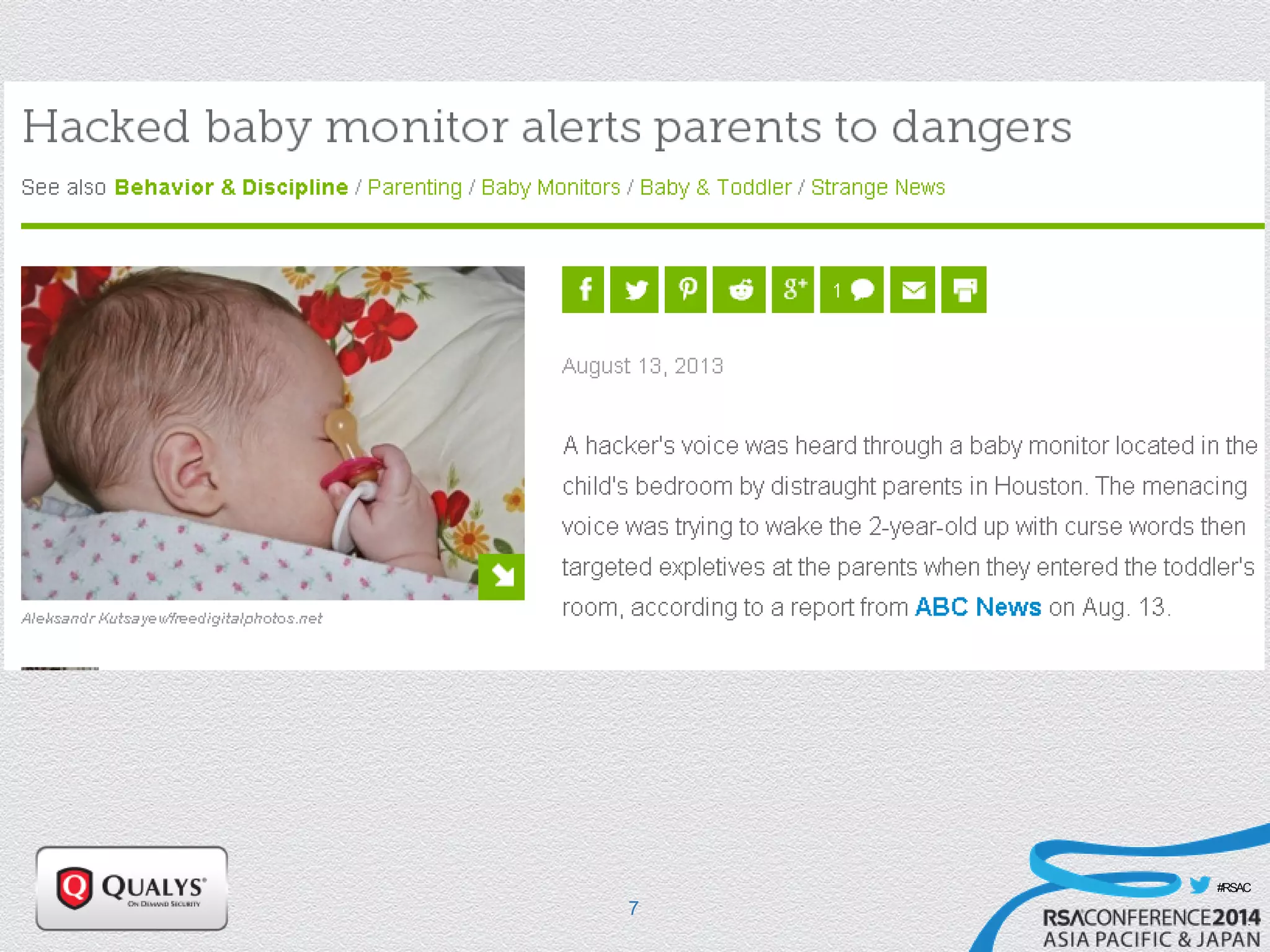
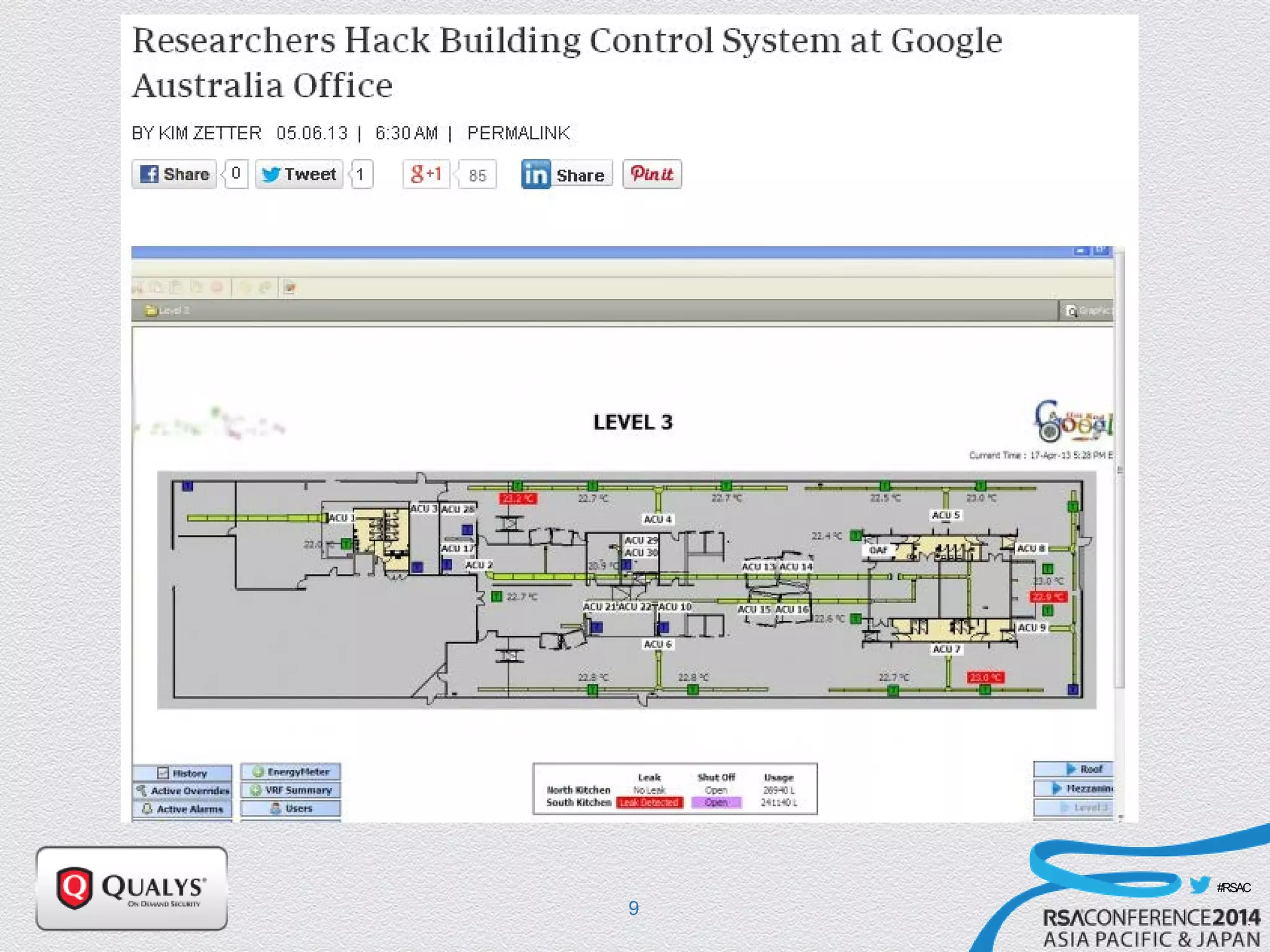
