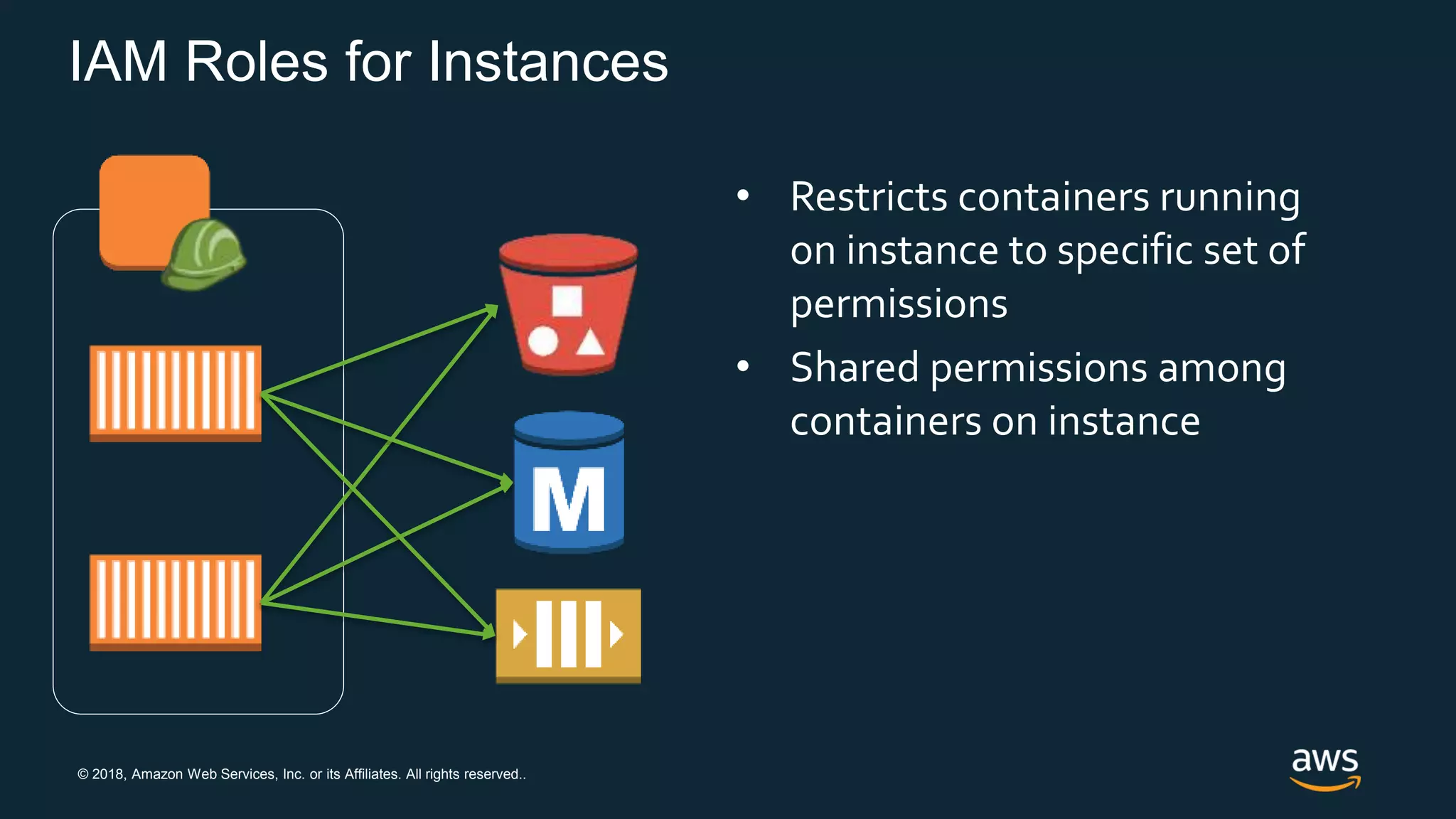
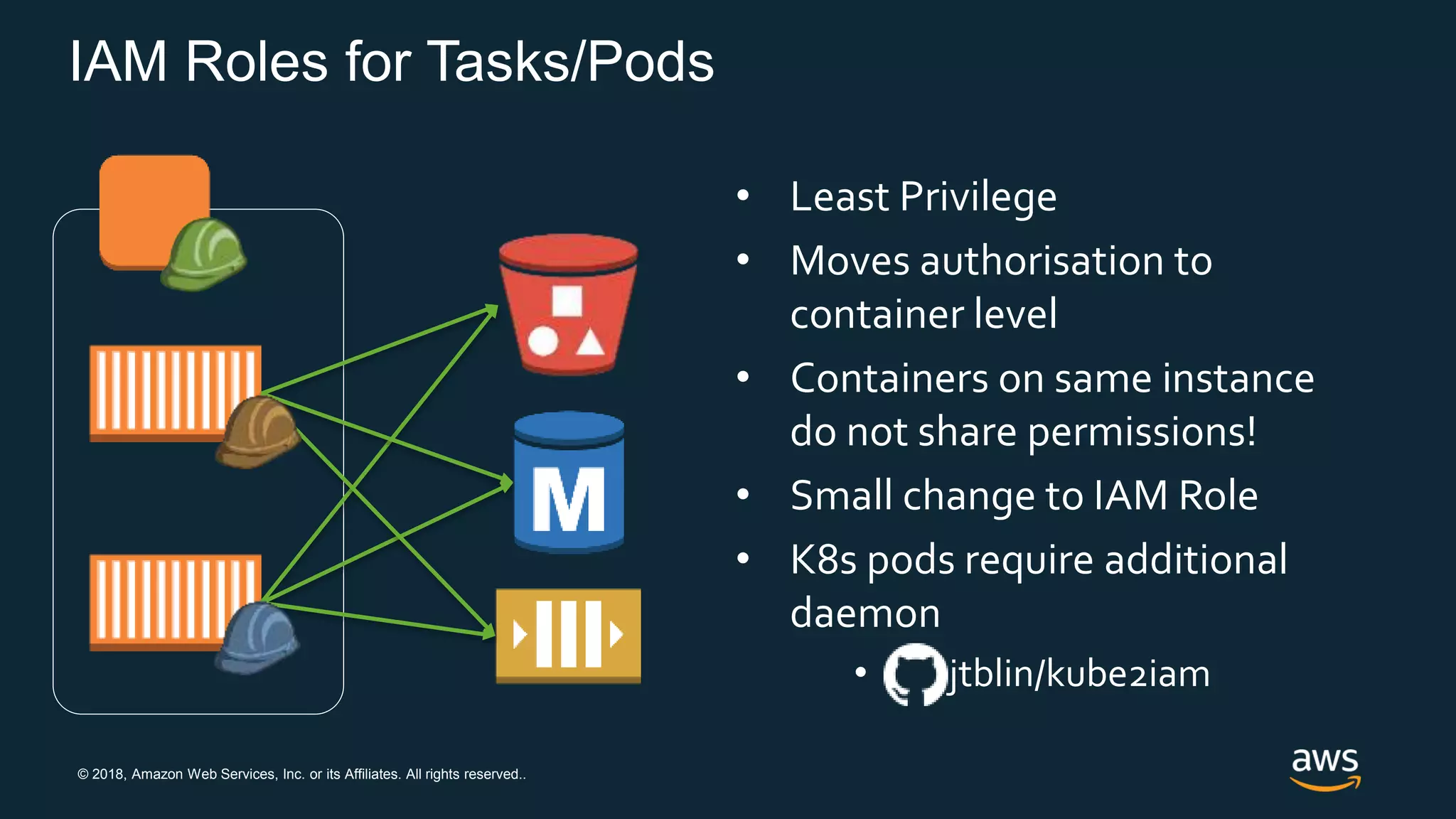
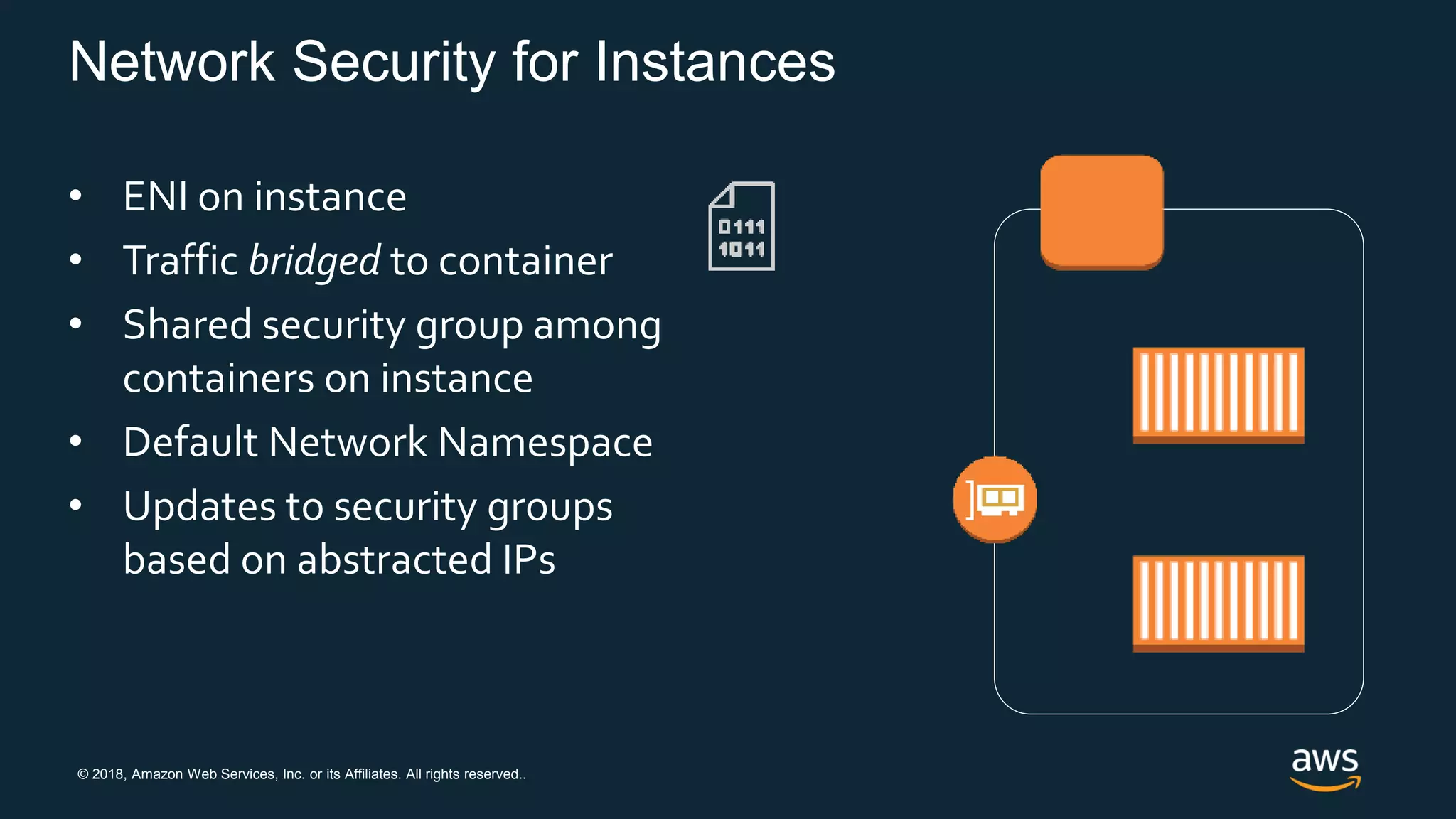
