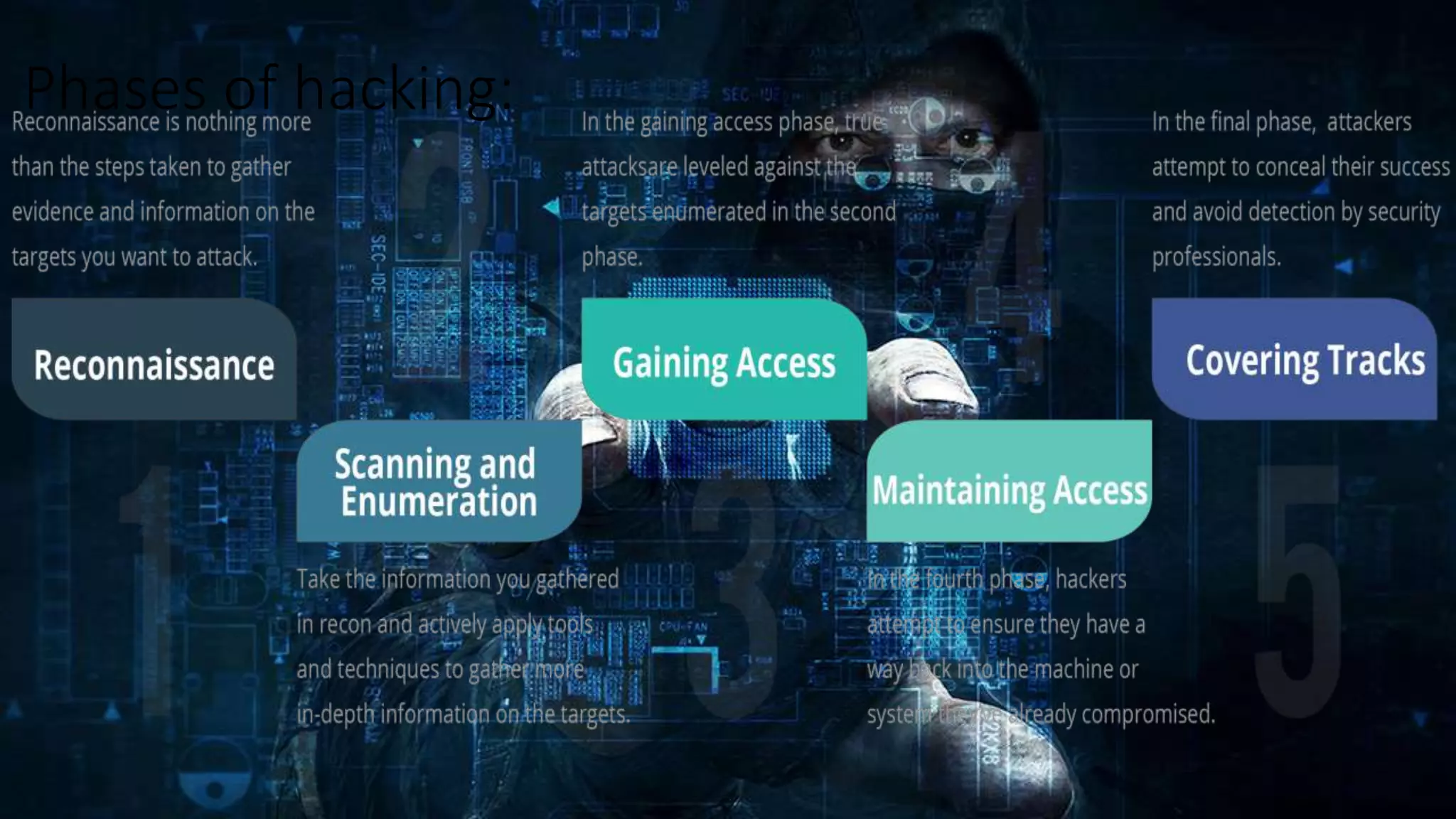
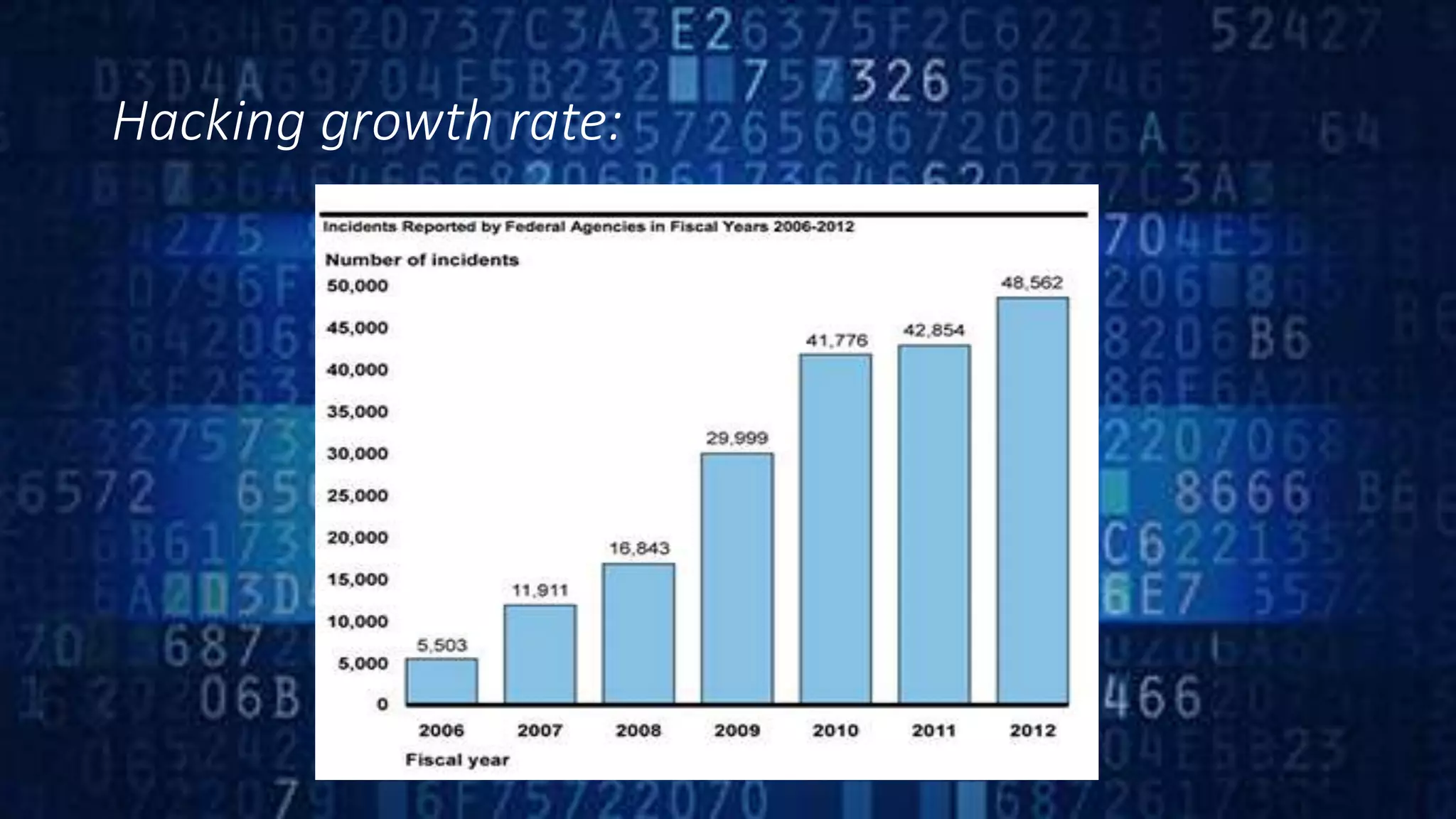
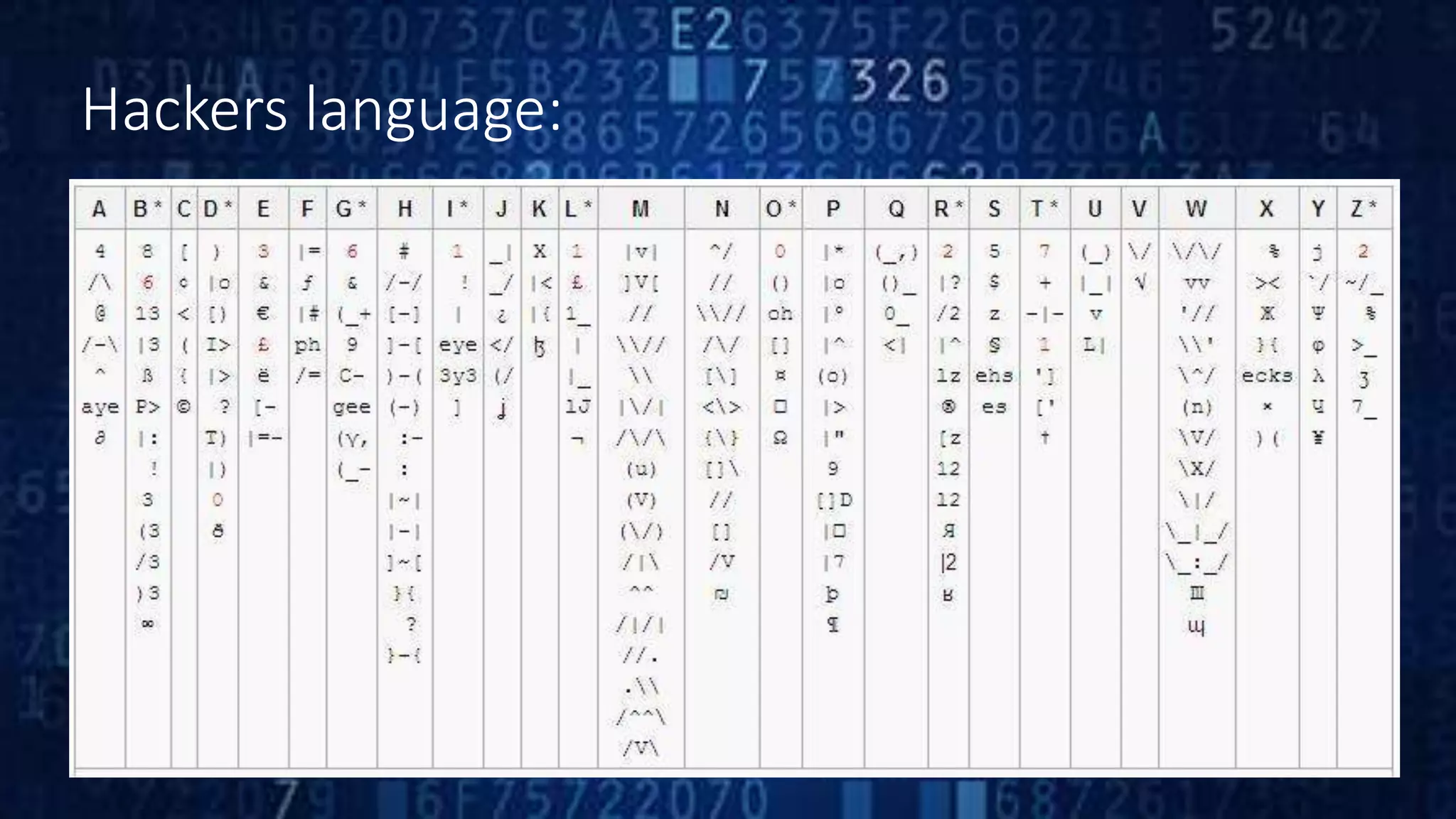
Ethical hacking involves legally hacking into computer systems and networks to identify security vulnerabilities for clients, with their permission. It is part of an overall security program. Ethical hackers have strong programming and networking skills. There are three types of hackers - white hat hackers who use skills for defense, black hat hackers who engage in malicious activities, and grey hat hackers who work both offensively and defensively. Ethical hacking is important for security testing and system hardening to improve security and prevent breaches. However, there is a risk that ethical hackers could misuse knowledge or sensitive information.