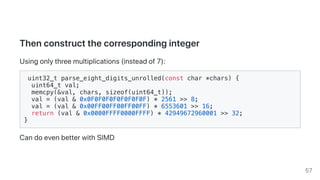
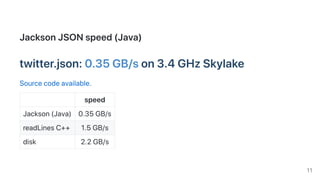
This document discusses techniques for quickly parsing JSON documents. It begins by benchmarking different JSON parsing libraries and finds that simdjson, which uses SIMD instructions, can parse Twitter's JSON feed at 2.4 GB/s on a 3.4 GHz CPU, around 4 times faster than other libraries. It then describes four tricks used in simdjson to achieve this speed: 1) avoiding hard-to-predict branches, 2) using wide SIMD instructions, 3) avoiding memory and object allocation, and 4) measuring performance through benchmark-driven development. The document provides several examples showing how these tricks can dramatically speed up JSON parsing and related tasks.











![Writerandomnumbersonanarray.
while (howmany != 0) {
out[index] = random();
index += 1;
howmany--;
}
e.g.,~3cyclesperiteration
16](https://image.slidesharecdn.com/qcon2019-191109155258/85/Parsing-JSON-Really-Quickly-Lessons-Learned-16-320.jpg)
![Writeonlyoddrandomnumbers:
while (howmany != 0) {
val = random();
if( val is odd) { // <=== new
out[index] = val;
index += 1;
}
howmany--;
}
17](https://image.slidesharecdn.com/qcon2019-191109155258/85/Parsing-JSON-Really-Quickly-Lessons-Learned-17-320.jpg)

![Gobranchless!while (howmany != 0) {
val = random();
out[index] = val;
index += (val bitand 1);
howmany--;
}
backtounder4cycles!
Detailsandcodeavailable
19](https://image.slidesharecdn.com/qcon2019-191109155258/85/Parsing-JSON-Really-Quickly-Lessons-Learned-19-320.jpg)














![Example2.Classifyingcharacters
comma(0x2c) ,
colon(0x3a) :
brackets(0x5b,0x5d,0x7b,0x7d): [, ], {, }
white-space(0x09,0x0a,0x0d,0x20)
others
Classify16,32or64charactersatonce!
36](https://image.slidesharecdn.com/qcon2019-191109155258/85/Parsing-JSON-Really-Quickly-Lessons-Learned-36-320.jpg)


![Startwithanarrayof4-bitvalues
[1,1,0,2,0,5,10,15,7,8,13,9,0,13,5,1]
Createalookuptable
[200,201,202,203,204,205,206,207,208,209,210,211,212,213,214,215]
0 200,1 201,2 202
Result:
[201,201,200,202,200,205,210,215,207,208,213,209,200,213,205,201]
39](https://image.slidesharecdn.com/qcon2019-191109155258/85/Parsing-JSON-Really-Quickly-Lessons-Learned-39-320.jpg)











![while (word != 0) {
result[i] = trailingzeroes(word);
word = word & (word - 1);
i++;
}
Ifnumberof1sper64-bitishardtopredict:lotsofmispredictions!!!
52](https://image.slidesharecdn.com/qcon2019-191109155258/85/Parsing-JSON-Really-Quickly-Lessons-Learned-52-320.jpg)

![Reducethenumberofmispredictionbydoingmoreworkperiteration:
while (word != 0) {
result[i] = trailingzeroes(word);
word = word & (word - 1);
result[i+1] = trailingzeroes(word);
word = word & (word - 1);
result[i+2] = trailingzeroes(word);
word = word & (word - 1);
result[i+3] = trailingzeroes(word);
word = word & (word - 1);
i+=4;
}
Discardbogusindexesbycountingthenumberof1sintheworddirectly(e.g.,
bitCount )
54](https://image.slidesharecdn.com/qcon2019-191109155258/85/Parsing-JSON-Really-Quickly-Lessons-Learned-54-320.jpg)