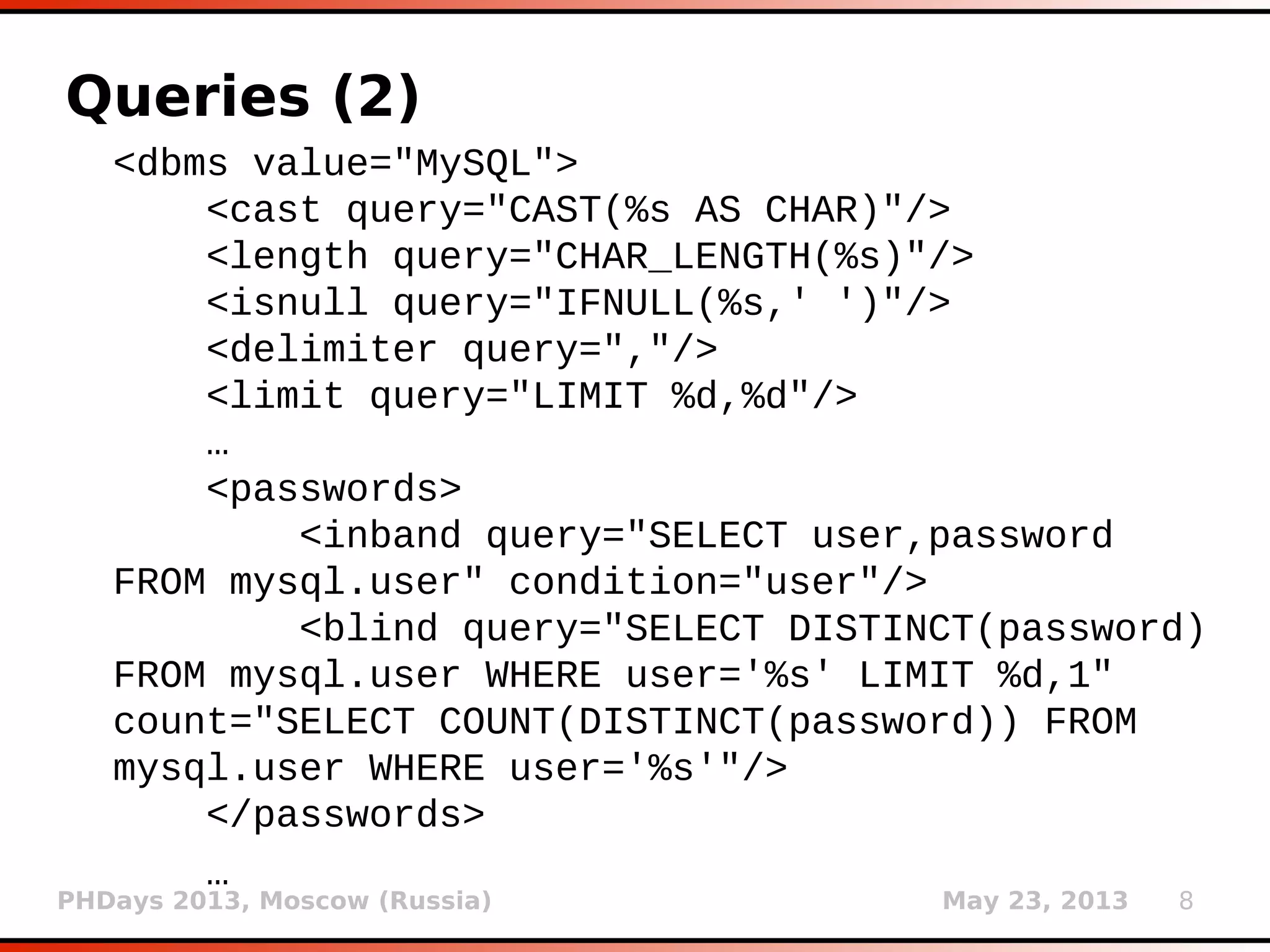
This document summarizes sqlmap, an open source penetration testing tool used for detecting and exploiting SQL injection flaws. It discusses sqlmap's features such as supporting large data dumps, storing session data, XML payload and query formats, multithreading, direct database connections, loading requests from files, form and site crawling, authentication, detection of reflection and dynamic content, and fingerprinting of databases and web servers.

![PHDays 2013, Moscow (Russia) May 23, 2013 3
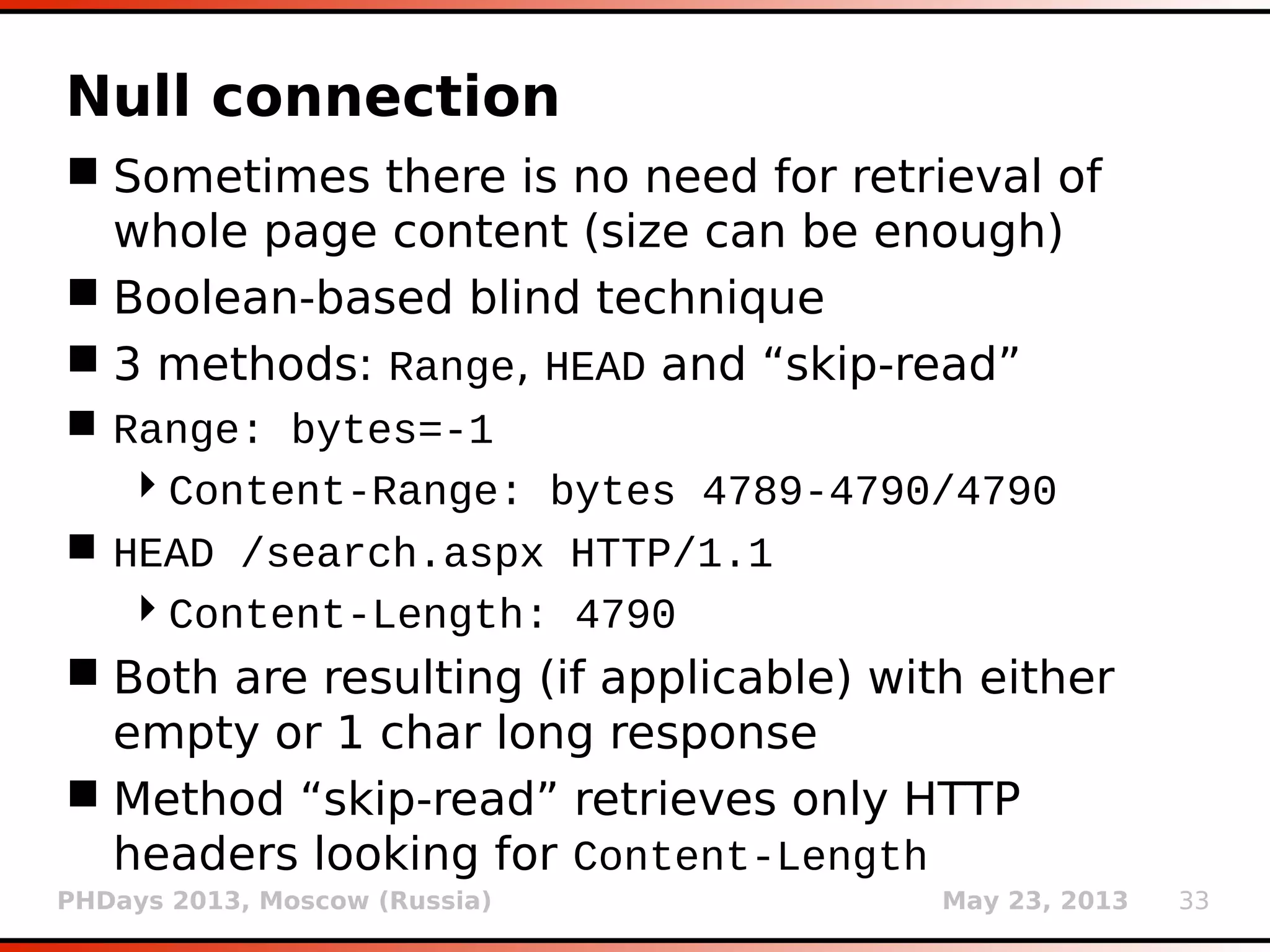
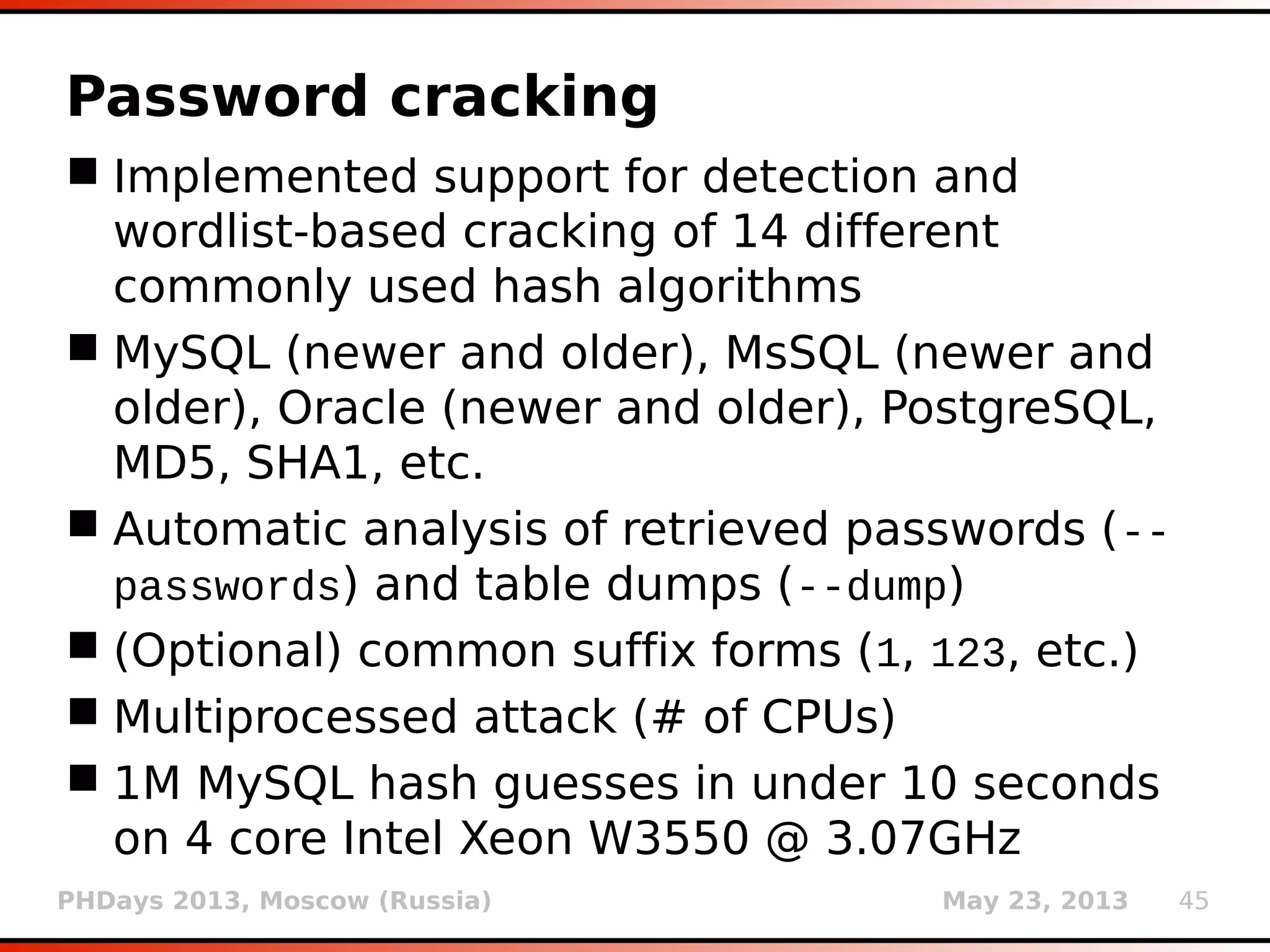
HashDB
Storage of resumable session data at
centralized place (local SQLite3 database)
Non-ASCII values are automatically
