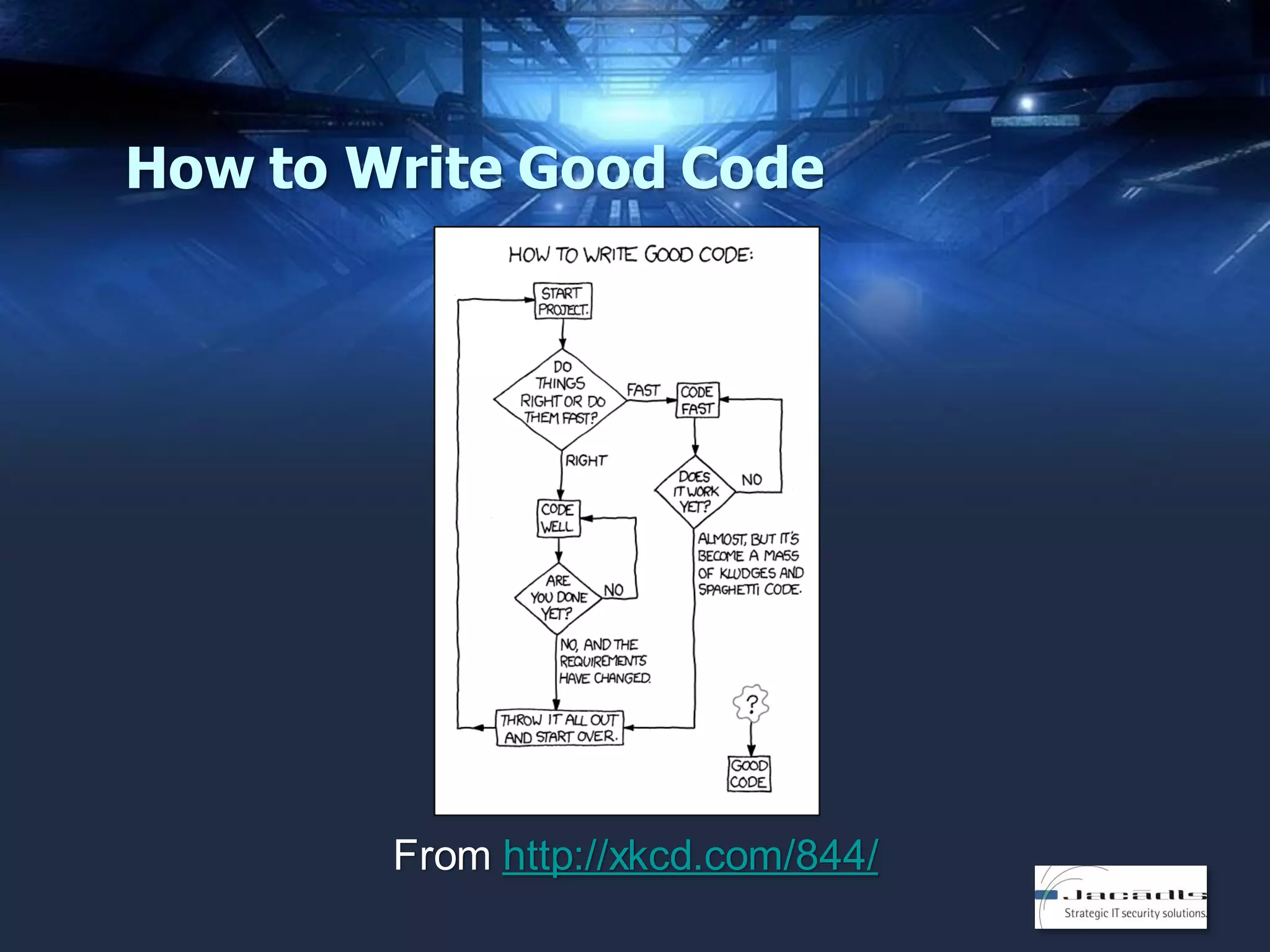
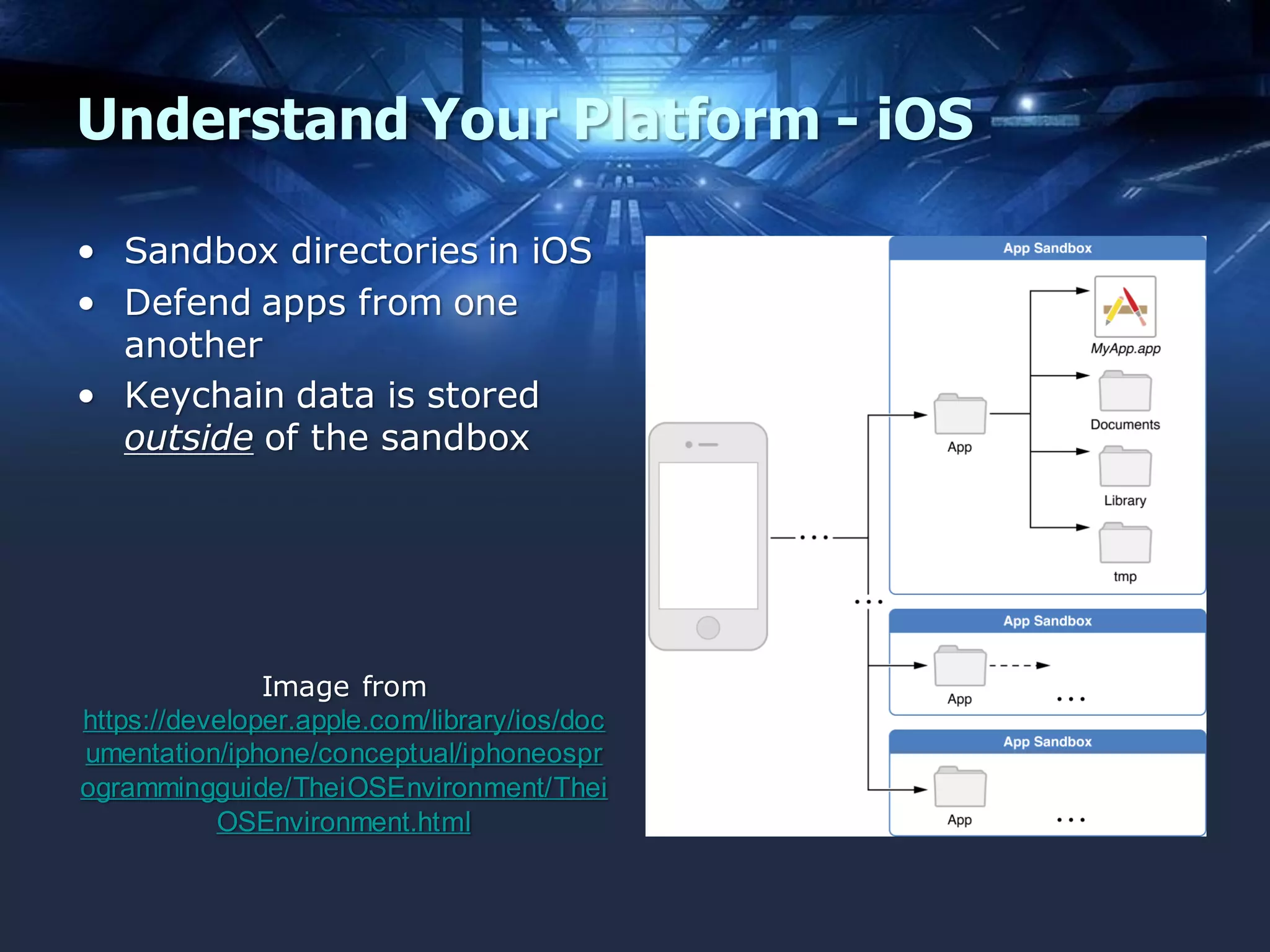
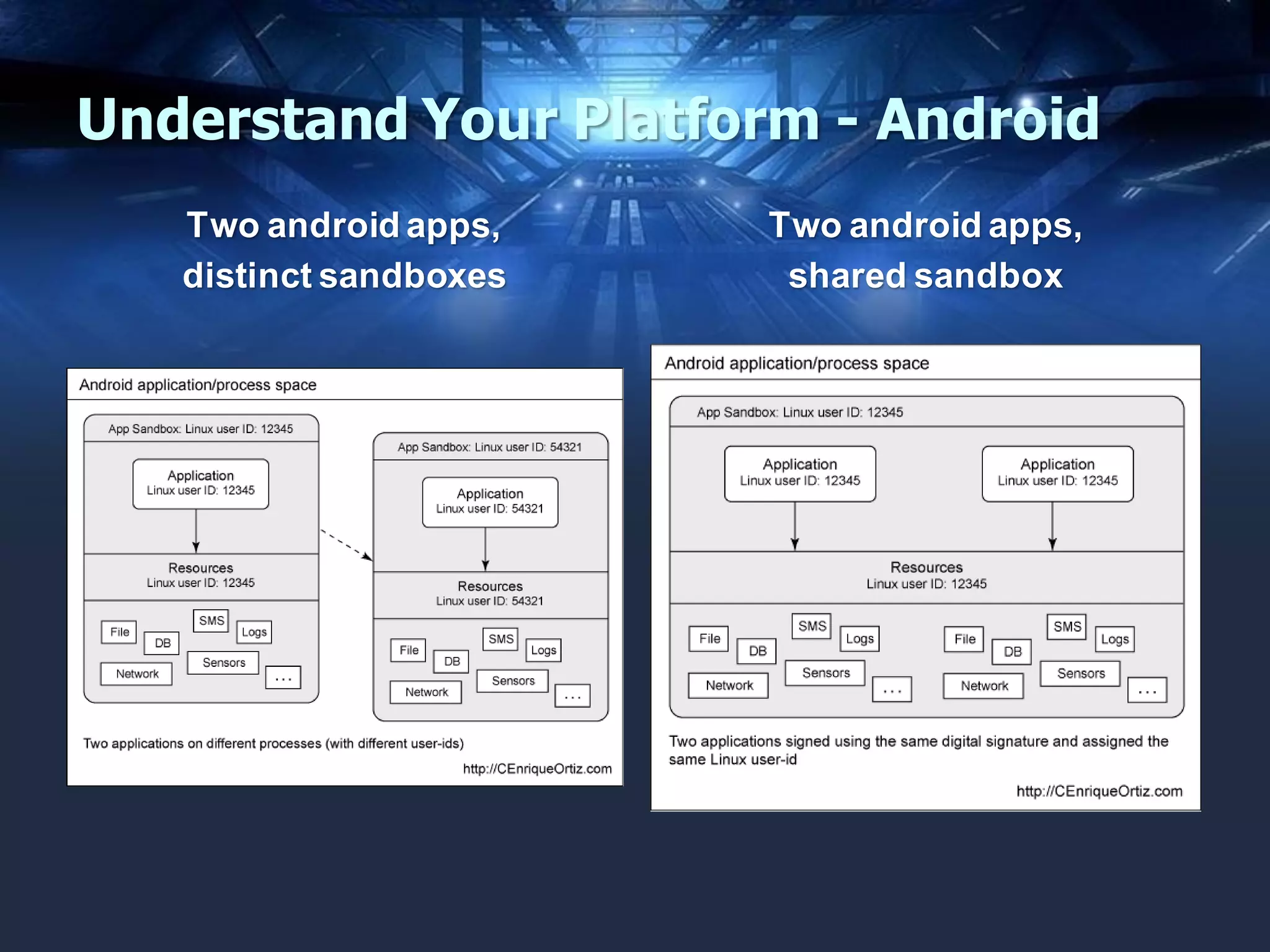
