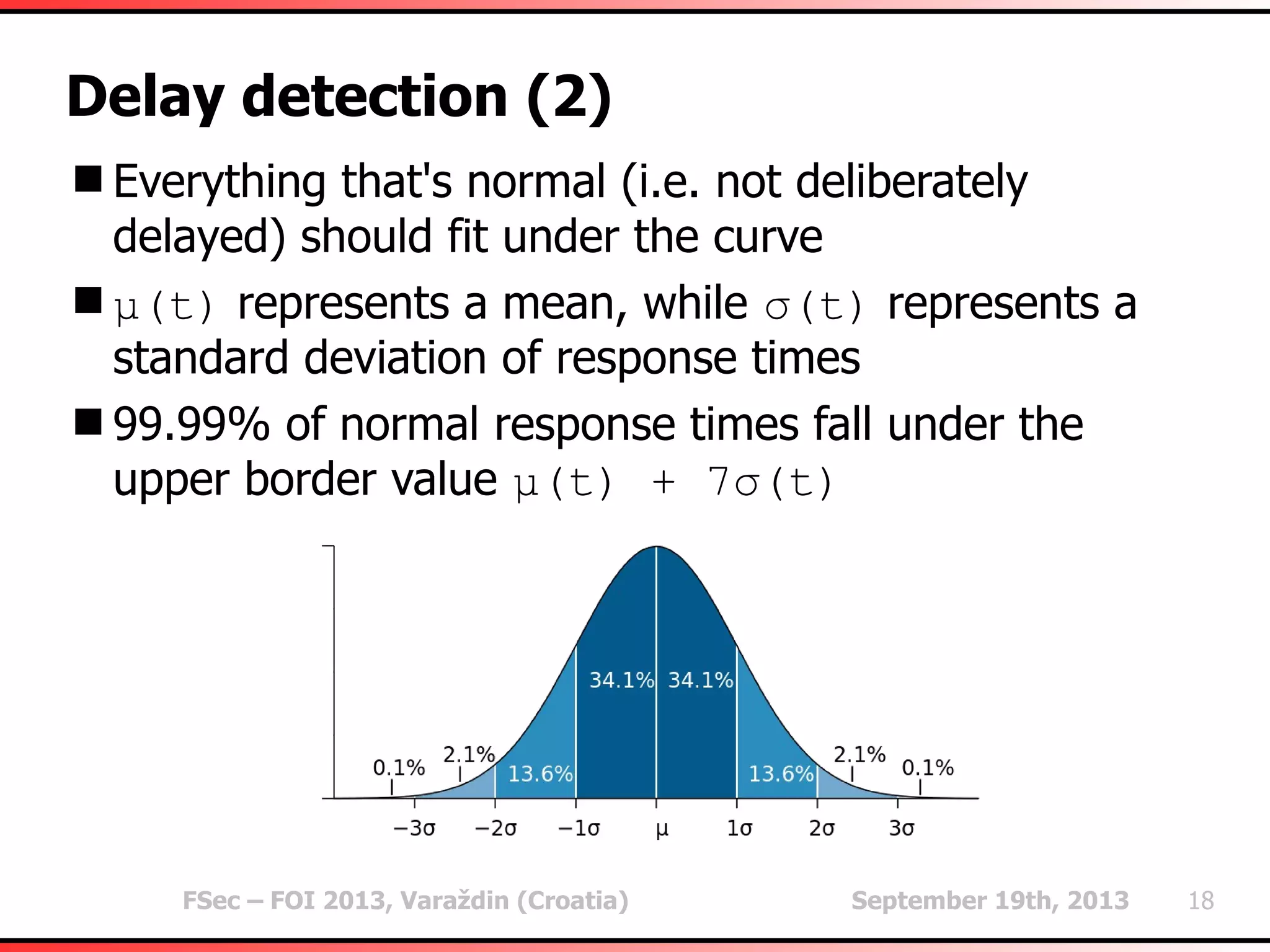
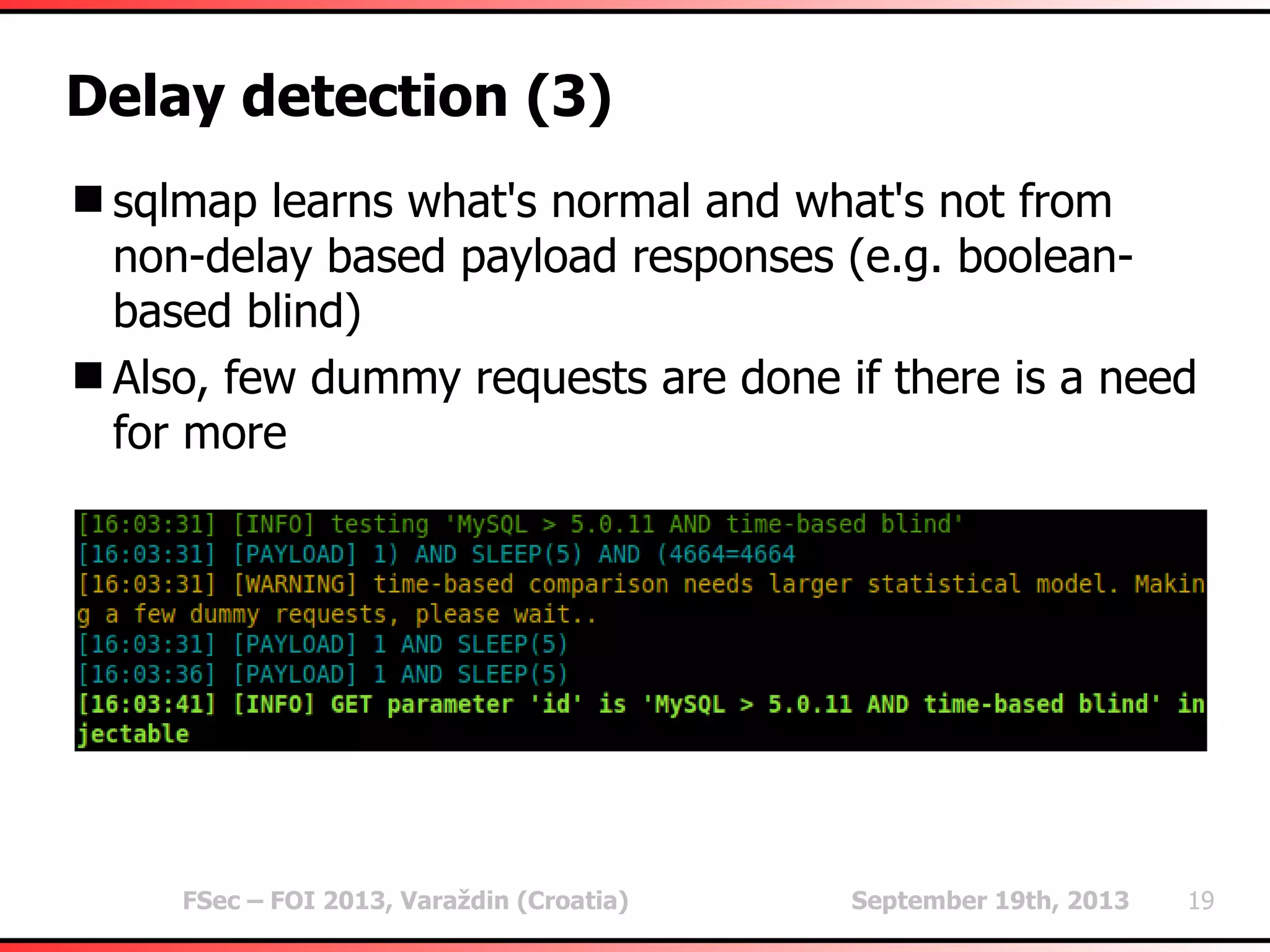
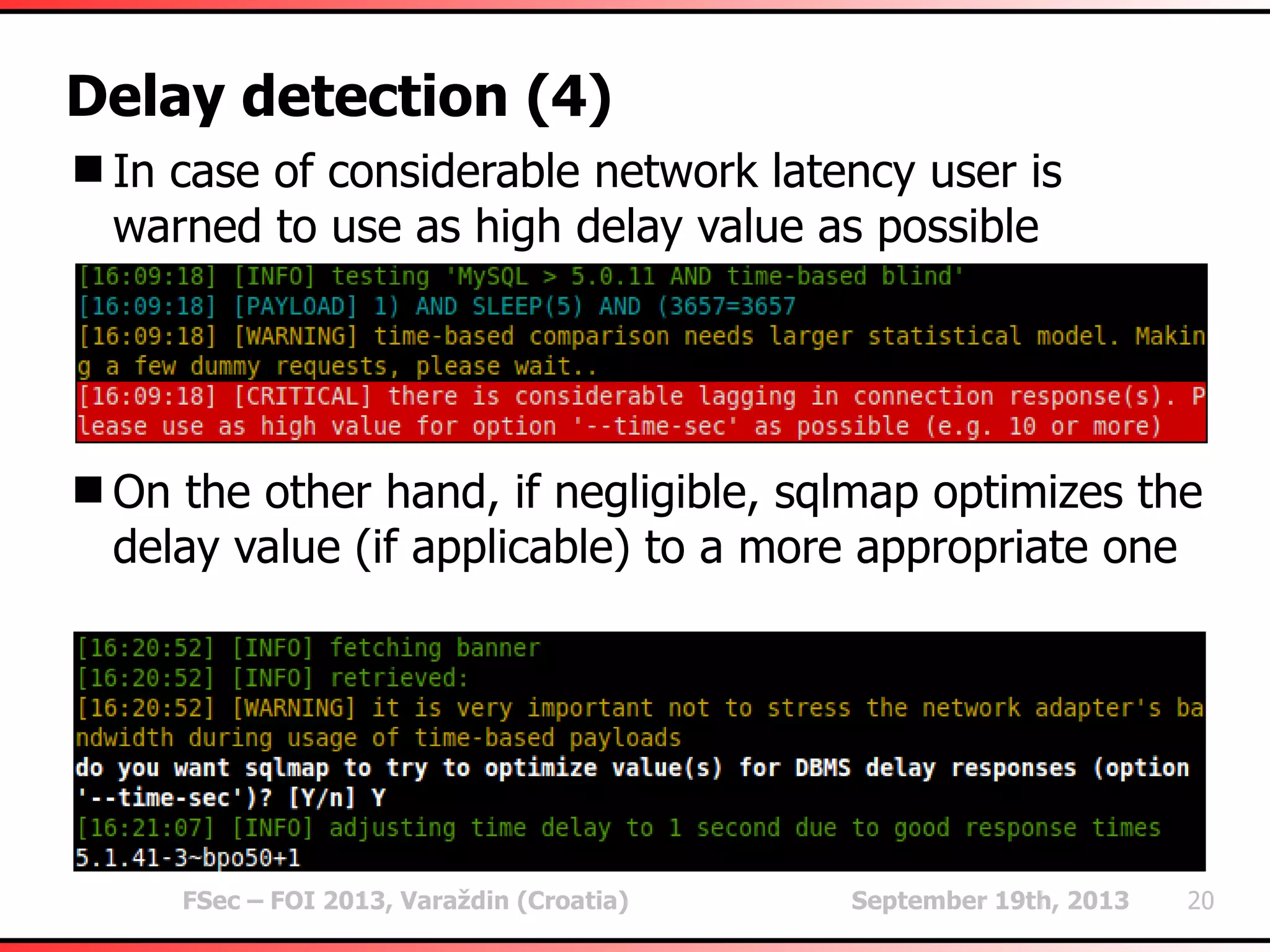
