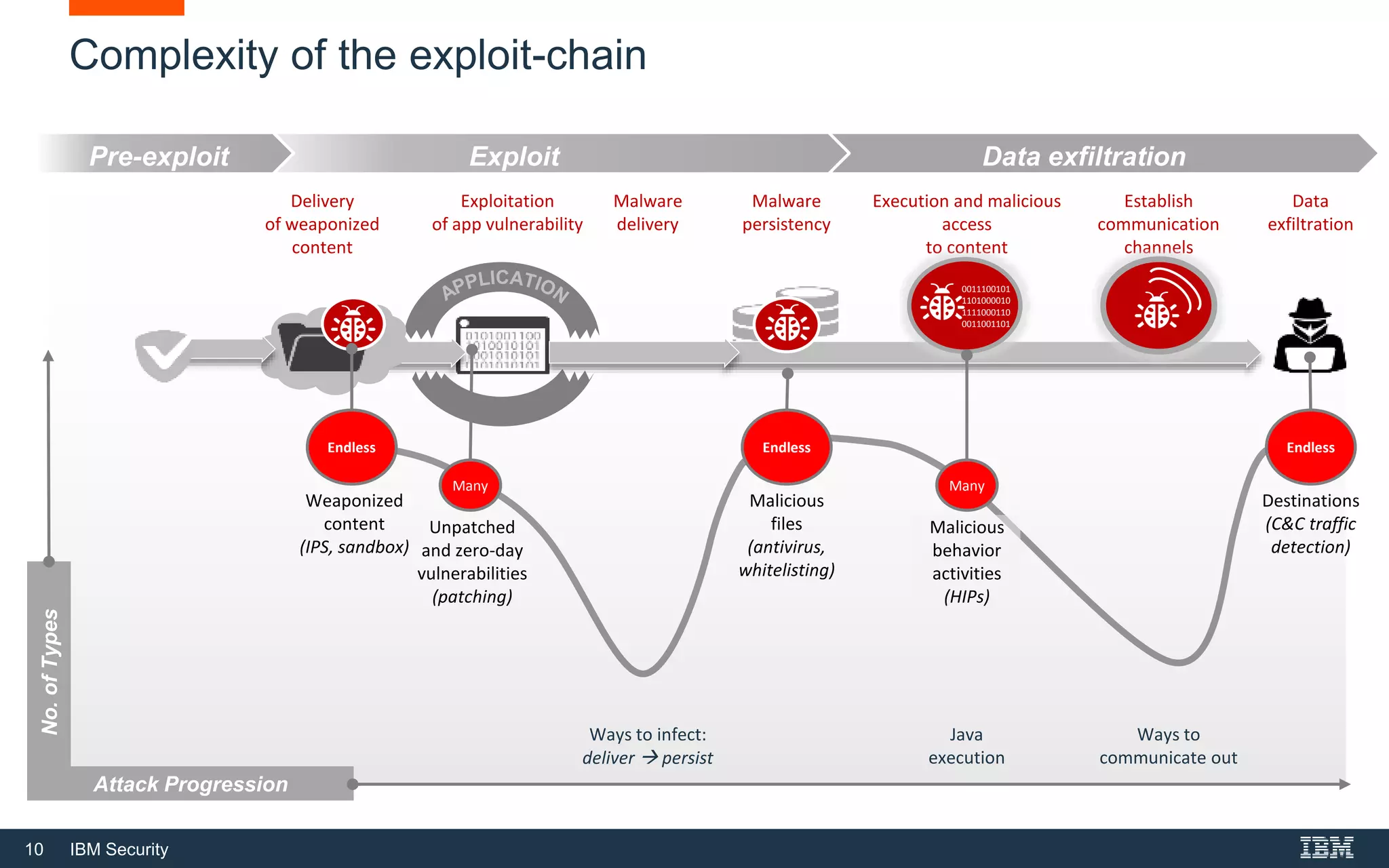
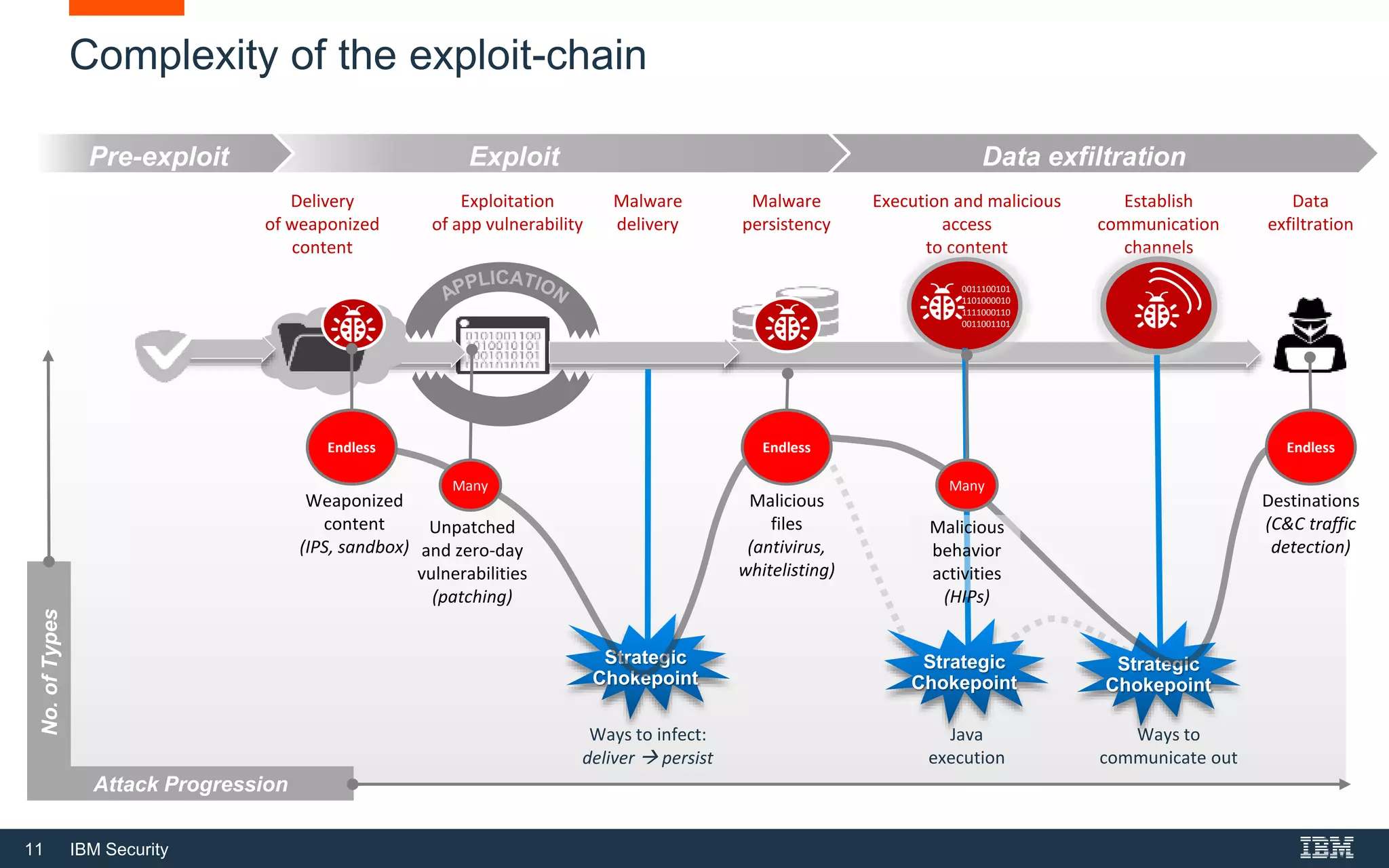
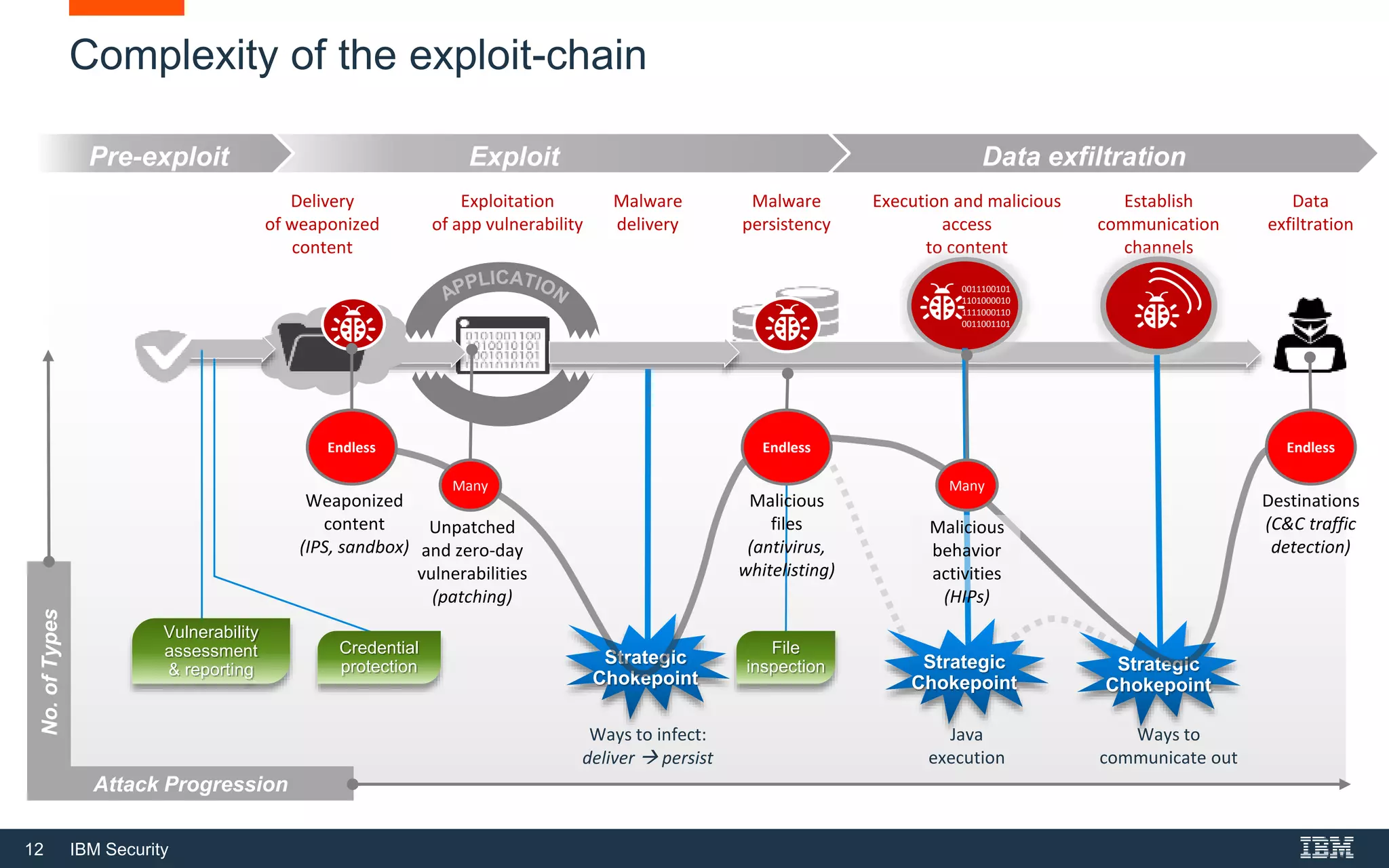
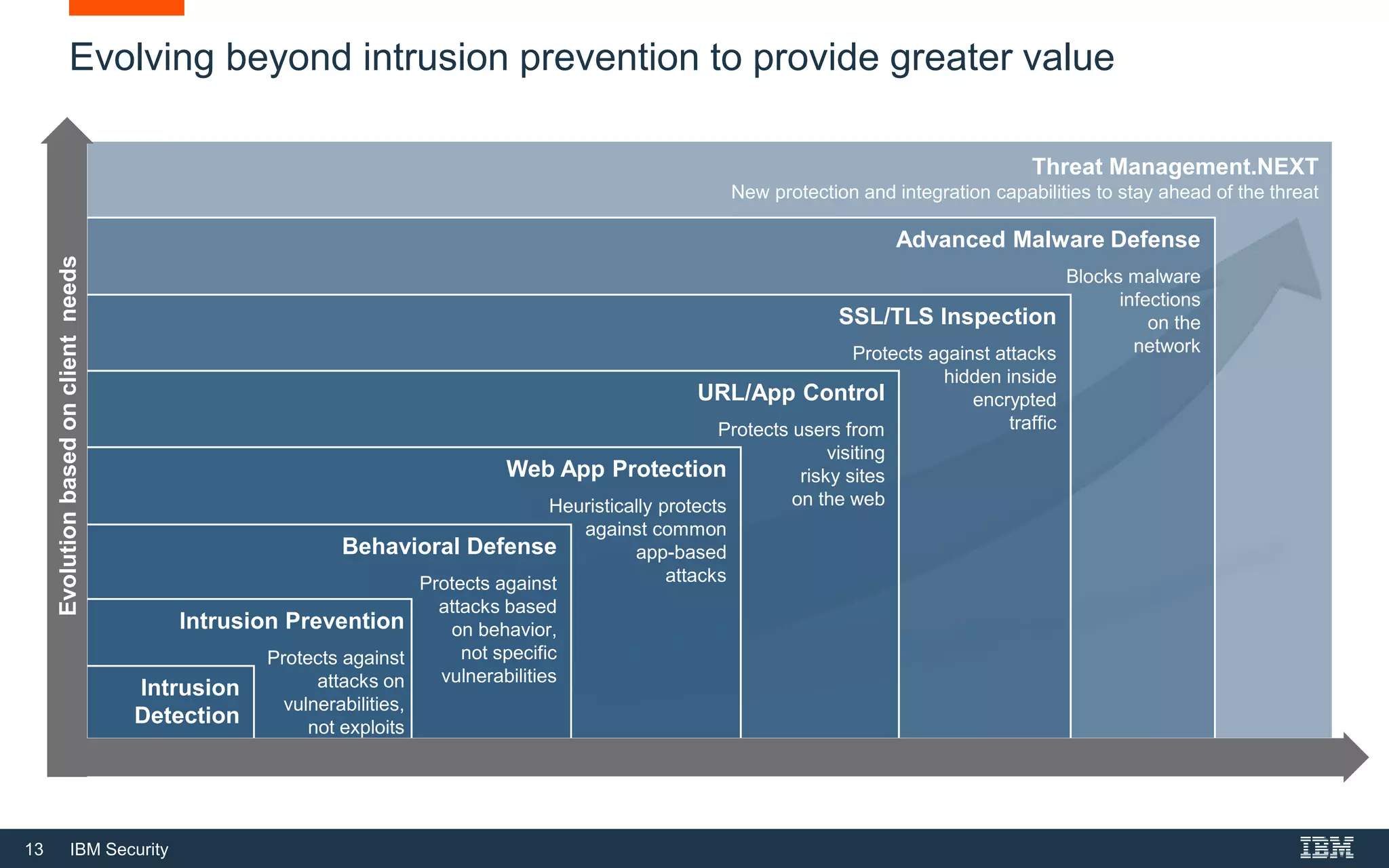
