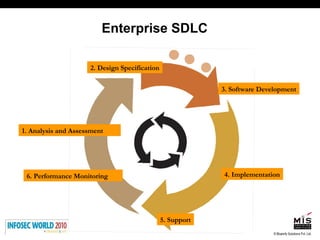
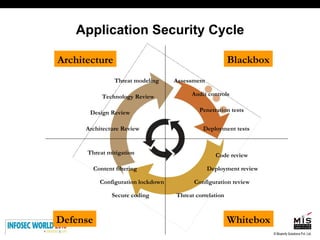
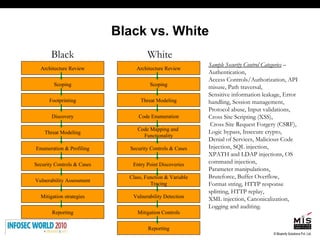
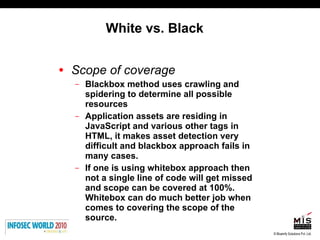
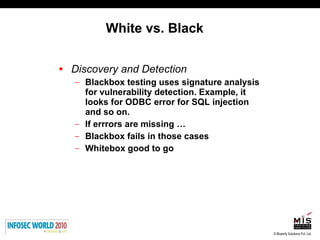
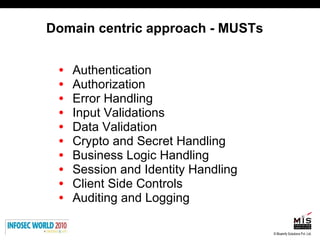
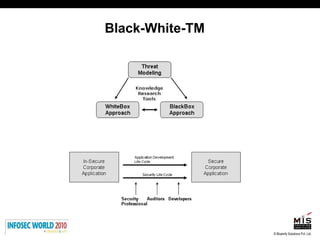
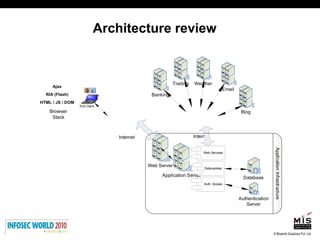
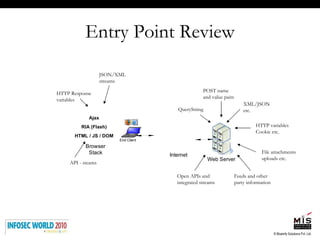
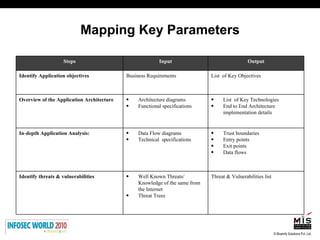
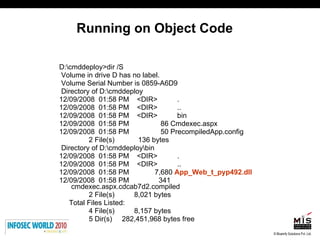
The document discusses secure software development lifecycles and application security. It notes that security is often not considered during traditional SDLC processes. It advocates doing threat modeling and source code analysis to integrate security. It also discusses differences between blackbox and whitebox testing approaches, and analyzing applications at the source code level versus object code level.

![Who Am I? Founder & Director Blueinfy Solutions Pvt. Ltd. (Brief) SecurityExposure.com Past experience Net Square, Chase, IBM & Foundstone Interest Web security research Published research Articles / Papers – Securityfocus, O’erilly, DevX, InformIT etc. Tools – wsScanner, scanweb2.0, AppMap, AppCodeScan, AppPrint etc. Advisories - .Net, Java servers etc. Books (Author) Web 2.0 Security – Defending Ajax, RIA and SOA Hacking Web Services Web Hacking http://shreeraj.blogspot.com [email_address] http://www.blueinfy.com](https://image.slidesharecdn.com/shreerajshahsecuresdlc-100421200619-phpapp02/85/Secure-SDLC-for-Software-2-320.jpg)














