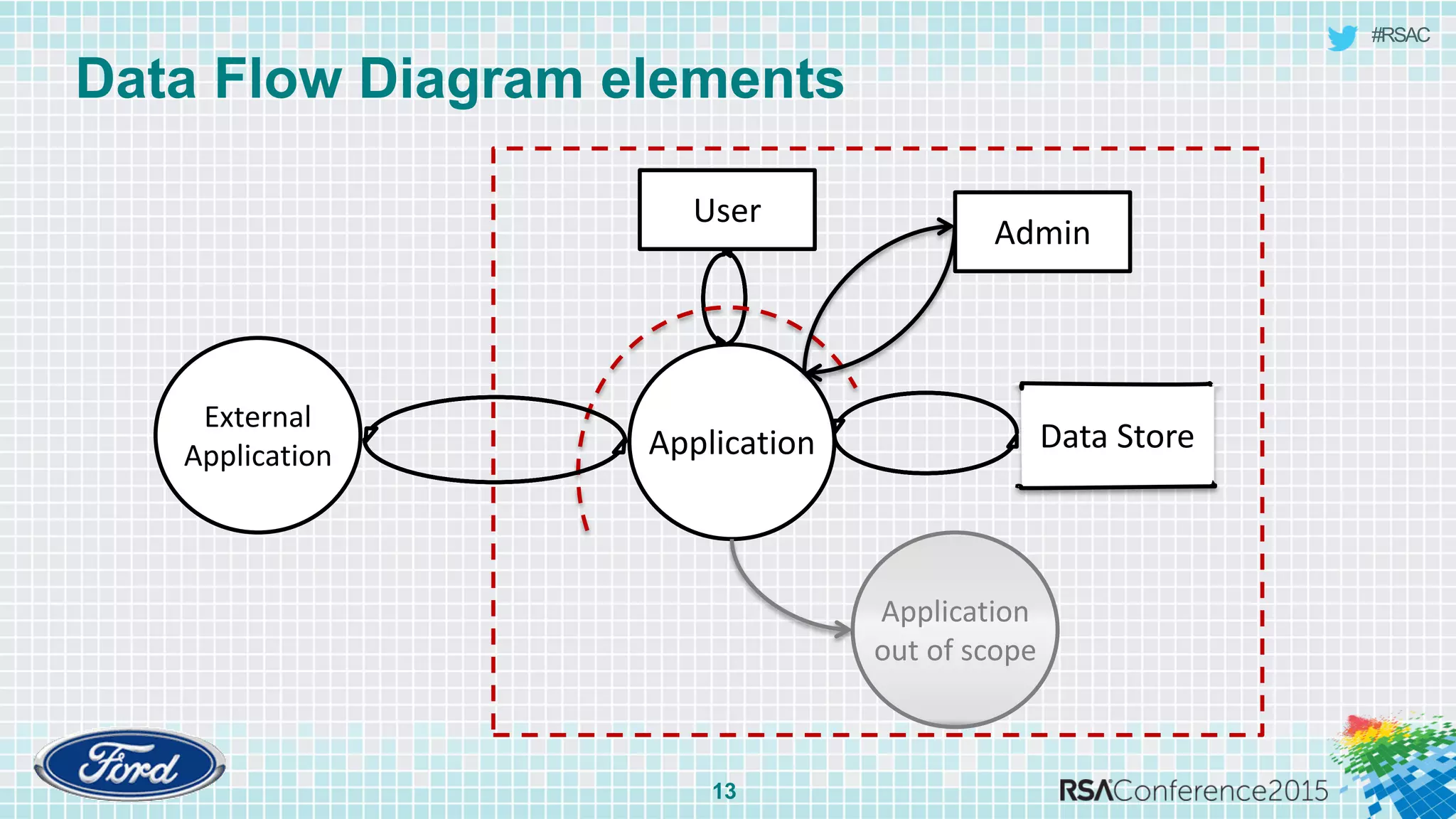
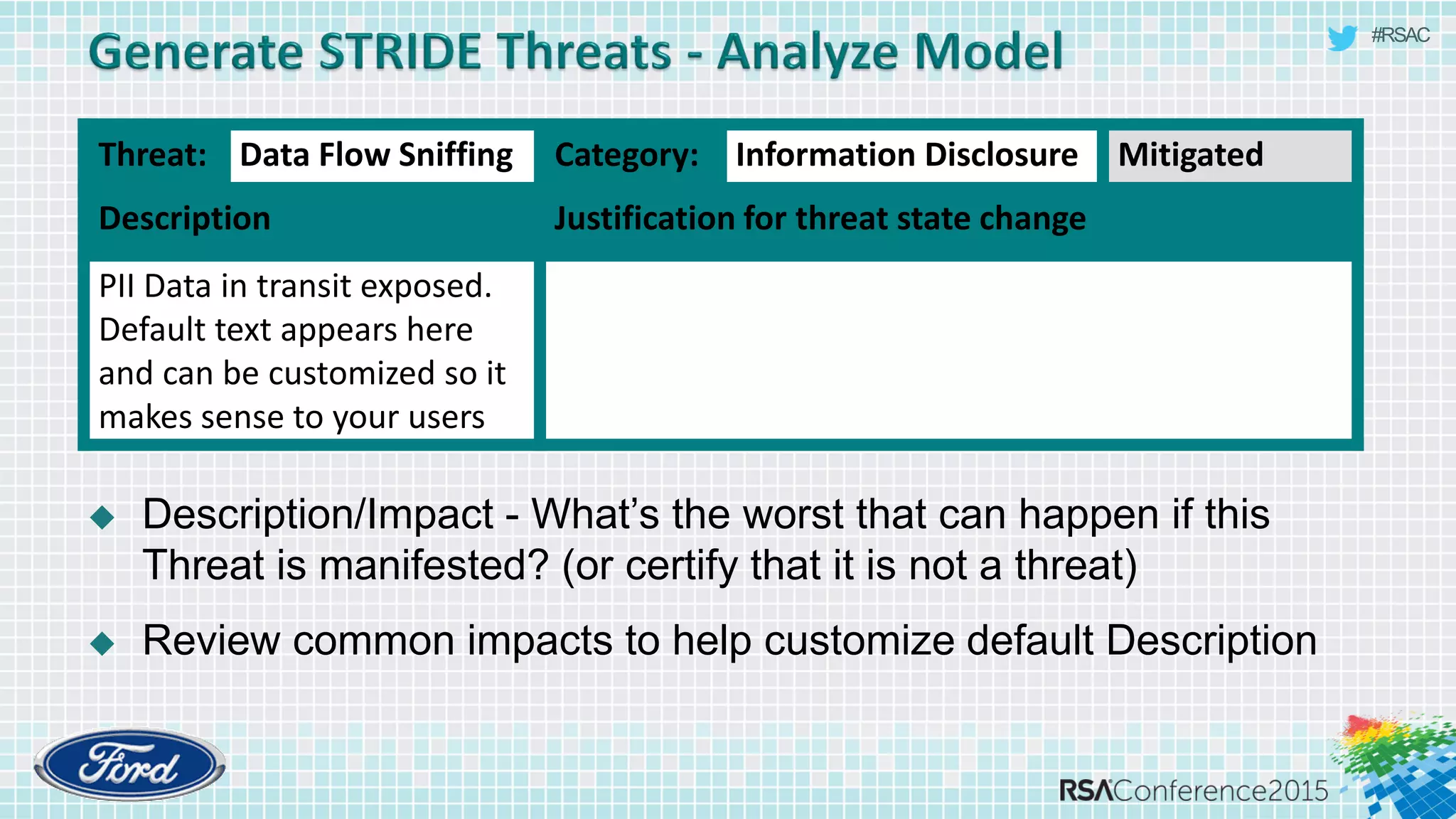
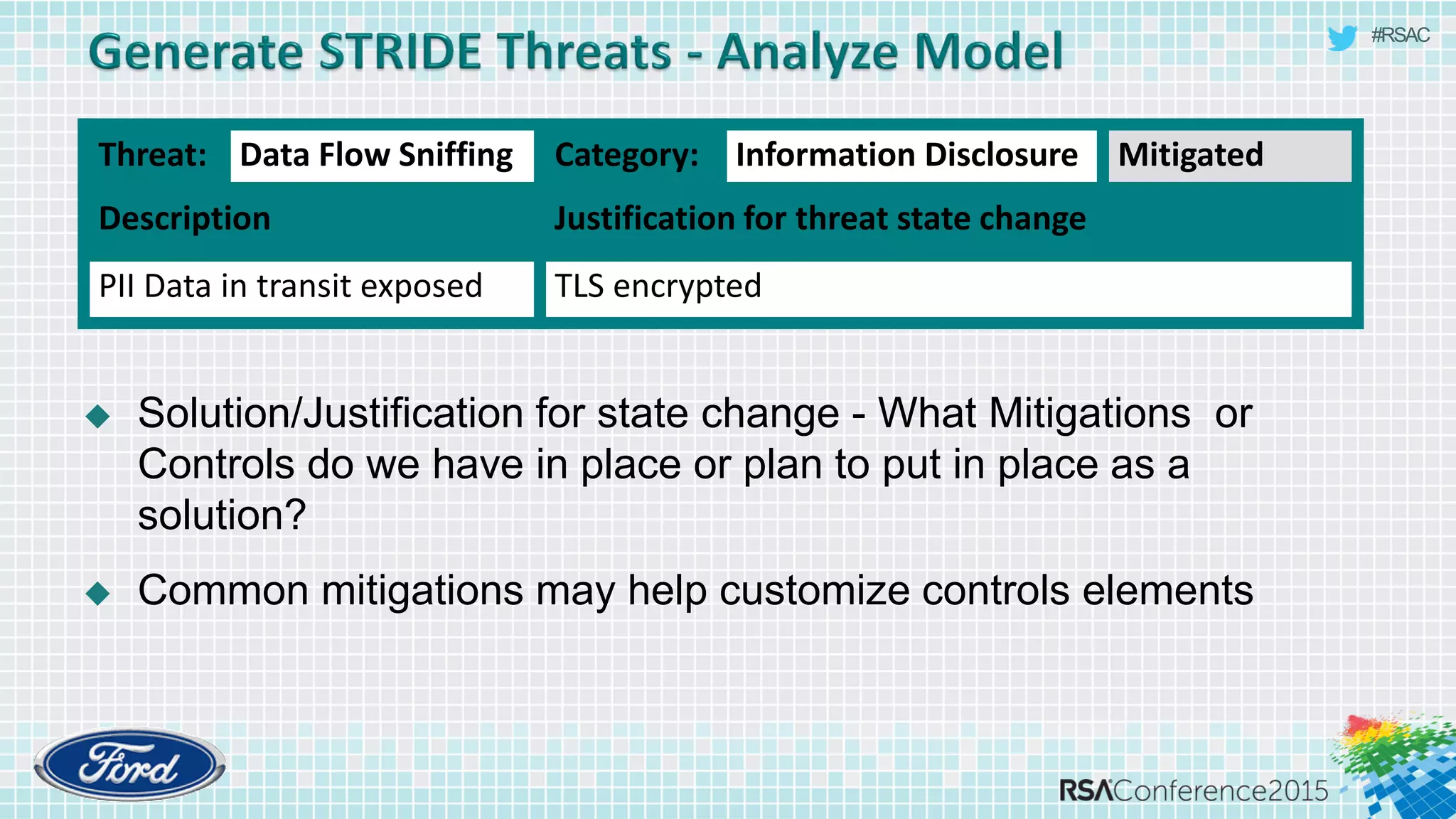
