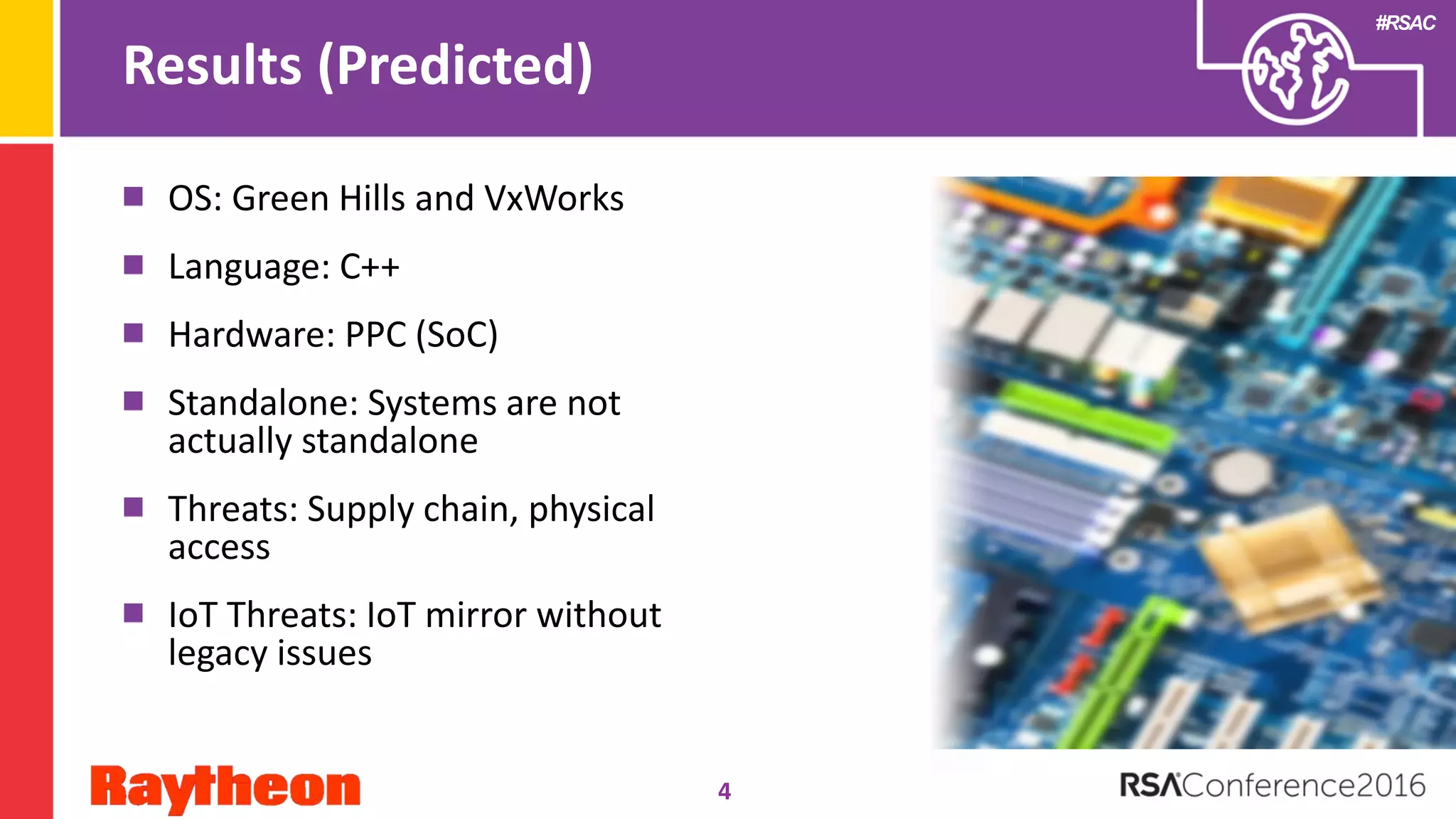
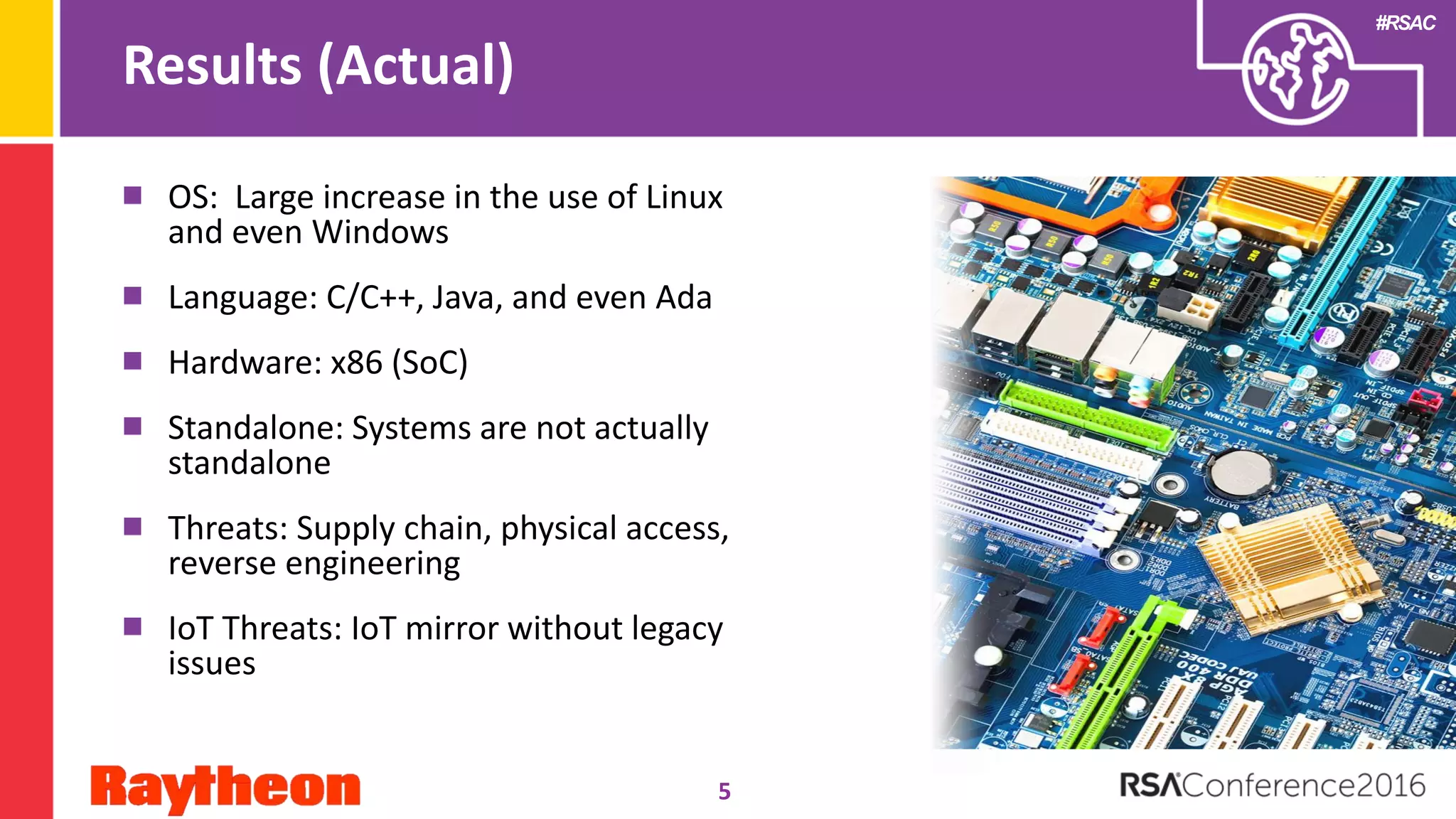
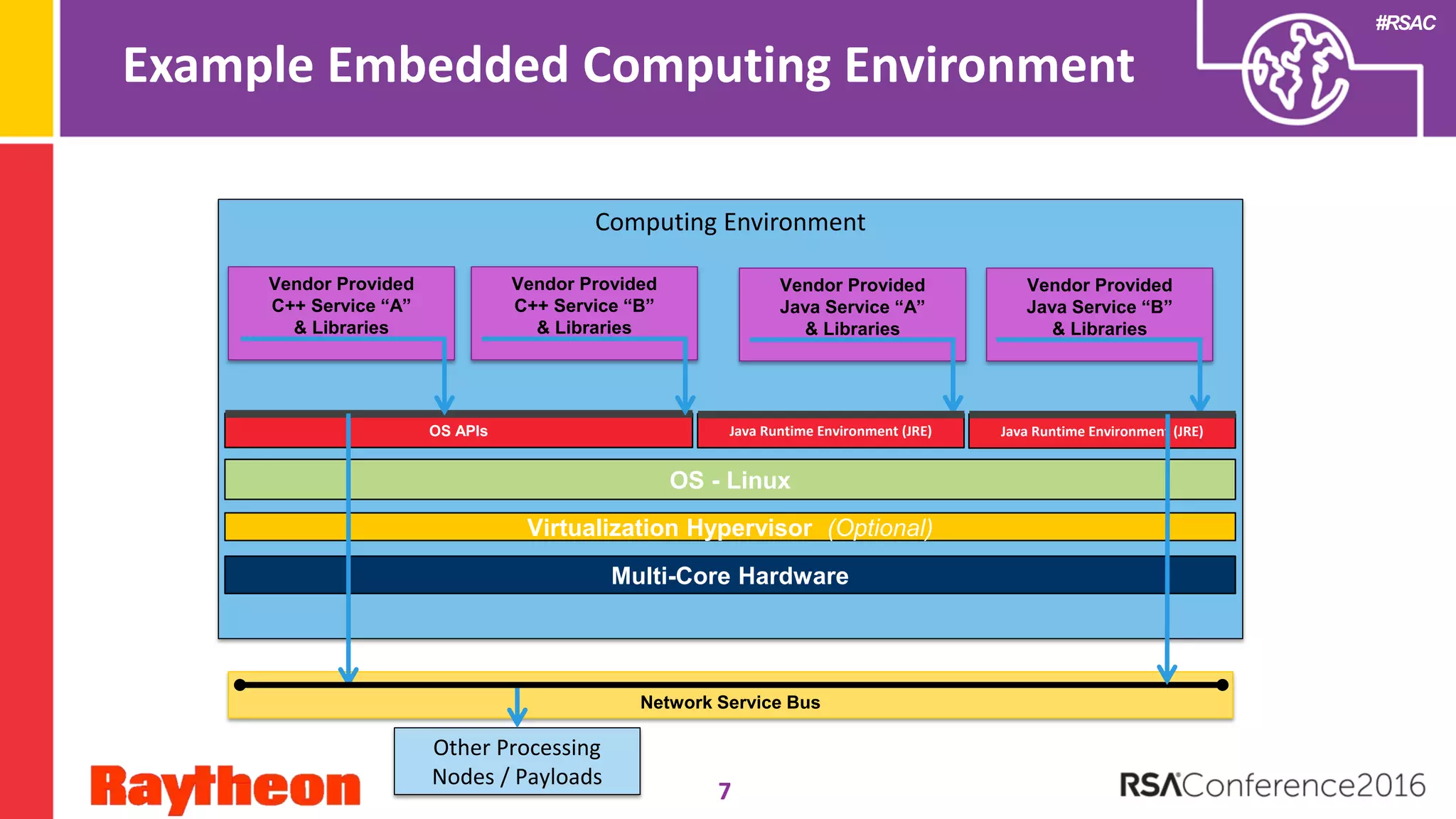
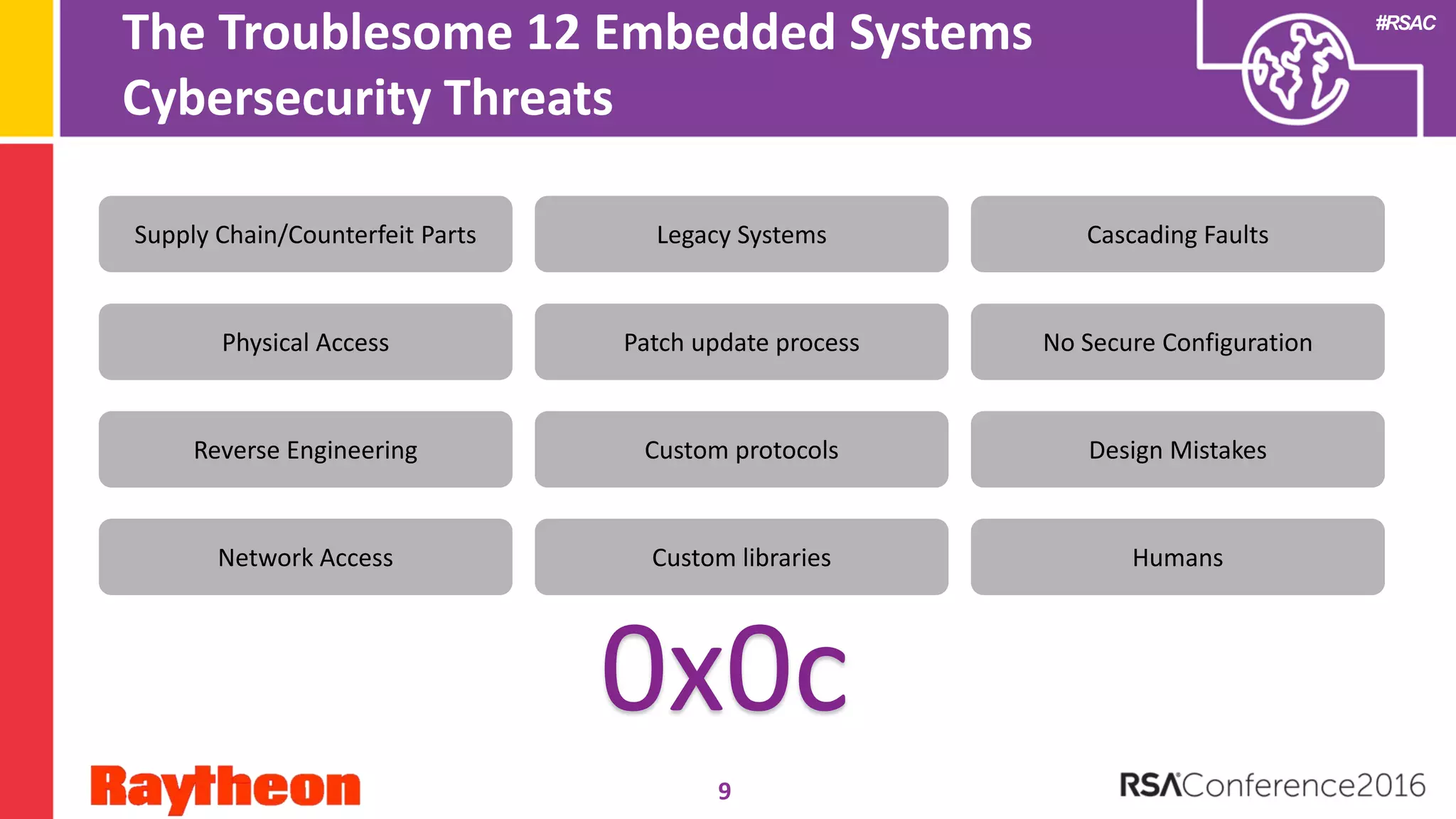
The document discusses common security issues faced by embedded systems and recommendations for improving security. It identifies 12 common embedded system security threats, including supply chain attacks, physical access, reverse engineering, lack of secure configurations, and human errors. The document recommends building security functions into embedded systems to defend against threats, maintaining control over security algorithms, and conducting risk assessments and vulnerability testing. Developers are advised to apply lessons from the presentation to their own work by considering top threats and seeking security advice within 6 months.