The document outlines 4 steps for embedding security into the software development lifecycle (SDLC):
1. Introduce automated security scanning tools like SonarQube and OWASP ZAP to find vulnerabilities and train developers on common risks.
2. Incorporate OWASP's proactive controls into the SDLC to shift from reactive scanning to secure coding.
3. Implement the OWASP Application Security Verification Standard (ASVS) to manage security based on risk levels.
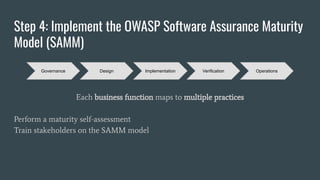
4. Use the OWASP Software Assurance Maturity Model (SAMM) for a maturity-based approach to securing the SDLC and optimizing resources.