![Traditional checks void temp( char *pszIn ) { char szBuff[10]; strcpy(szBuff, pszIn); . . . }](https://image.slidesharecdn.com/shreerajshahsecuresdlc-100421200619-phpapp02/85/Secure-SDLC-for-Software-42-320.jpg)




![Running on reverse engineering D:\cmddeploy\bin>ildasm /TEXT App_Web_t_pyp492.dll | grep System.Diagnostics.Pro cess .locals init (class [System]System.Diagnostics.ProcessStartInfo V_0, IL_001c: newobj instance void [System]System.Diagnostics.ProcessStartIn fo::.ctor() IL_0028: callvirt instance void [System]System.Diagnostics.ProcessStartIn fo::set_FileName(string) IL_0048: callvirt instance void [System]System.Diagnostics.ProcessStartIn fo::set_Arguments(string) IL_004f: callvirt instance void [System]System.Diagnostics.ProcessStartIn fo::set_WindowStyle(valuetype [System]System.Diagnostics.ProcessWindowStyle) IL_0055: call class [System]System.Diagnostics.Process [System]System .Diagnostics.Process::Start(class [System]System.Diagnostics.ProcessStartInfo)](https://image.slidesharecdn.com/shreerajshahsecuresdlc-100421200619-phpapp02/85/Secure-SDLC-for-Software-48-320.jpg)







![HTTP to Source http://192.168.1.50/Searchresult.aspx?ReferenceId=microsoft GET /Searchresult.aspx?ReferenceId=microsoft HTTP/1.1 Host: 192.168.1.50 User-Agent: Mozilla/5.0 (Windows; U; Windows NT 5.2; en-US; rv:1.9.0.1) Gecko/2008070208 Firefox/3.0.1 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8 Accept-Language: en-us,en;q=0.5 Accept-Encoding: gzip,deflate Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7 Keep-Alive: 300 Connection: keep-alive Cache-Control: max-age=0 protected void Page_Load(object sender, EventArgs e) { if (!Page.IsPostBack) { bindresult(Request.QueryString["ReferenceId"].ToString()); } }](https://image.slidesharecdn.com/shreerajshahsecuresdlc-100421200619-phpapp02/85/Secure-SDLC-for-Software-62-320.jpg)

![In compiled code IL_0007: callvirt instance class [System]System.Collections.Specialized.NameValueCollection [System.Web]System.Web.HttpRequest::get_QueryString() IL_000c: ldstr "id"](https://image.slidesharecdn.com/shreerajshahsecuresdlc-100421200619-phpapp02/85/Secure-SDLC-for-Software-64-320.jpg)
![Simple scan… import sys import os import re def scan4request(file): infile = open(file,"r") s = infile.readlines() linenum = 0 print 'Request Object Entry:' for line in s: linenum += 1 p = re.compile(".*.[Rr]equest.*[^\n]\n") m = p.match(line) if m: print linenum,":",m.group() file = sys.argv[1] scan4request(file)](https://image.slidesharecdn.com/shreerajshahsecuresdlc-100421200619-phpapp02/85/Secure-SDLC-for-Software-65-320.jpg)

![PHP/Coldfusion PHP $_GET[“var”] $_POST[“var”] $_REQUEST[“var”] Coldfusion #URL.name# - Getting from querystring “name” Similarly we can identify entry points for other aspects like POST or such by following list of key words FORM/form SERVER/server CLIENT/client SESSION/session](https://image.slidesharecdn.com/shreerajshahsecuresdlc-100421200619-phpapp02/85/Secure-SDLC-for-Software-69-320.jpg)

