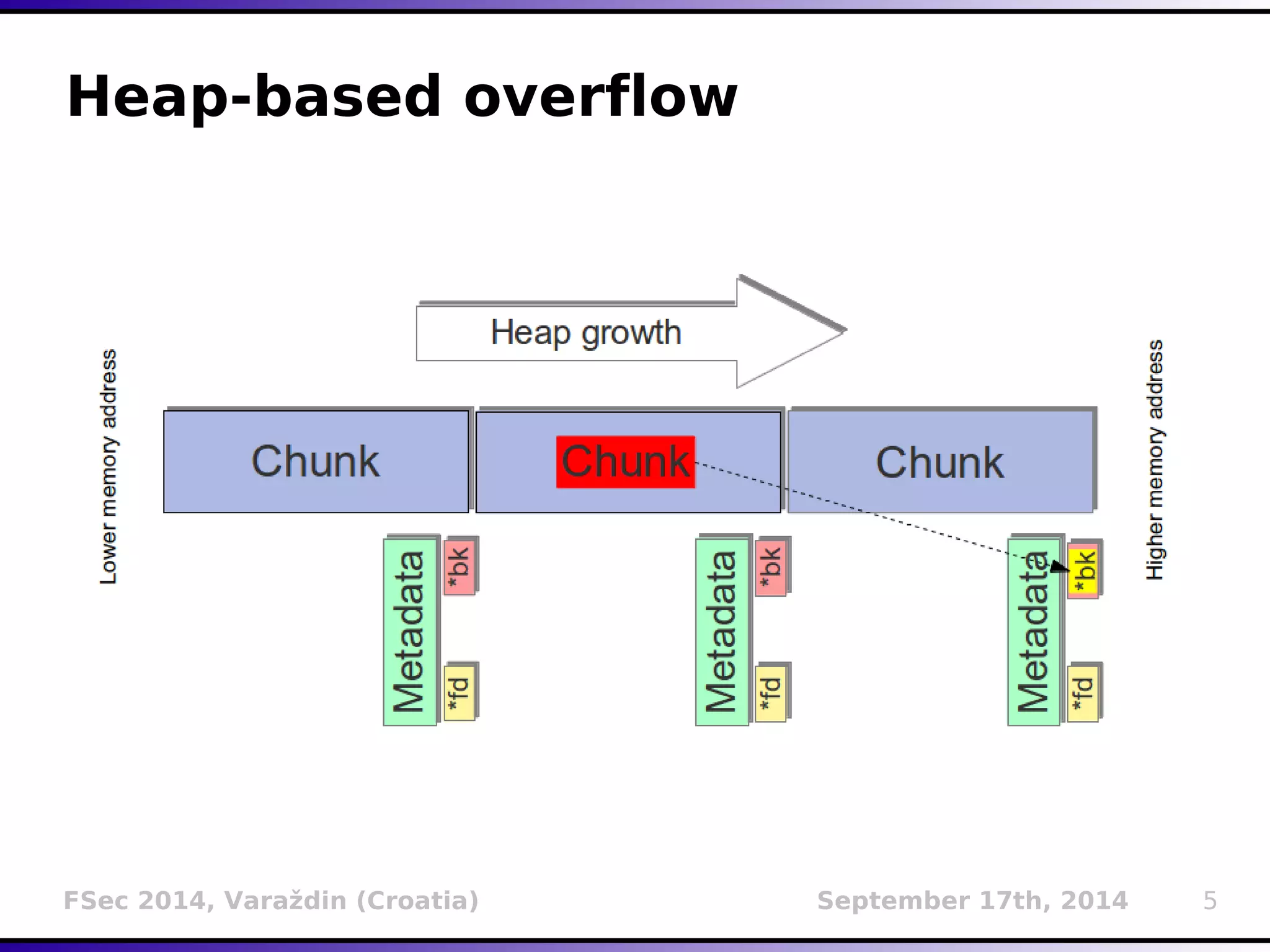
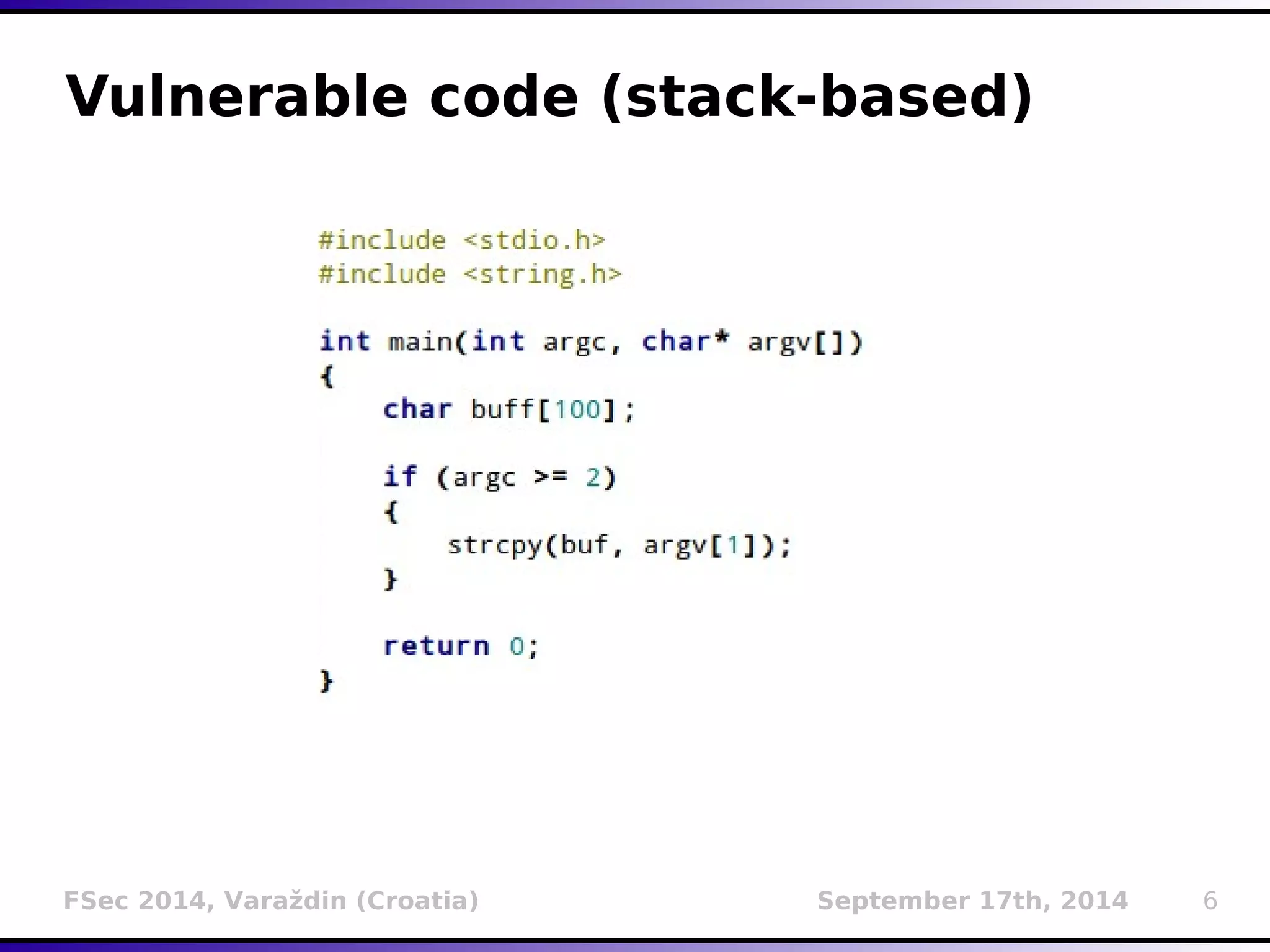
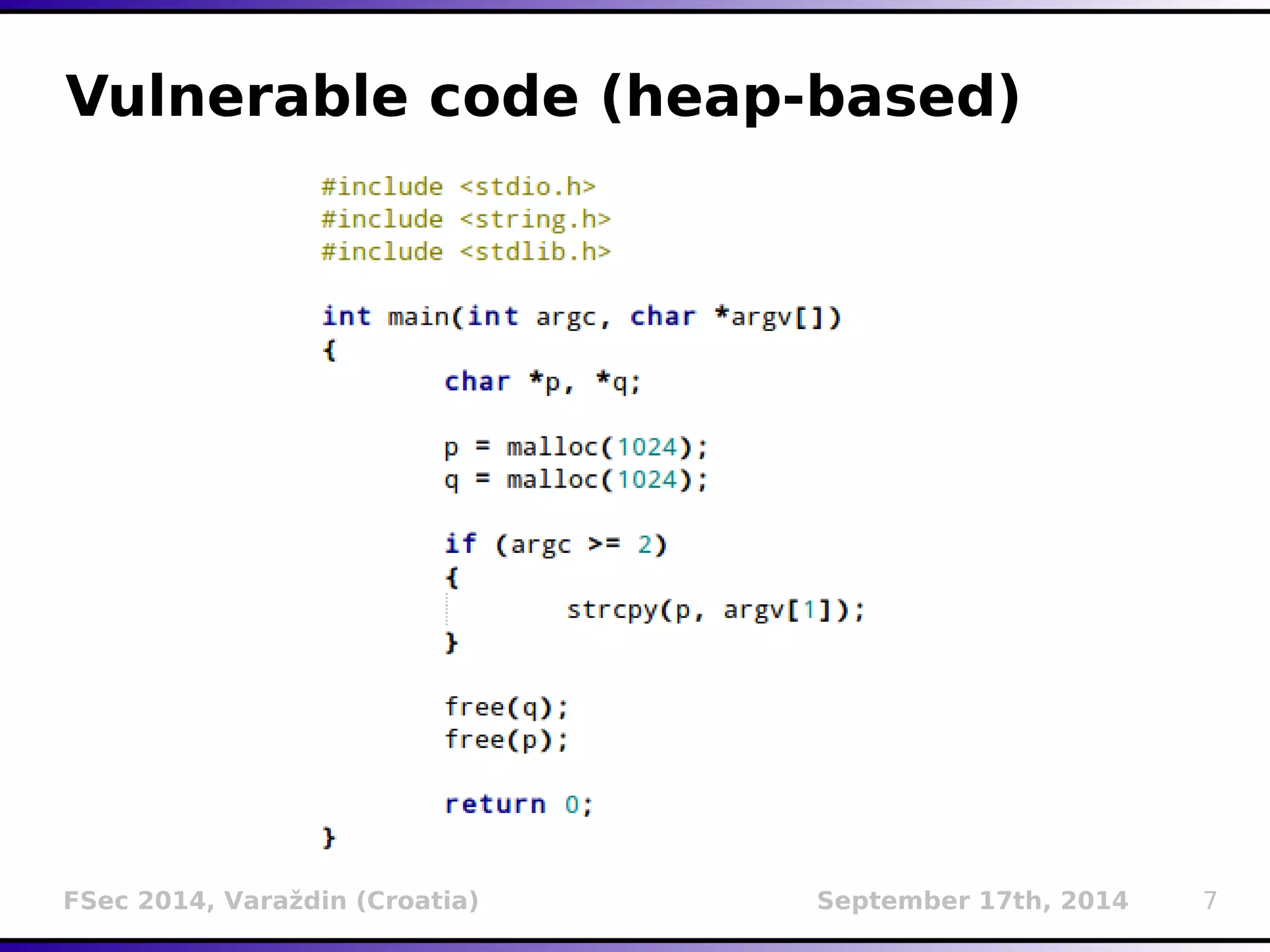