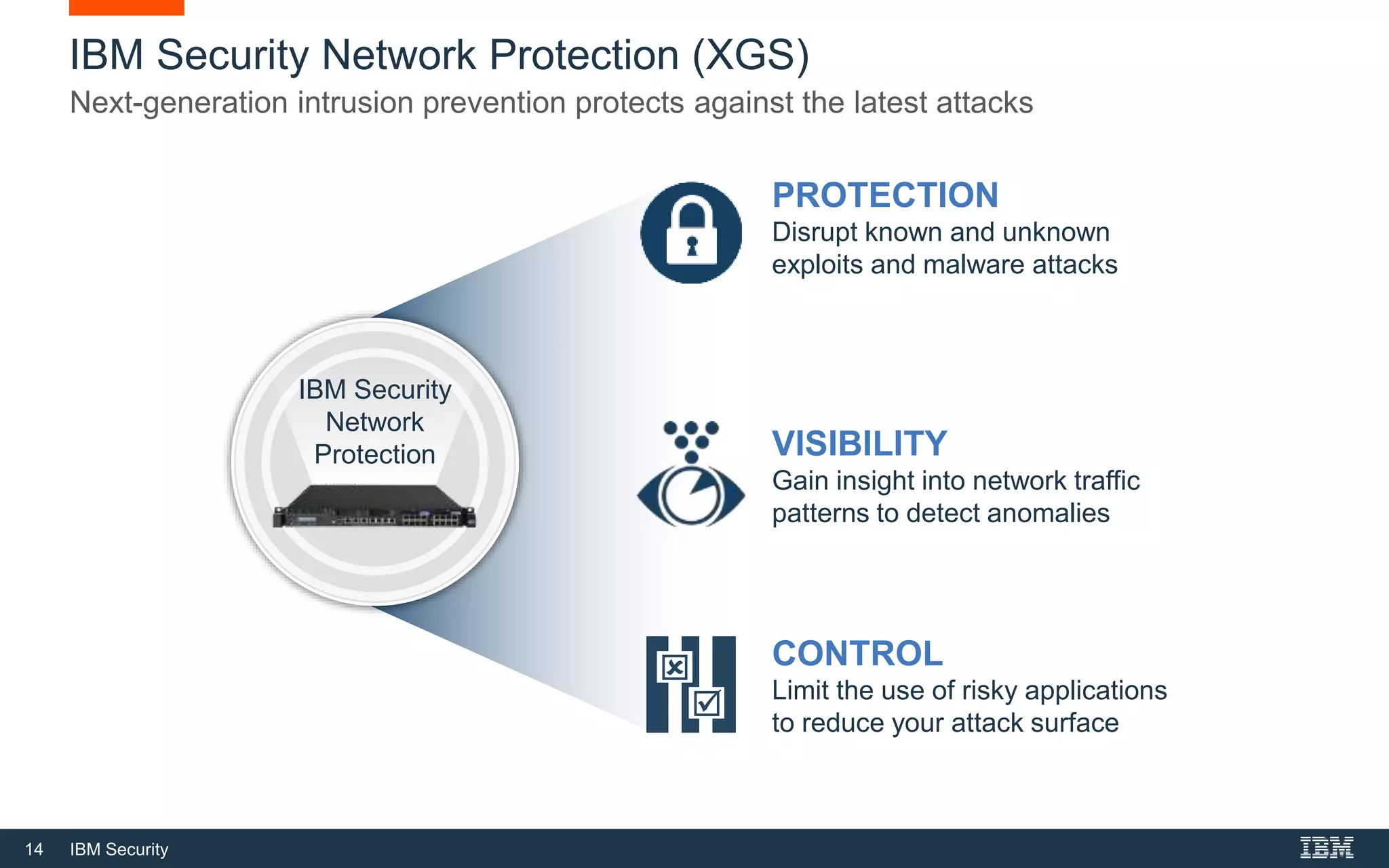
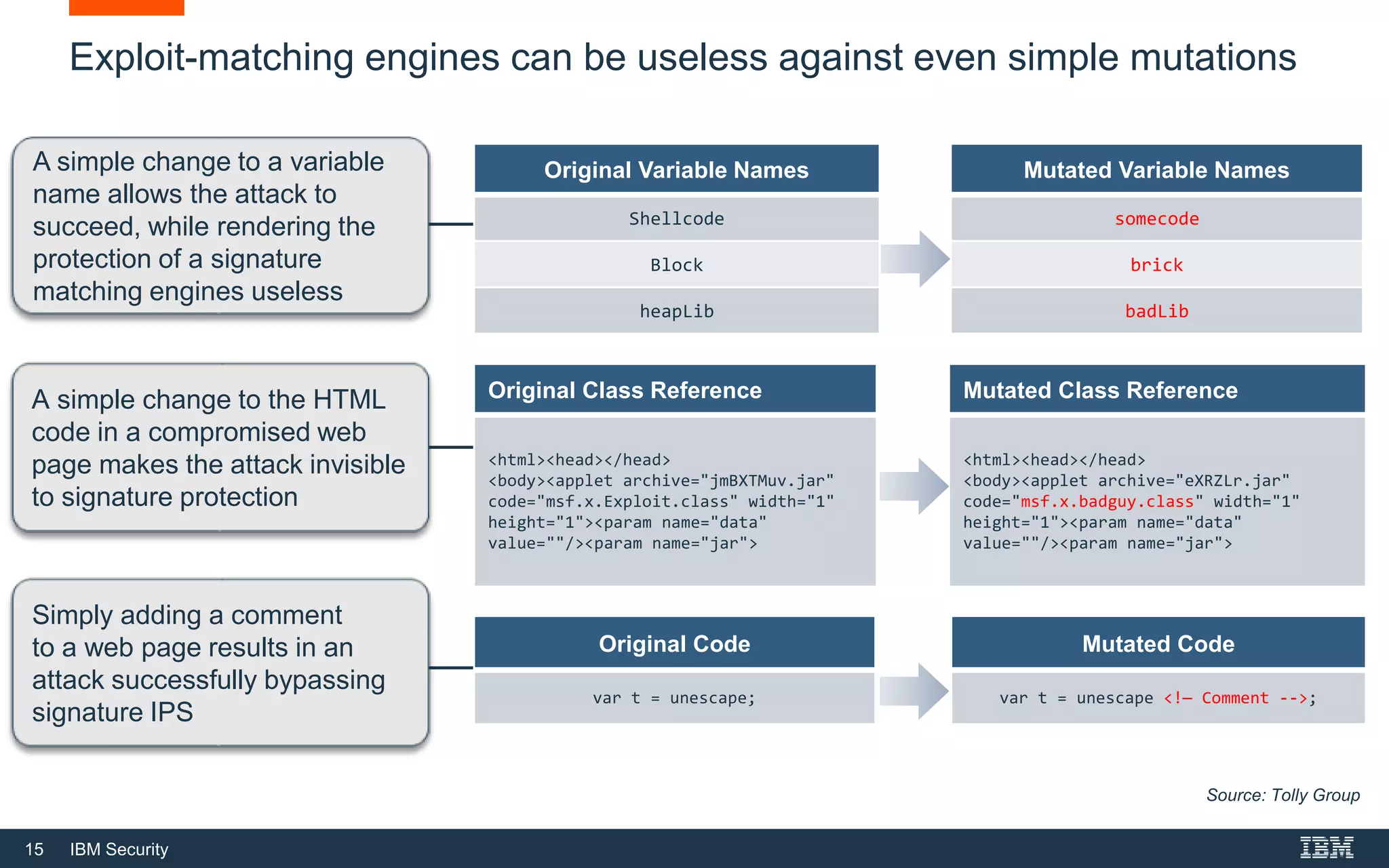
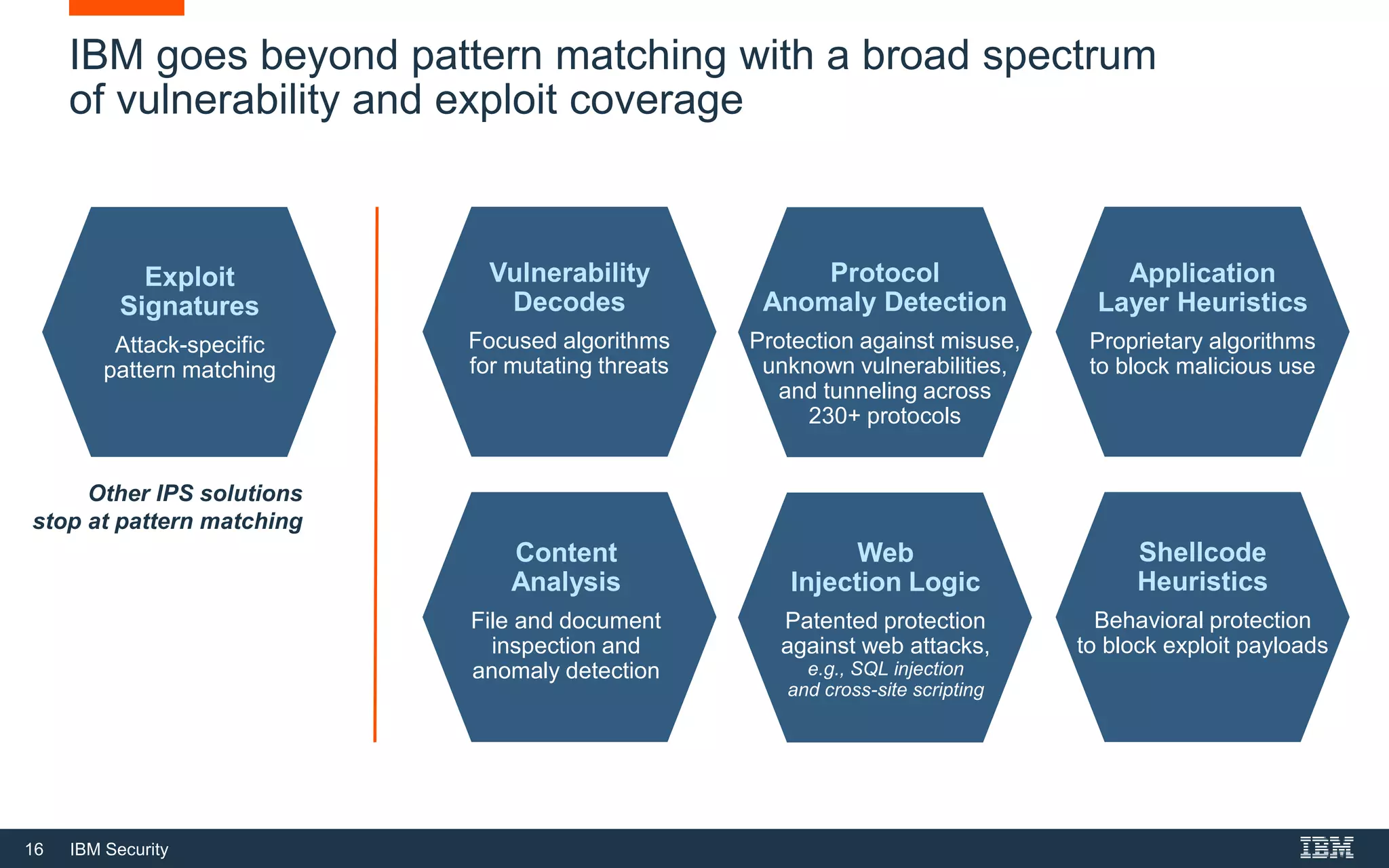
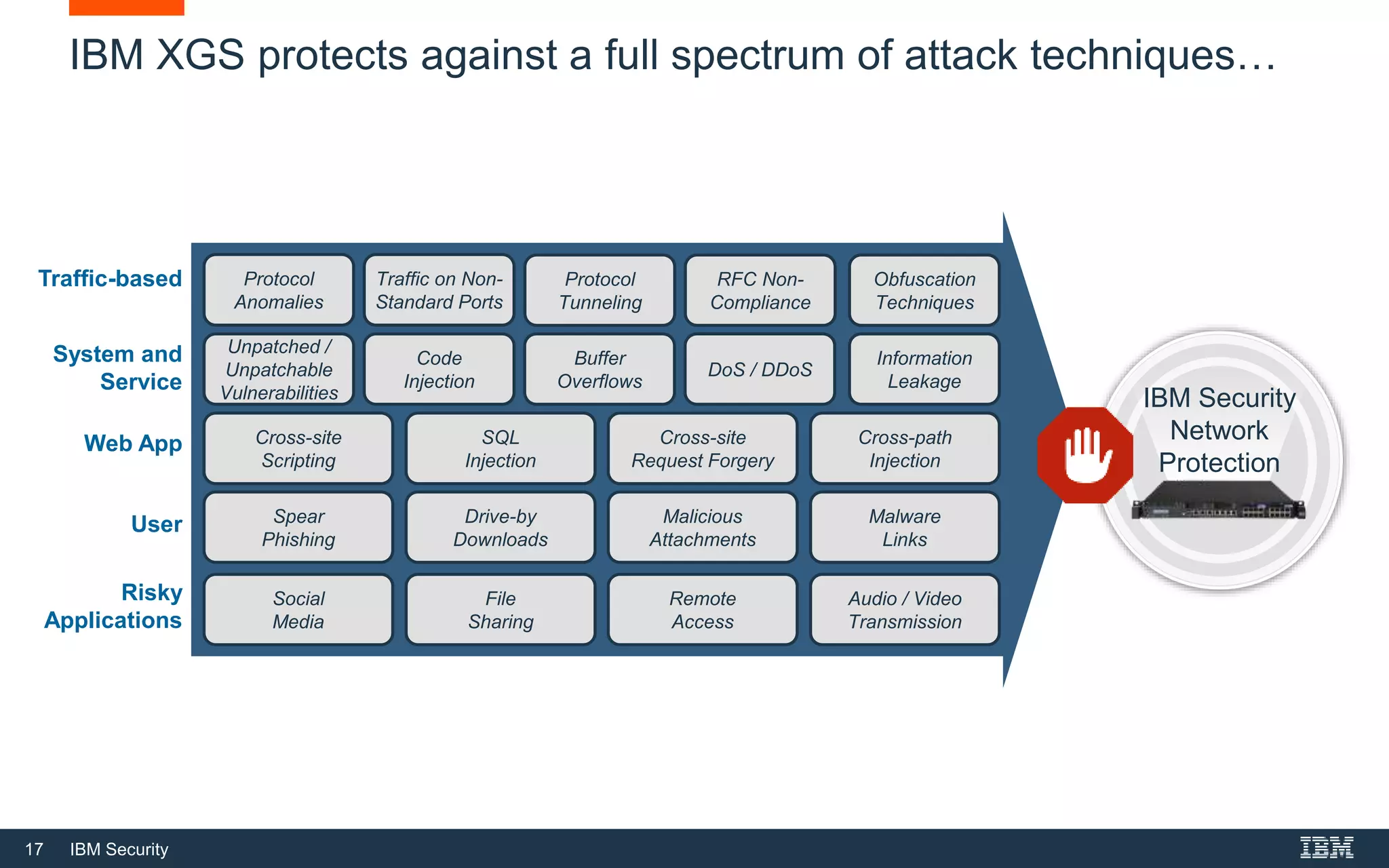
