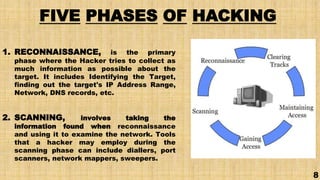
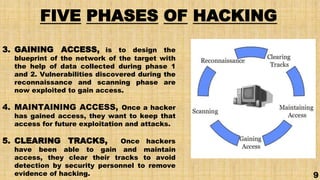
This document discusses hacking and ethical hacking. It defines different types of hackers such as white hat, grey hat, and black hat hackers. It also outlines types of hacking like website, network, email, and password hacking. The document explains that ethical hacking is legal and done with permission to test security vulnerabilities. It notes the five phases of hacking as reconnaissance, scanning, gaining access, maintaining access, and clearing tracks. Finally, it discusses the skills, advantages, disadvantages and career opportunities in ethical hacking.