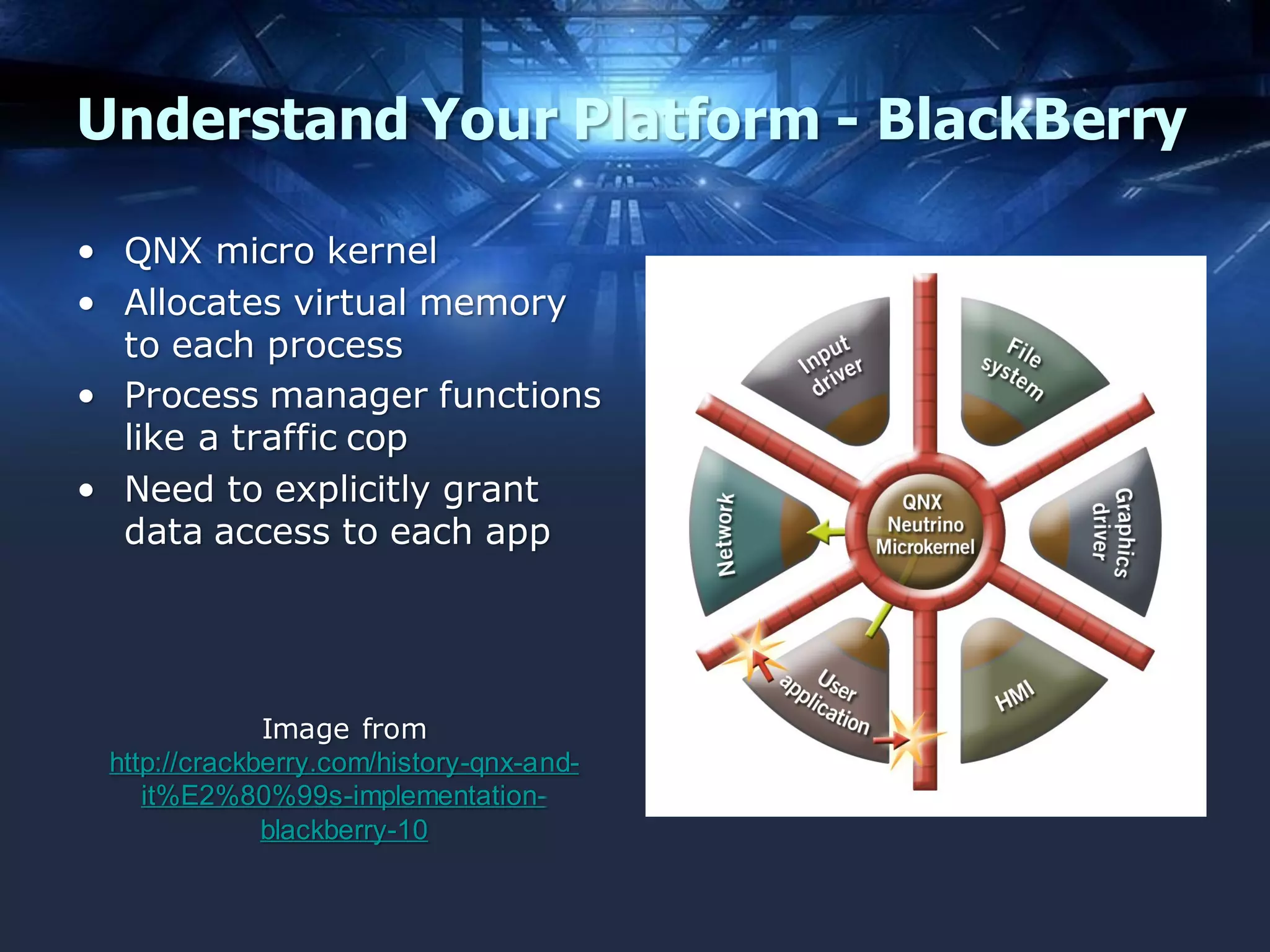
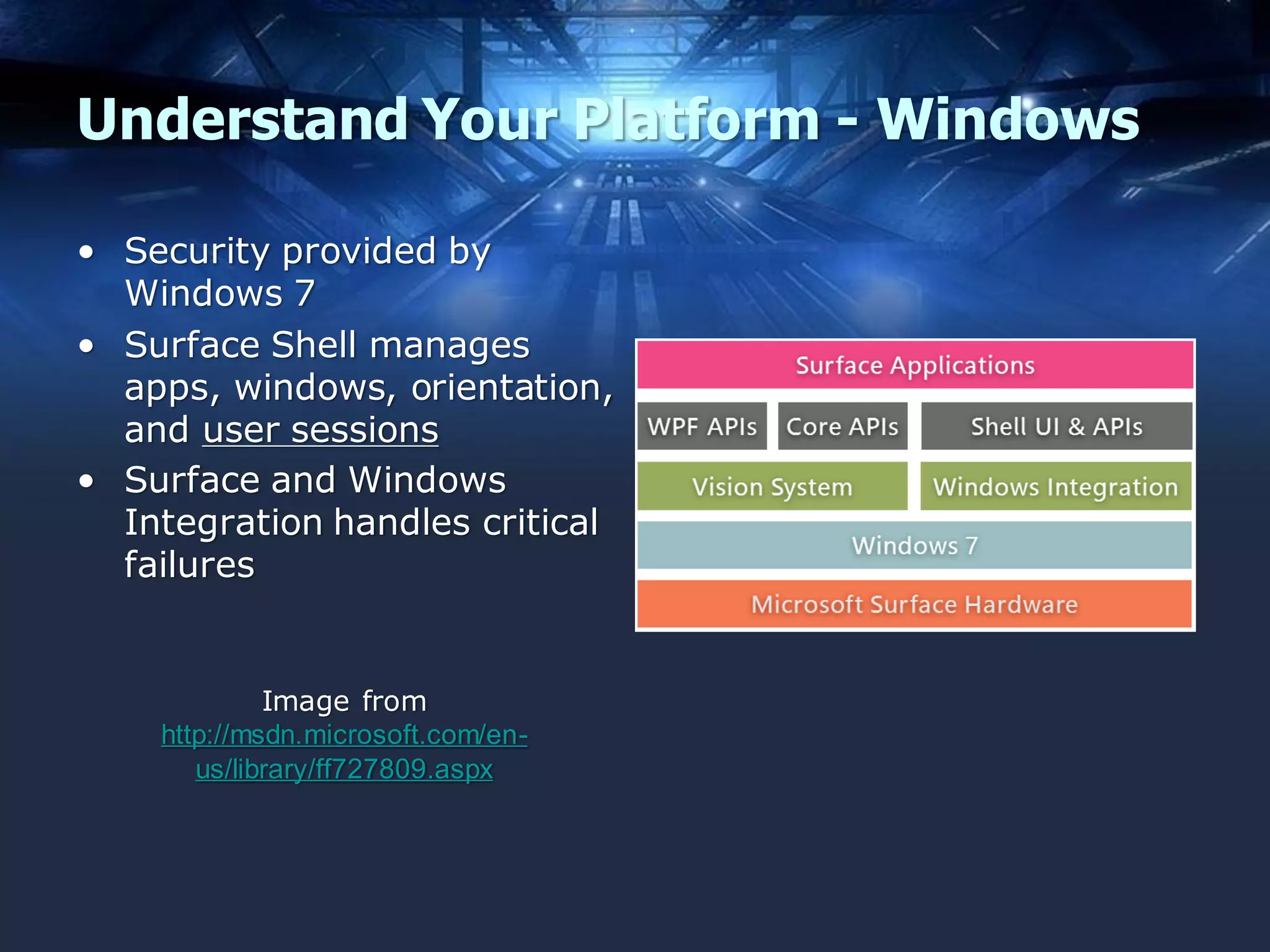