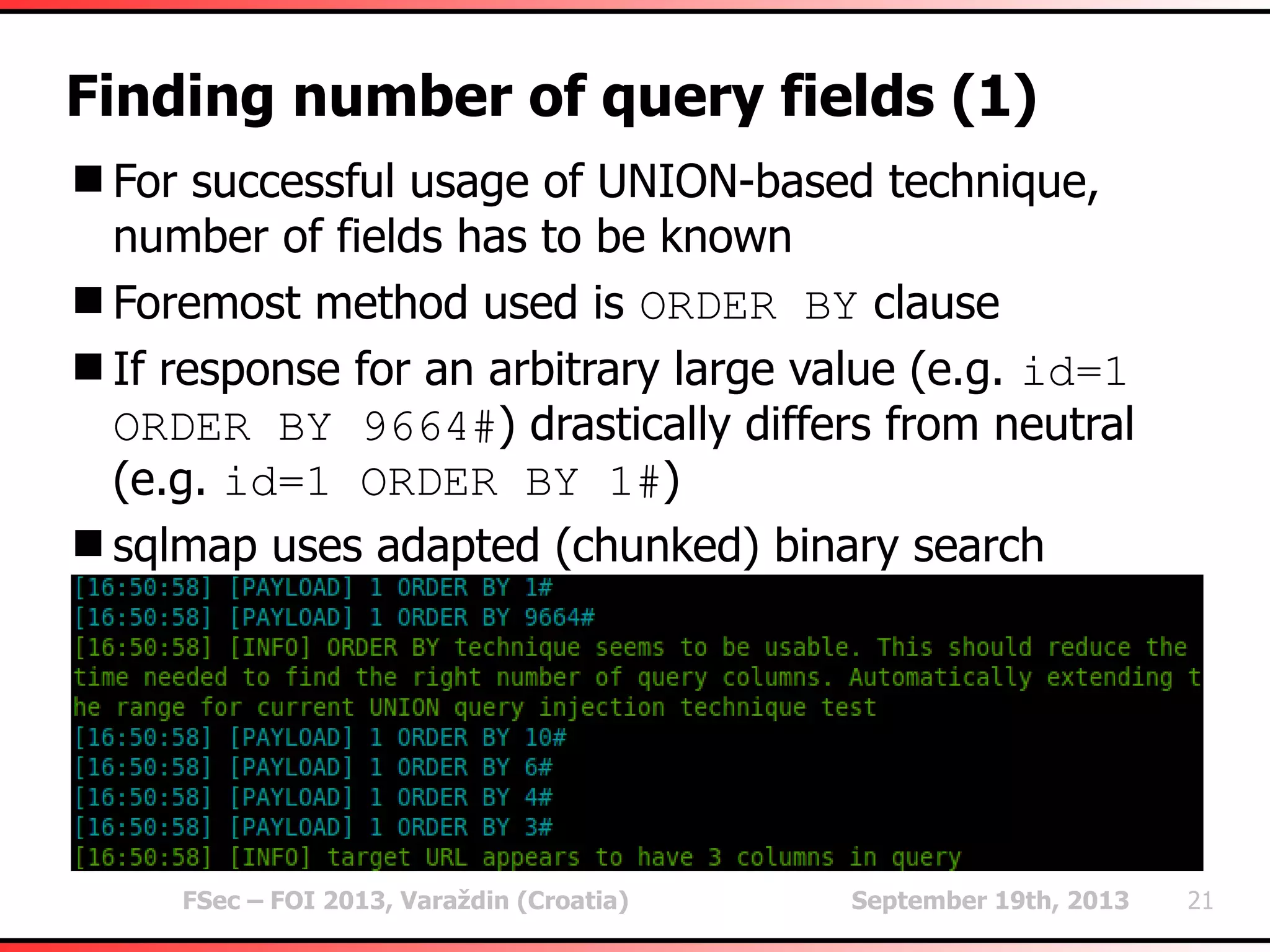
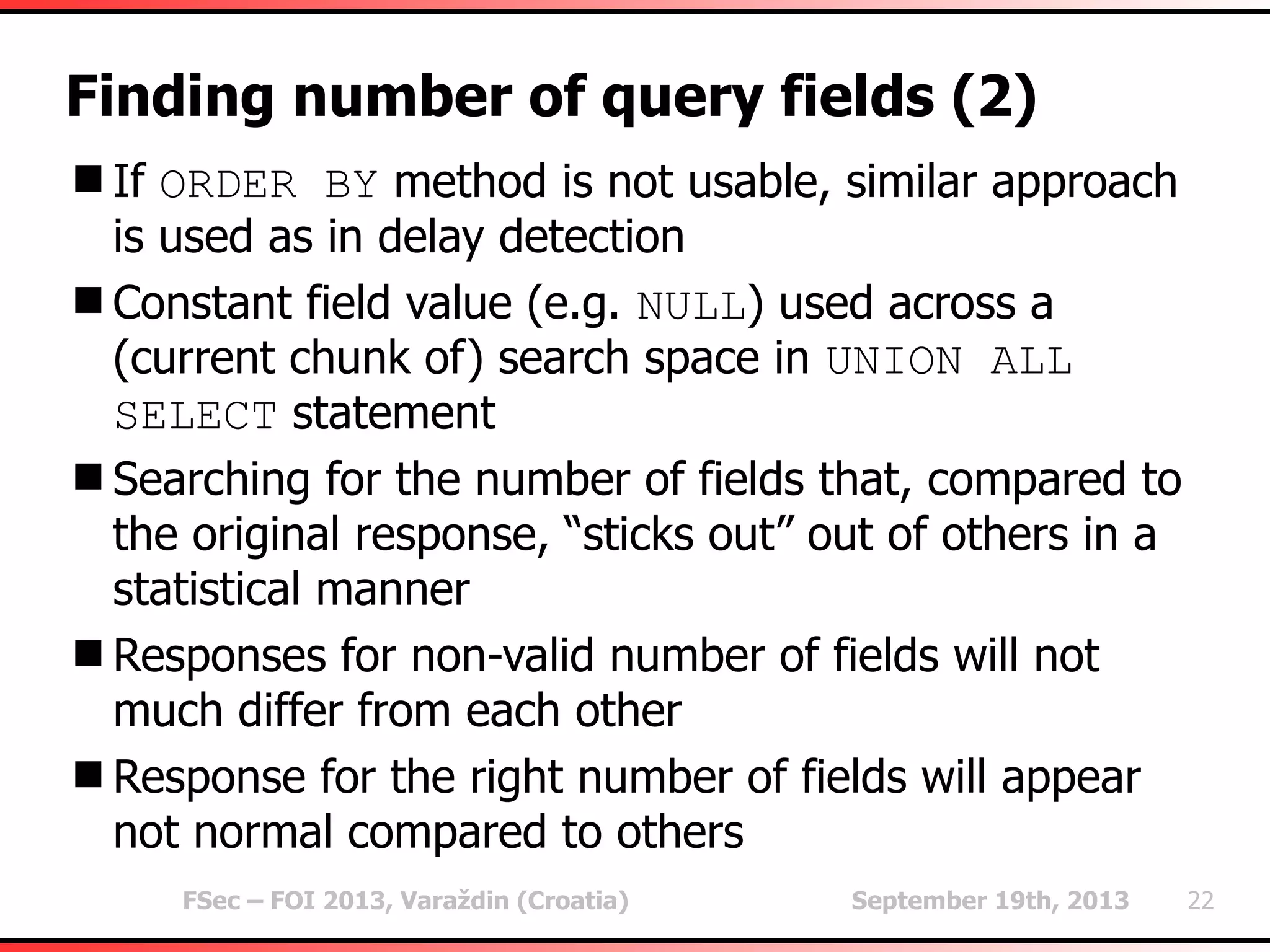
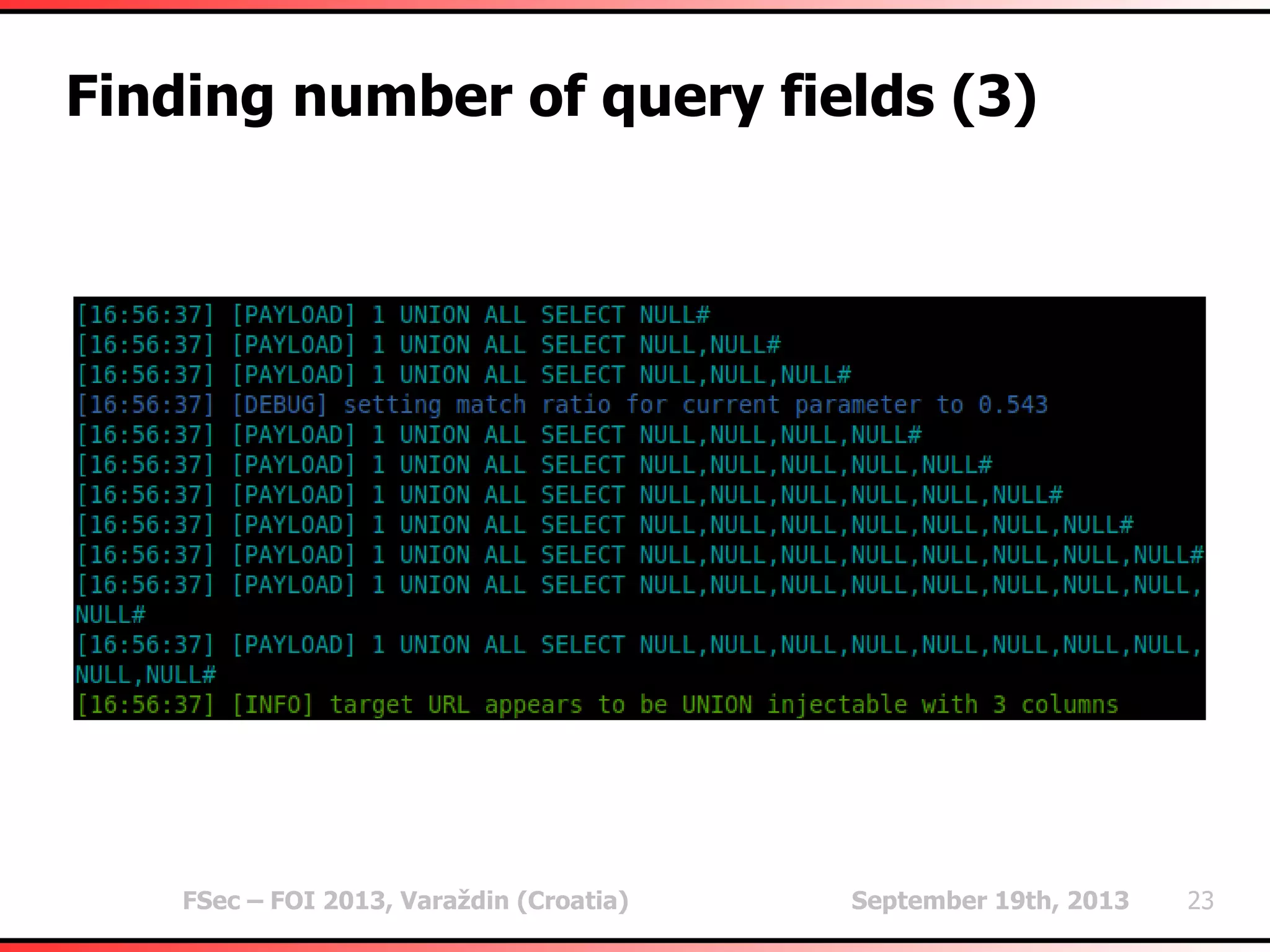