![Code for Web Services <%@ WebService Language="c#" Class="dvds4less" %> <%@ Assembly name="Microsoft.Data.SqlXml" %> using Microsoft.Data.SqlXml; using System.Xml; using System; using System.Web.Services; using System.Data.SqlClient; using System.IO; public class dvds4less { [WebMethod] public string Intro() { return "DVDs4LESS - Information APIs for web application usage and other business usage"; } [WebMethod] public string getProductInfo(string id) { … . Code for this function }](https://image.slidesharecdn.com/shreerajshahsecuresdlc-100421200619-phpapp02/85/Secure-SDLC-for-Software-72-320.jpg)
![JSON-RPC <%@ WebHandler Class="JayrockWeb.DemoService" Language="C#" %> namespace JayrockWeb { using System; using System.Configuration; using System.Data; using System.Data.SqlClient; using System.Collections; using System.Collections.Specialized; using System.Web; using System.Web.SessionState; using System.Web.UI; using System.Web.UI.WebControls; using System.Drawing; using Jayrock.Json; using Jayrock.JsonRpc; using Jayrock.JsonRpc.Web; [ JsonRpcHelp("This is a JSON-RPC service that demonstrates the basic features of the Jayrock library.") ] public class DemoService : JsonRpcHandler, IRequiresSessionState { [JsonRpcMethod("getProduct", Idempotent = true)] [ JsonRpcHelp("Returns Product Info") ] public DataSet GetProductSet(string id) { … . Code goes here… }](https://image.slidesharecdn.com/shreerajshahsecuresdlc-100421200619-phpapp02/85/Secure-SDLC-for-Software-73-320.jpg)
![PHP <?php require_once('nusoap/nusoap.php'); // ------ Implemention of method // ---- getLang(langTo) ------------------------------------------------------ function getLang($langTo) { $trText = array( "bonjour" => "french", "ciao" => "italian", "hallo" => "german", "namaste" => "hindi" ); $greeting = ""; $key = array_search($langTo, $trText); $greeting = array_keys($trText[$langTo]); return $greeting; }](https://image.slidesharecdn.com/shreerajshahsecuresdlc-100421200619-phpapp02/85/Secure-SDLC-for-Software-75-320.jpg)


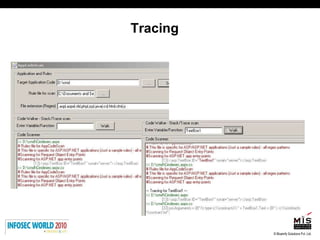
![Simple tracing… import sys import os import re def scan4trace(file,var): infile = open(file,"r") s = infile.readlines() print 'Tracing variable:'+var linenum=0 for line in s: linenum += 1 p = re.compile(".*."+var+".*") m = p.match(line) if m: print "[",linenum,"]",line file = sys.argv[1] var = sys.argv[2] scan4trace(file,var)](https://image.slidesharecdn.com/shreerajshahsecuresdlc-100421200619-phpapp02/85/Secure-SDLC-for-Software-82-320.jpg)
![Running… D:\sca-rb>trace.py d:\cmd\Cmdexec.aspx.cs TextBox1 Tracing variable:TextBox1 [ 33 ] psi.Arguments = @"/c type c:\\contracts\\" + TextBox1.Text + @" > c:\\contracts\\contract.txt"; D:\sca-rb>trace.py d:\cmd\Cmdexec.aspx.cs psi Tracing variable:psi [ 31 ] System.Diagnostics.ProcessStartInfo psi = new System.Diagnostics. ProcessStartInfo(); [ 32 ] psi.FileName = @"C:\WINDOWS\system32\cmd.exe"; [ 33 ] psi.Arguments = @"/c type c:\\contracts\\" + TextBox1.Text + @" > c:\\contracts\\contract.txt"; [ 34 ] psi.WindowStyle = System.Diagnostics.ProcessWindowStyle.Hidden; [ 35 ] System.Diagnostics.Process.Start(psi);](https://image.slidesharecdn.com/shreerajshahsecuresdlc-100421200619-phpapp02/85/Secure-SDLC-for-Software-83-320.jpg)
![CONCLUSION – QUESTIONS! [email_address] http://www.blueinfy.com](https://image.slidesharecdn.com/shreerajshahsecuresdlc-100421200619-phpapp02/85/Secure-SDLC-for-Software-86-320.jpg)