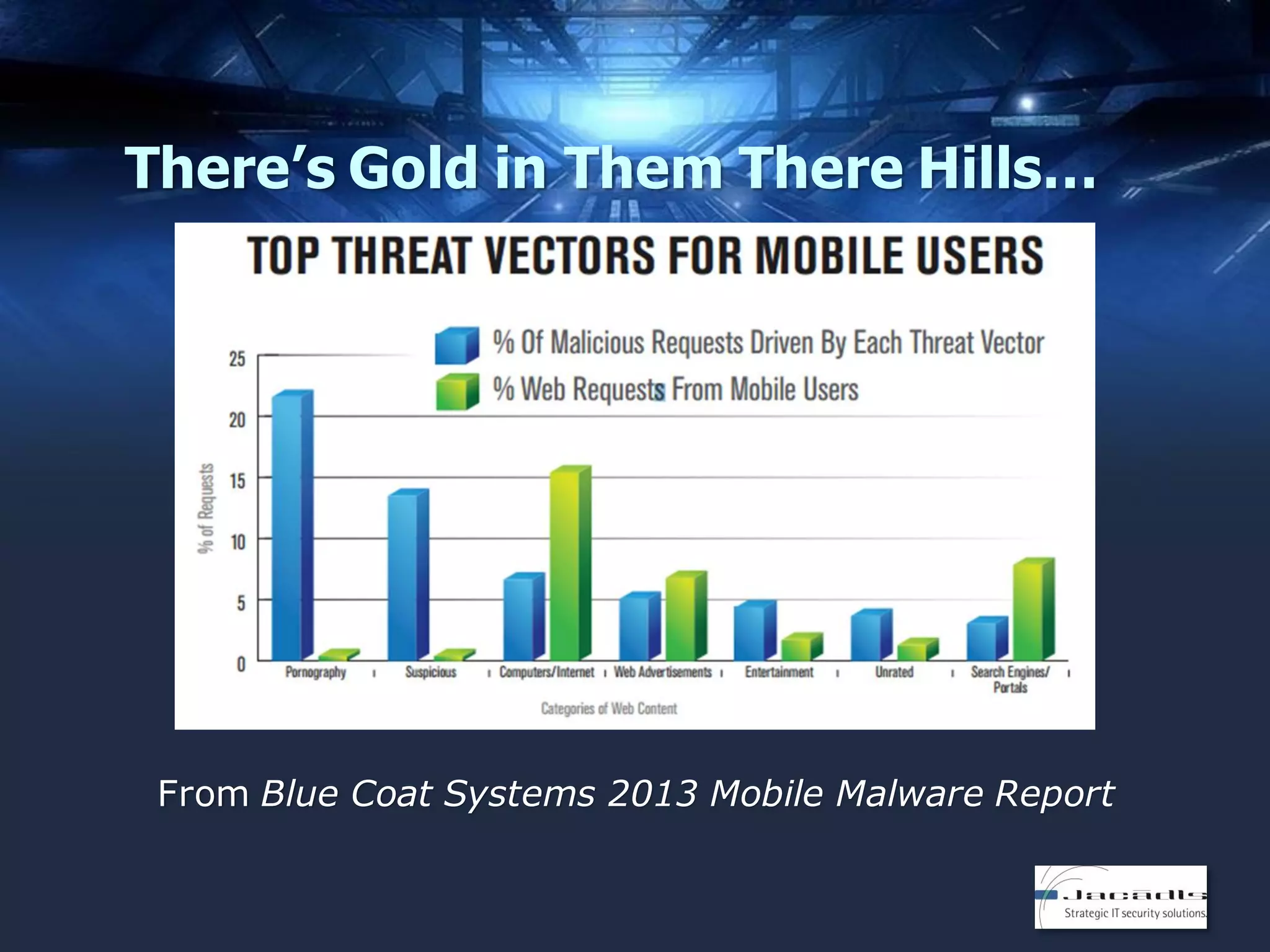
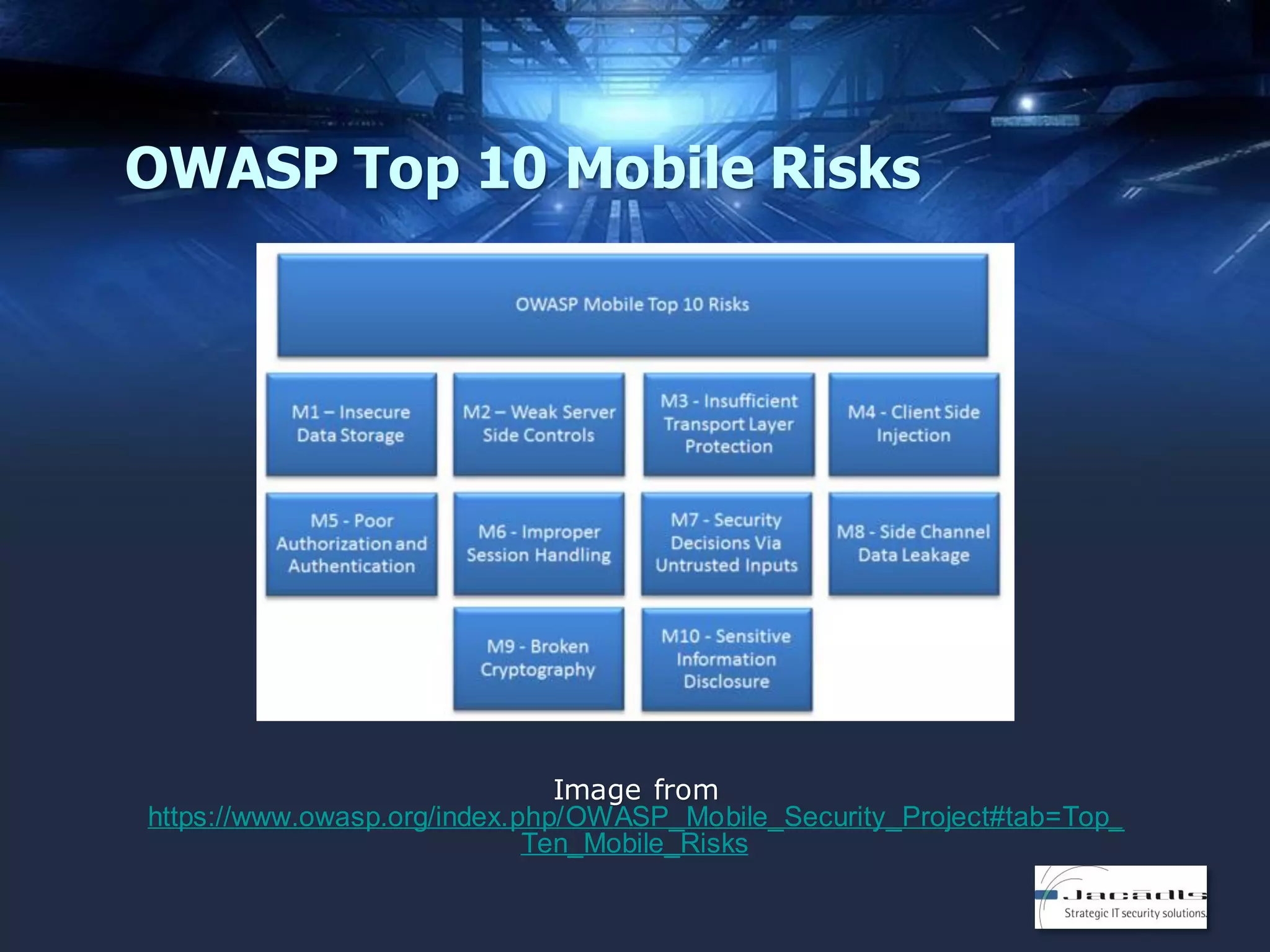
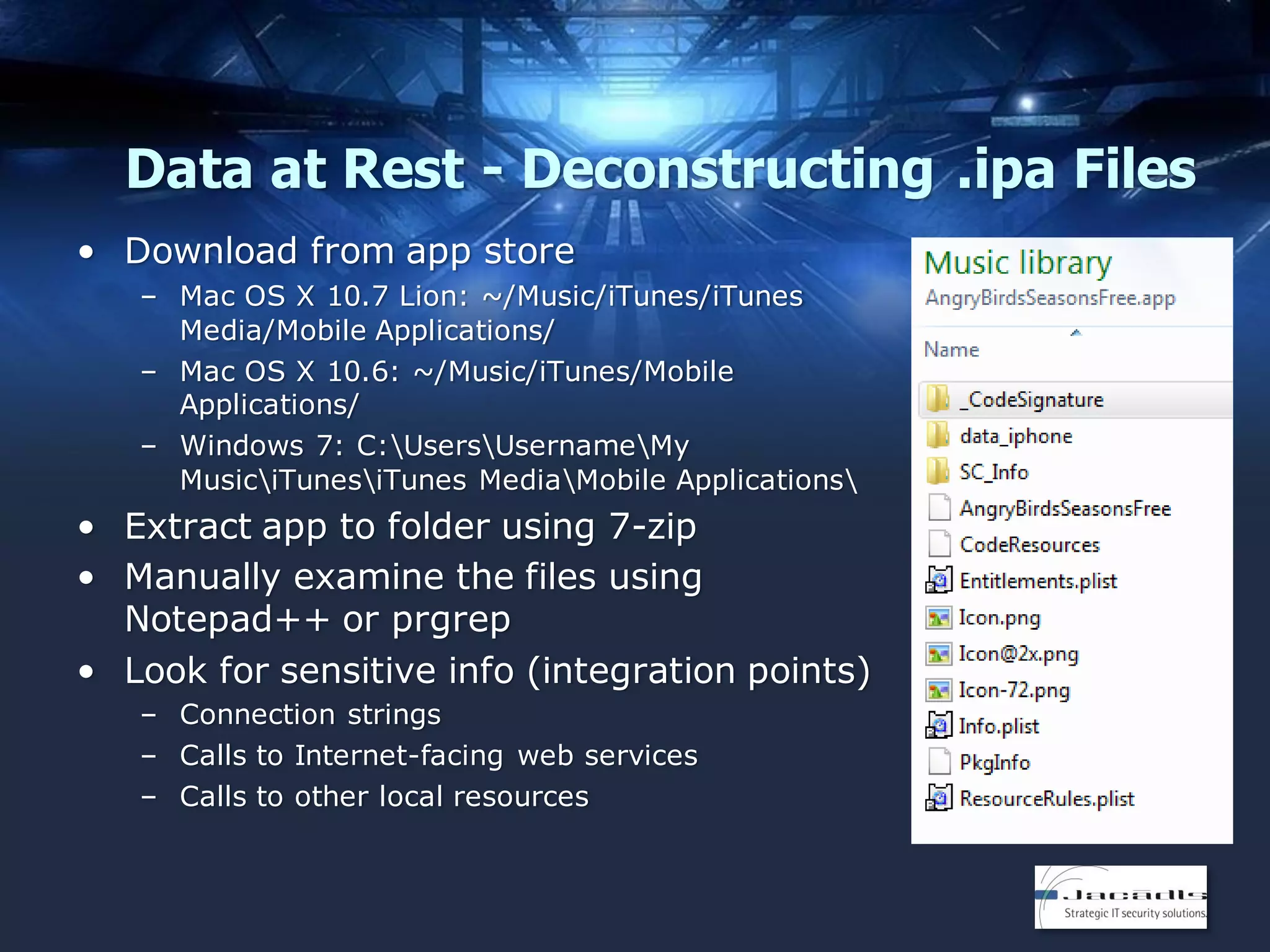
