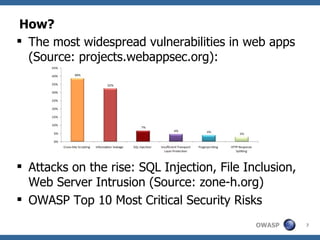
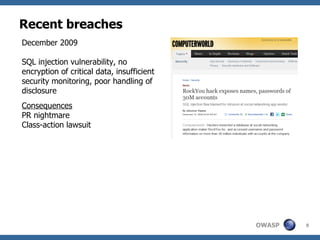
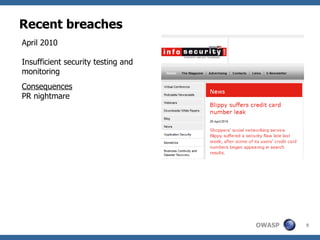
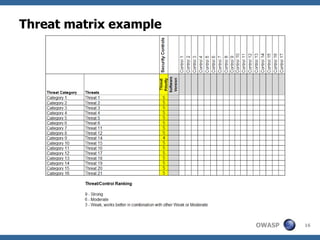
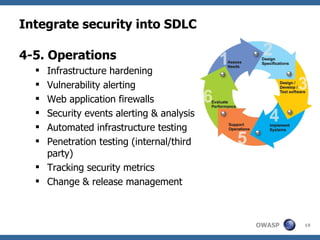
The document discusses the importance of building secure web applications in a cloud environment, highlighting the rise of web app vulnerabilities and the need for proactive security measures. It outlines strategies for integrating security into the software development life cycle, emphasizes the significance of employee training, and suggests benchmarks for security practices. The document warns of the consequences of neglecting web app security, including financial losses and reputational damage, while advocating for a structured and phased approach to implementing security protocols.