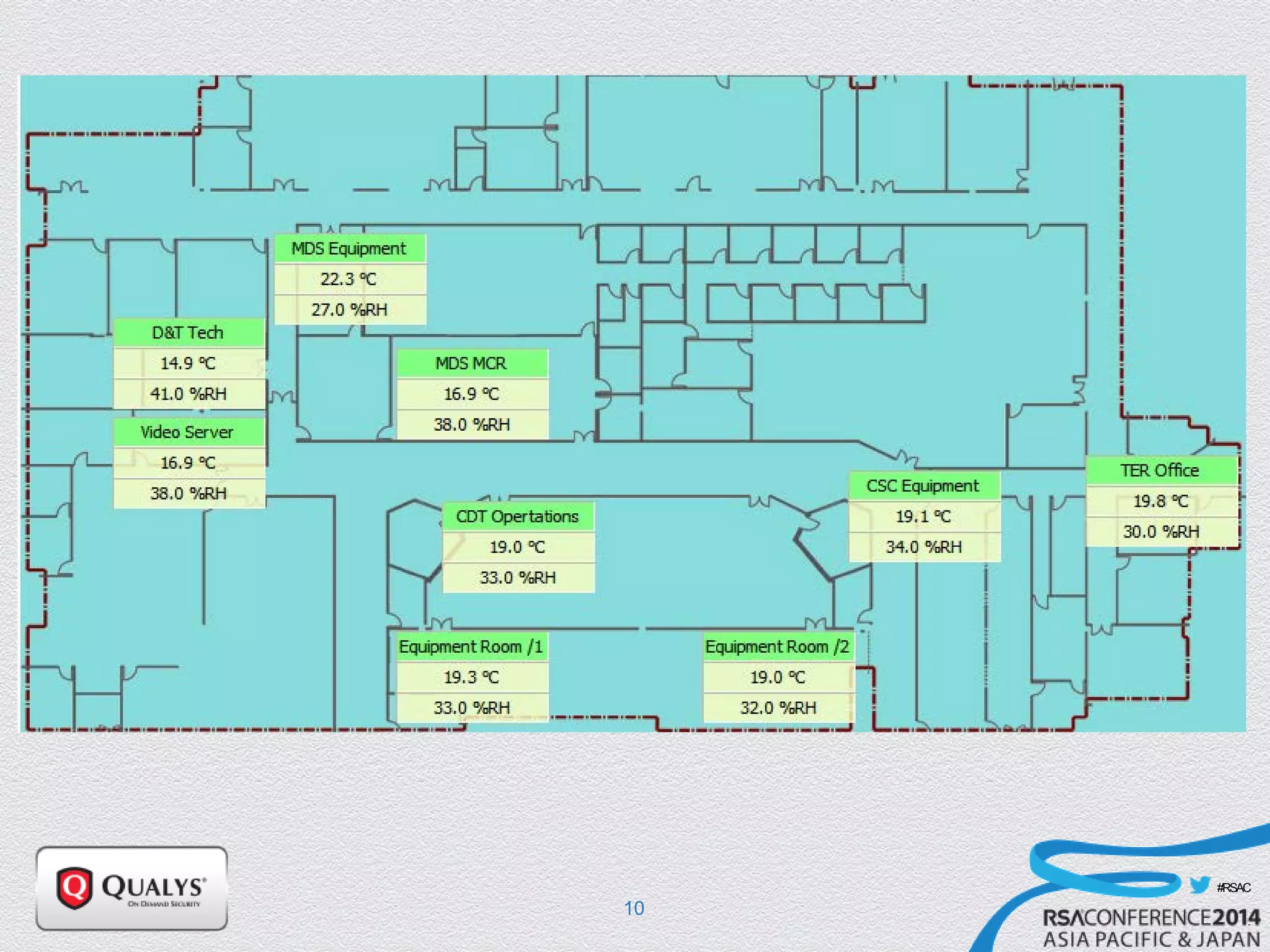