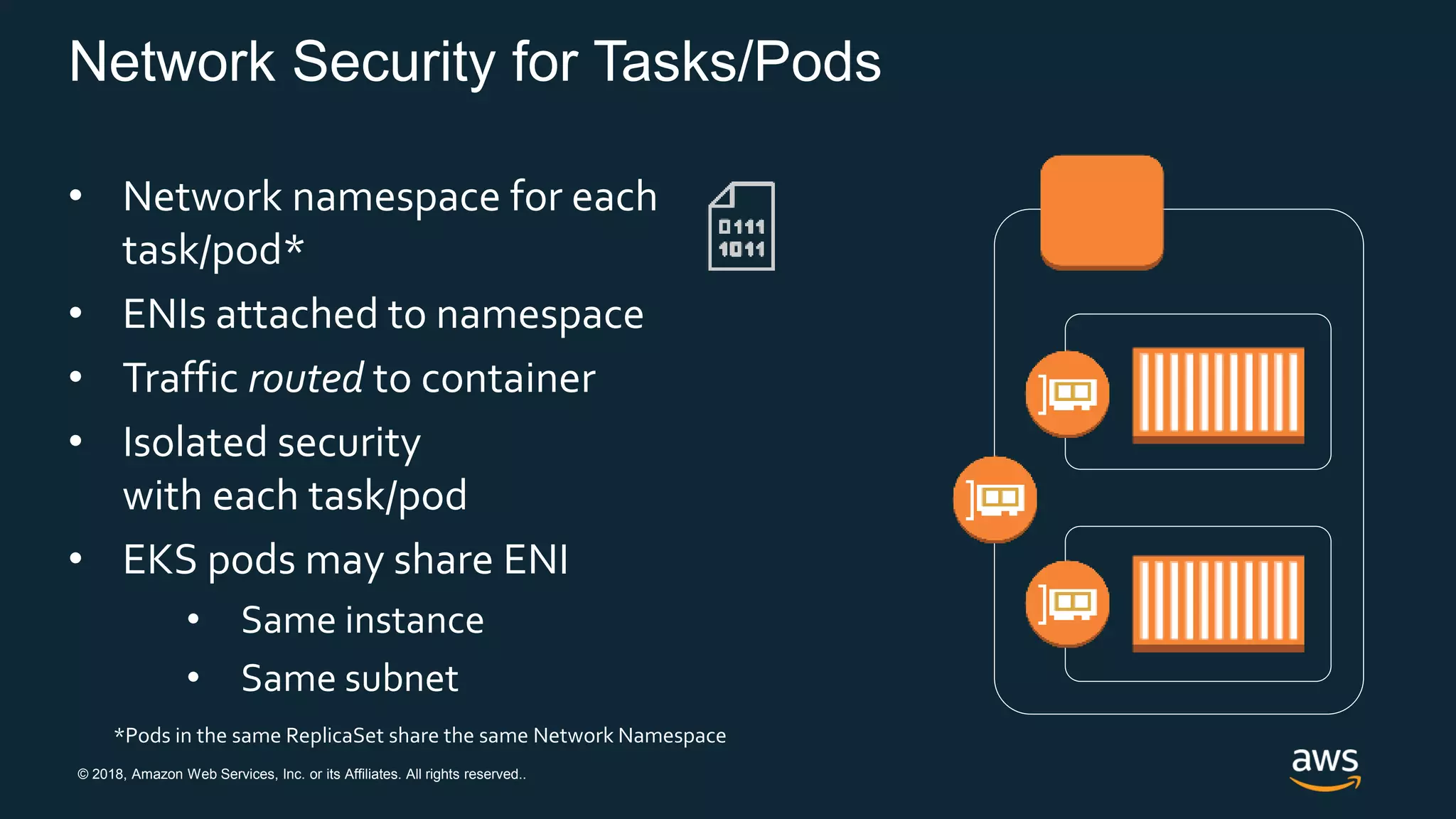
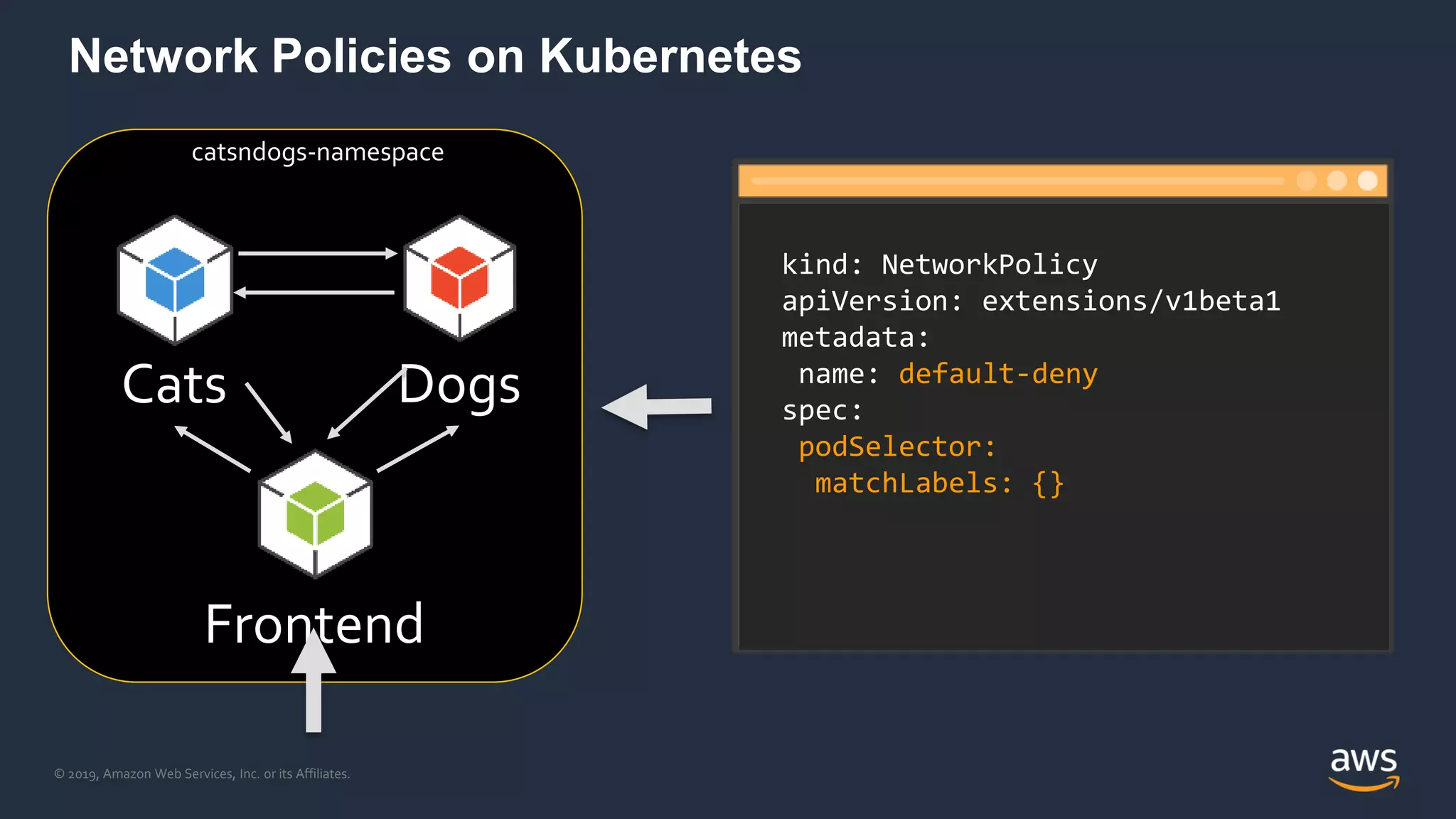
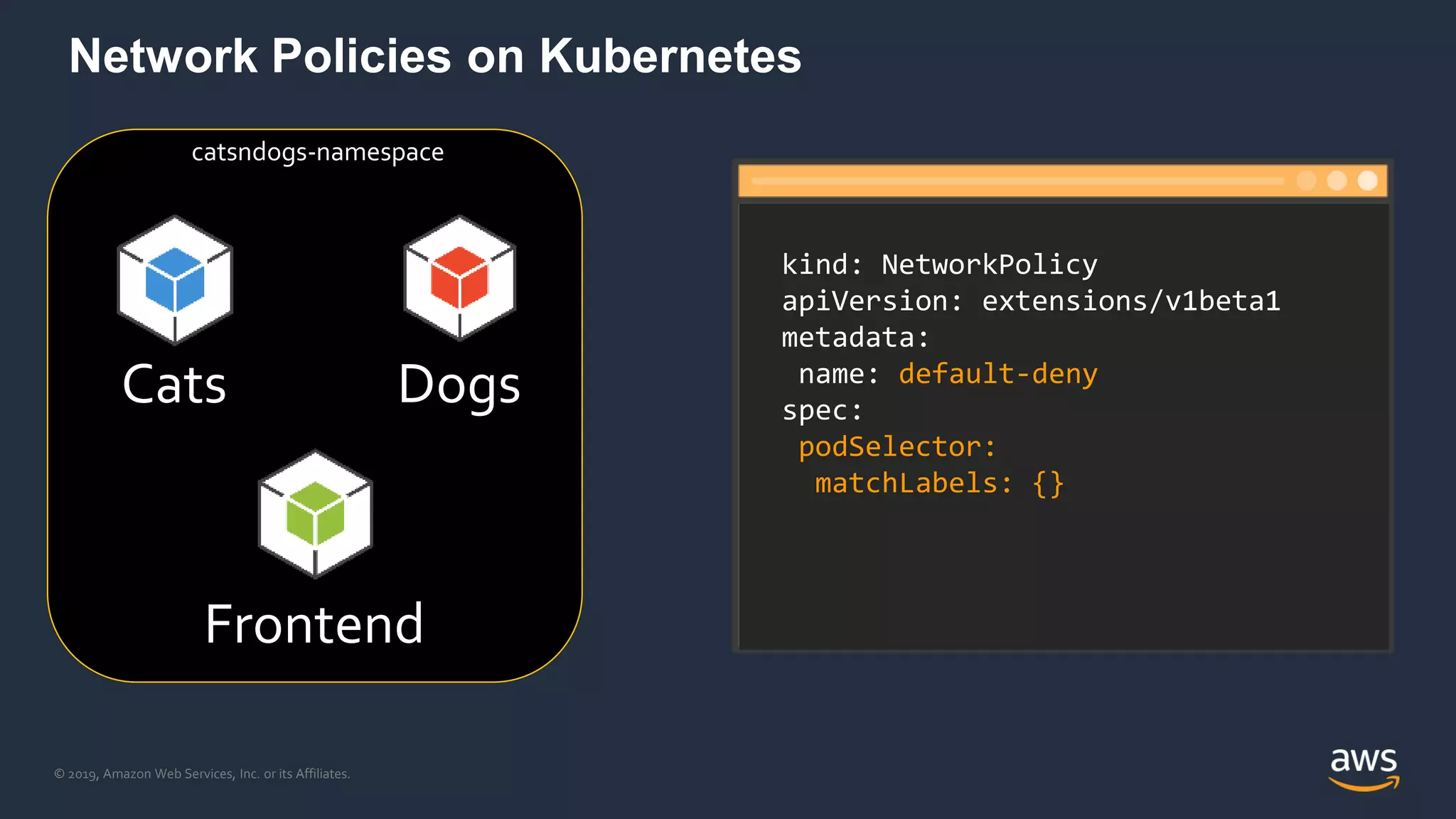