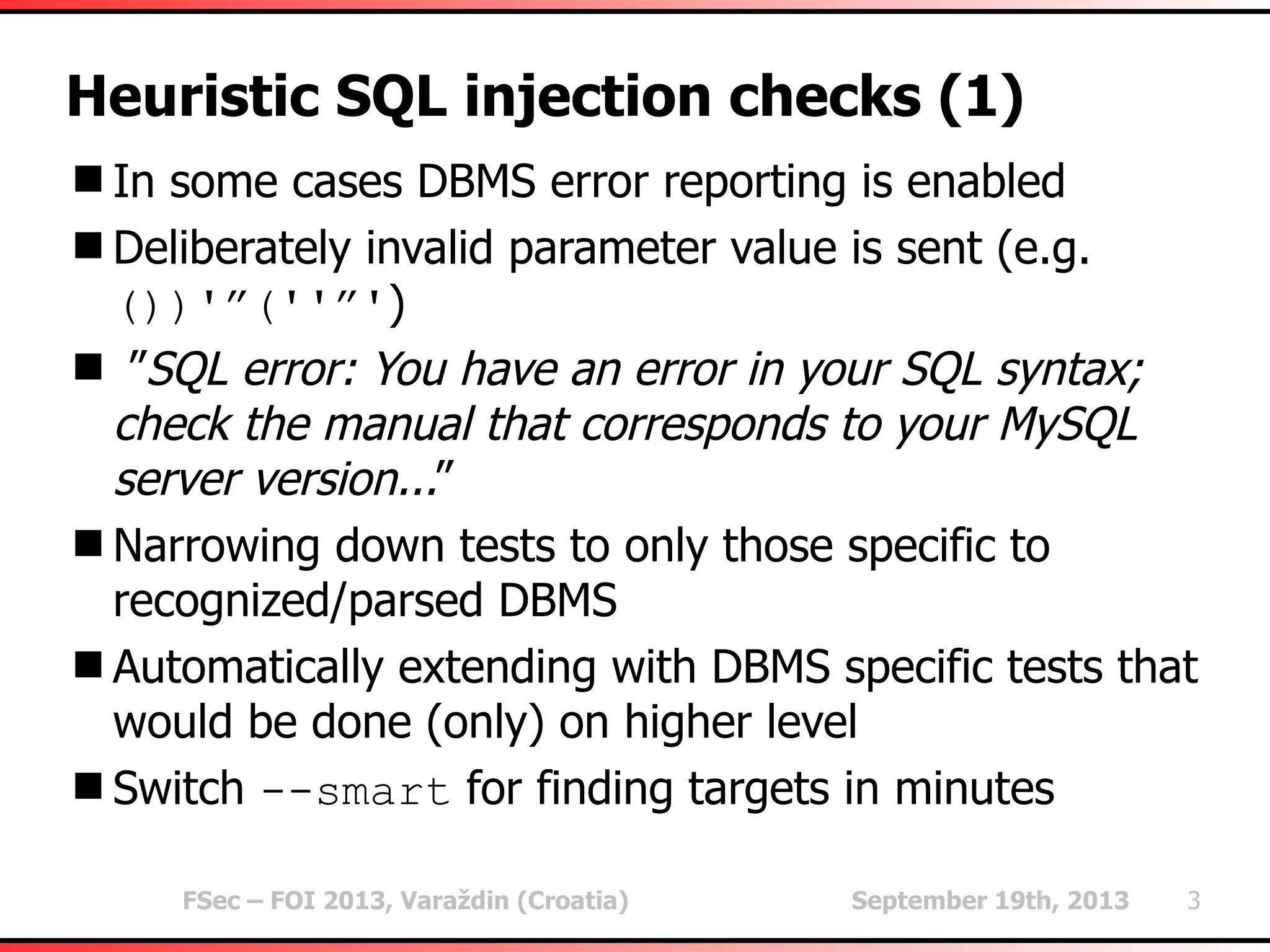
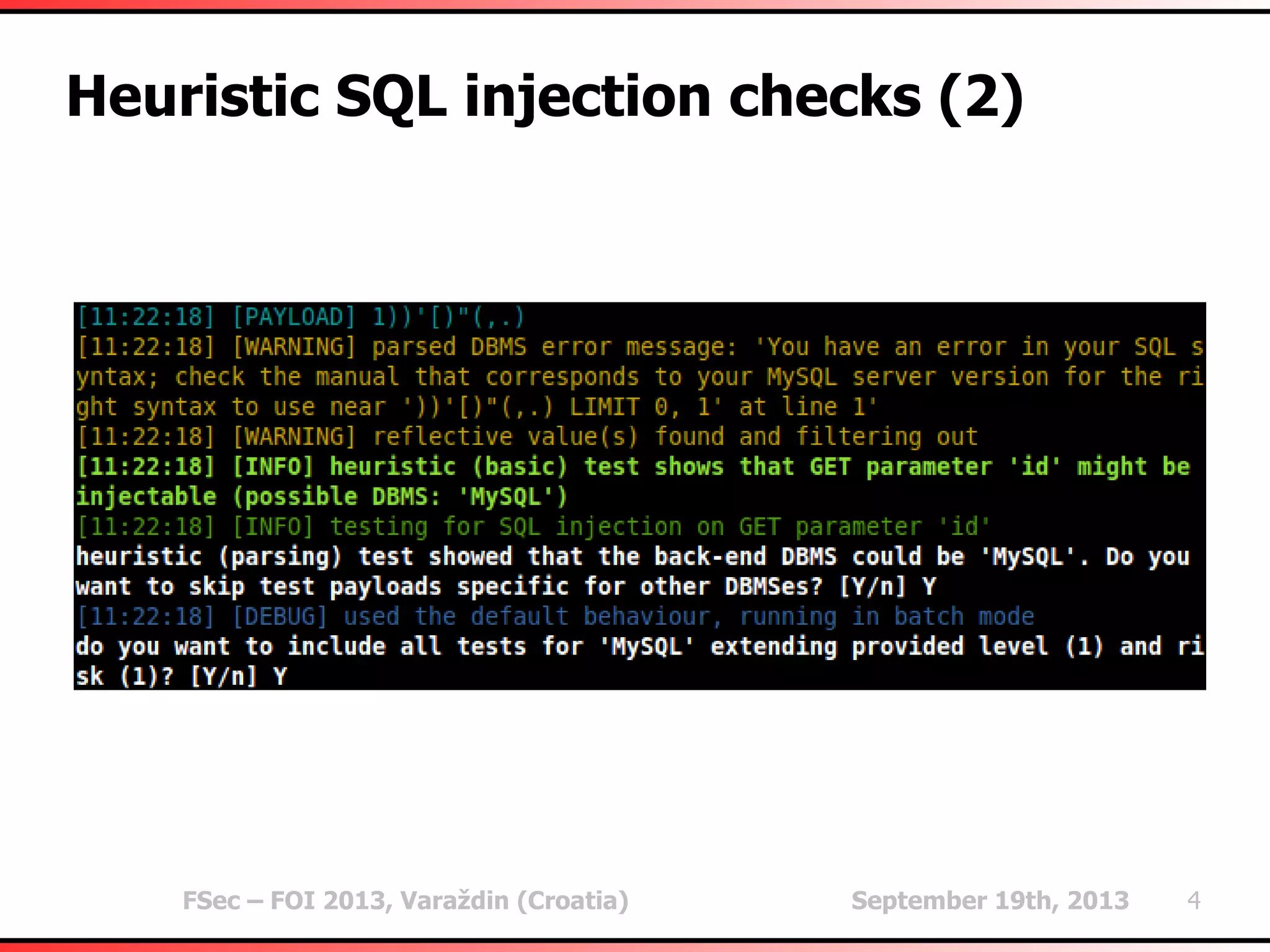
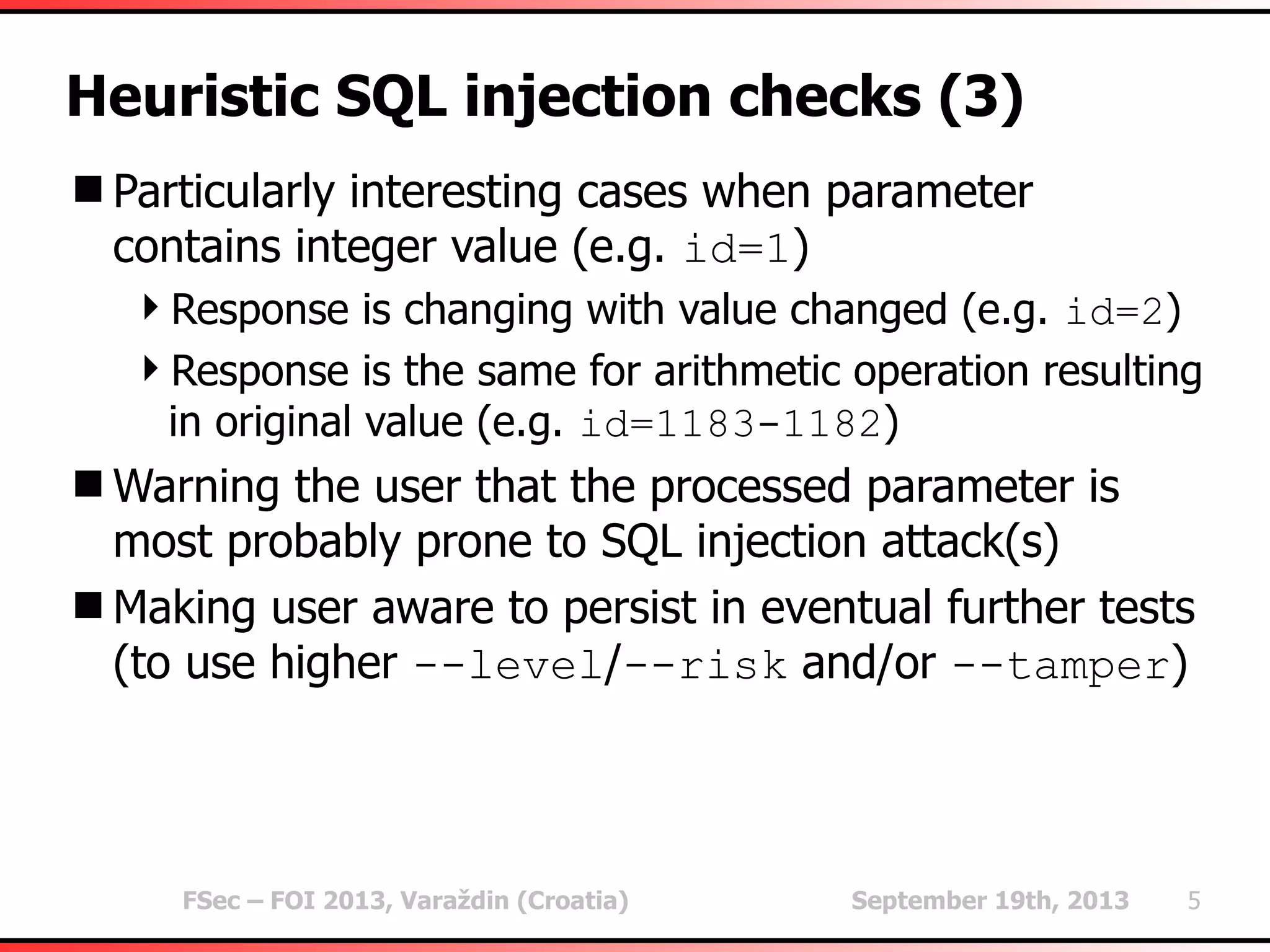
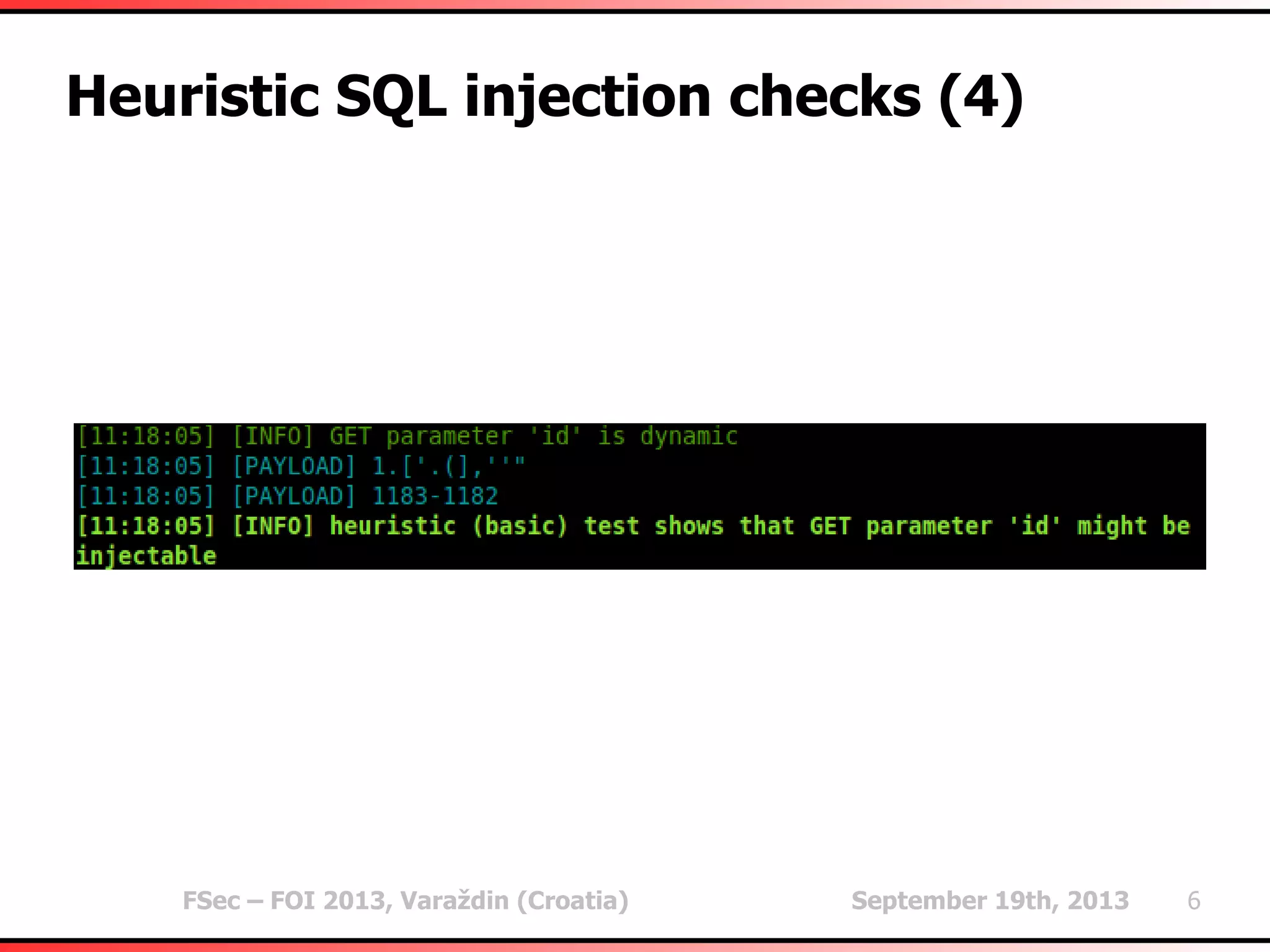