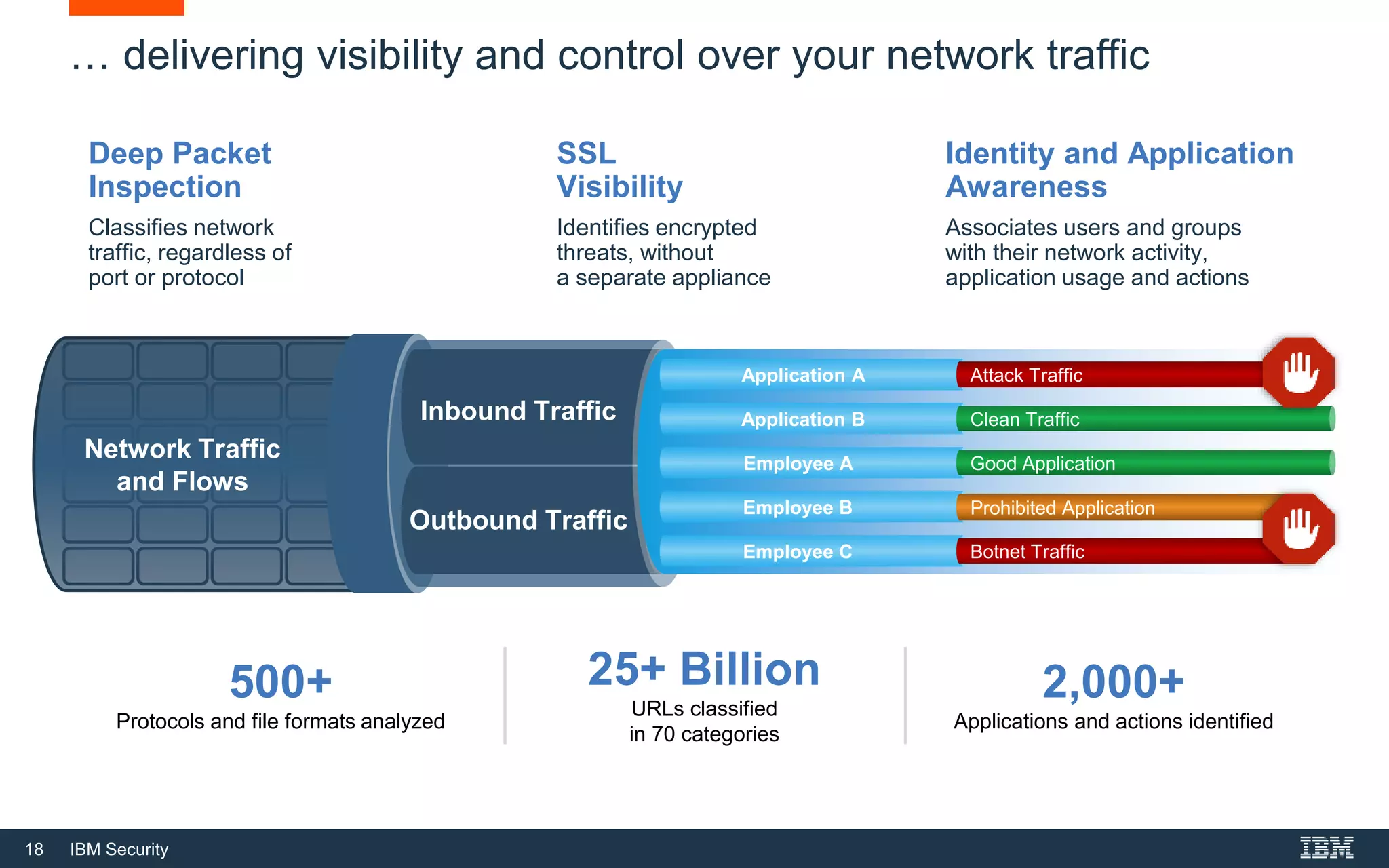
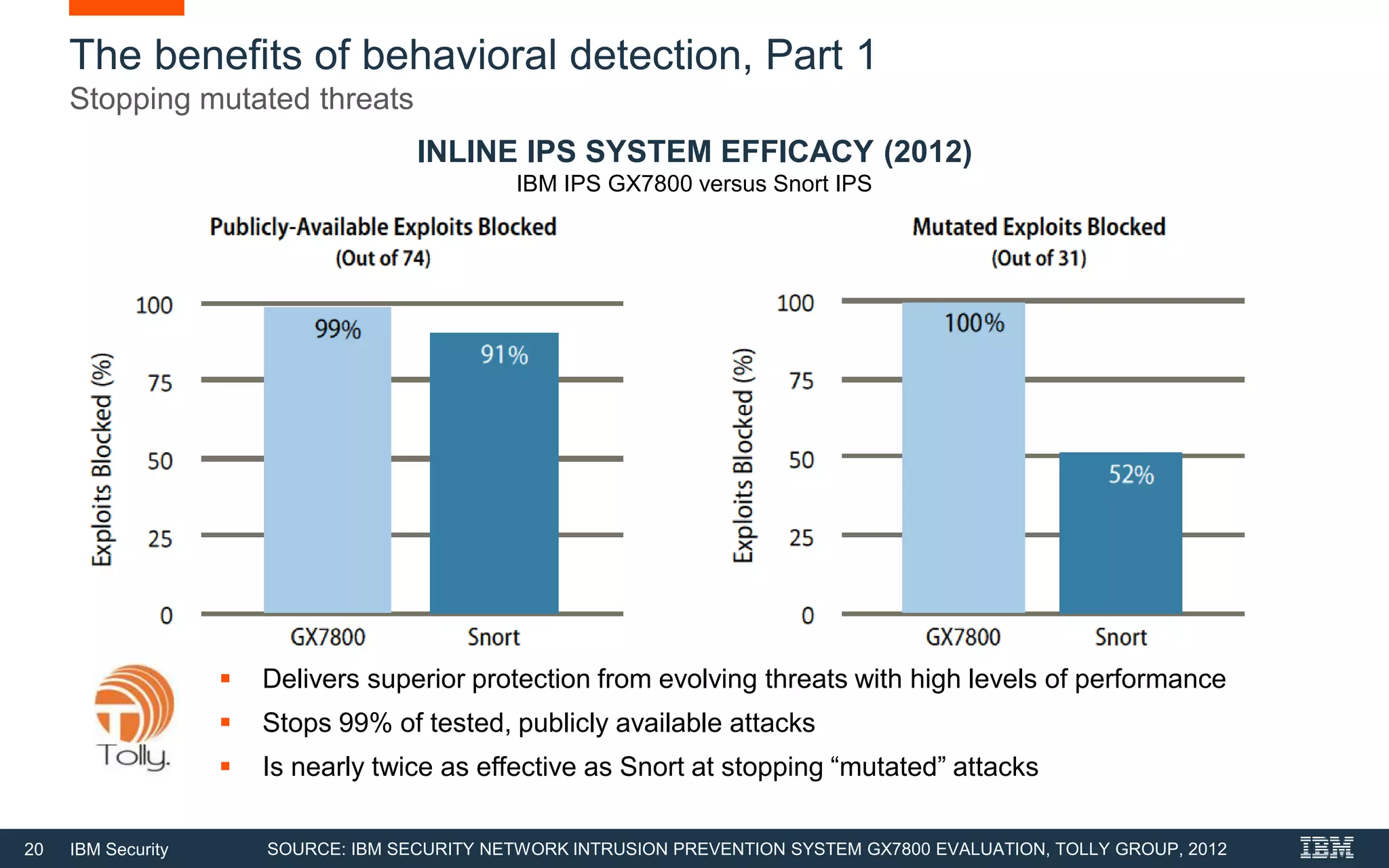
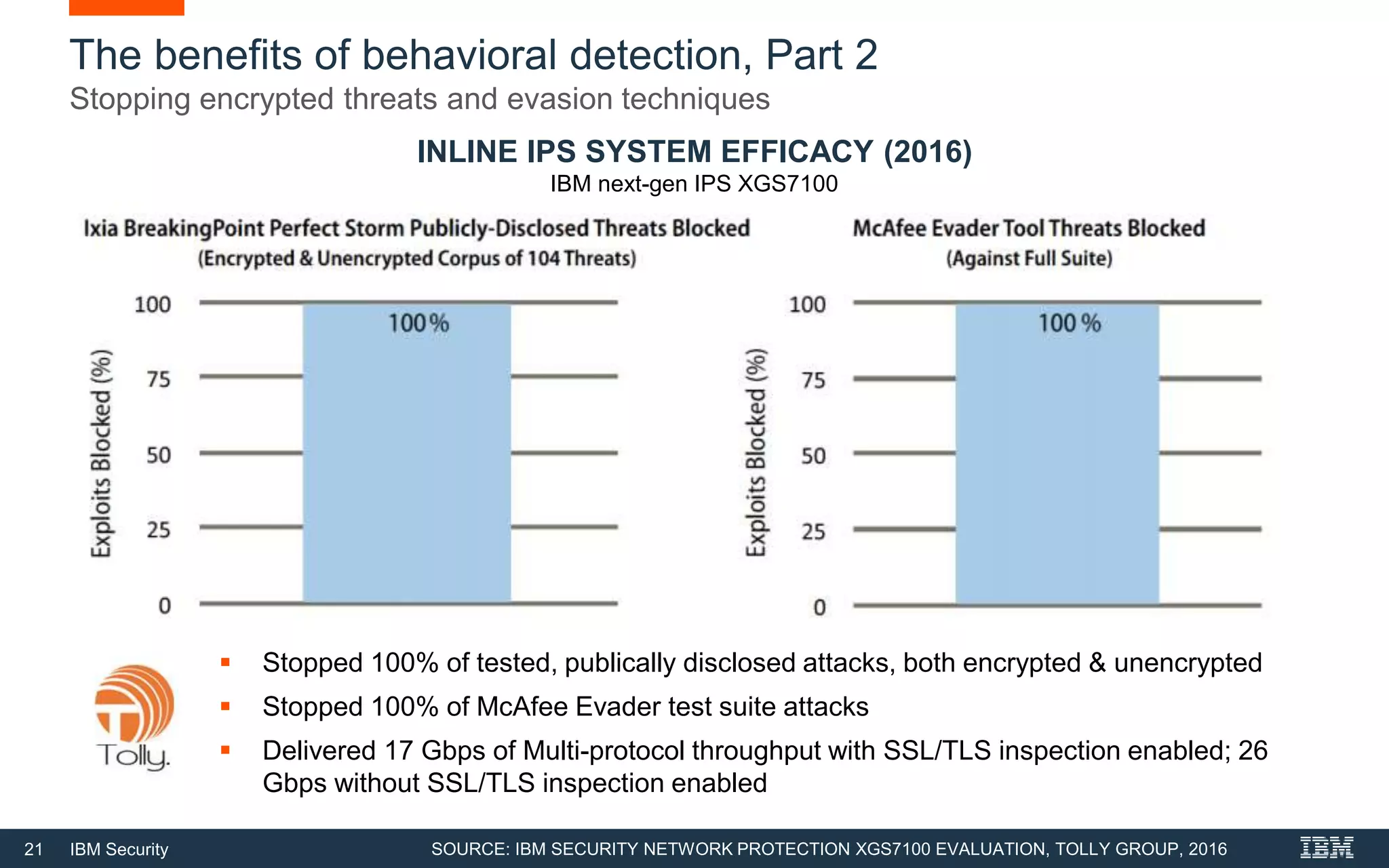
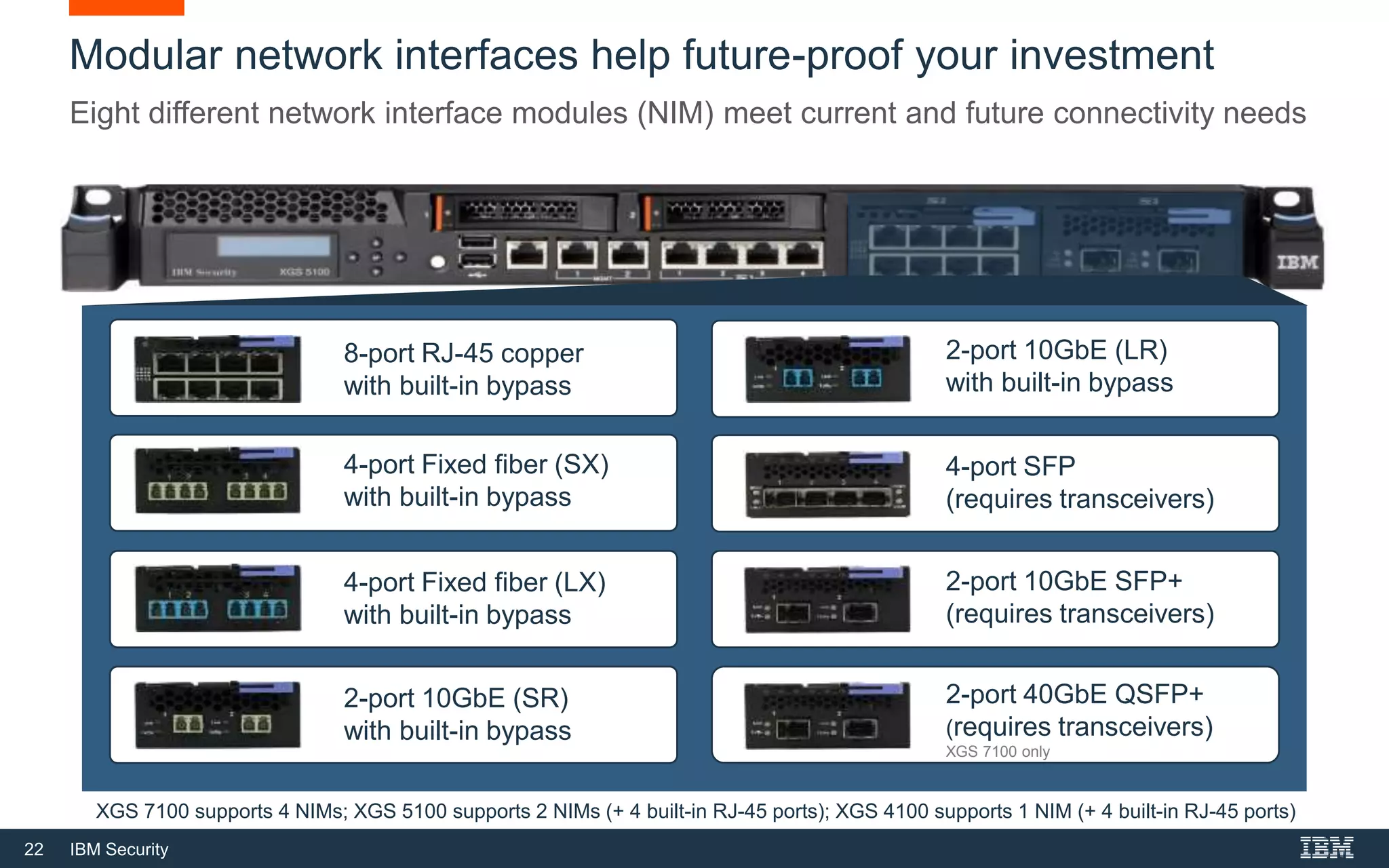