serialized/deserialized (pickle)
INSERT INTO storage VALUES
(LONG(MD5(target_url || key ||
MILESTONE_SALT)[:8]), stored_value)
MILESTONE_SALT is changed whenever there is a
change in HashDB mechanism that is bringing
incompatibility with previous versions
key uniquely describes storage_value for a
given target_url (e.g.: KB_INJECTIONS, SELECT
banner FROM v$version WHERE ROWNUM=1, etc.)](https://image.slidesharecdn.com/phdays-2013-miroslavstampar-sqlmapunderthehood-130523010924-phpapp01/75/sqlmap-Under-the-Hood-3-2048.jpg)
![PHDays 2013, Moscow (Russia) May 23, 2013 5
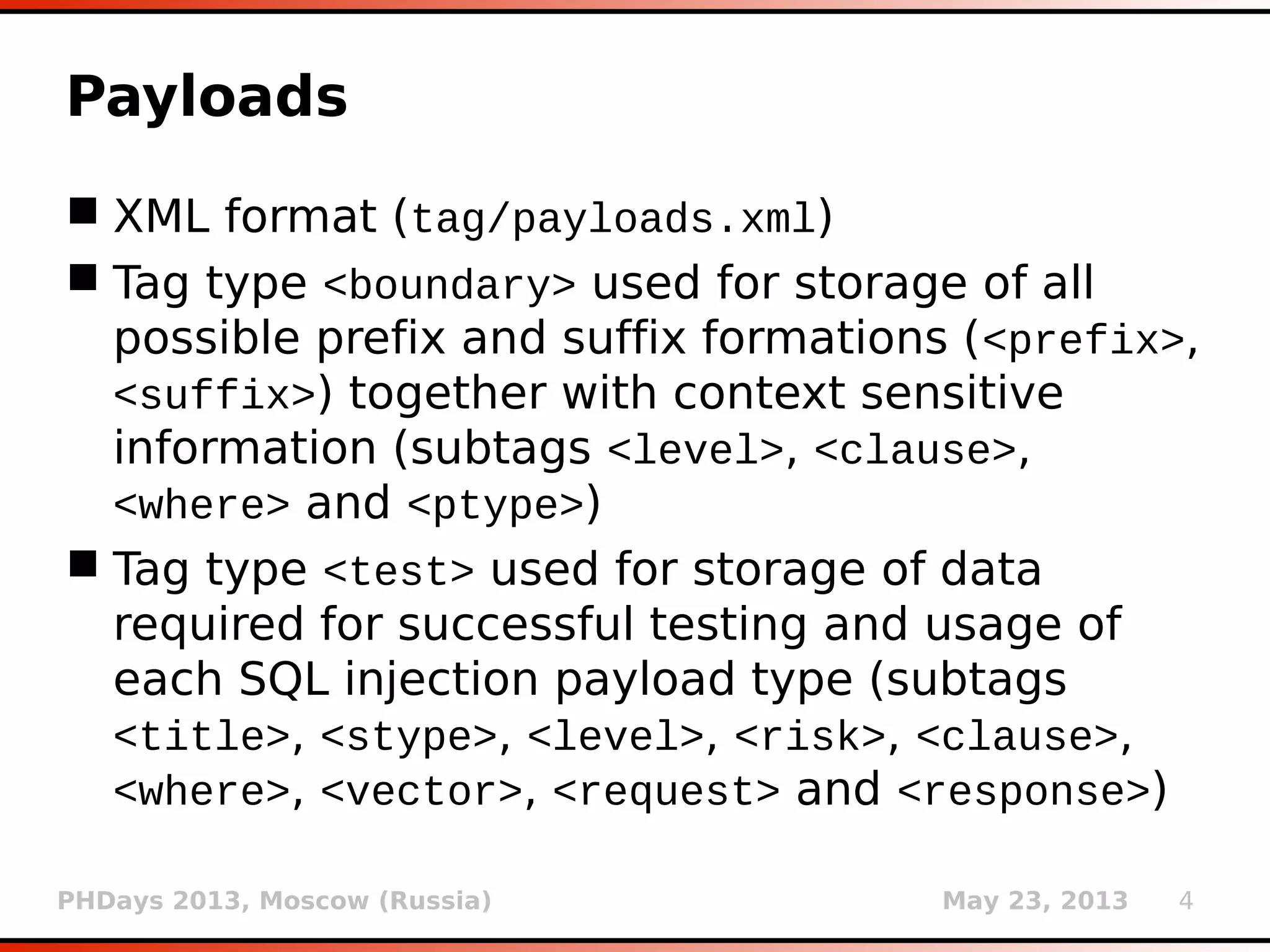
Payloads (2)
<boundary>
<level>1</level>
<clause>1</clause>
<where>1,2</where>
<ptype>1</ptype>
<prefix>)</prefix>
<suffix>AND