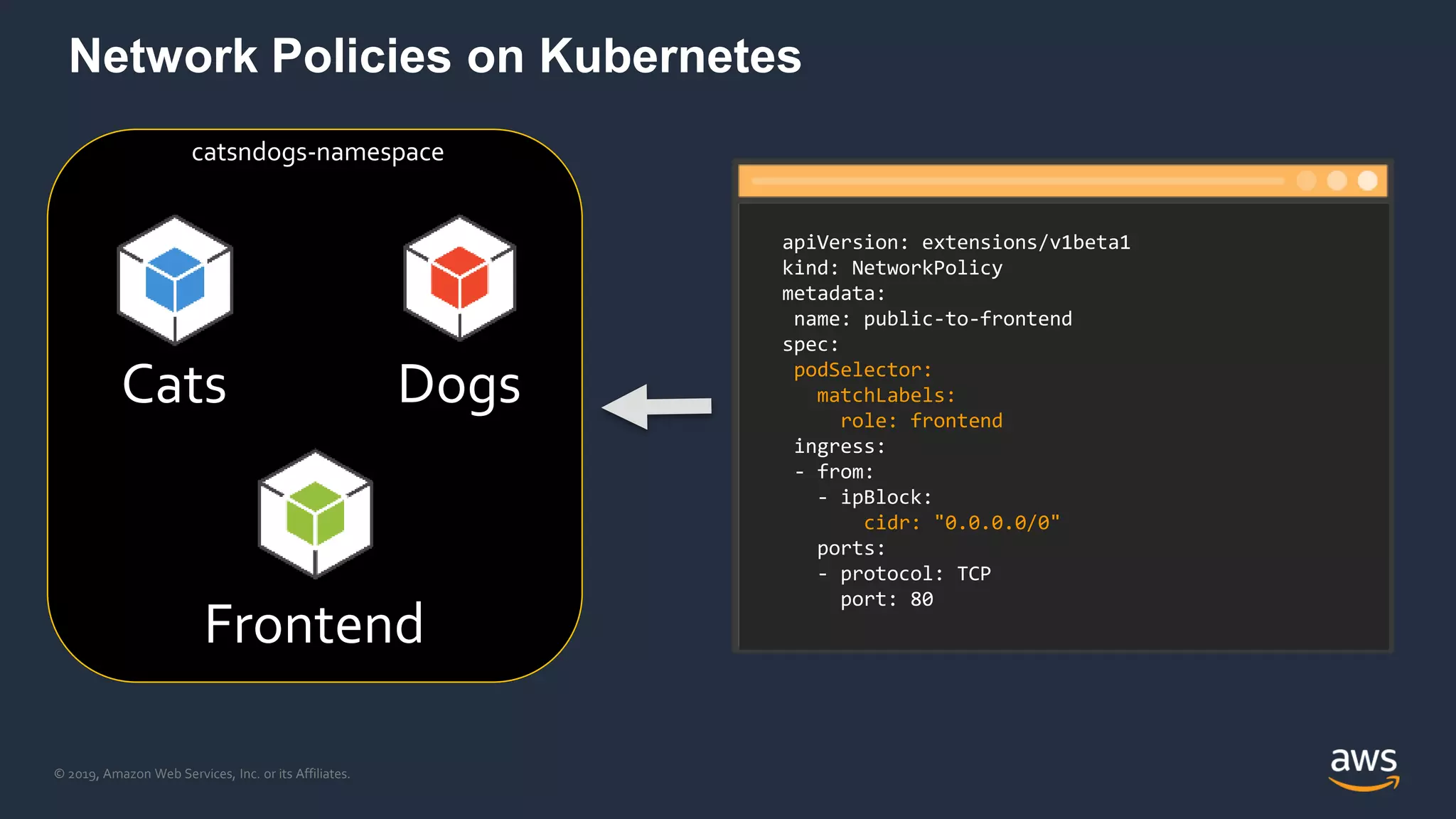
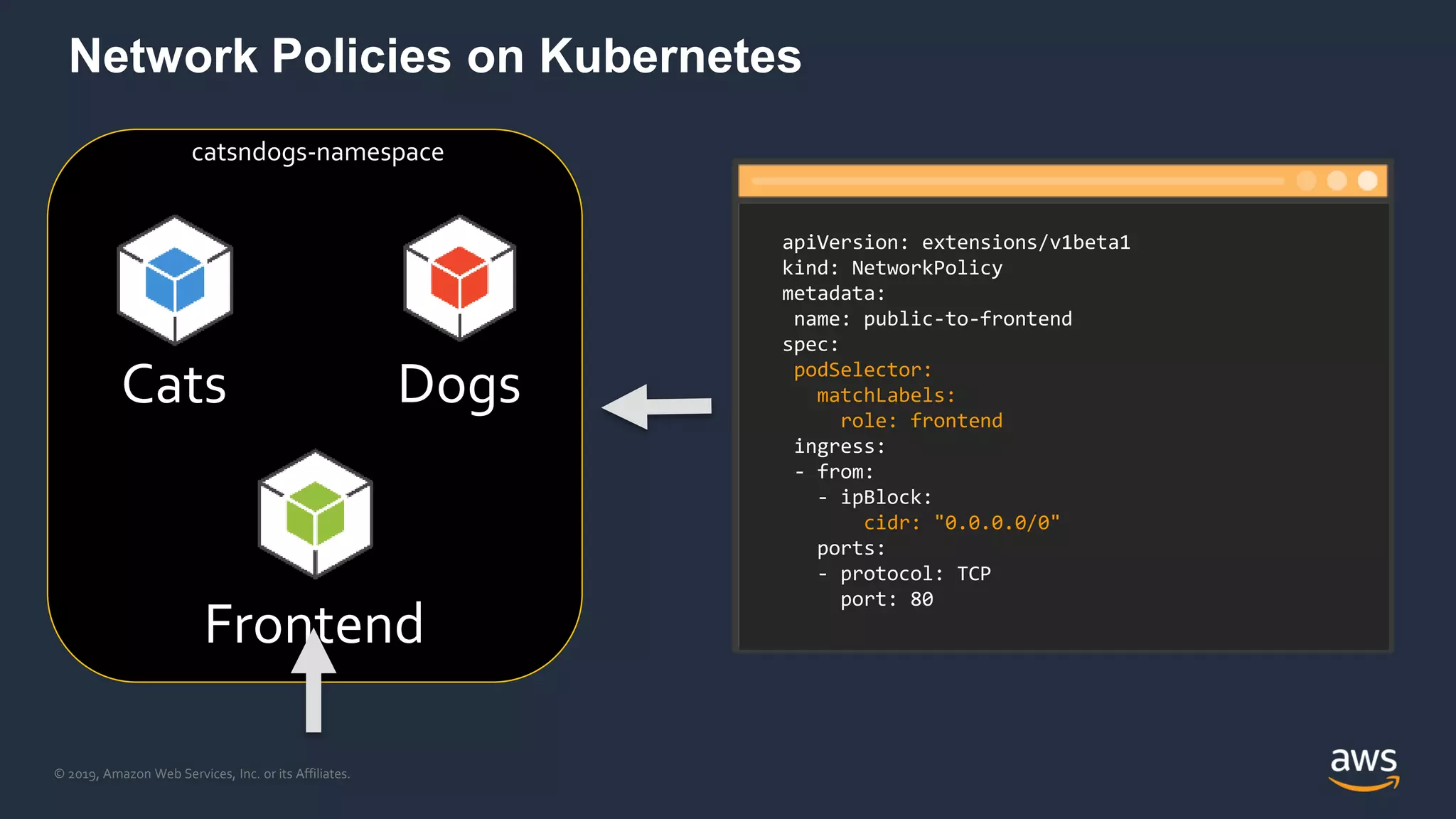
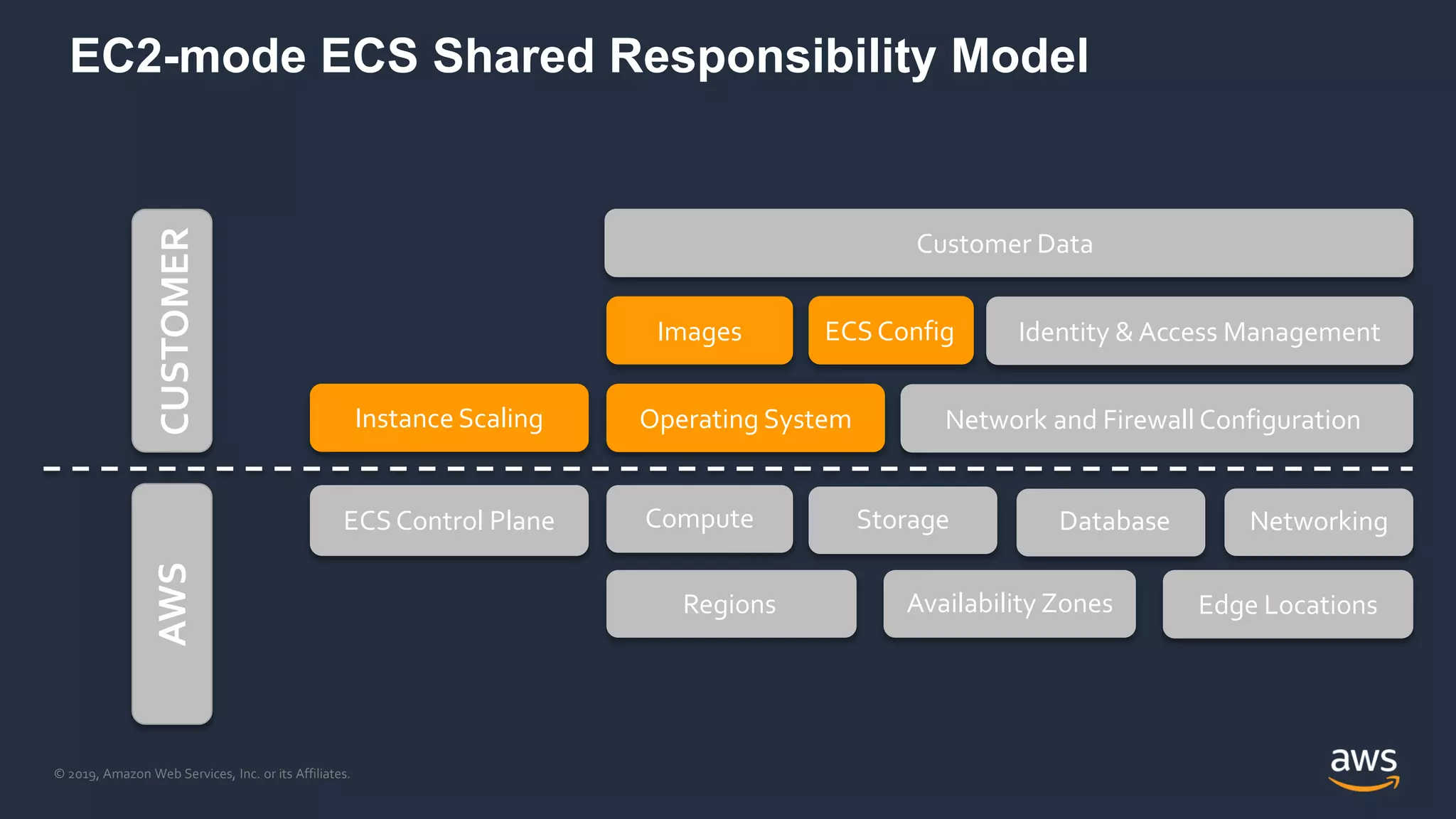