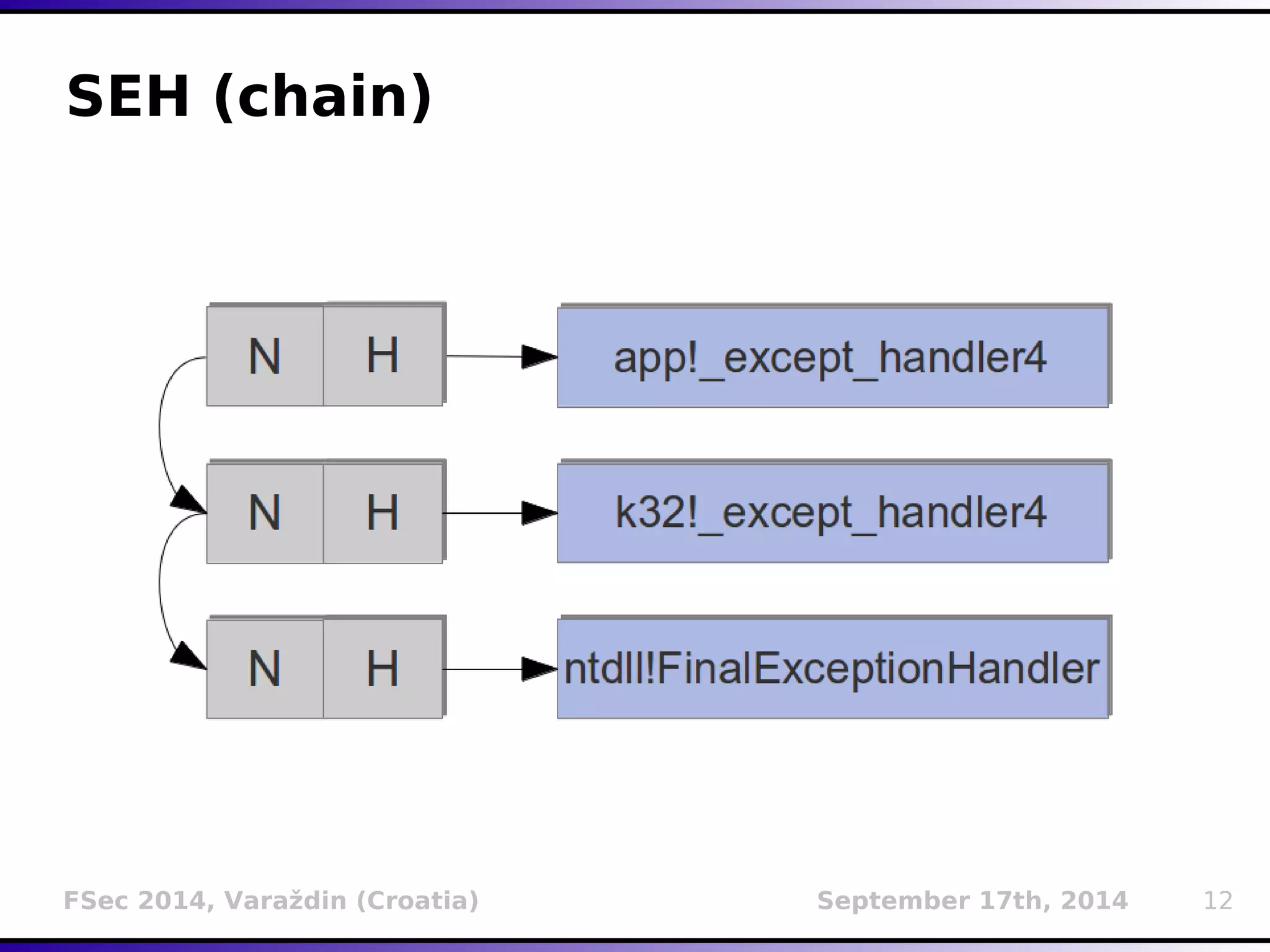
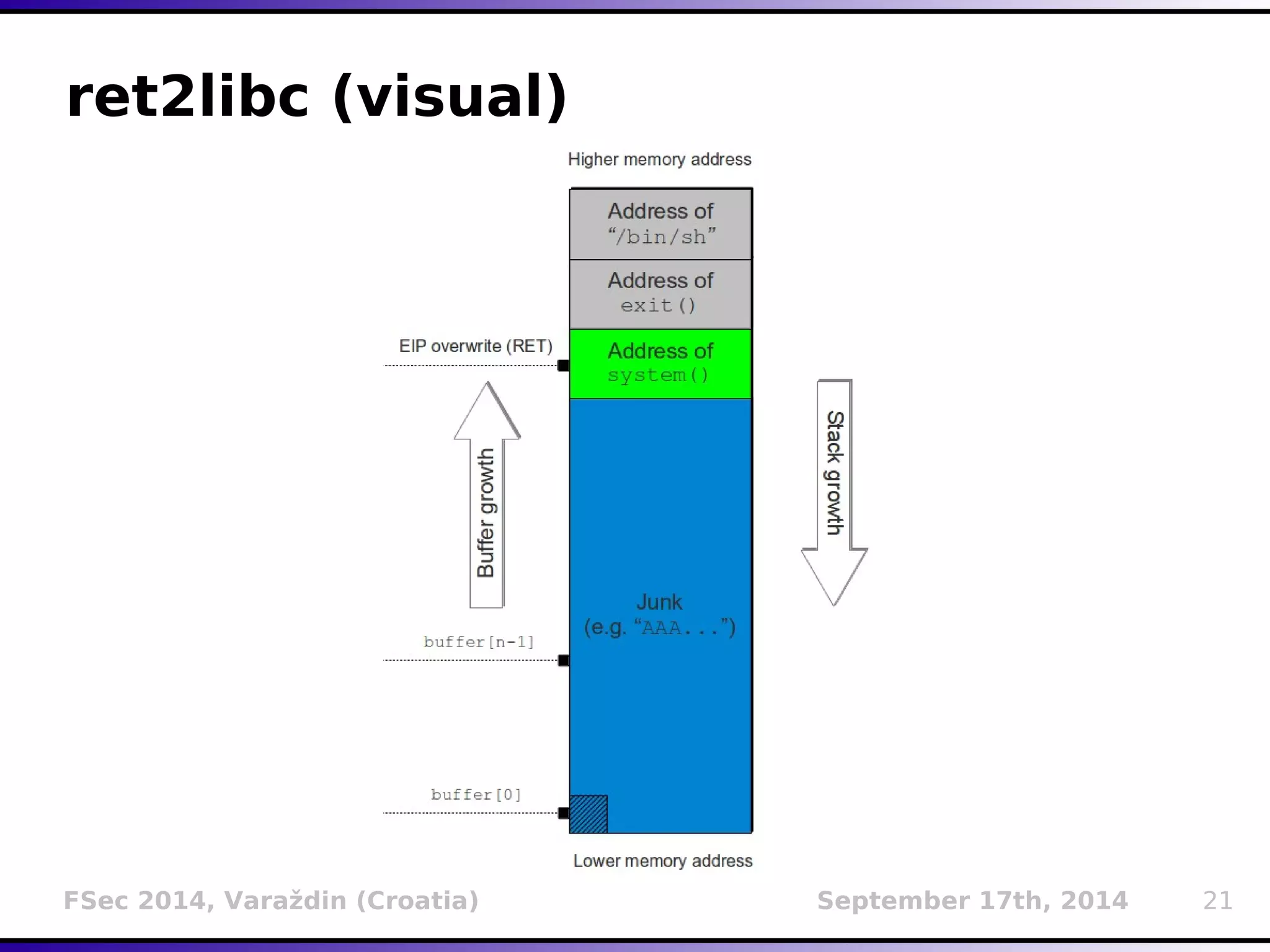
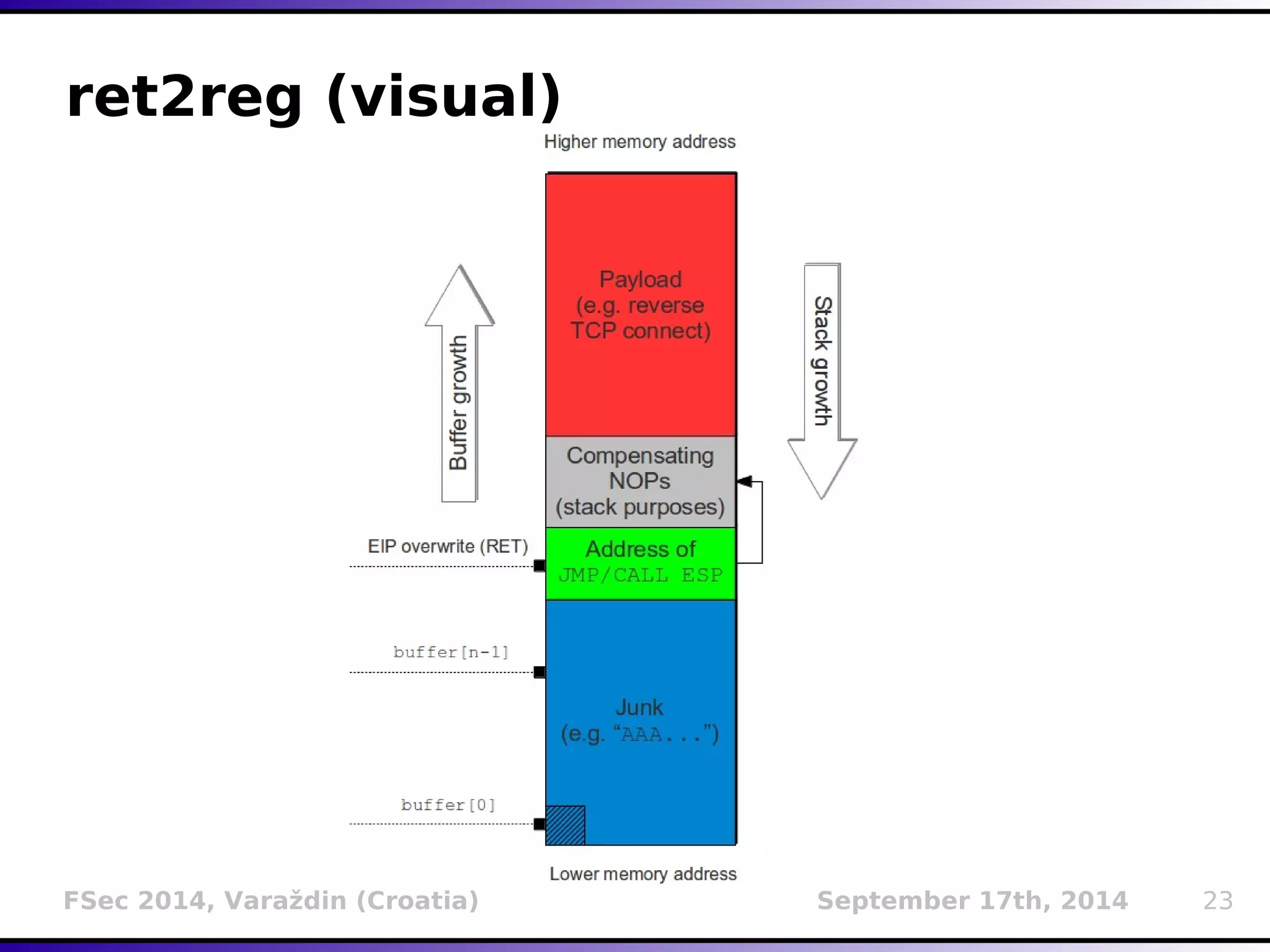