([RANDNUM]=[RANDNUM]</suffix>
</boundary>](https://image.slidesharecdn.com/phdays-2013-miroslavstampar-sqlmapunderthehood-130523010924-phpapp01/75/sqlmap-Under-the-Hood-5-2048.jpg)
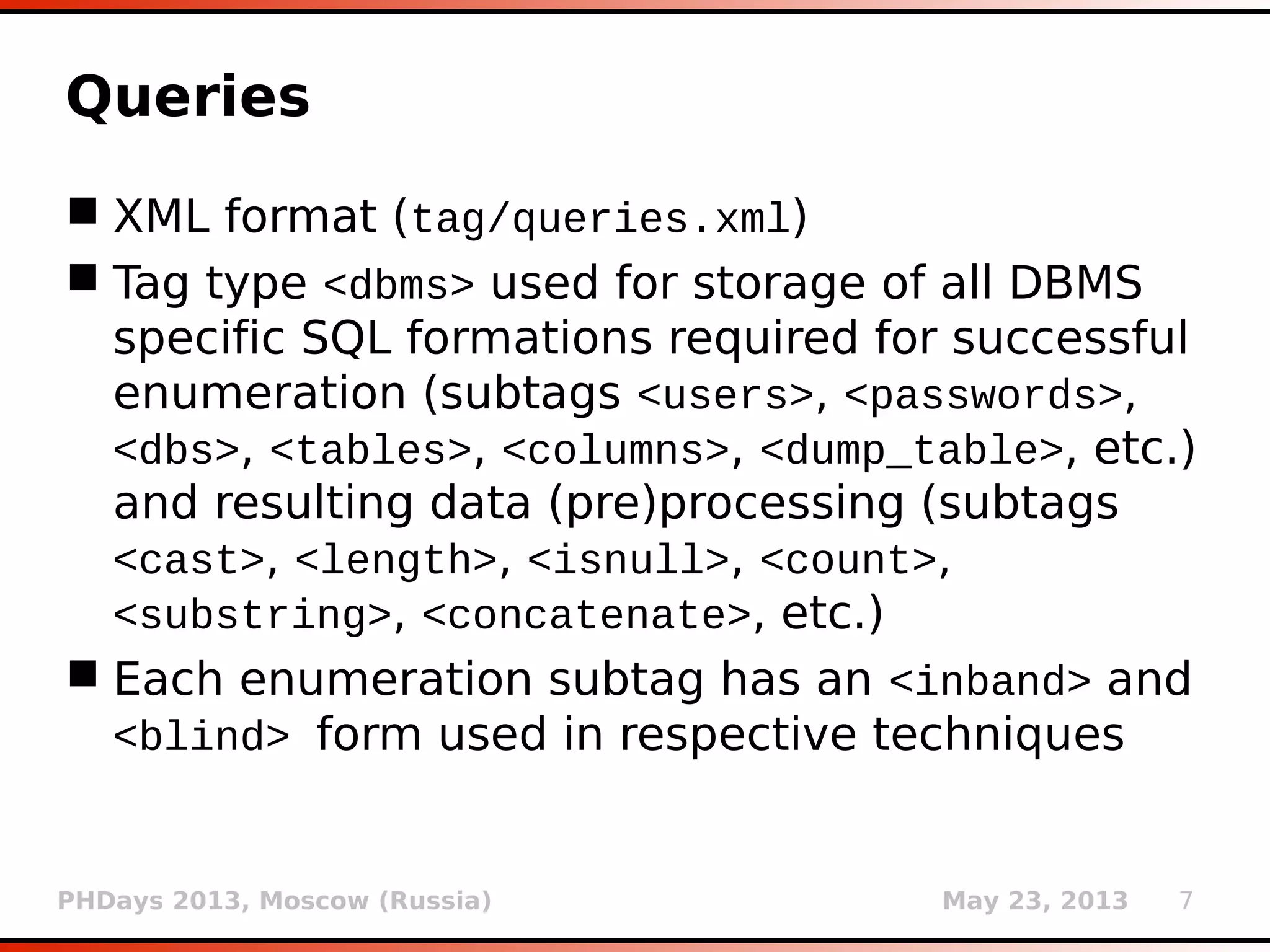
![PHDays 2013, Moscow (Russia) May 23, 2013 6
Payloads (3)
<test>
<title>Microsoft SQL Server/Sybase AND error-based - WHERE or HAVING
clause (IN)</title>
<stype>2</stype>
<level>2</level>
<risk>0</risk>
<clause>1</clause>
<where>1</where>
<vector>AND [RANDNUM] IN (('[DELIMITER_START]'+([QUERY])
+'[DELIMITER_STOP]'))</vector>
<request>
<payload>AND [RANDNUM] IN (('[DELIMITER_START]'+(SELECT (CASE WHEN
([RANDNUM]=[RANDNUM]) THEN '1' ELSE '0' END))
+'[DELIMITER_STOP]'))</payload>
</request>
<response>
<grep>[DELIMITER_START](?P<result>.*?)