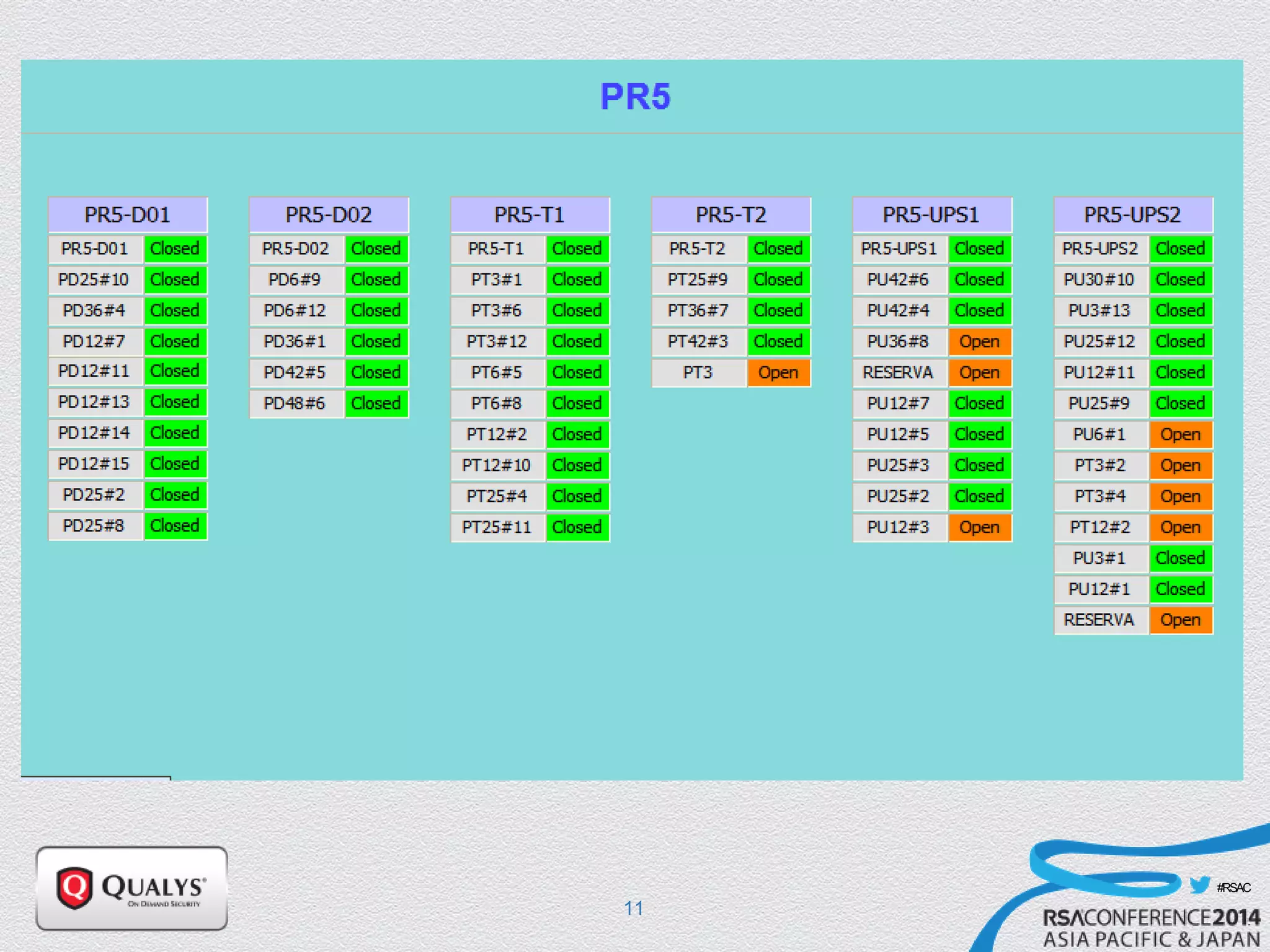
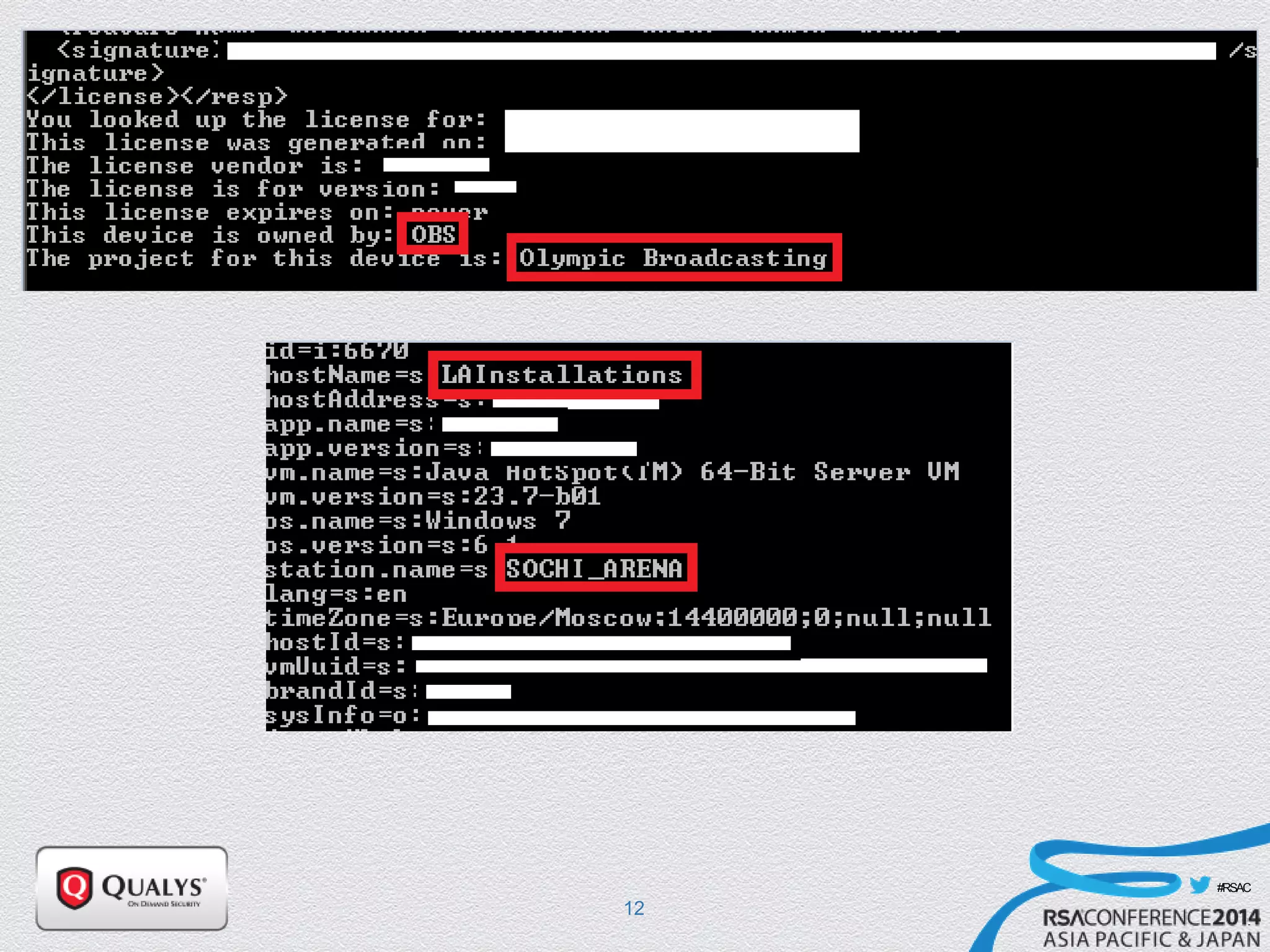