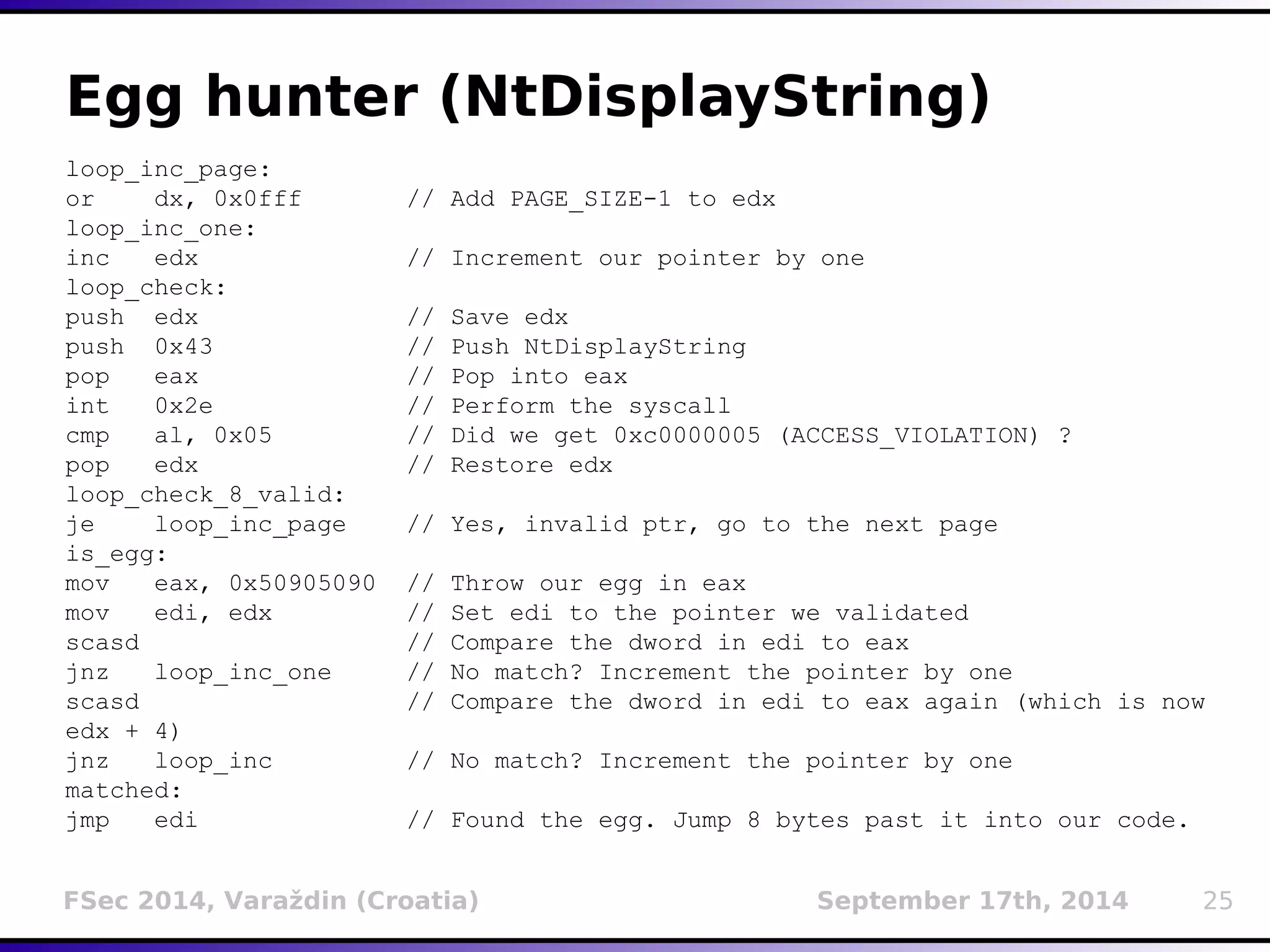
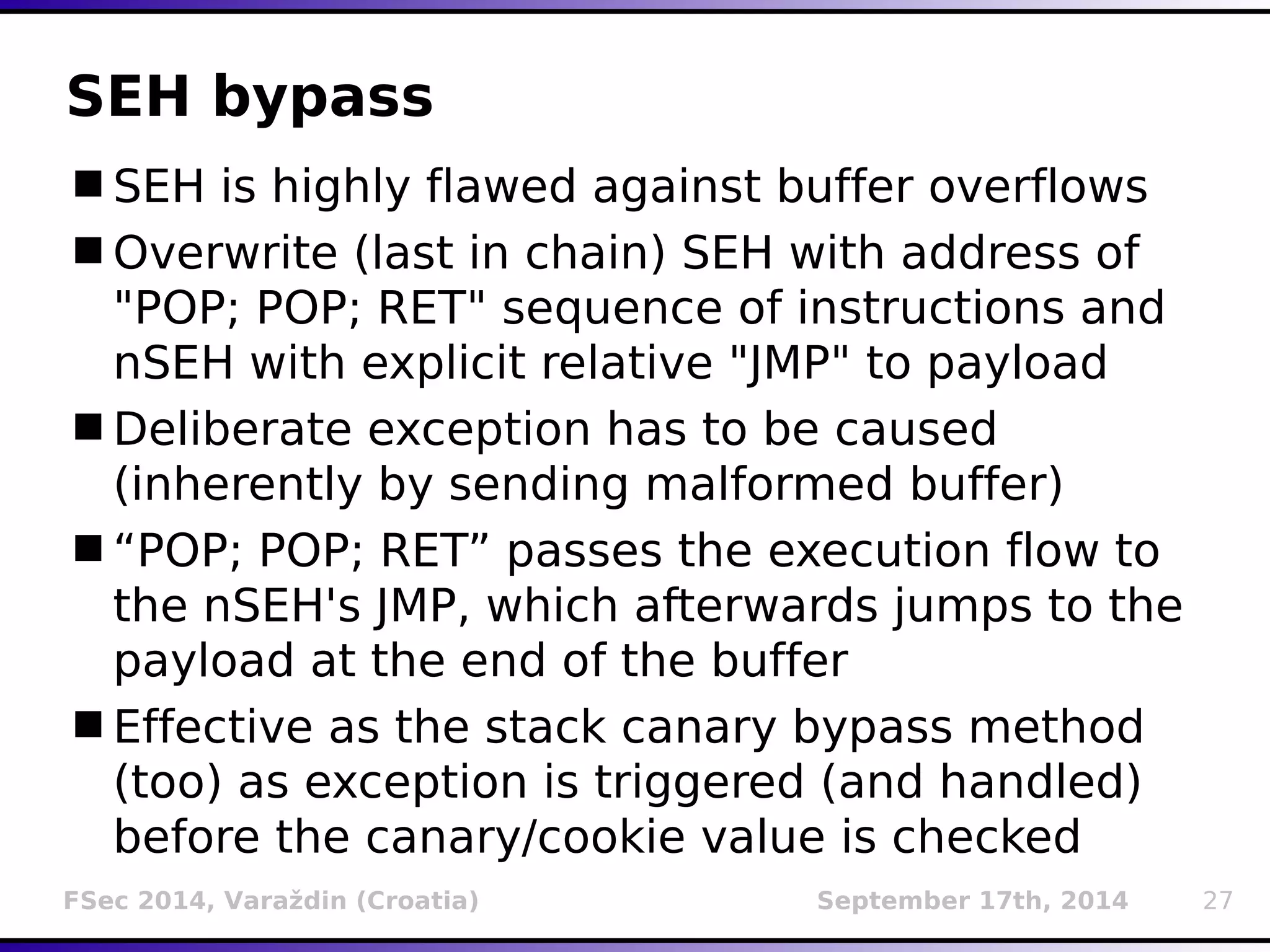
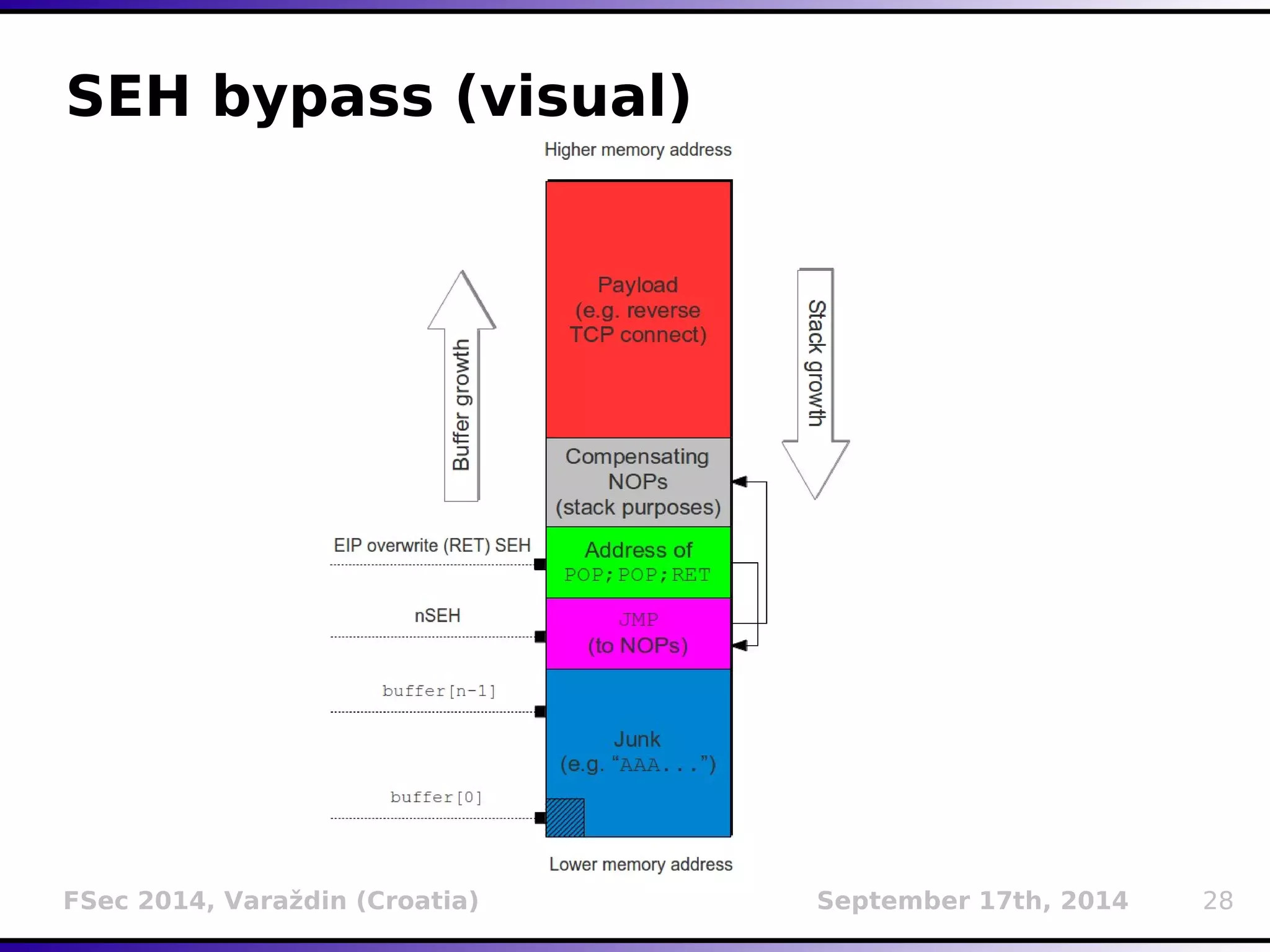
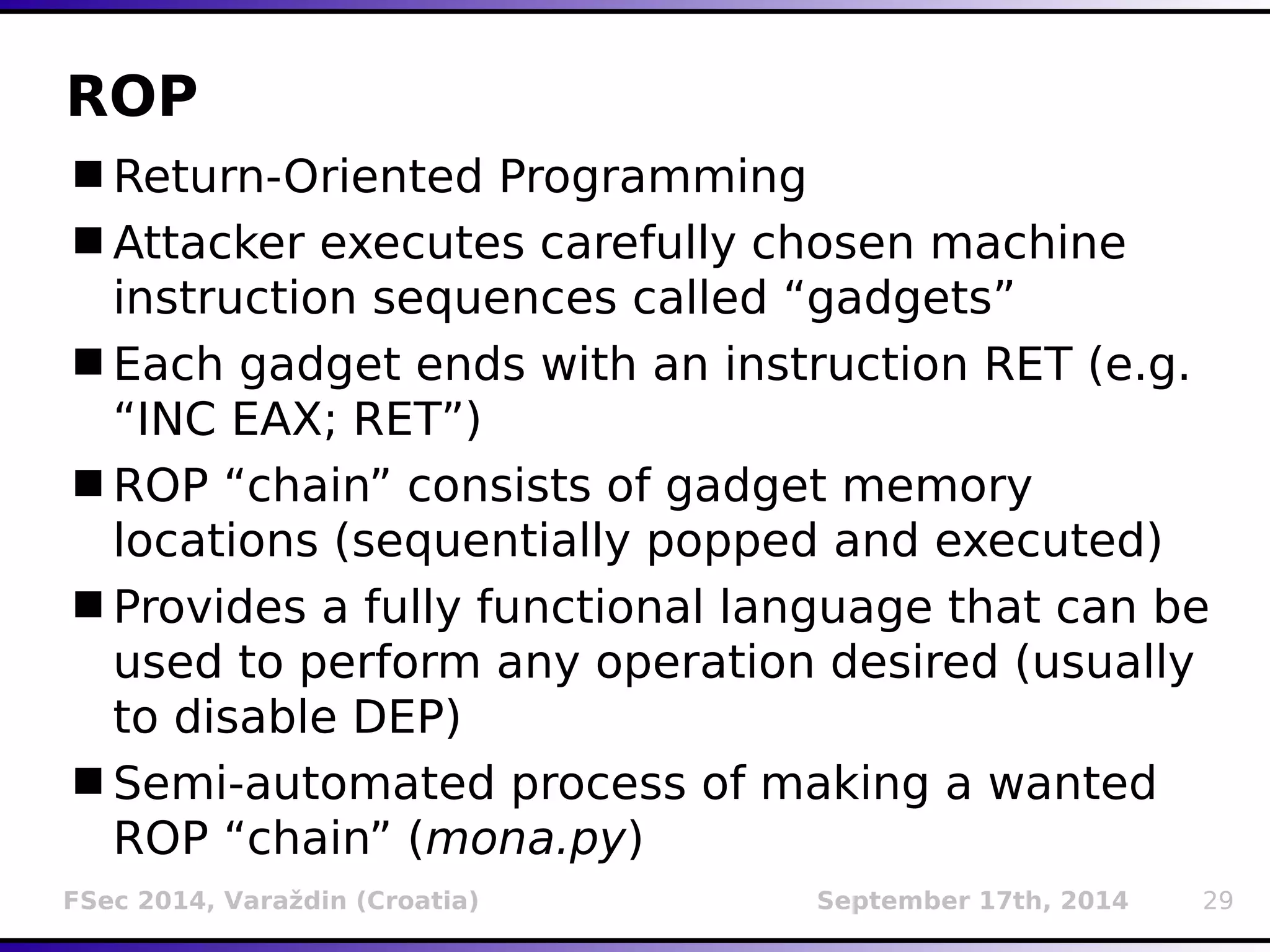