[DELIMITER_STOP]</grep>
</response>
<details>
<dbms>Microsoft SQL Server</dbms>
<dbms>Sybase</dbms>
<os>Windows</os>
</details>
</test>](https://image.slidesharecdn.com/phdays-2013-miroslavstampar-sqlmapunderthehood-130523010924-phpapp01/75/sqlmap-Under-the-Hood-6-2048.jpg)


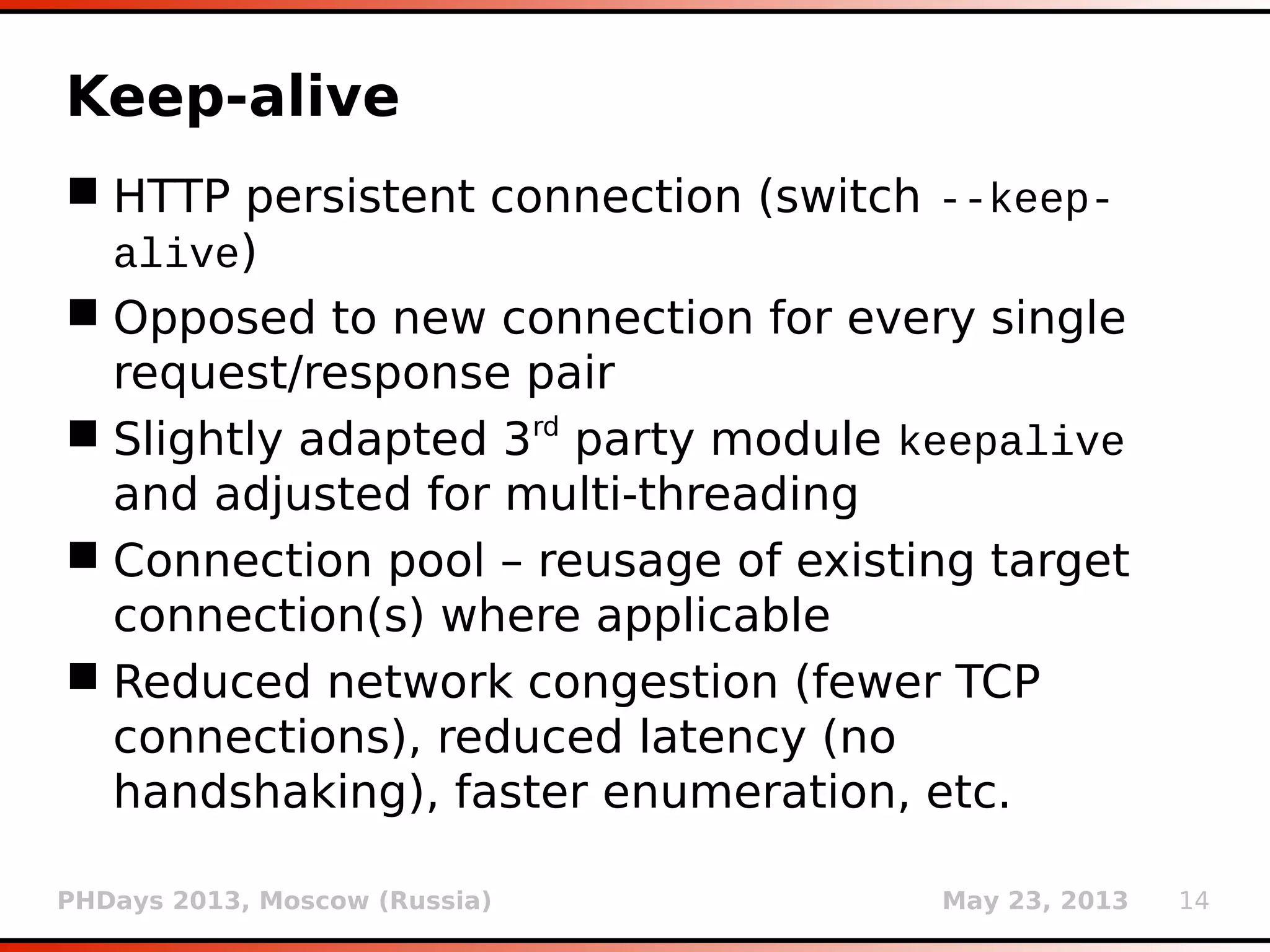
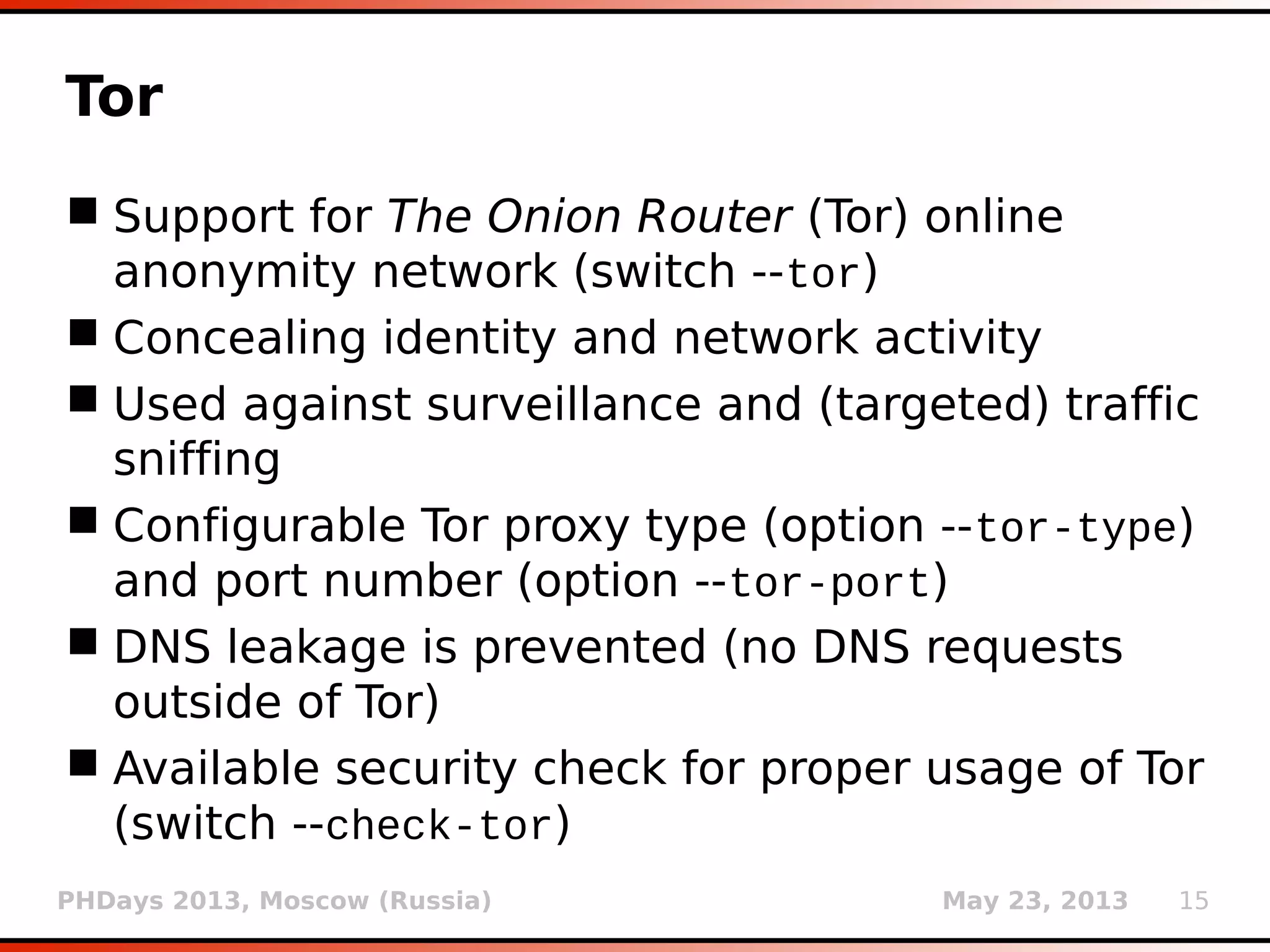