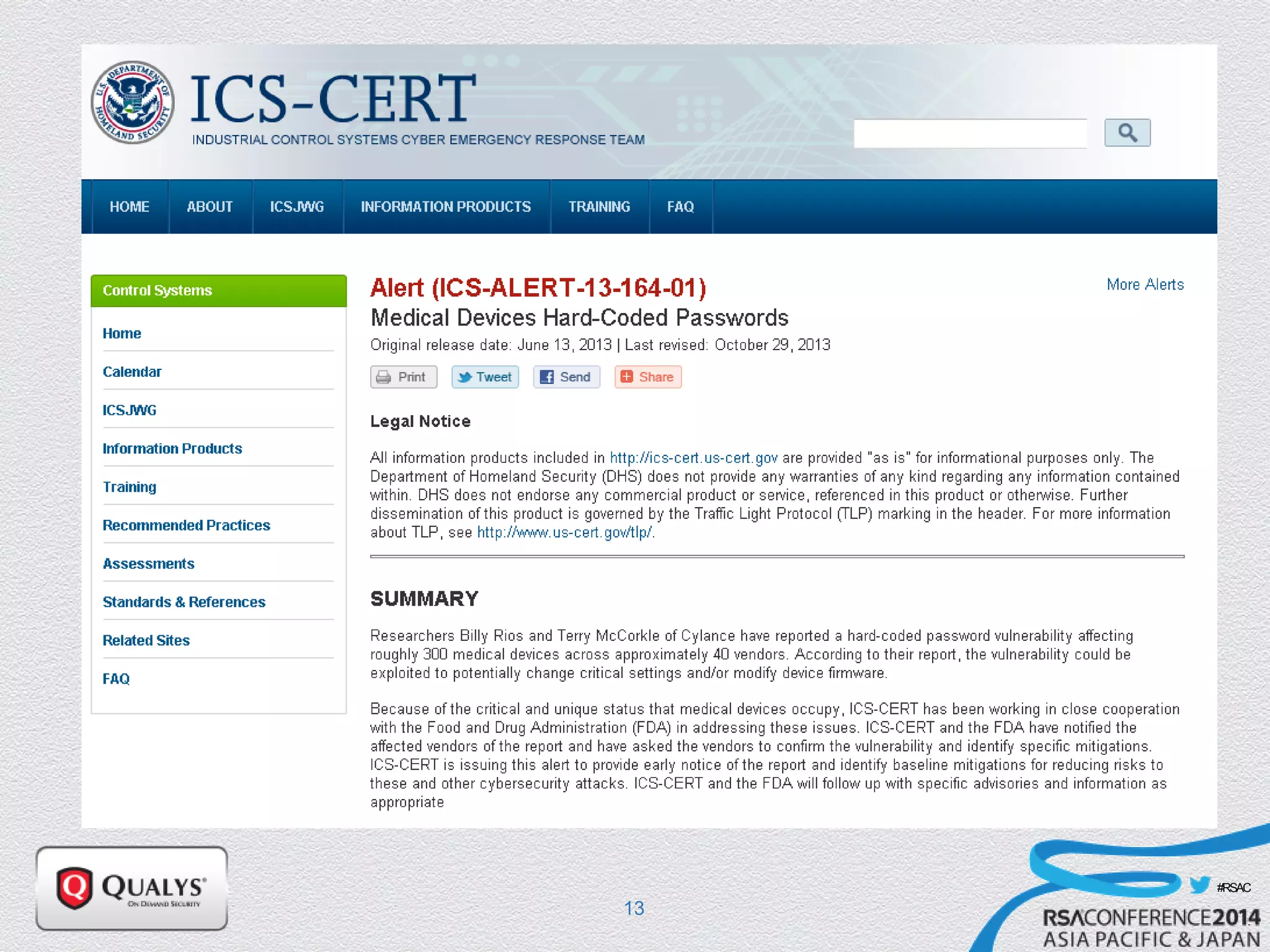