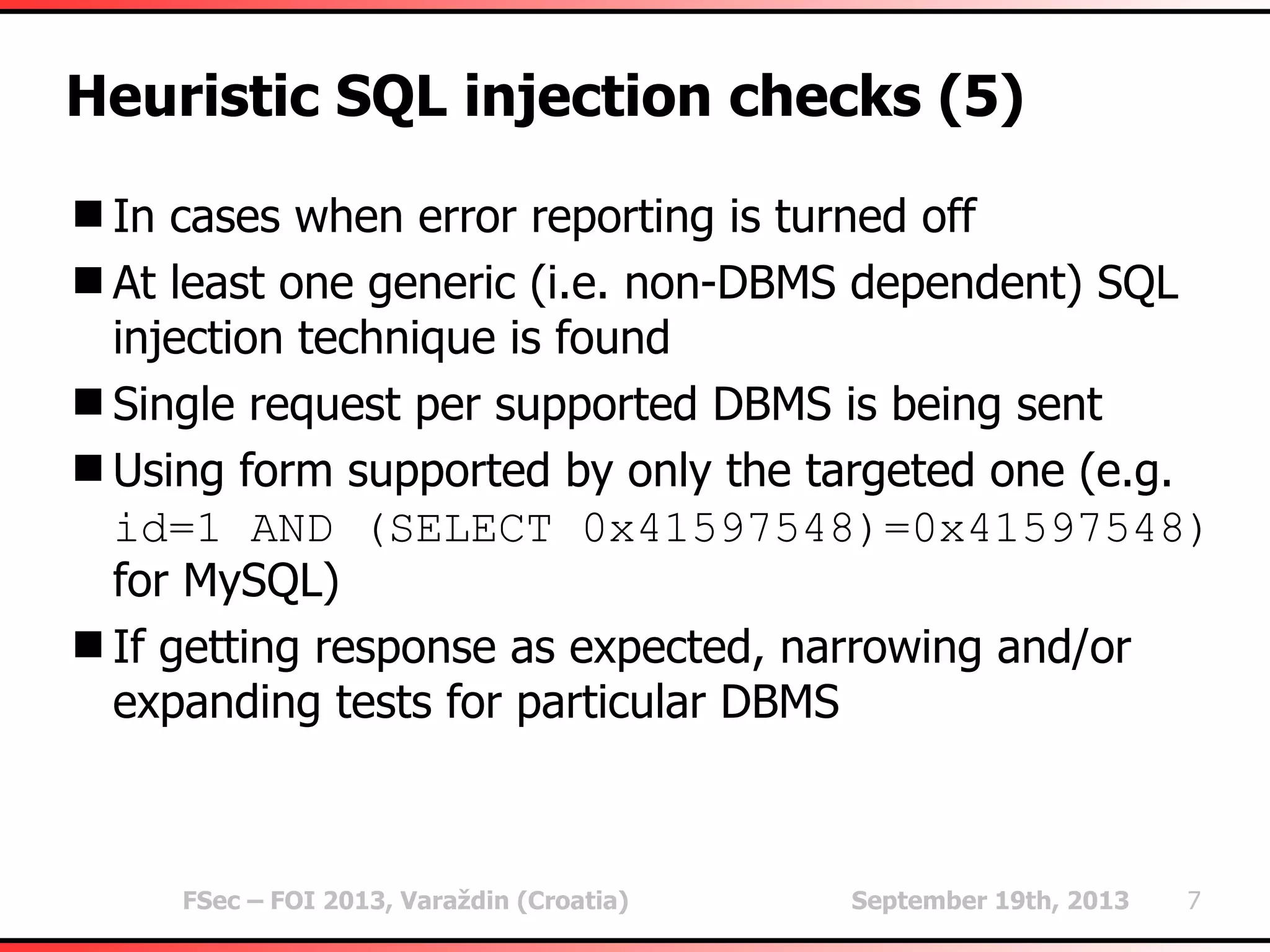
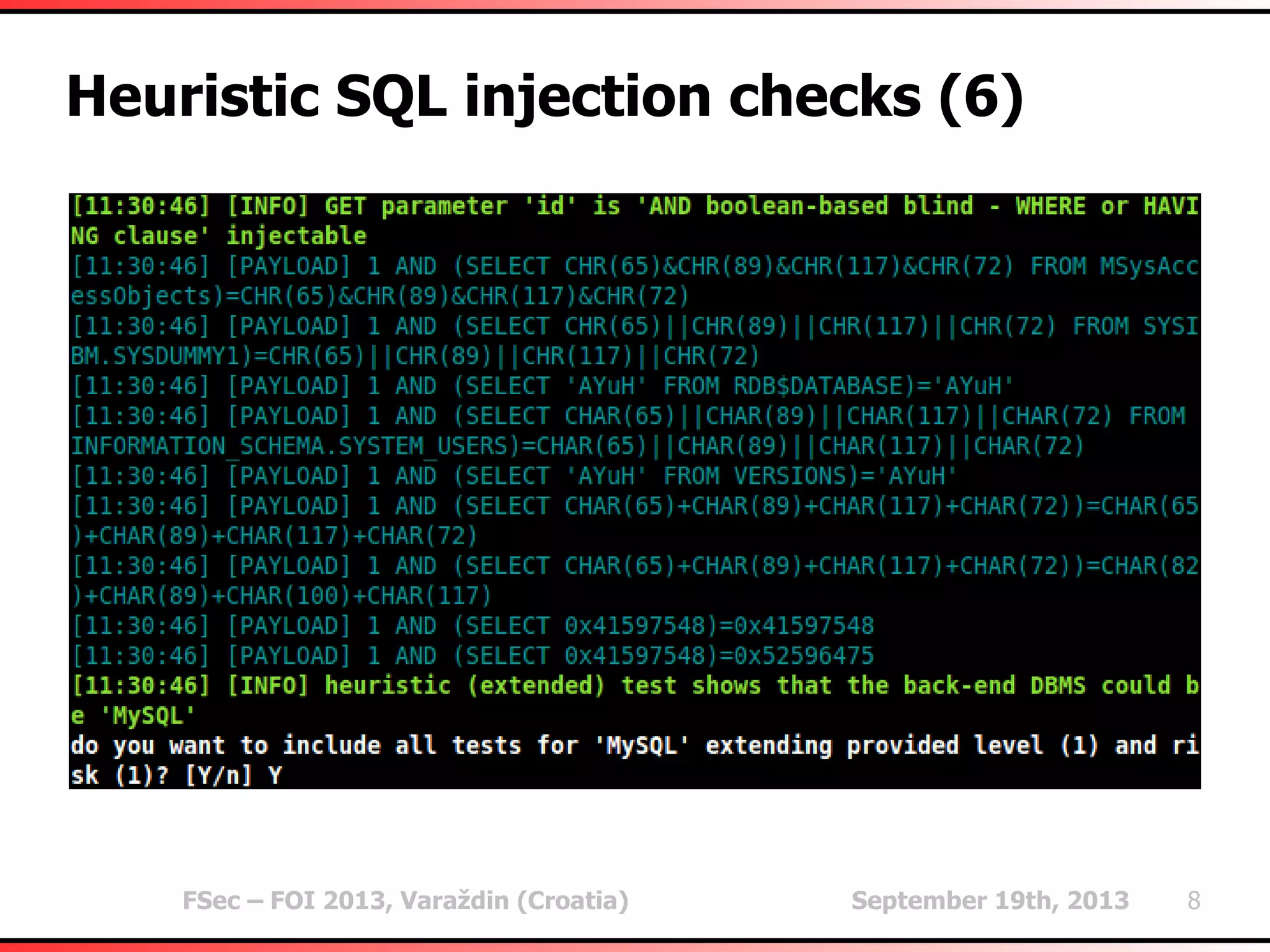
The document outlines heuristic methods utilized in SQLMap for detecting SQL injection vulnerabilities. It details various checks, including error-based, type casting, and WAF (Web Application Firewall) detection techniques, to help identify potential SQL injection points efficiently. Additionally, it covers methods for determining query field counts and addresses false positives and delays in response times during testing.