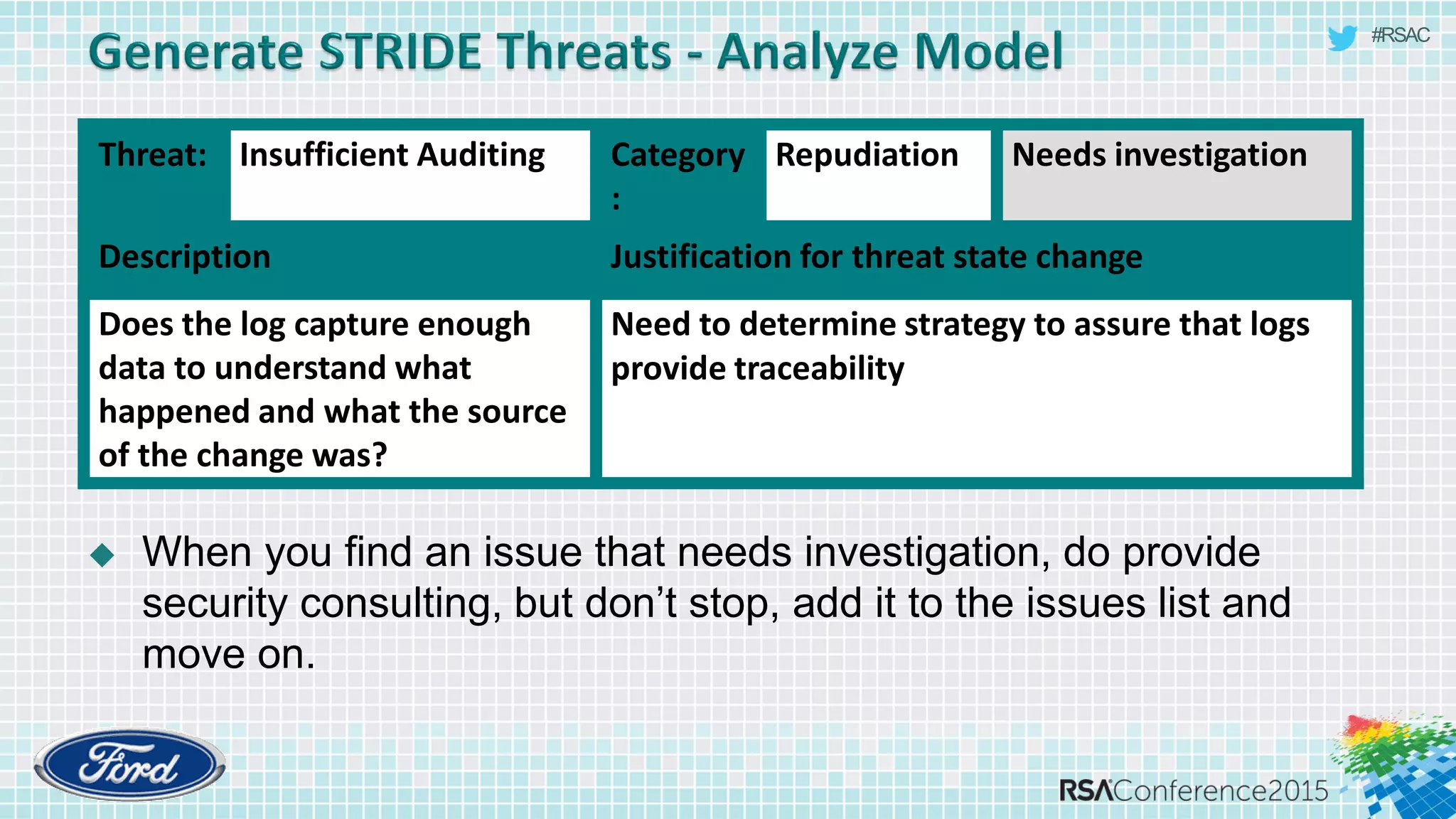
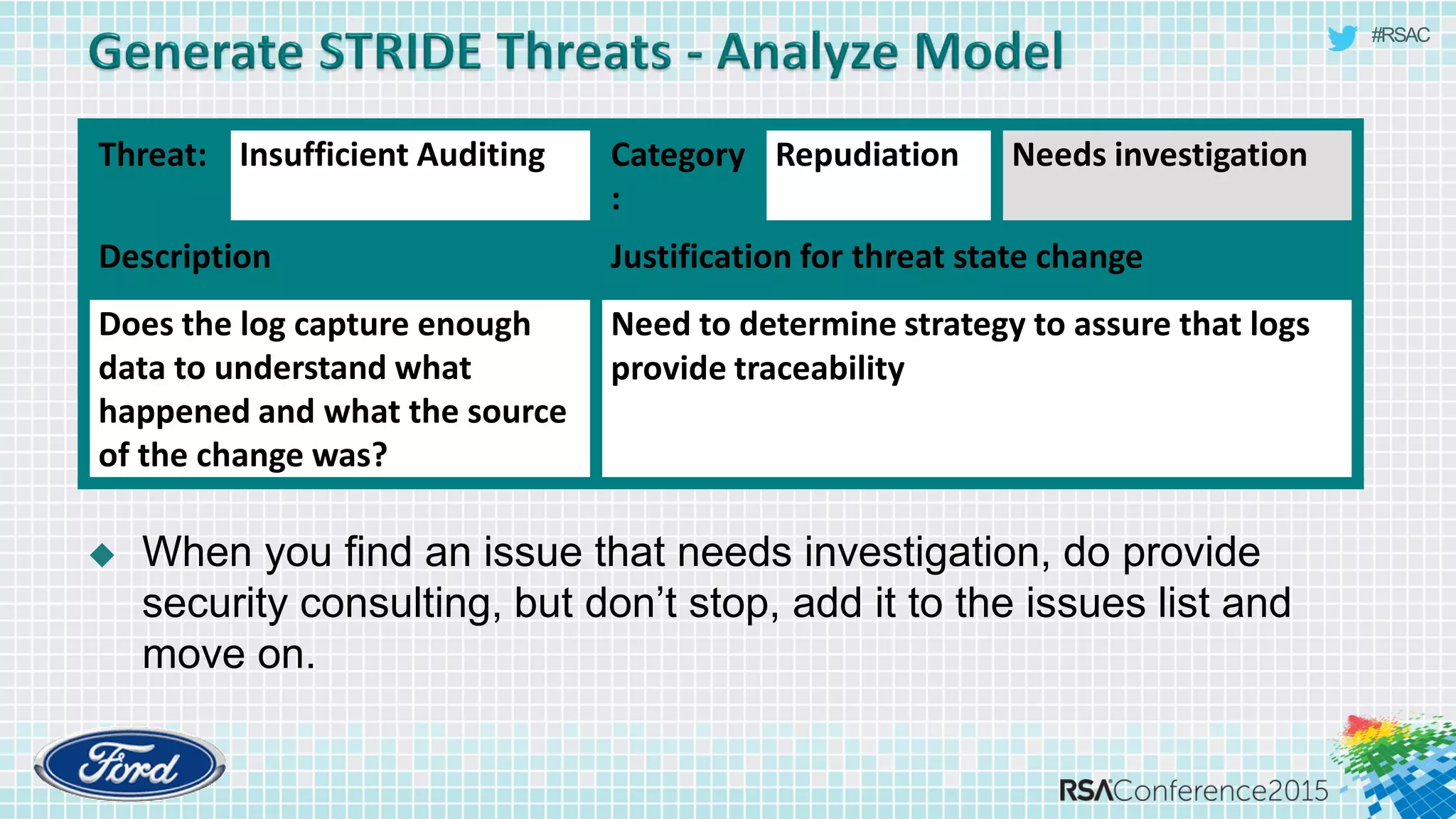