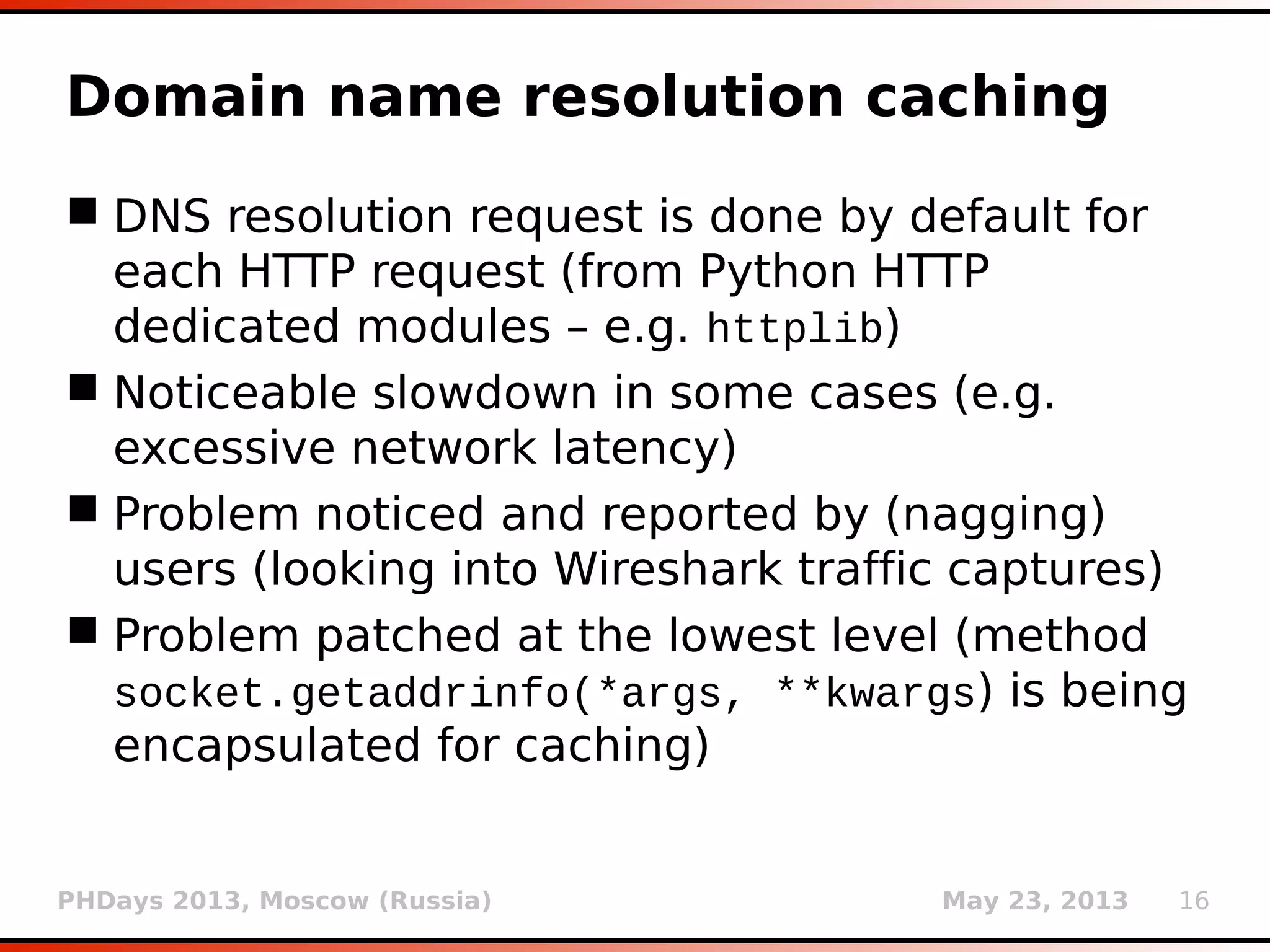

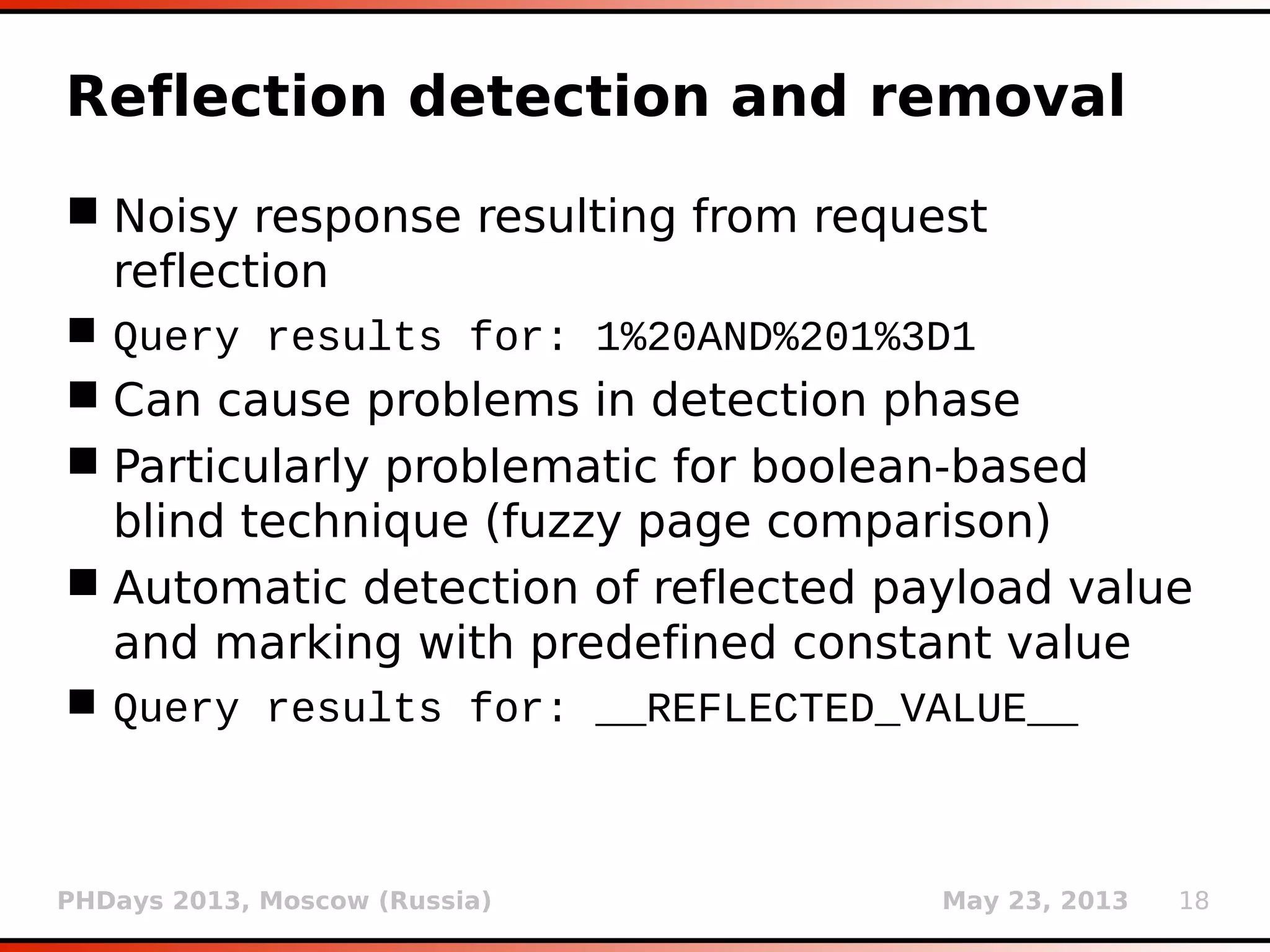




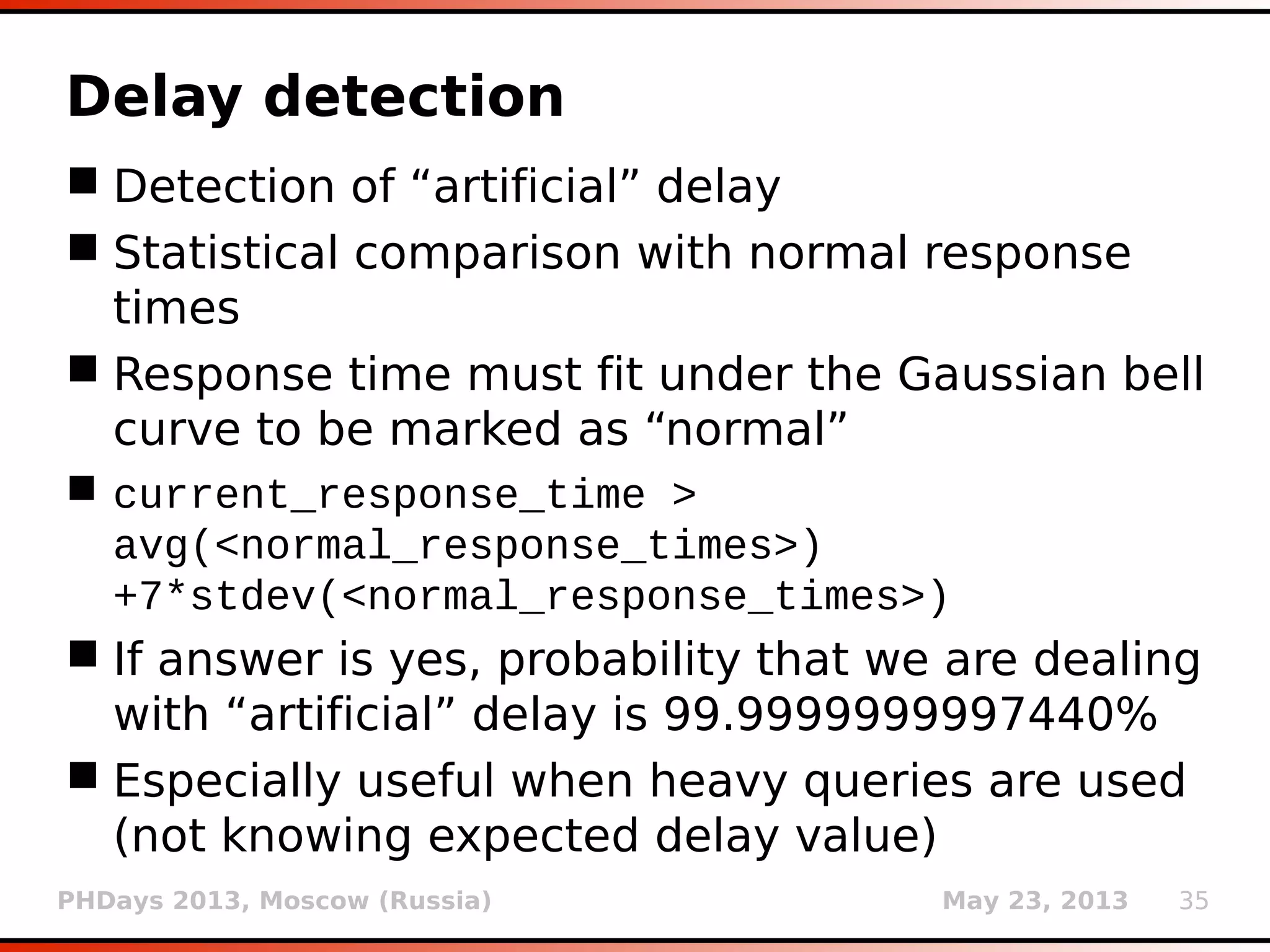
![PHDays 2013, Moscow (Russia) May 23, 2013 25