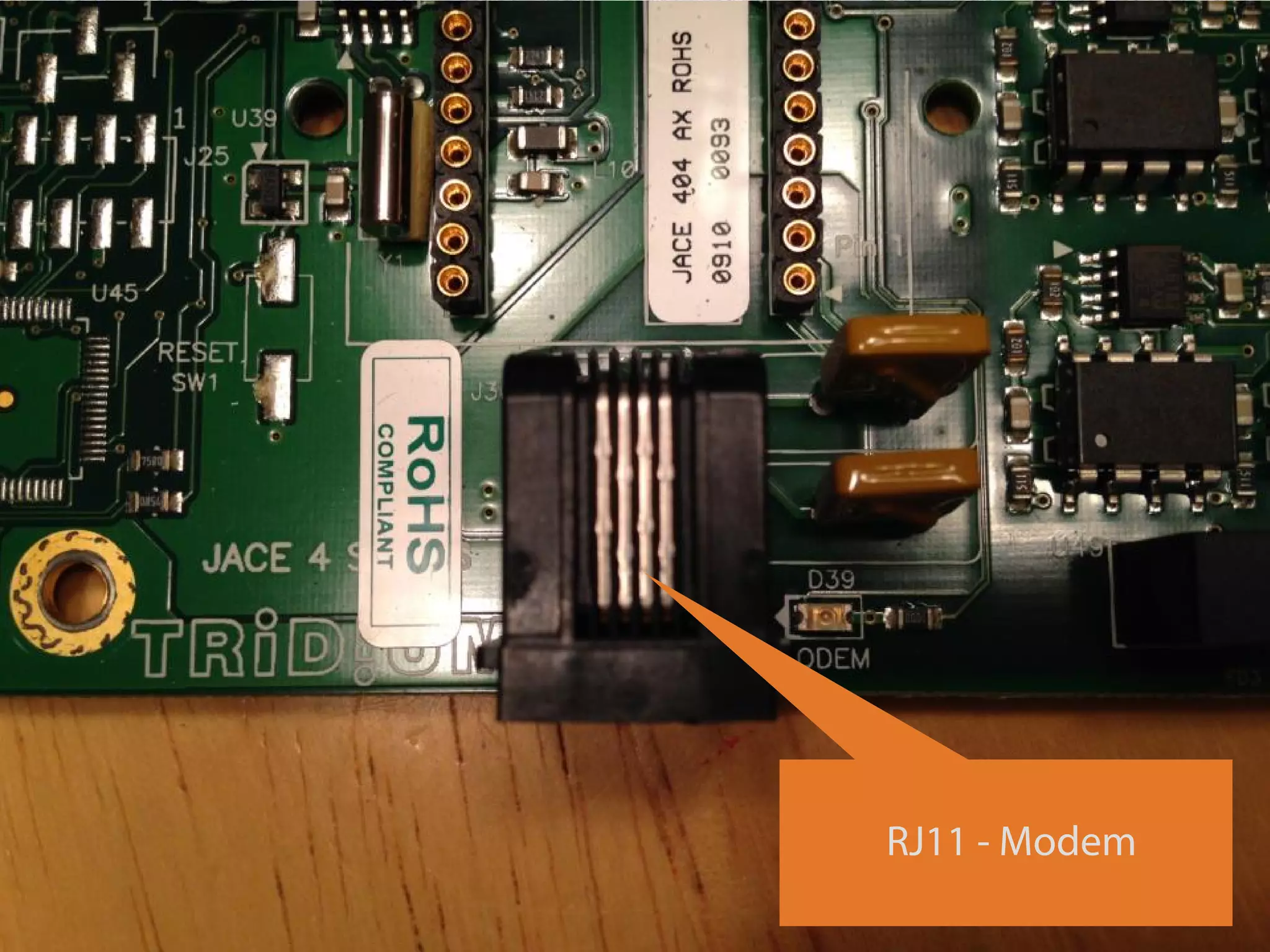
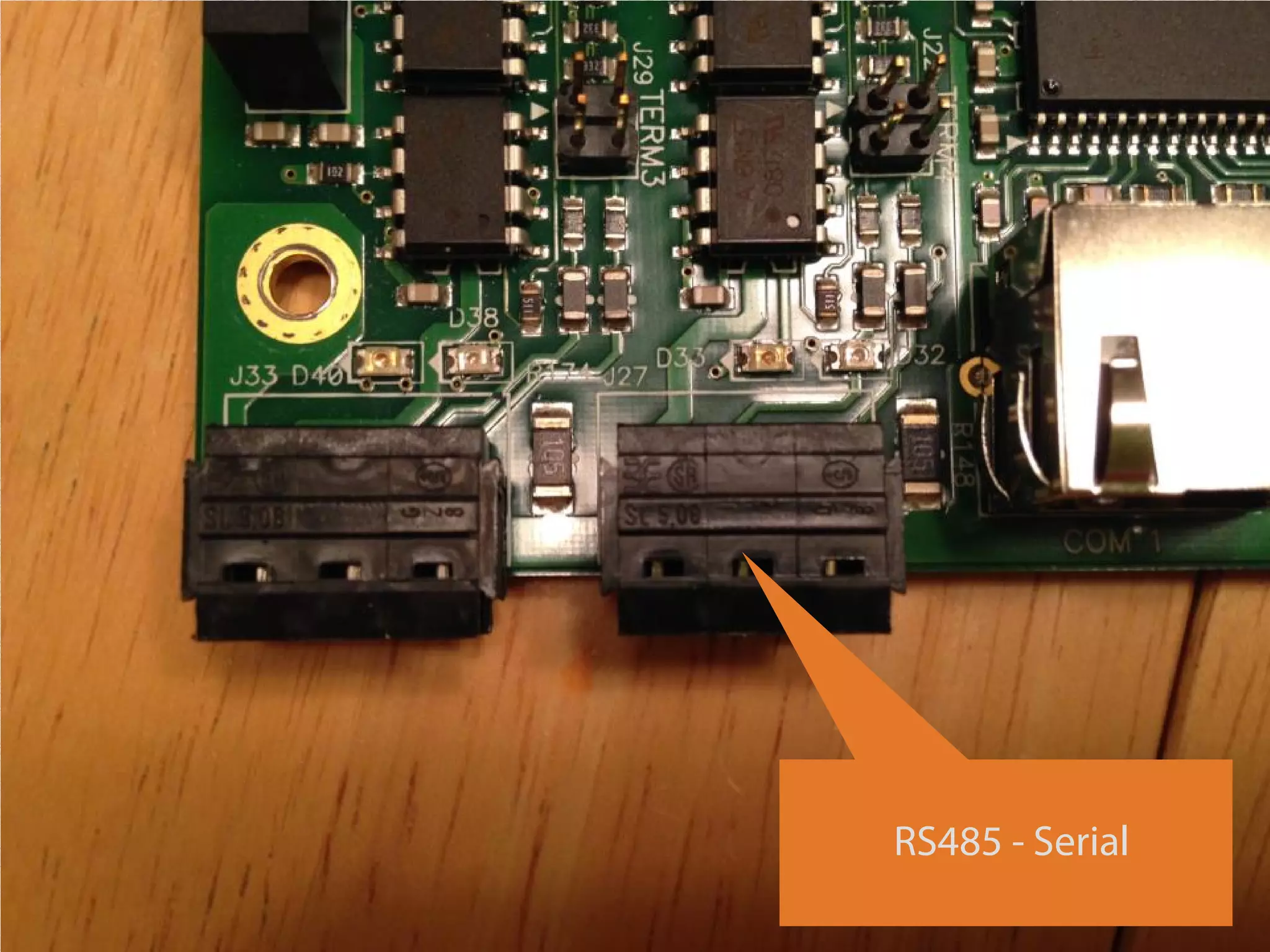
