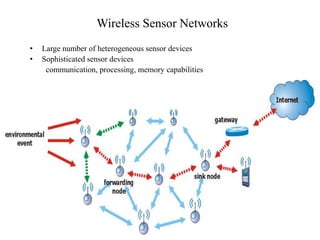
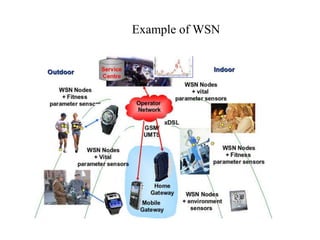
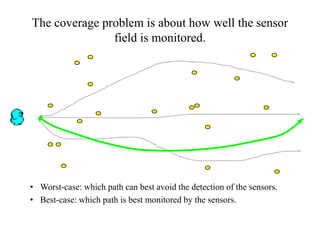
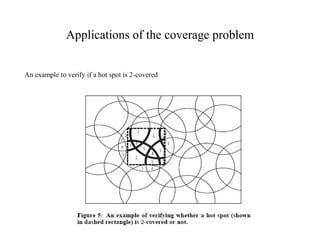
This document discusses energy efficient and secured intrusion detection in wireless sensor networks. It begins with an introduction to wireless sensor networks, their applications such as environmental monitoring and military surveillance, and their characteristics including being energy constrained and prone to errors. It then discusses challenges in wireless sensor networks related to heterogeneity, distributed processing, bandwidth, and energy efficiency. Next, it covers the coverage problem in determining how well an area is monitored by sensors and discusses worst-case and best-case coverage scenarios. It also introduces the concept of hot spots which are important areas that need more sensor coverage. Finally, it provides references for further information.