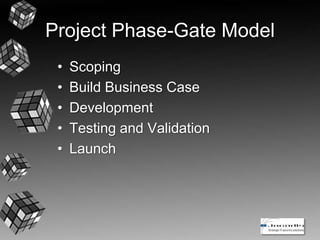
The document provides an overview of integrating security into the application development process. It discusses seeking to understand development methodologies, programming languages, and risk frameworks. It also covers source code security best practices like code reviews and tools. Application security and software quality assurance testing methods are reviewed. The document also discusses analyzing deployed applications and other considerations like training and metrics. Resources for further learning are provided.