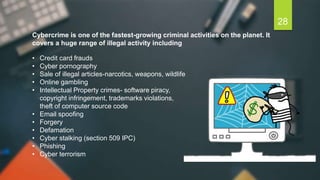
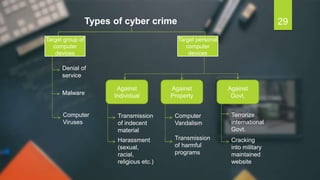
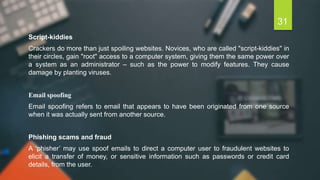
The document discusses the Information Technology Act of 2000 in India. It was passed to promote e-commerce and regulate electronic transactions. Some key points:
- The Act provides legal recognition for digital signatures and electronic documents to facilitate online transactions and e-governance.
- It established regulatory authorities for certifying digital signature certificates and created provisions to prevent cybercrimes like hacking and publishing of obscene content online.
- Major amendments in 2008 introduced concepts of electronic signatures beyond digital signatures, data protection responsibilities for companies, and new cybercrimes under the Act.