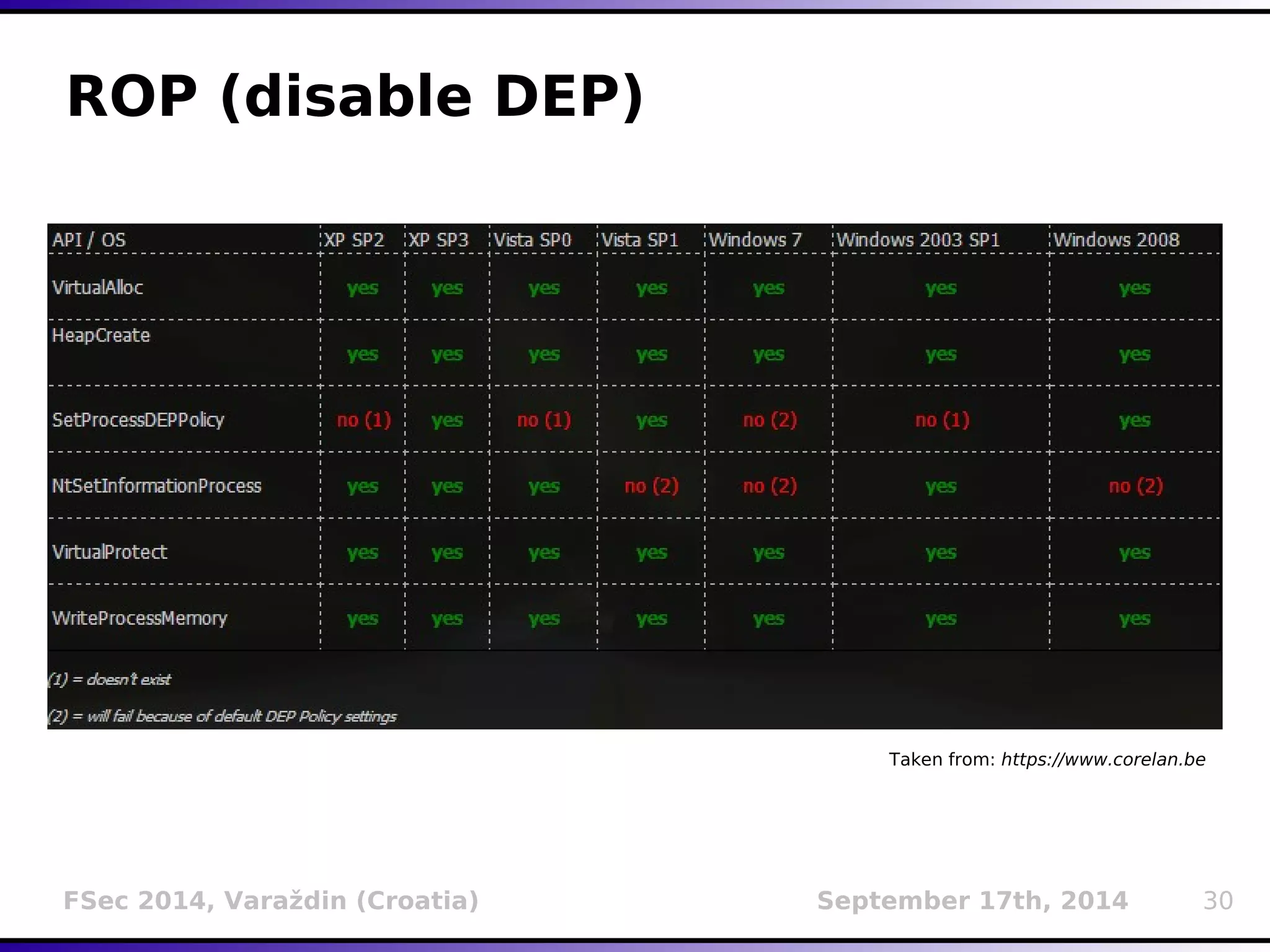
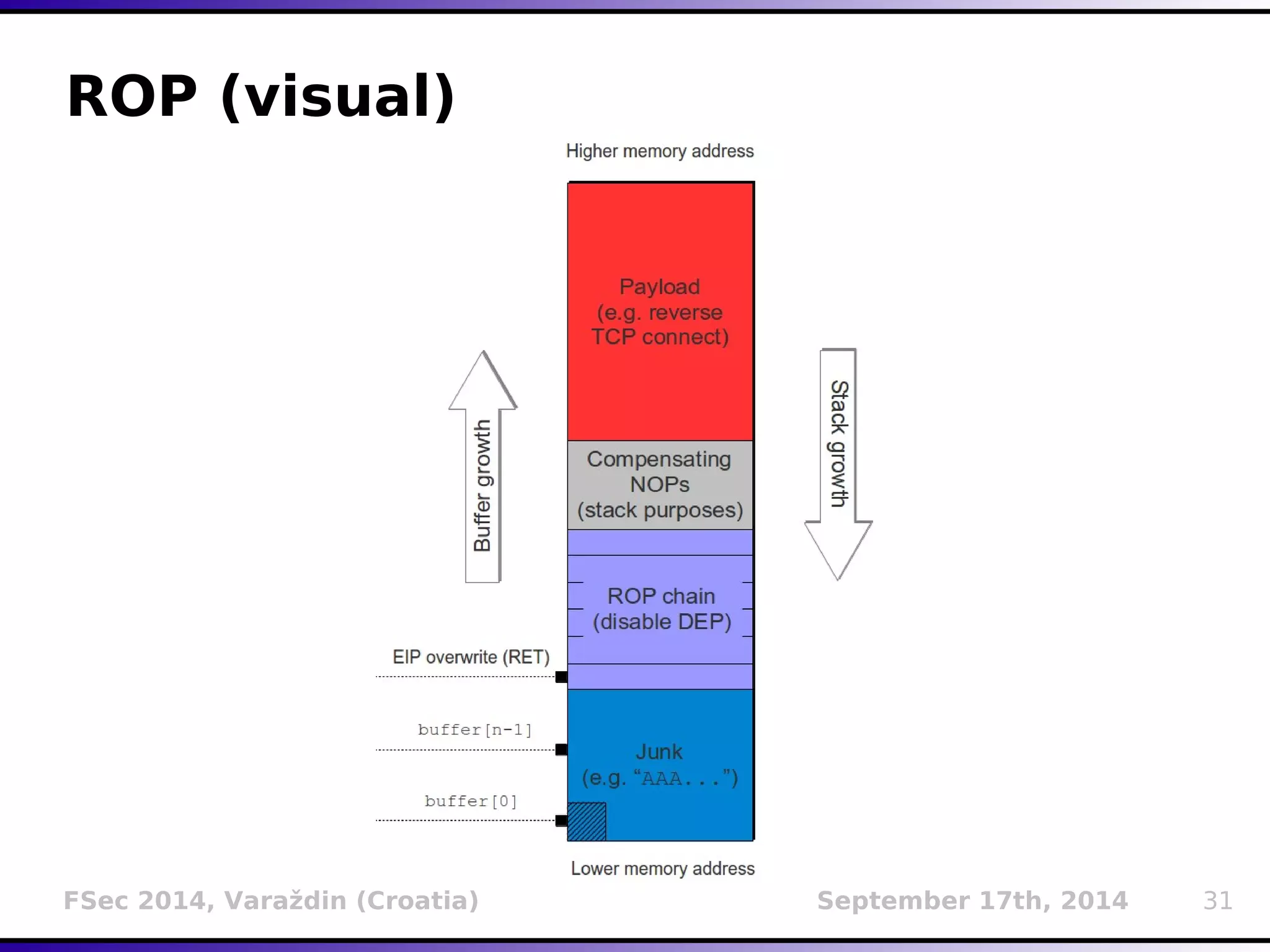
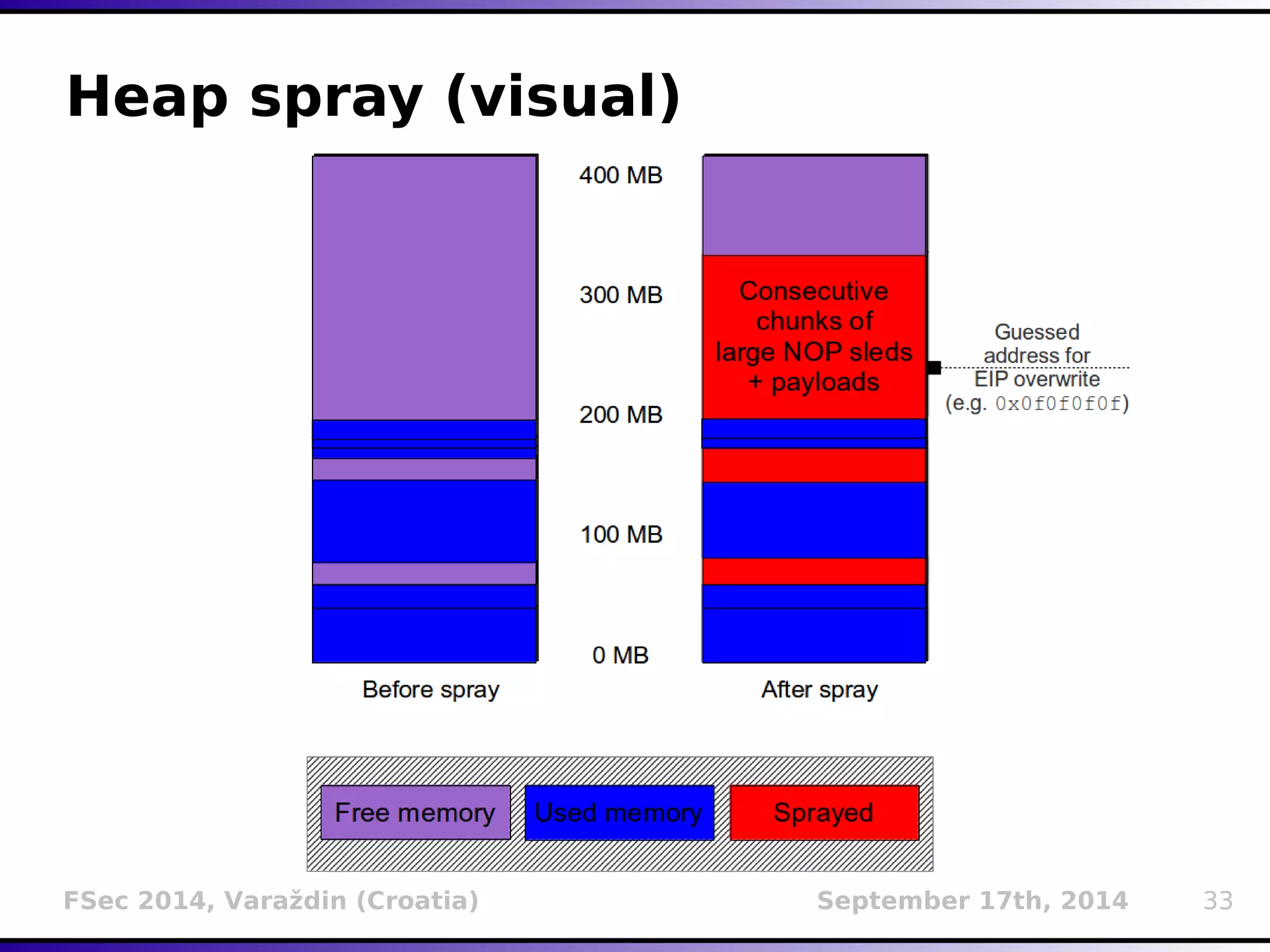
The document presents a detailed overview of buffer overflow vulnerabilities, covering their historical context, types (stack-based and heap-based), and various exploitation techniques such as return-oriented programming (ROP) and heap spraying. Additionally, it discusses preventive measures including stack canaries, address space layout randomization (ASLR), and data execution prevention (DEP). The presentation highlights the evolution of these concepts and techniques over the years and their relevance in computer security.