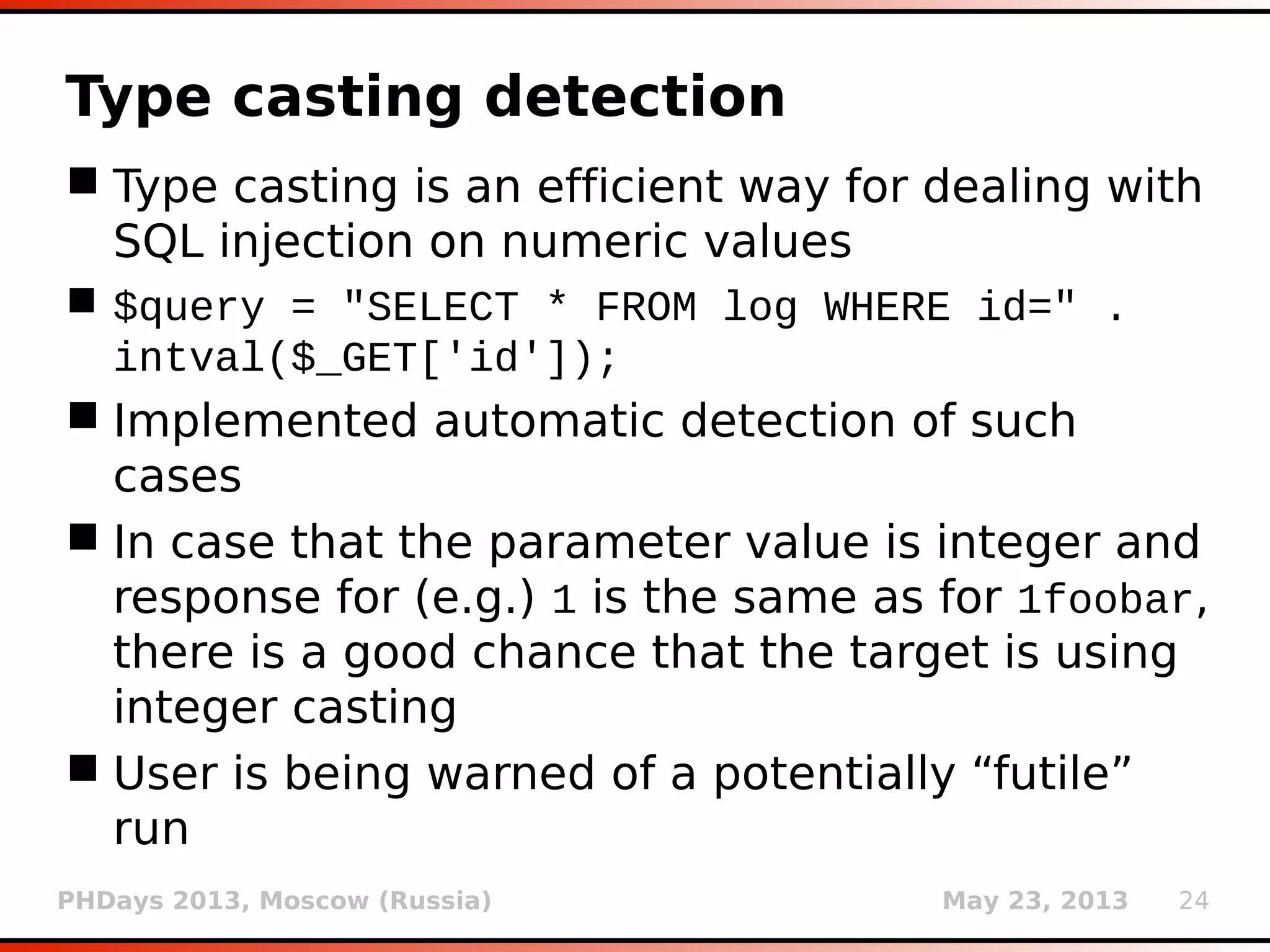
Type casting detection
Type casting is an efficient way for dealing with
SQL injection on numeric values
$query = "SELECT * FROM log WHERE id=" .