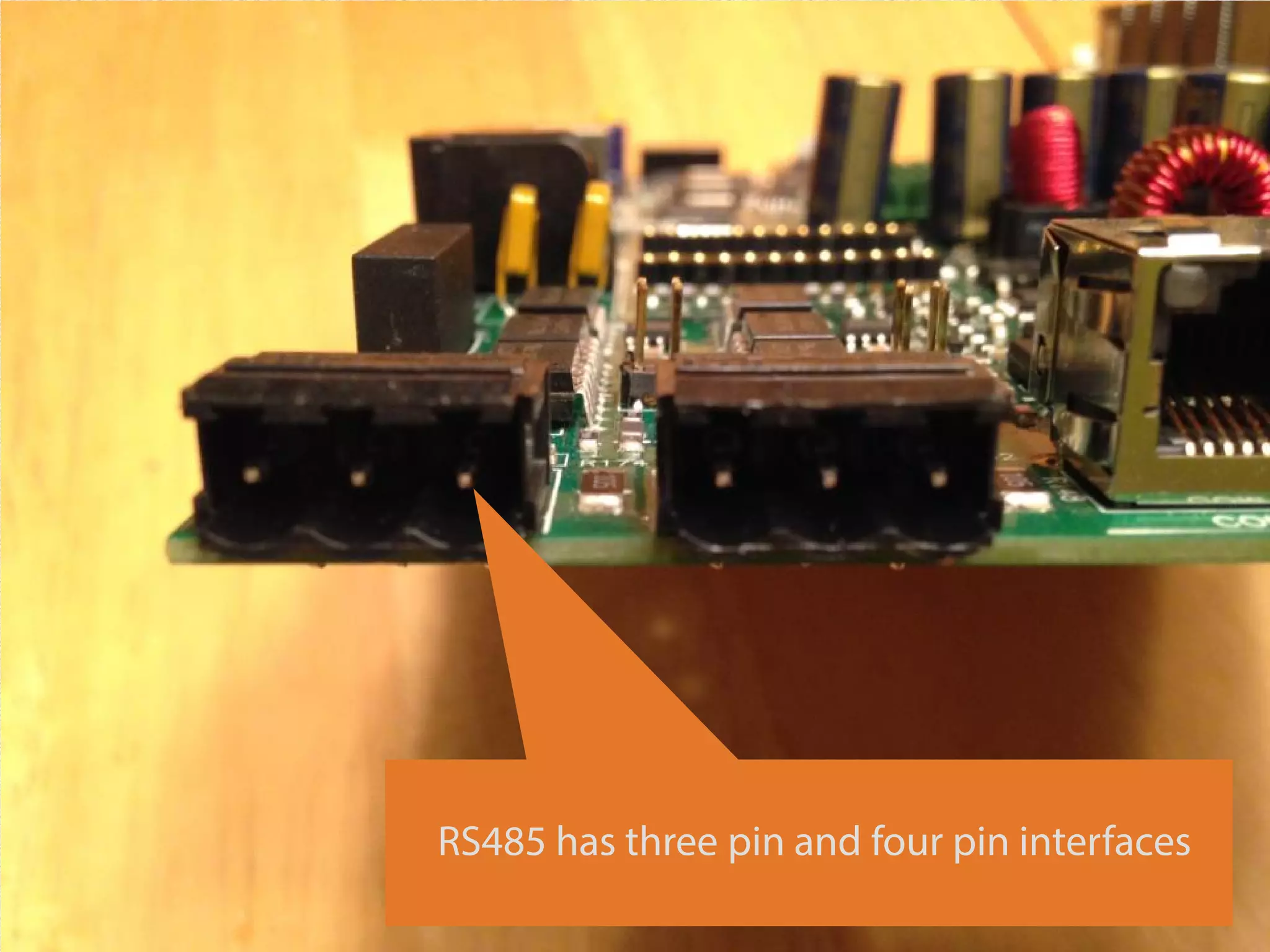
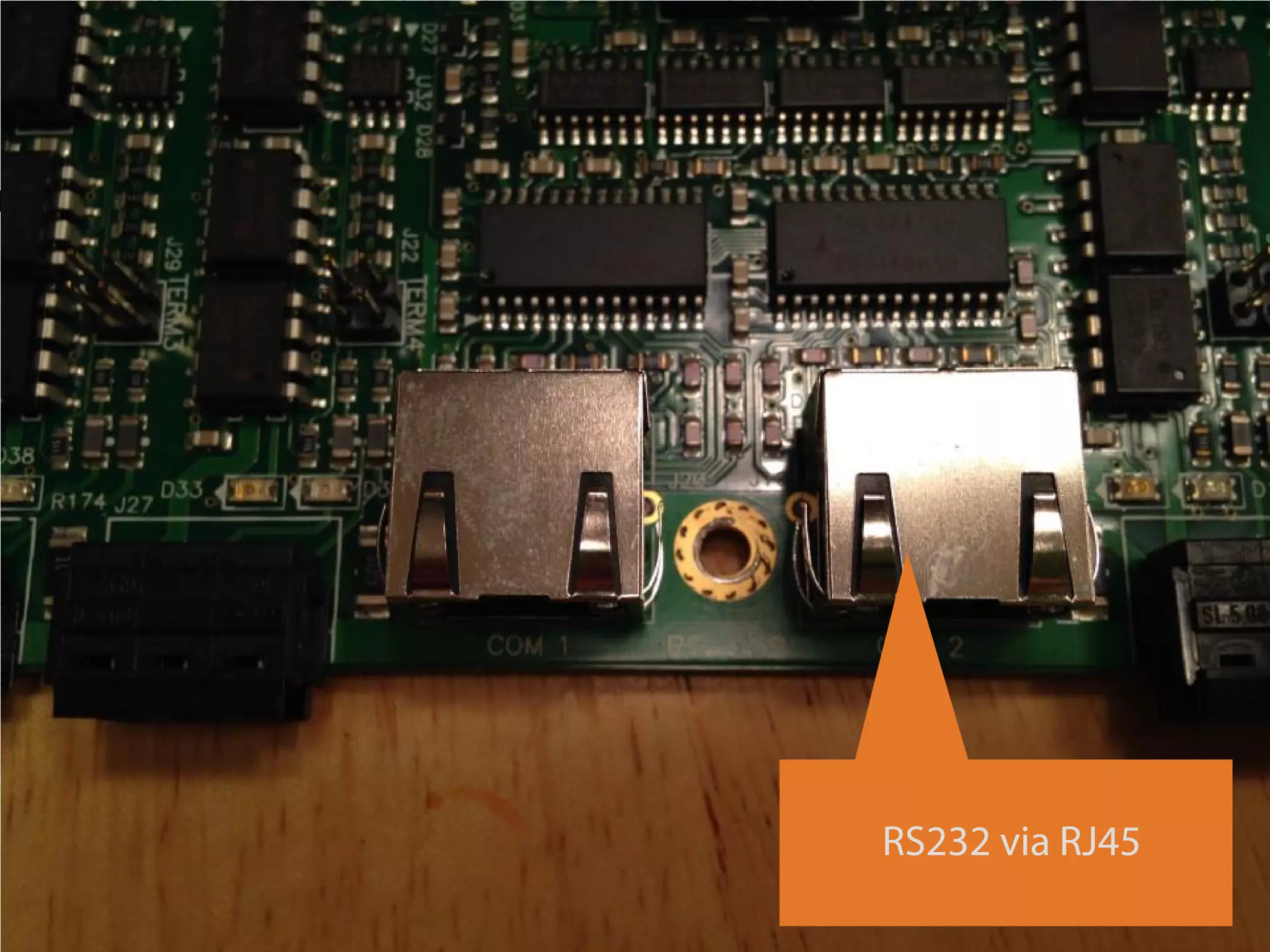
