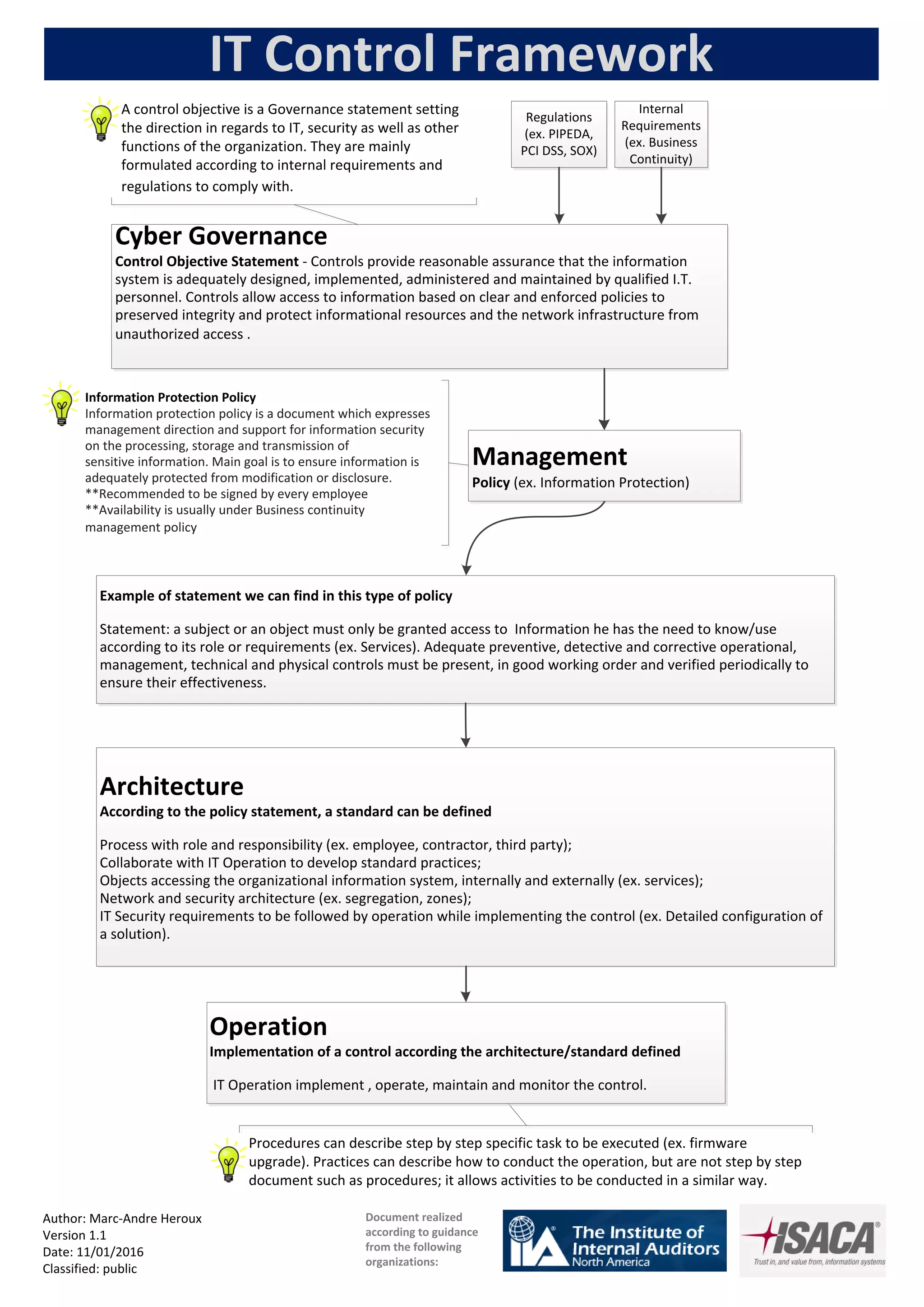
Controls are designed and implemented by qualified IT personnel to provide reasonable assurance that the information system is adequately protected. Access to information is based on clear and enforced policies to preserve integrity and protect informational resources and network infrastructure from unauthorized access. A control objective statement sets the direction for IT, security, and other organizational functions according to internal requirements and regulations. An information protection policy expresses management support for securing sensitive information and ensuring it is adequately protected from modification or disclosure.