intval($_GET['id']);
Implemented automatic detection of such
cases
In case that the parameter value is integer and
response for (e.g.) 1 is the same as for 1foobar,
there is a good chance that the target is using
integer casting
User is warned of a potentially “futile” run](https://image.slidesharecdn.com/phdays-2013-miroslavstampar-sqlmapunderthehood-130523010924-phpapp01/75/sqlmap-Under-the-Hood-25-2048.jpg)

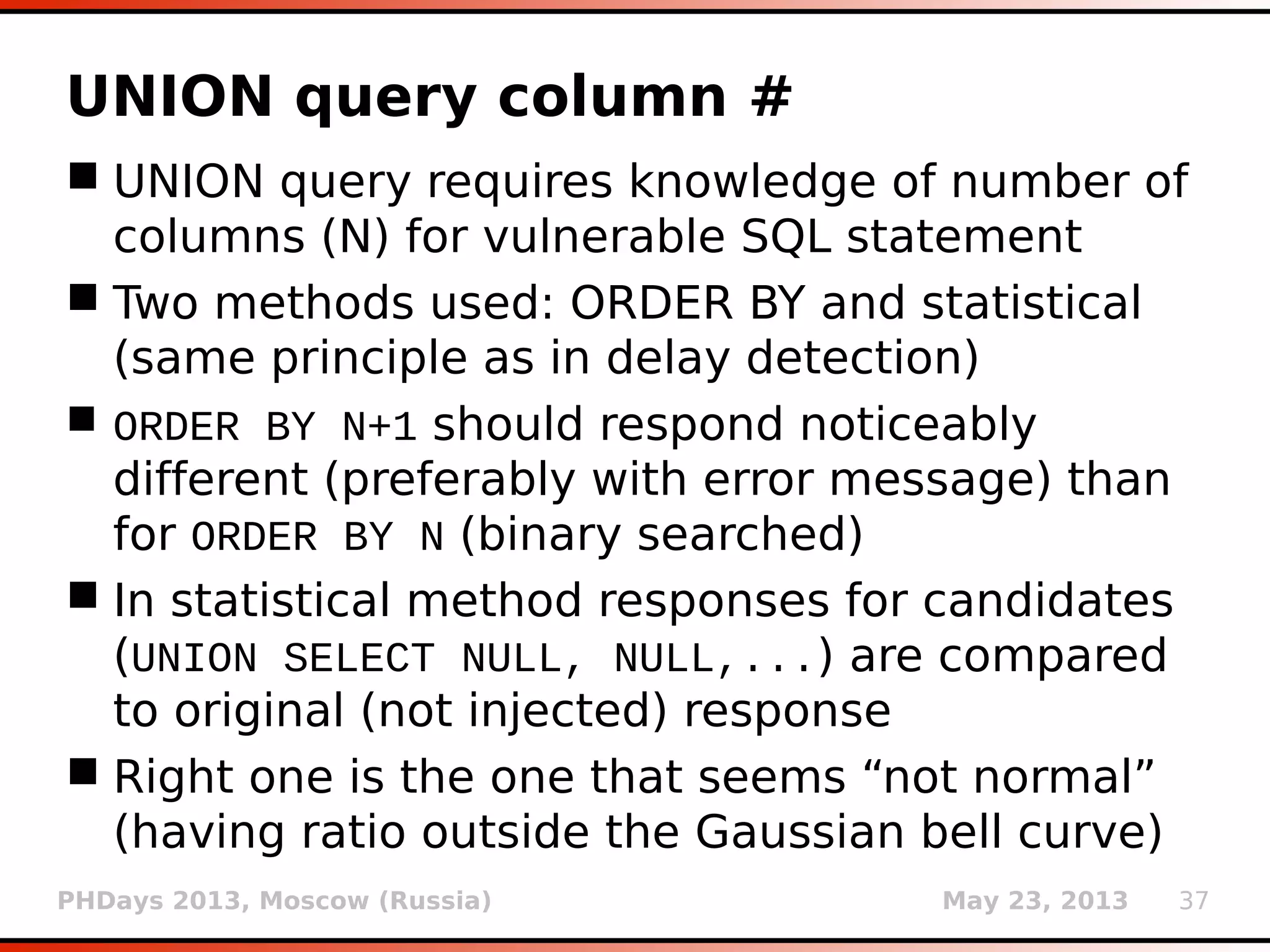
![PHDays 2013, Moscow (Russia) May 23, 2013 32
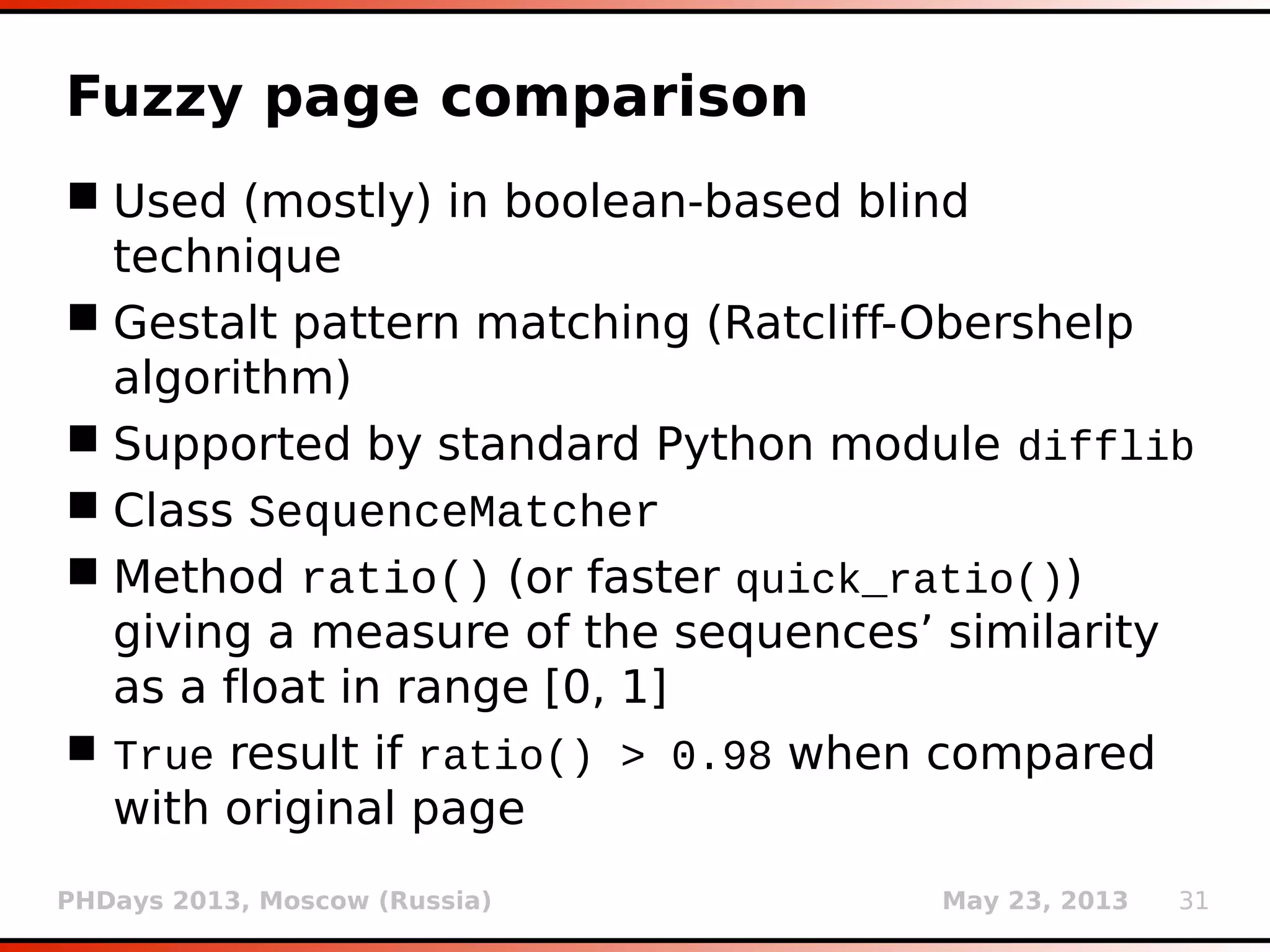
Fuzzy page comparison
Used (mostly) in boolean-based blind
technique
Gestalt pattern matching (Ratcliff-Obershelp
algorithm)
Supported by standard Python module difflib
Class SequenceMatcher
Method ratio() (or faster quick_ratio())
giving a measure of the sequences’ similarity
as a float in range [0, 1]
True result if ratio() > 0.98 when compared
with original page](https://image.slidesharecdn.com/phdays-2013-miroslavstampar-sqlmapunderthehood-130523010924-phpapp01/75/sqlmap-Under-the-Hood-32-2048.jpg)