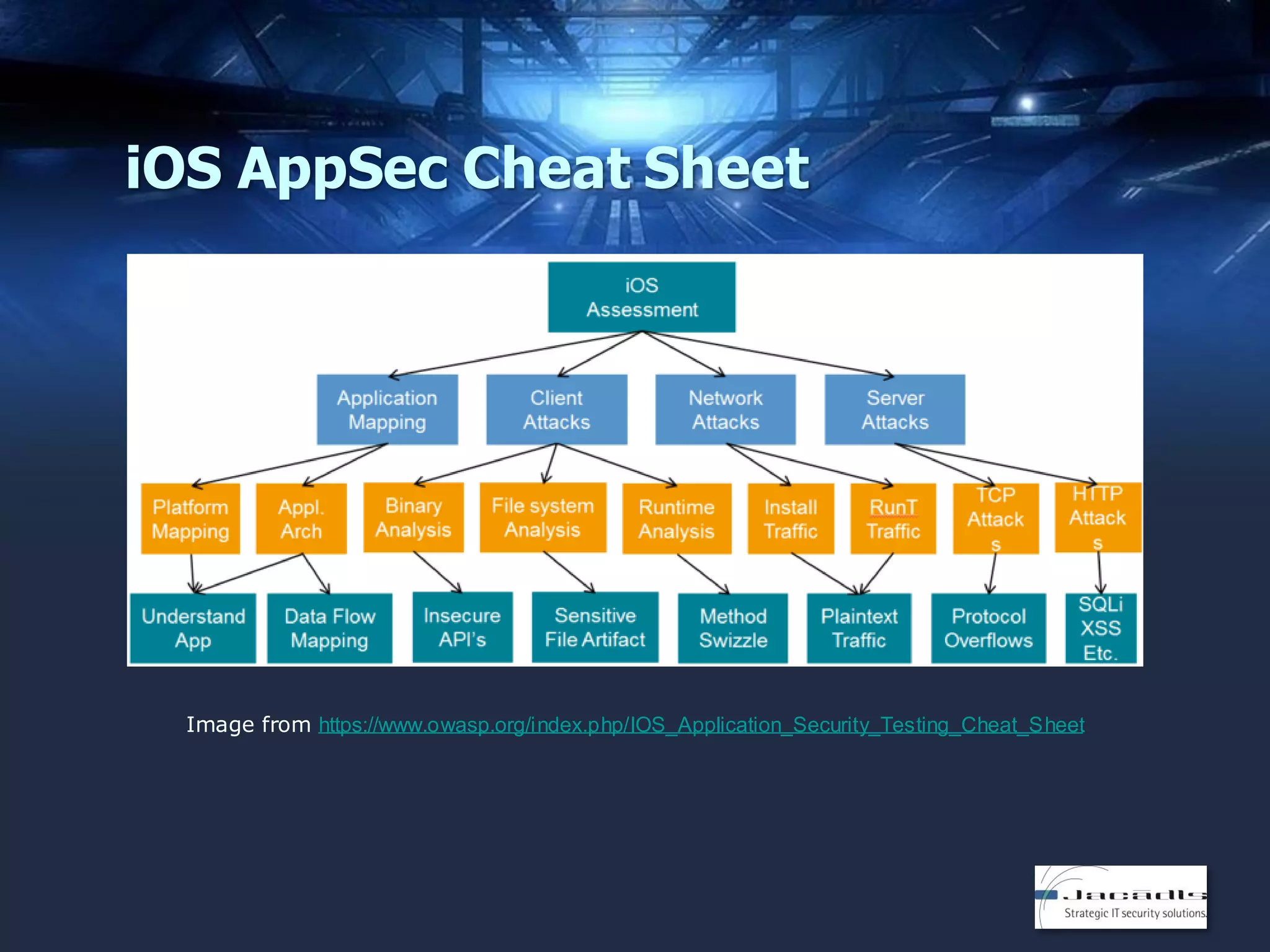
The document discusses mobile application security, focusing on both offensive and defensive strategies within the software development lifecycle (SDLC). It addresses different mobile platforms such as iOS, Android, and Windows, detailing security frameworks, analysis techniques, and defensive tools. Additionally, it emphasizes the importance of developer training and provides a variety of resources for secure app development and vulnerability testing.