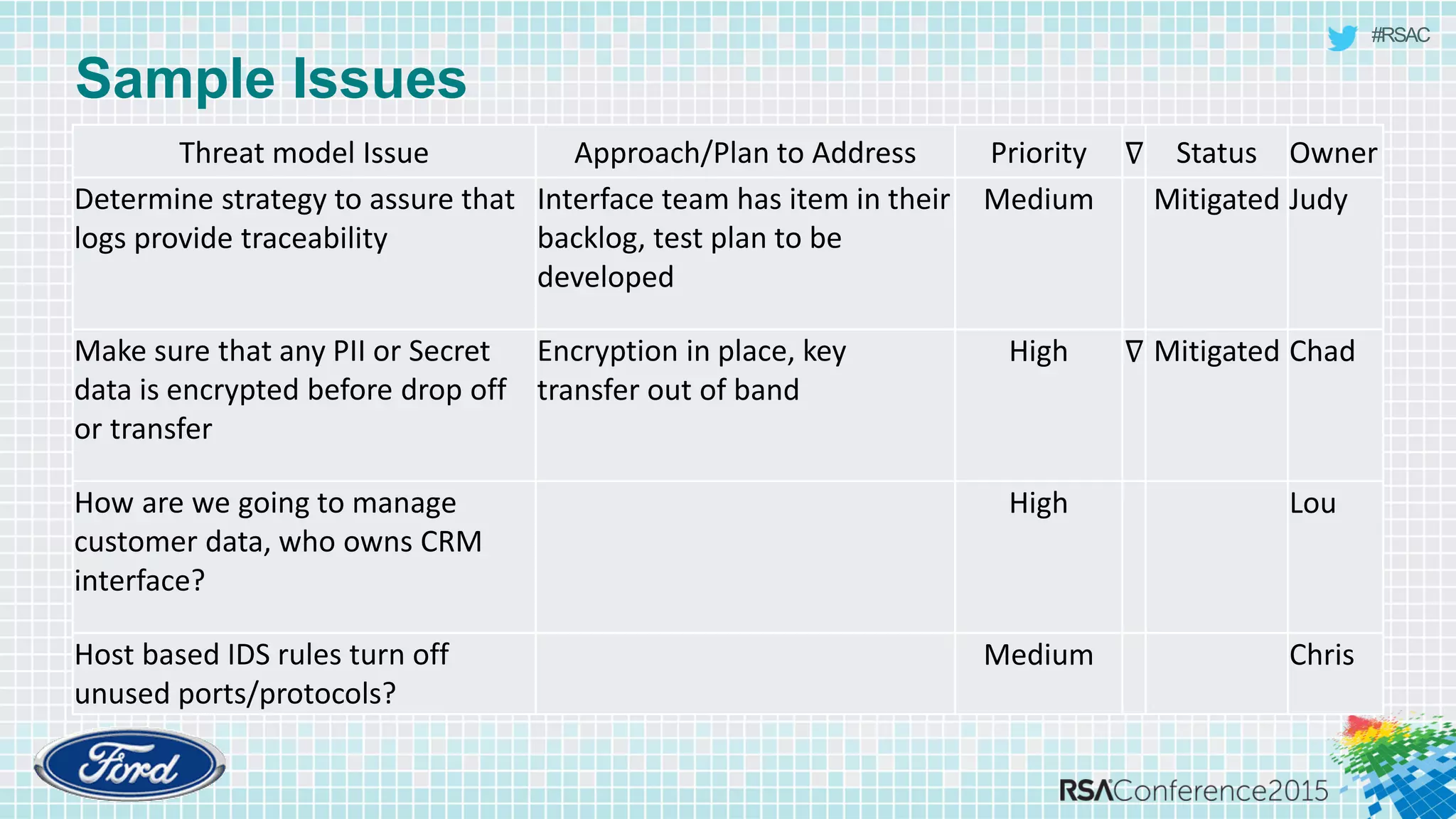
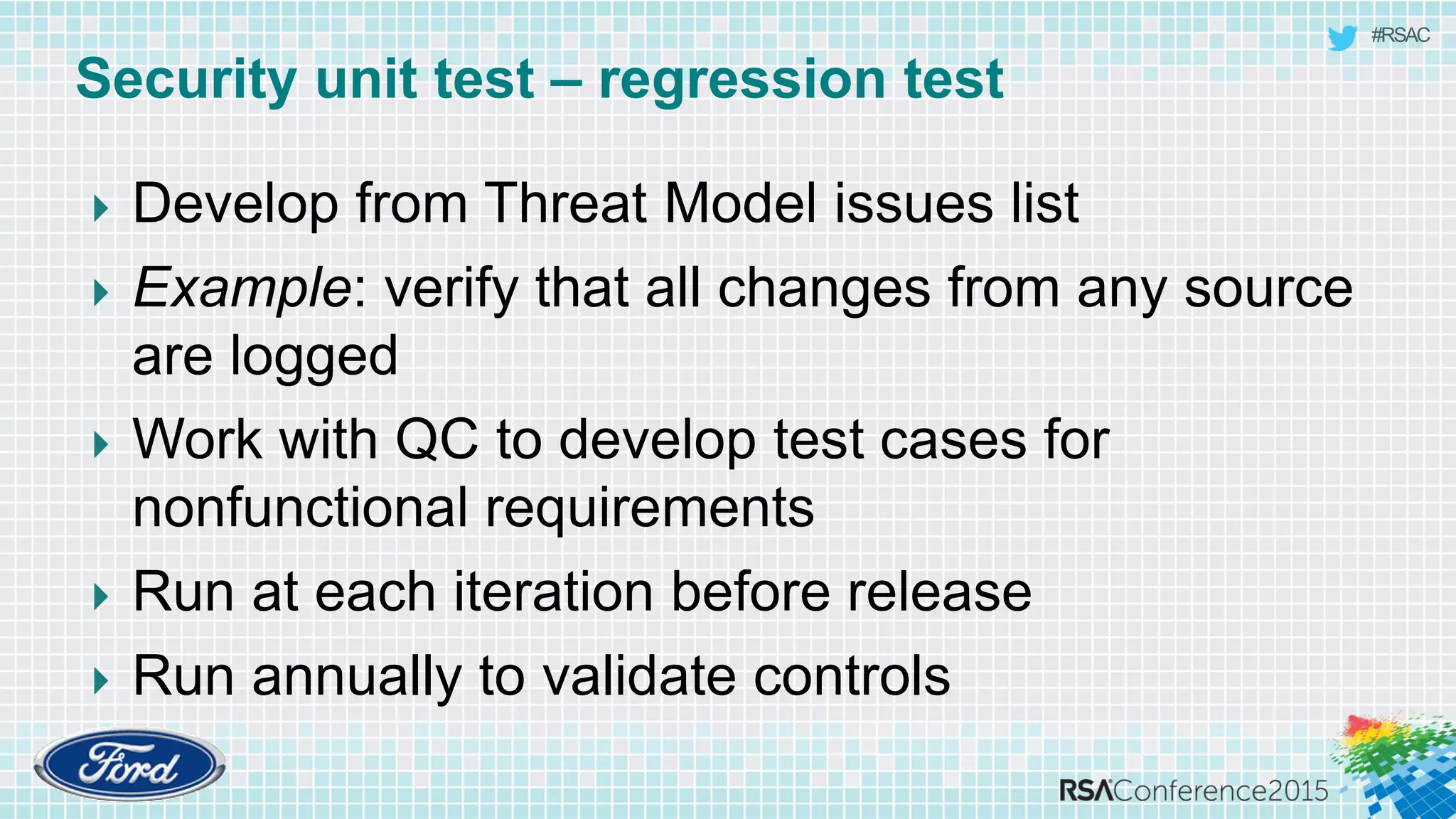
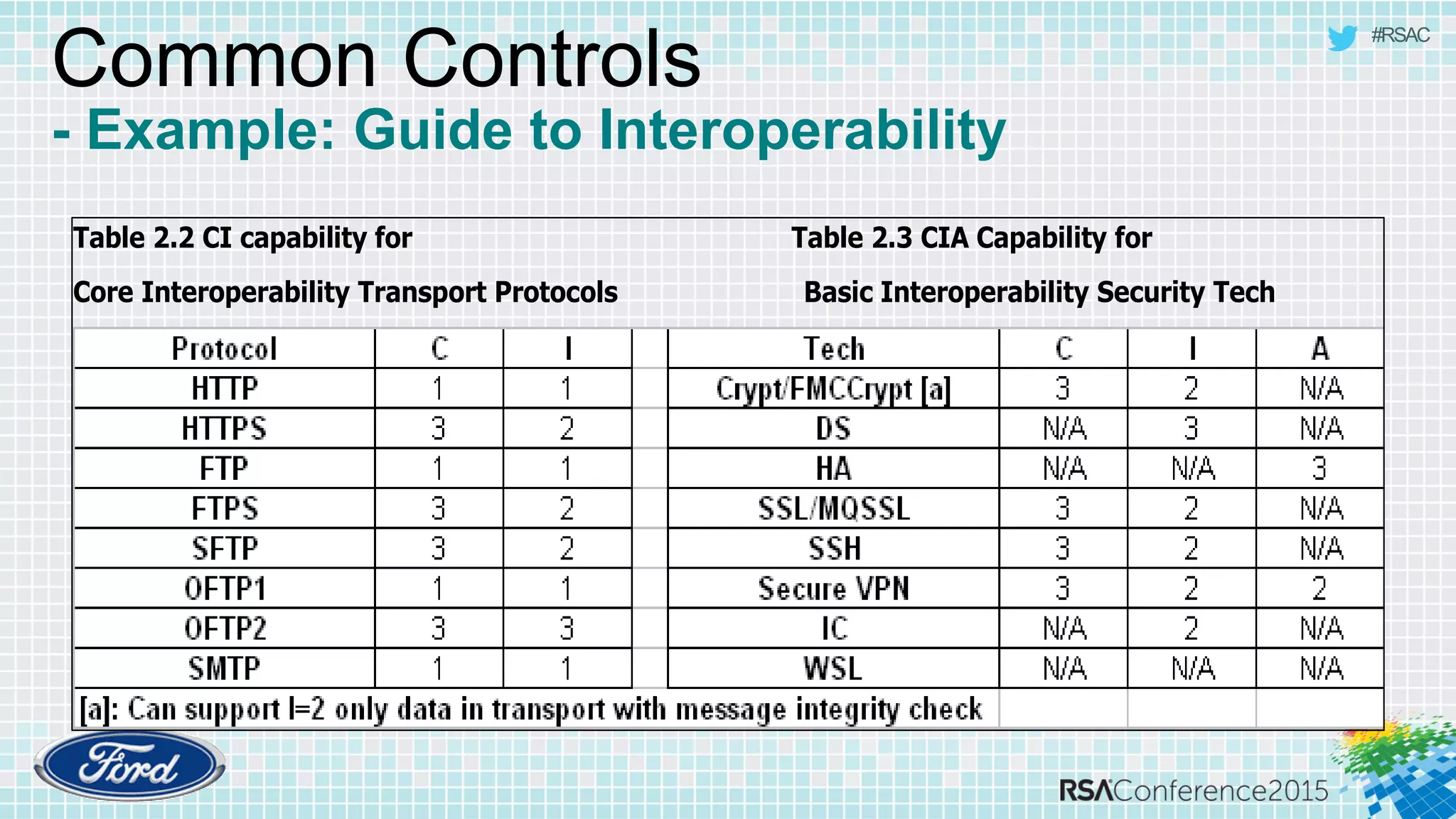