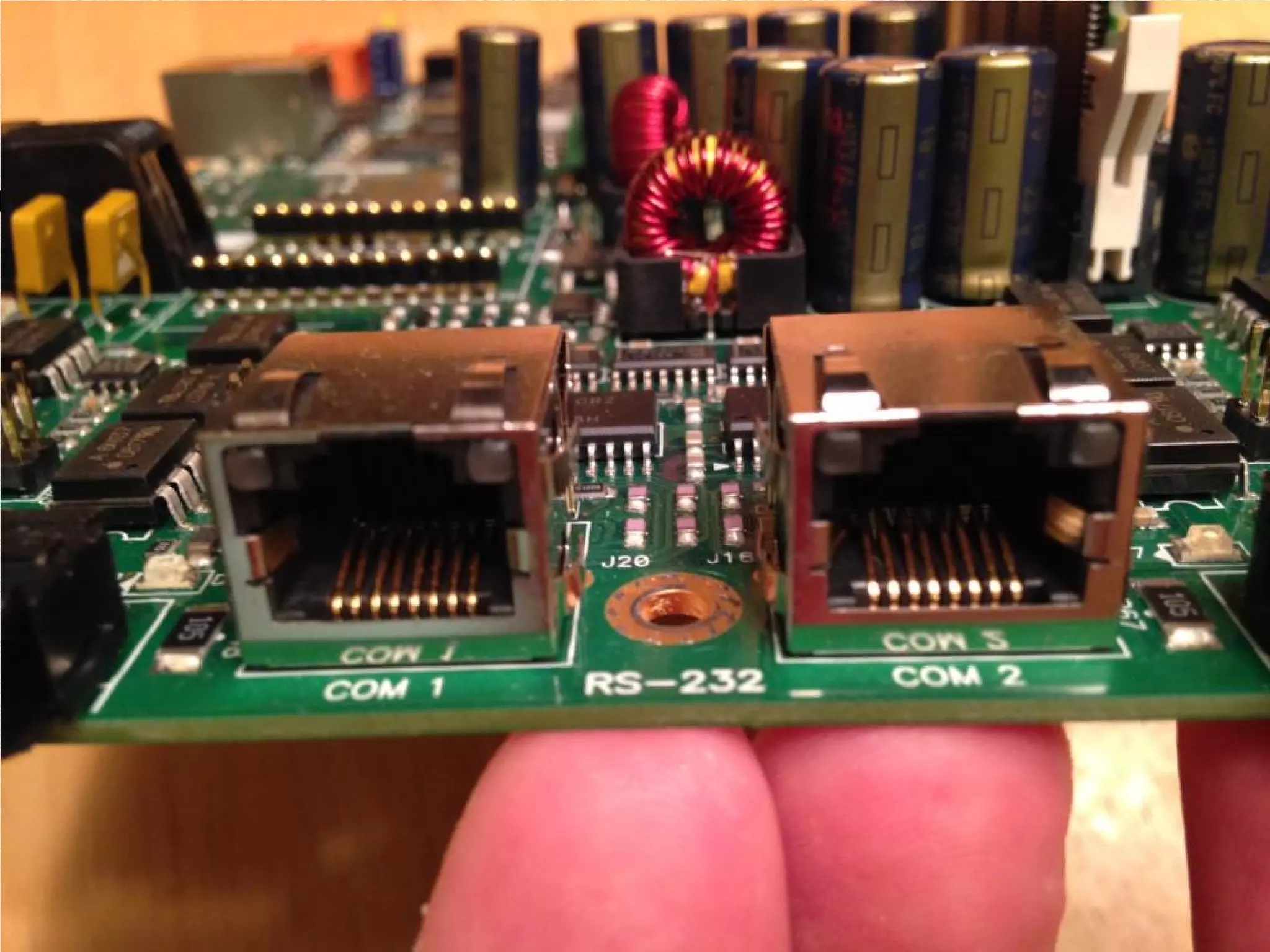