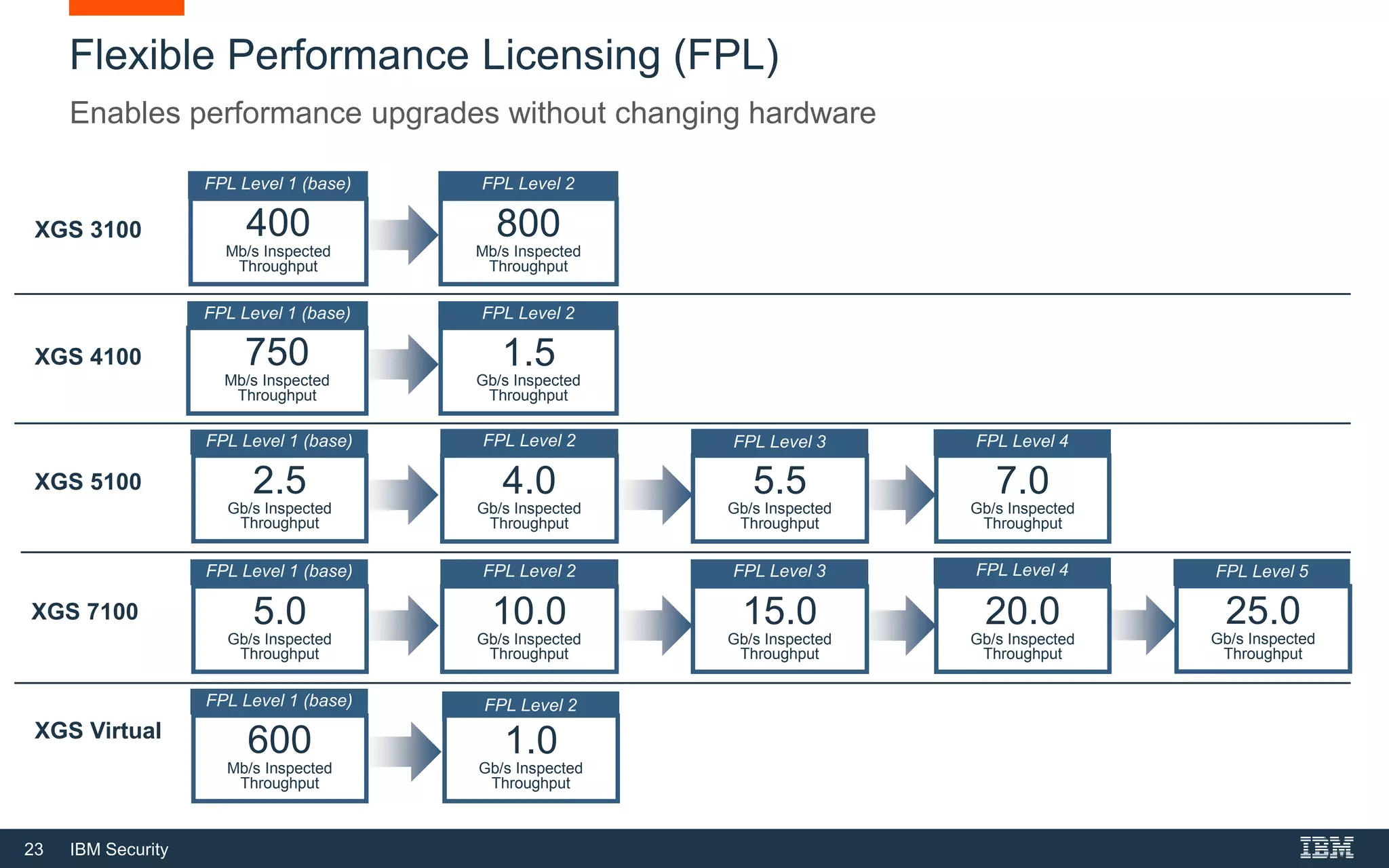
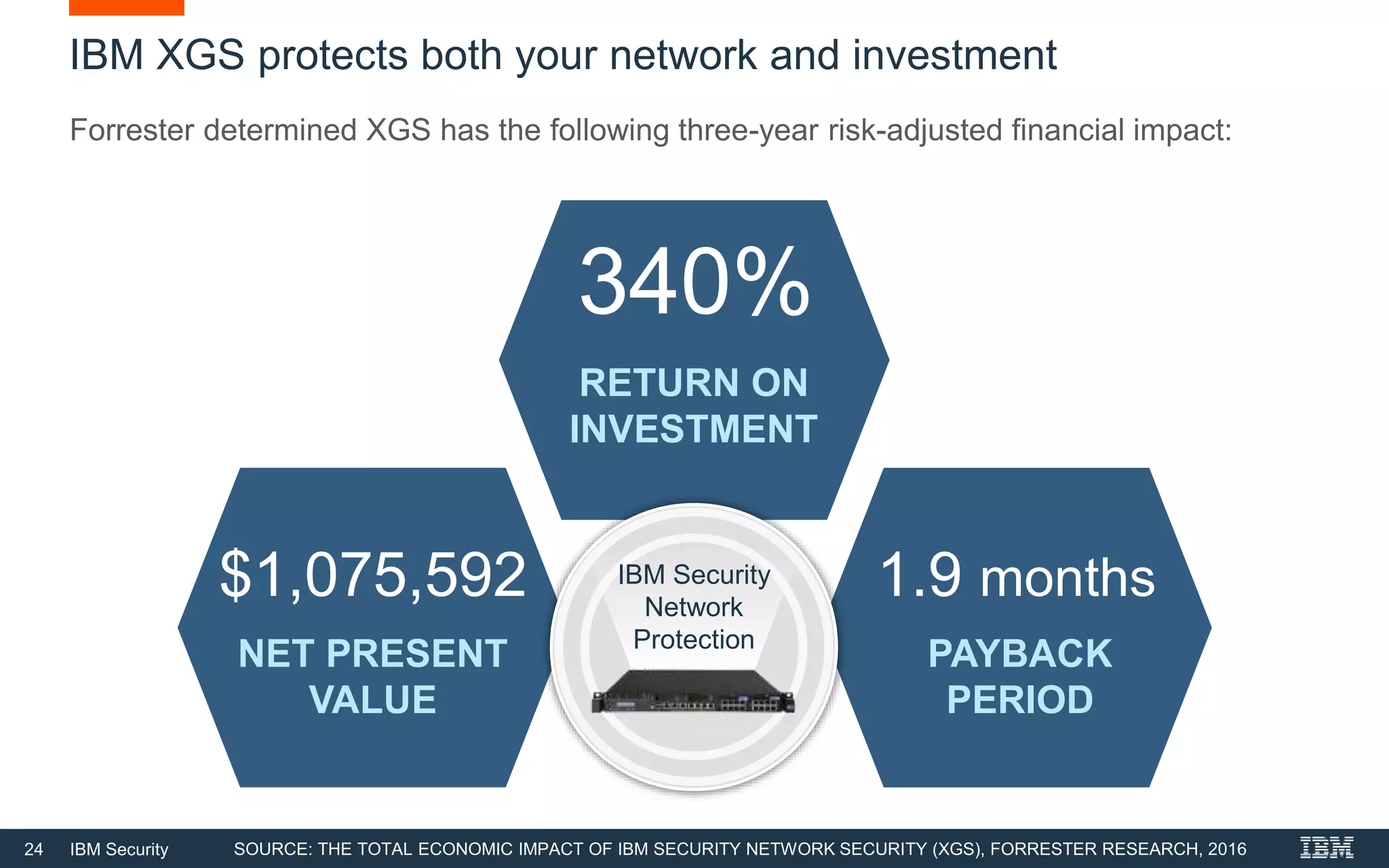
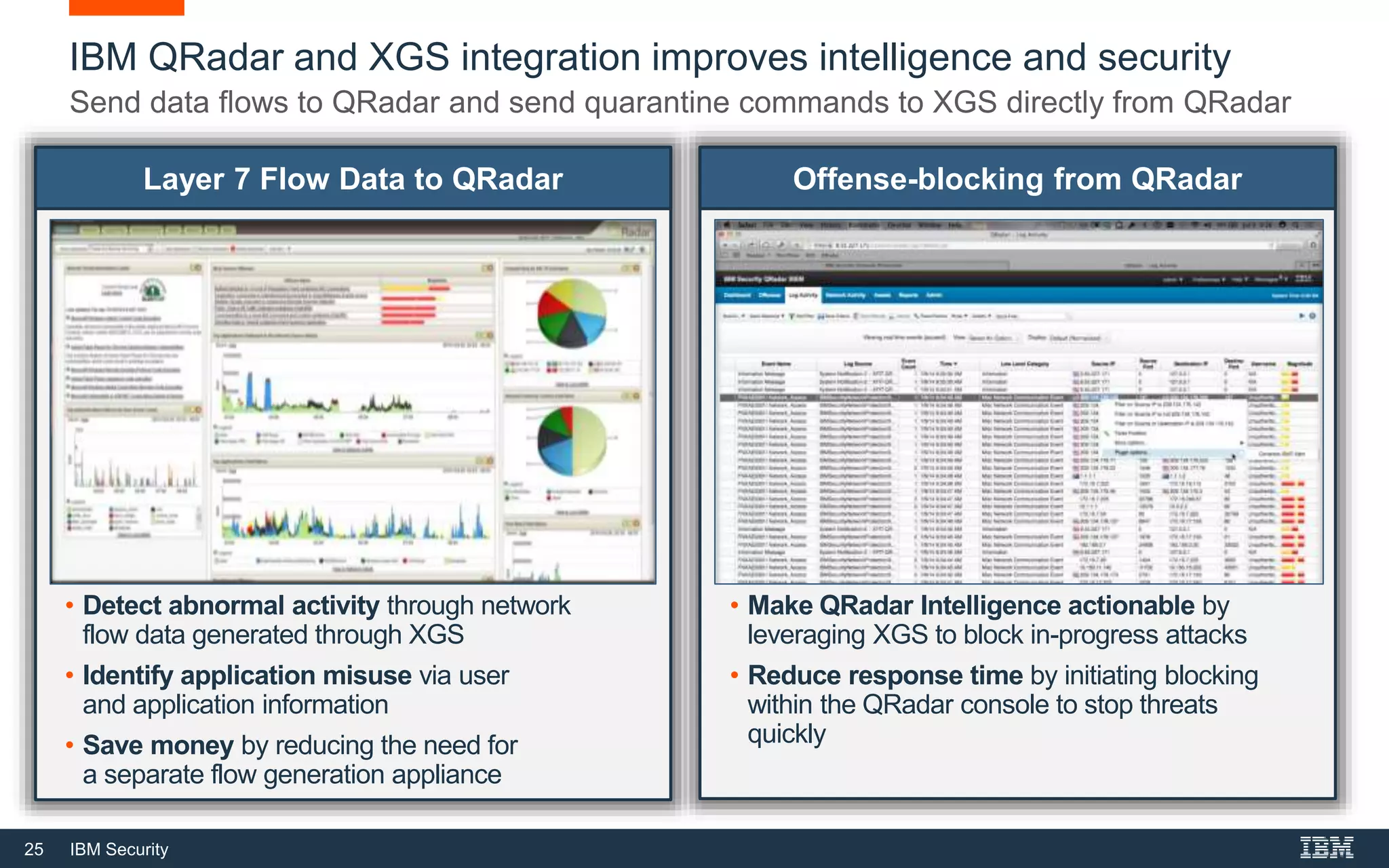
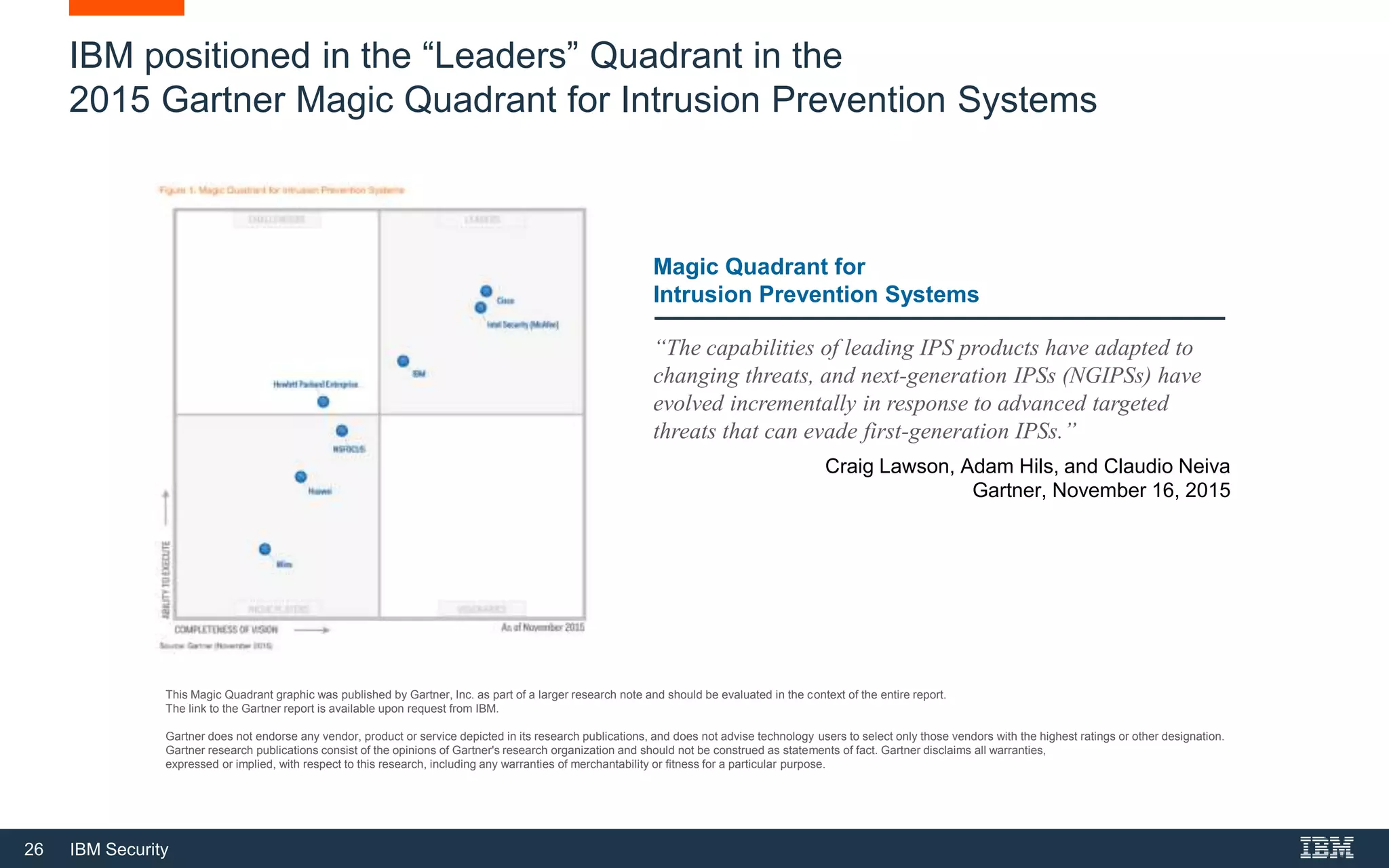
The document discusses top 5 things to look for in an intrusion prevention system (IPS) solution and how IBM's next-generation IPS addresses these areas. It recommends looking for 1) behavioral threat detection methods, 2) granular application and user controls, 3) fast encrypted traffic inspection, 4) flexible performance options like Field Programmable Gate Arrays (FPGAs) and modular network interfaces, and 5) integration capabilities with security investments like IBM QRadar. The document claims IBM's next-gen IPS (XGS) provides all of these areas to protect against modern attacks beyond just signature-based methods.