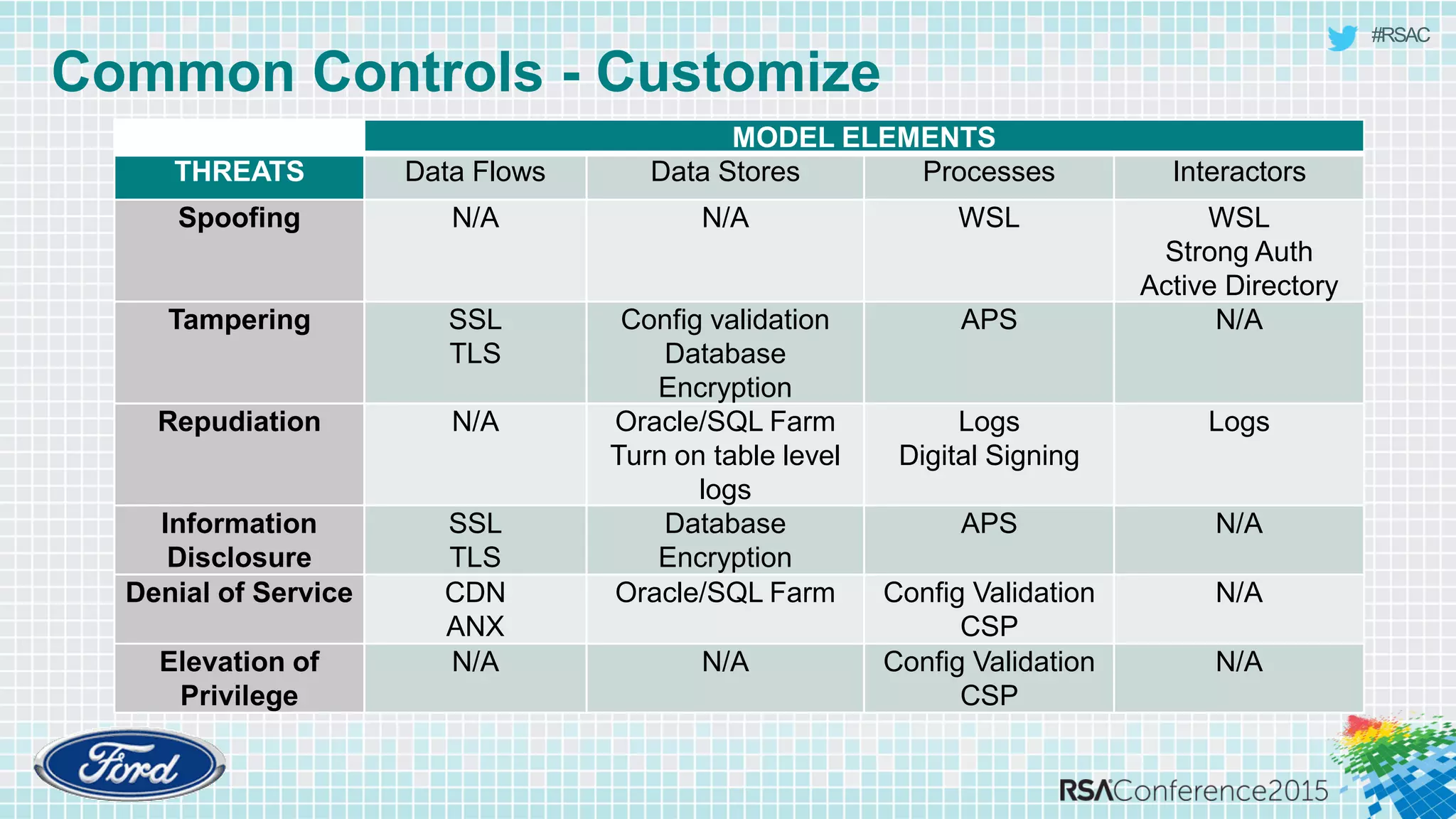
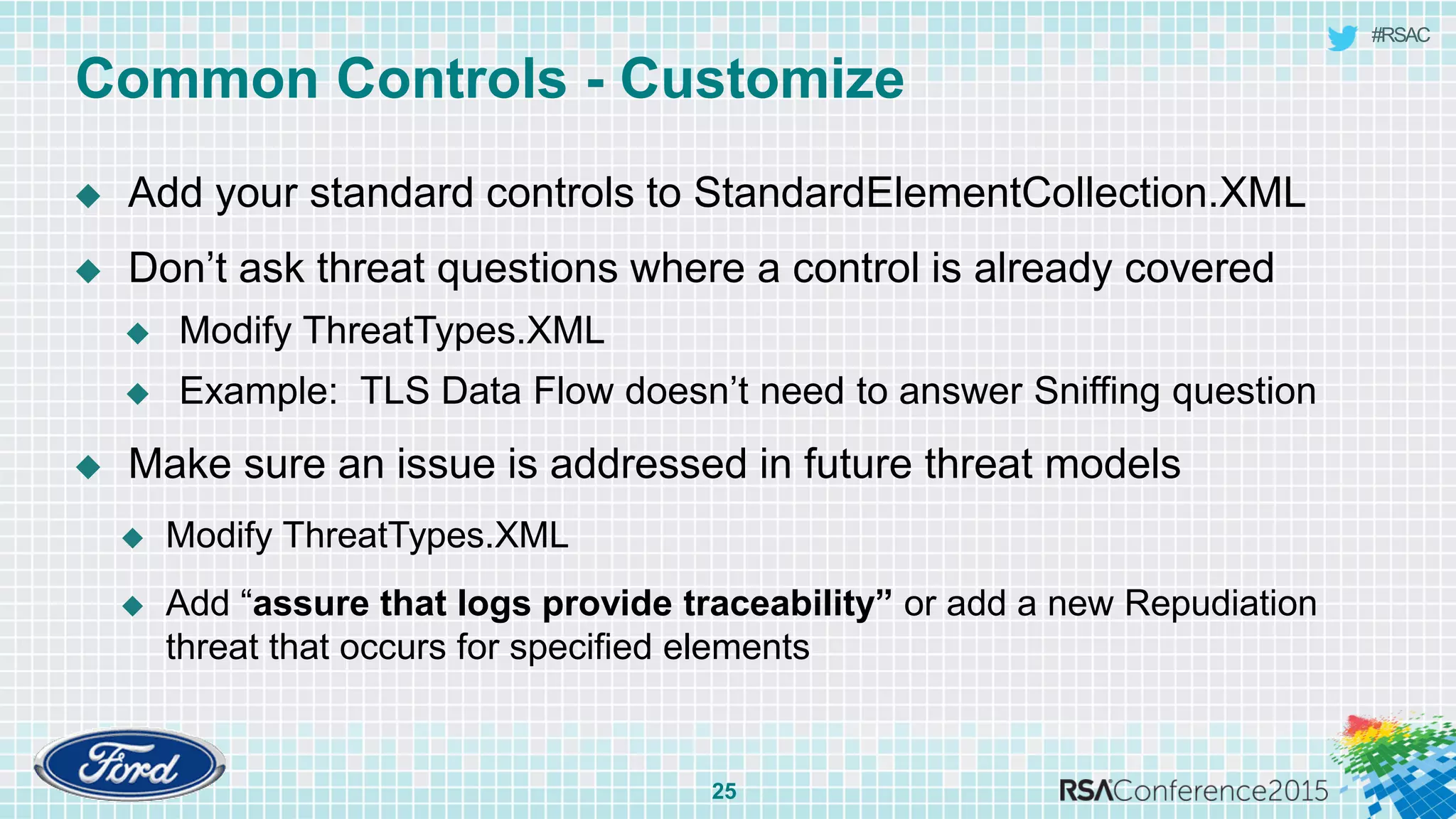
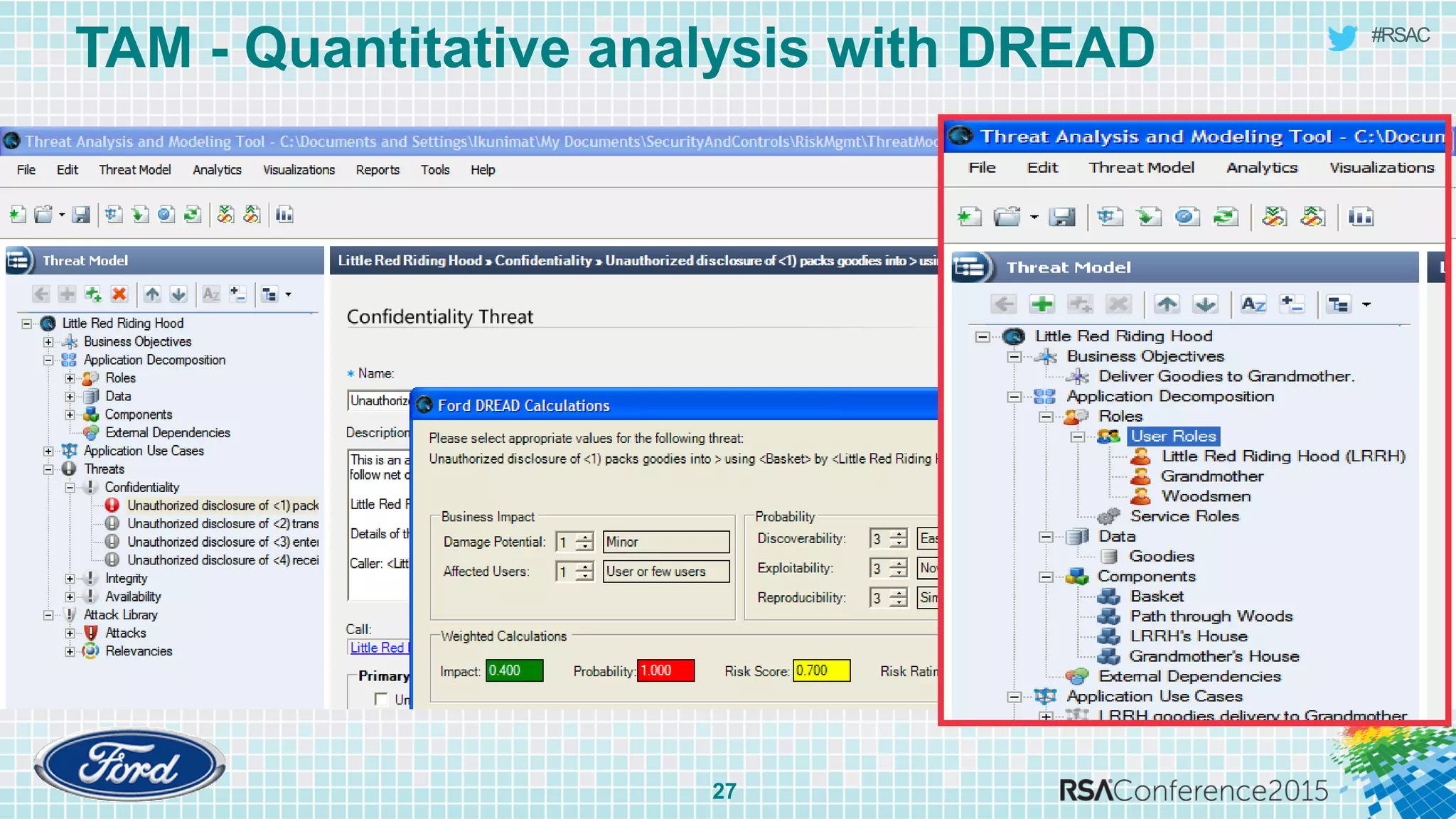
The document discusses techniques for rapid threat modeling. It begins with an overview of threat modeling and the STRIDE methodology. It then provides lessons learned for making threat modeling faster, such as setting time limits for sessions, prioritizing what to model, and customizing common controls. The document also discusses capturing issues identified and using threat modeling as part of a broader security analysis process.