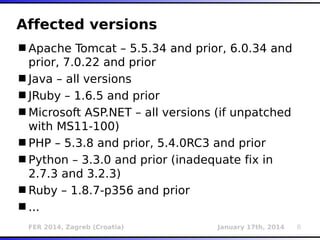
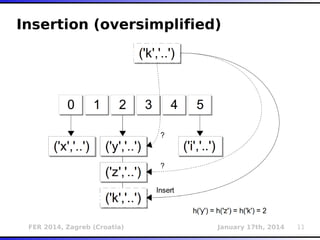
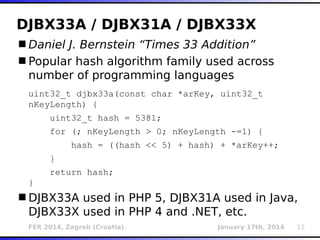
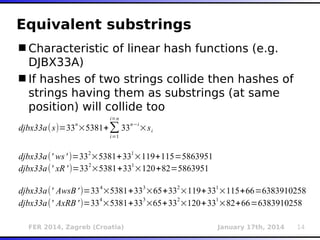
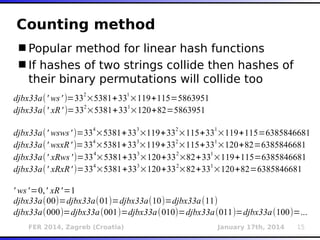
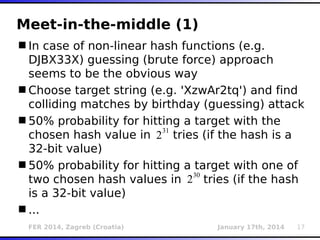
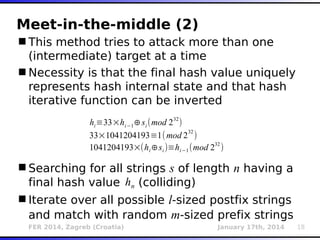
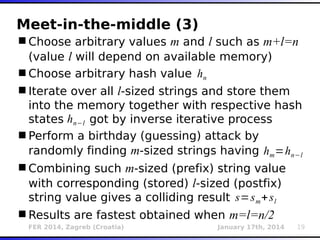
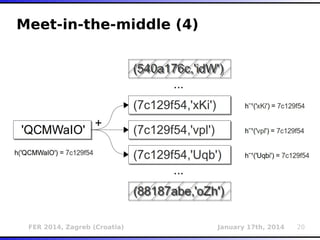
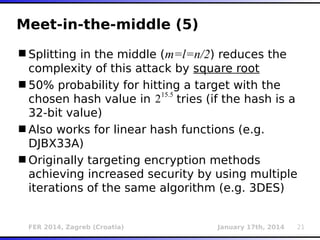
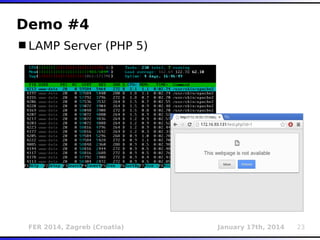
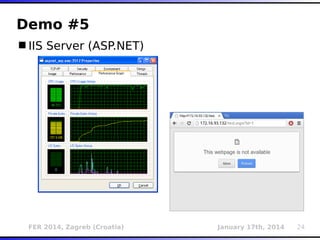
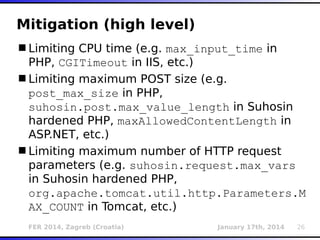
The document outlines various types of Denial of Service (DoS) attacks, particularly focusing on hash DoS attacks that exploit hash table collisions. It details the mechanisms of these attacks, the affected software versions, and methods of mitigation. The content includes technical descriptions of hash algorithms and strategies for collision generation, alongside mitigation techniques to reduce vulnerability to such attacks.