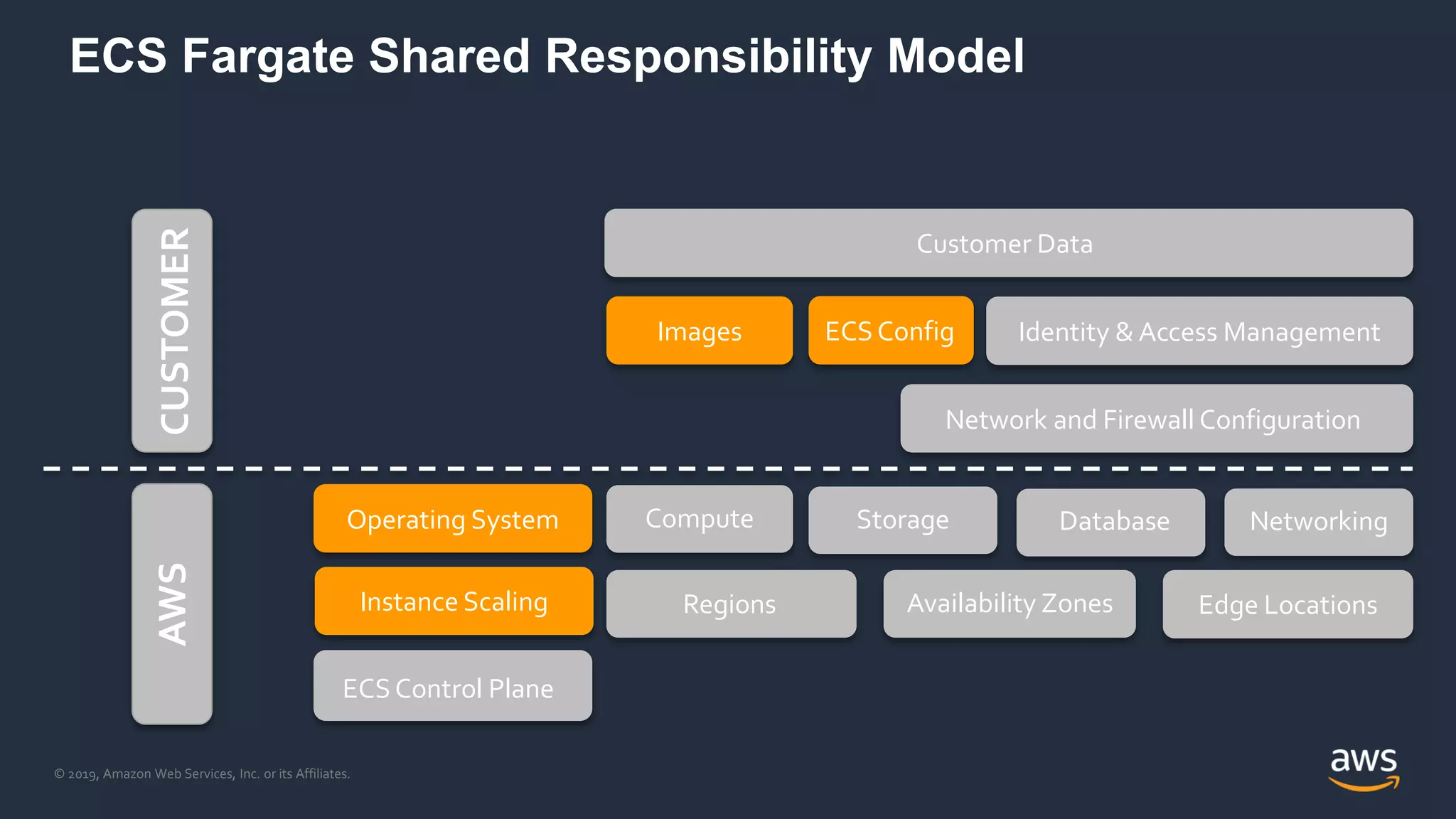
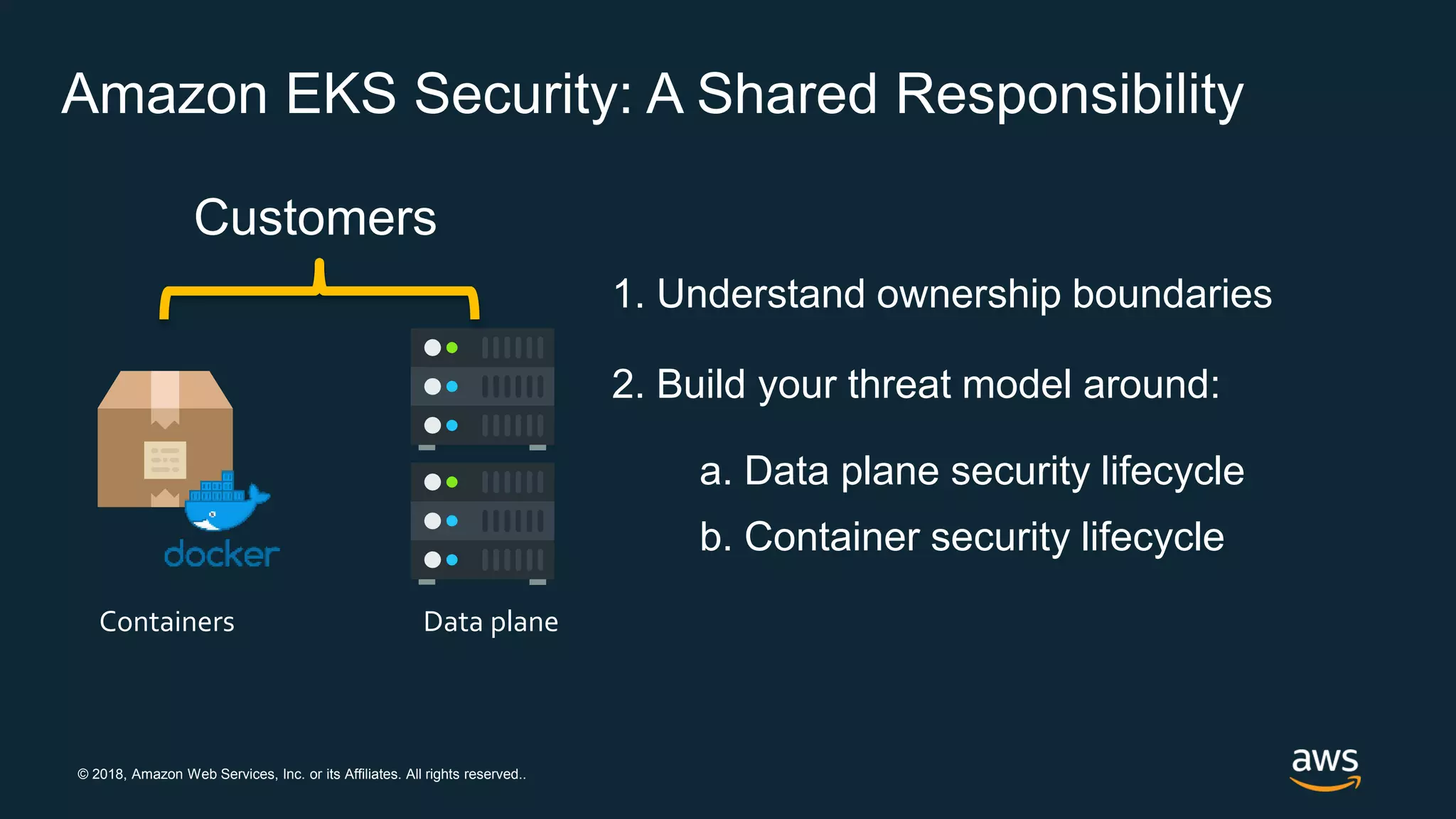
The document discusses securing containers on AWS, covering the history, implementation, and best practices for container security. It highlights the importance of understanding image sources, managing access controls, and maintaining operational security through continuous monitoring. Additionally, it touches on orchestration tools like Kubernetes and AWS-specific technologies such as EKS and Fargate for managing container deployments securely.









