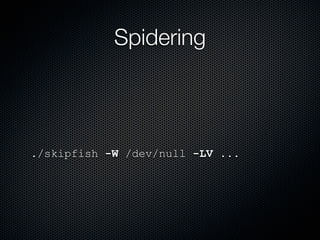
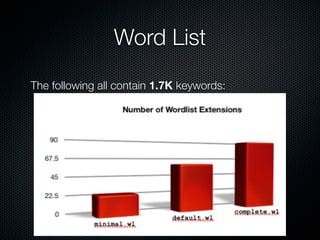
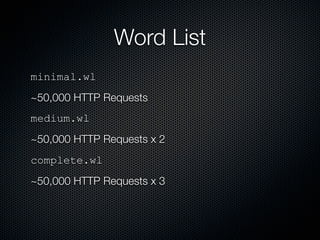
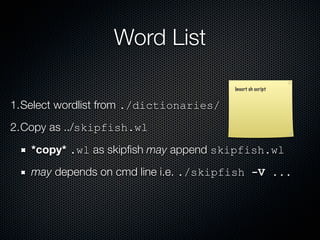
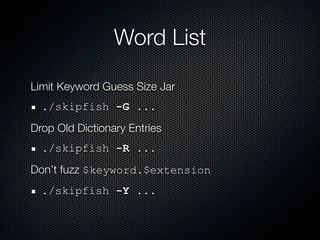
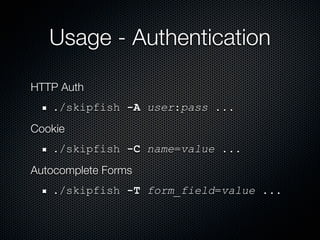
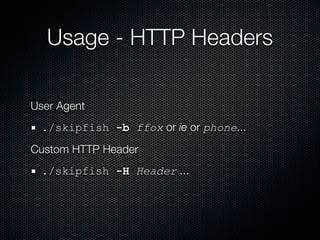
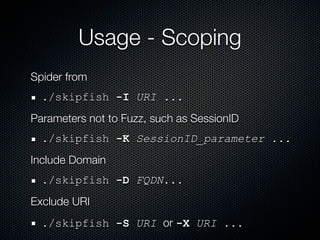
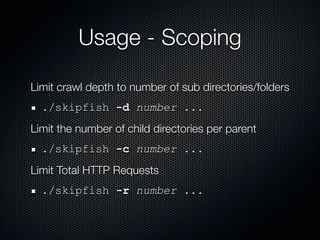
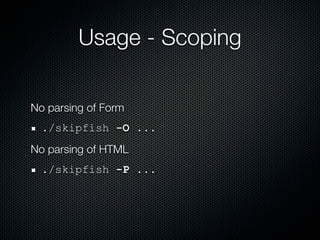
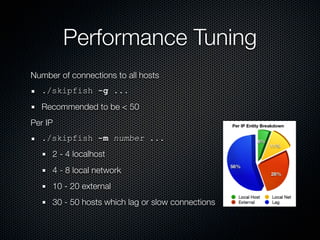
Skipfish is a fast web application security scanner developed by Michal Zalewski, which utilizes word lists for spidering and testing web applications. The document outlines its capabilities, installation instructions, usage commands, and performance tuning recommendations. Additionally, it discusses issues such as false positives and limitations within the tool.