![FSec – FOI 2013, Varaždin (Croatia) September 19th, 2013 9
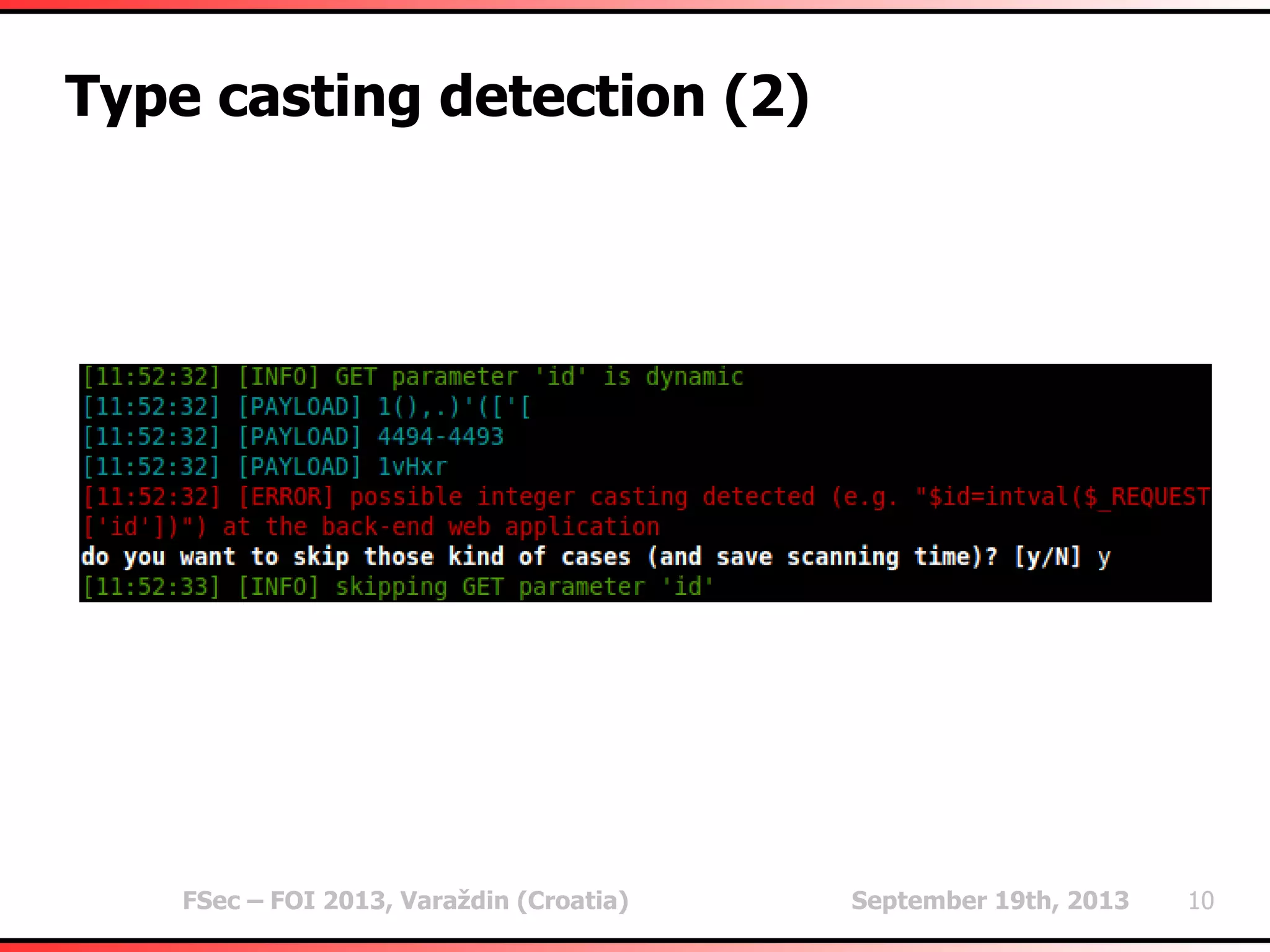
Type casting detection (1)
In some cases (preventive) hard type casting (e.g.
$id=intval($_REQUEST['id'])) is used
Especially noticeable on integer parameter values
(e.g. id=1)
Different responses for different integer values (e.g.
id=2)
Same response for appended random string values
(e.g. id=1vHxr)
High probability that the type casting is being used
(hence, not exploitable)
Warning the user of a potentially futile run](https://image.slidesharecdn.com/fsec-2013-miroslavstampar-heuristicmethodsusedinsqlmap-130919105020-phpapp02/75/Heuristic-methods-used-in-sqlmap-9-2048.jpg)