![© 2018, Amazon Web Services, Inc. or its Affiliates. All rights reserved..
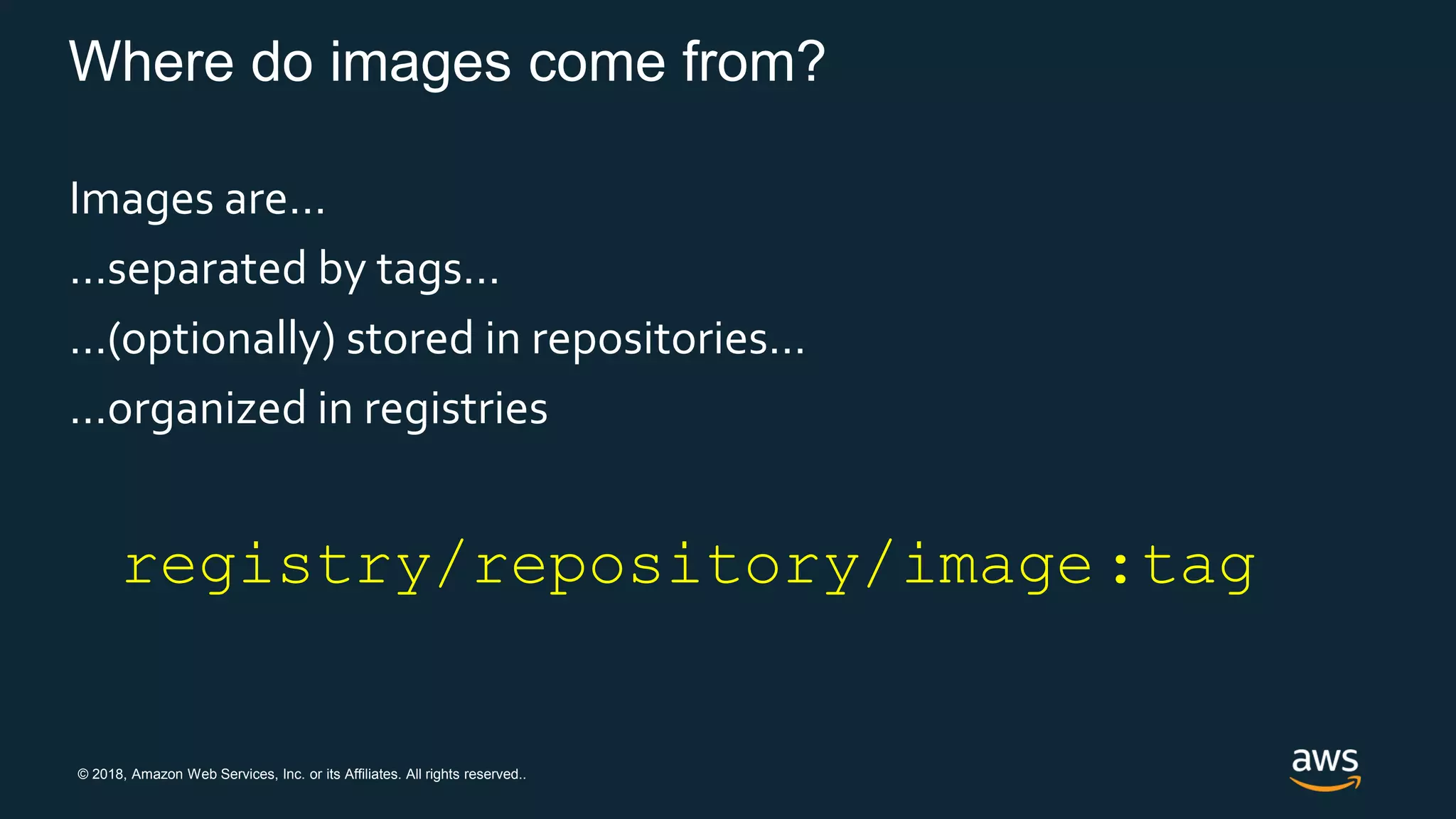
Multi-Stage Builds
• Each Dockerfile command is one layer
• Shell tricks (like &&) to reduce layers?
• Maintain multiple Dockerfiles?
• Dev Dockerfile: build/debug
• Prod Dockerfile: just run
• Solution: Multi-Stage Builds:
• Or build without Docker at all?
• Kaniko / Skaffold
FROM golang:1.7.3
WORKDIR /go/src/scott/app
COPY app.go .
RUN go build -o app .
FROM alpine:3.7
WORKDIR /root/
COPY --from=0 /go/src/scott/app .
CMD ["./app"]](https://image.slidesharecdn.com/csa-container-security-in-aws-dw-190704165344/75/Csa-container-security-in-aws-dw-31-2048.jpg)