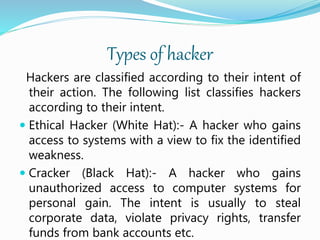
The document discusses hacking and ethical hacking. It defines hacking as identifying weaknesses in computer systems to exploit them, and defines a hacker as someone who finds and exploits weaknesses. It describes different types of hackers including ethical (white hat) hackers who fix weaknesses, crackers (black hat) who hack for personal gain, grey hats who identify weaknesses to reveal them, and script kiddies who use existing tools. The document explains that ethical hacking identifies weaknesses to develop countermeasures and protects organizations, and is legal if certain rules and certifications are followed.