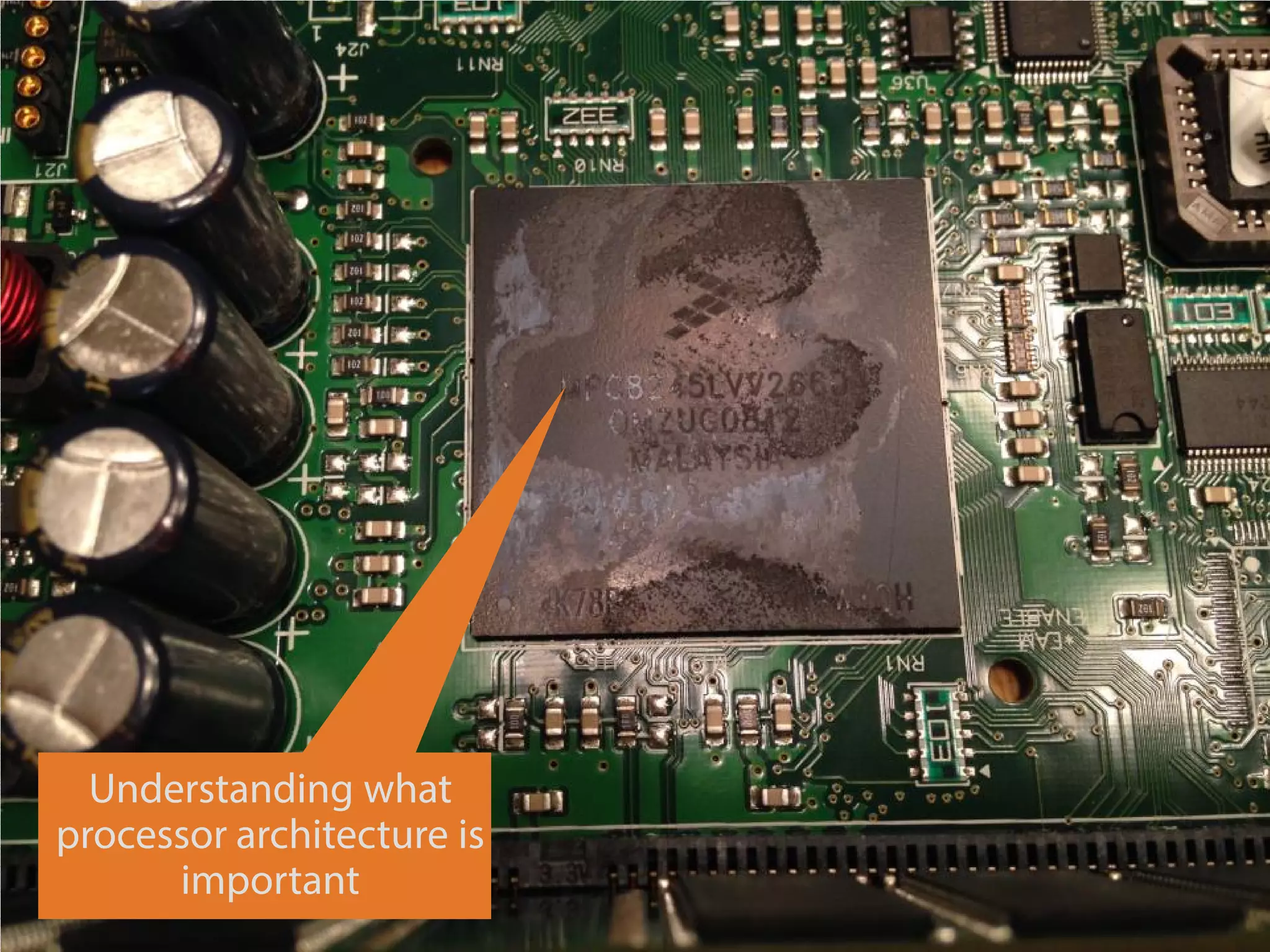
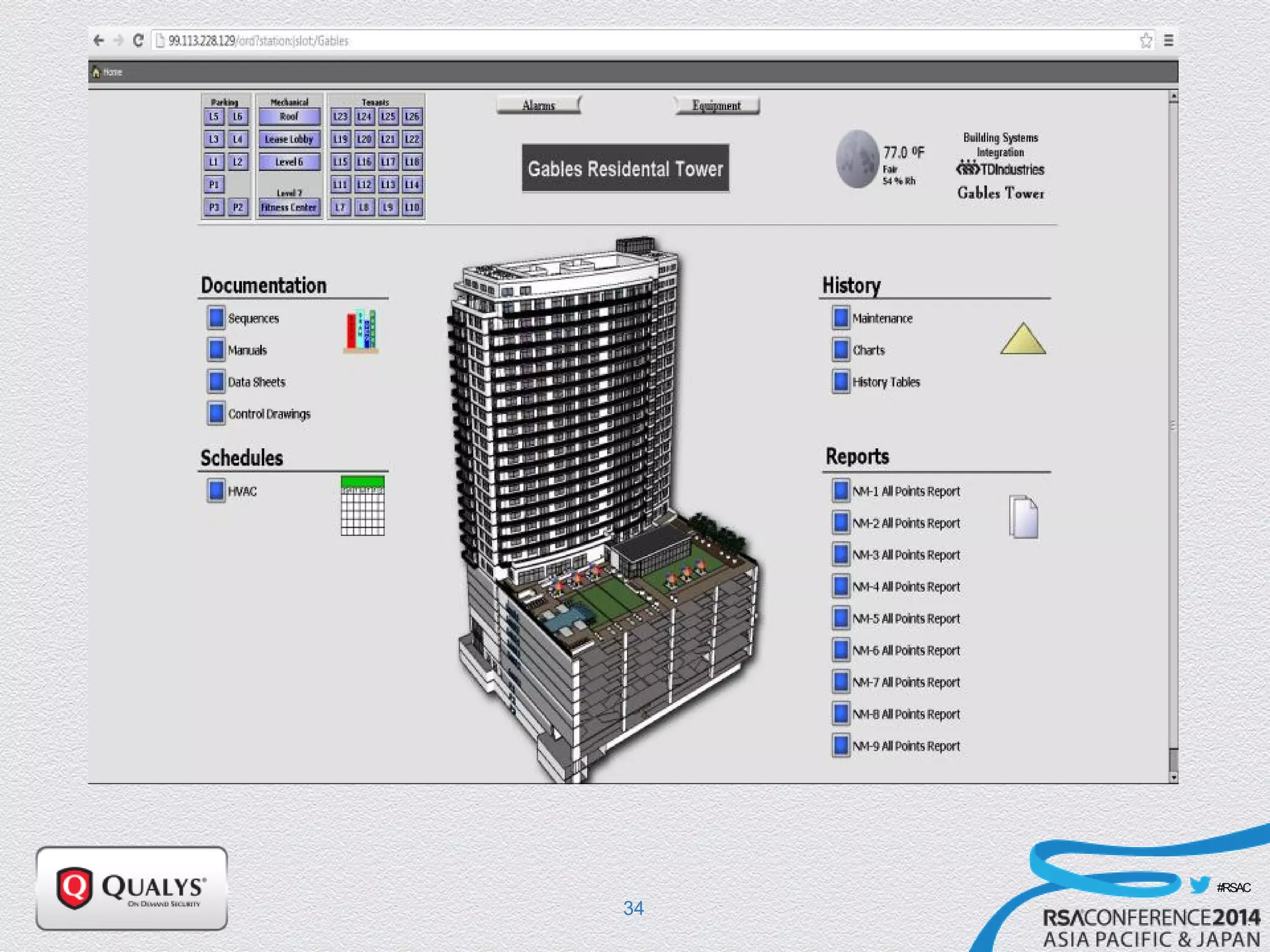
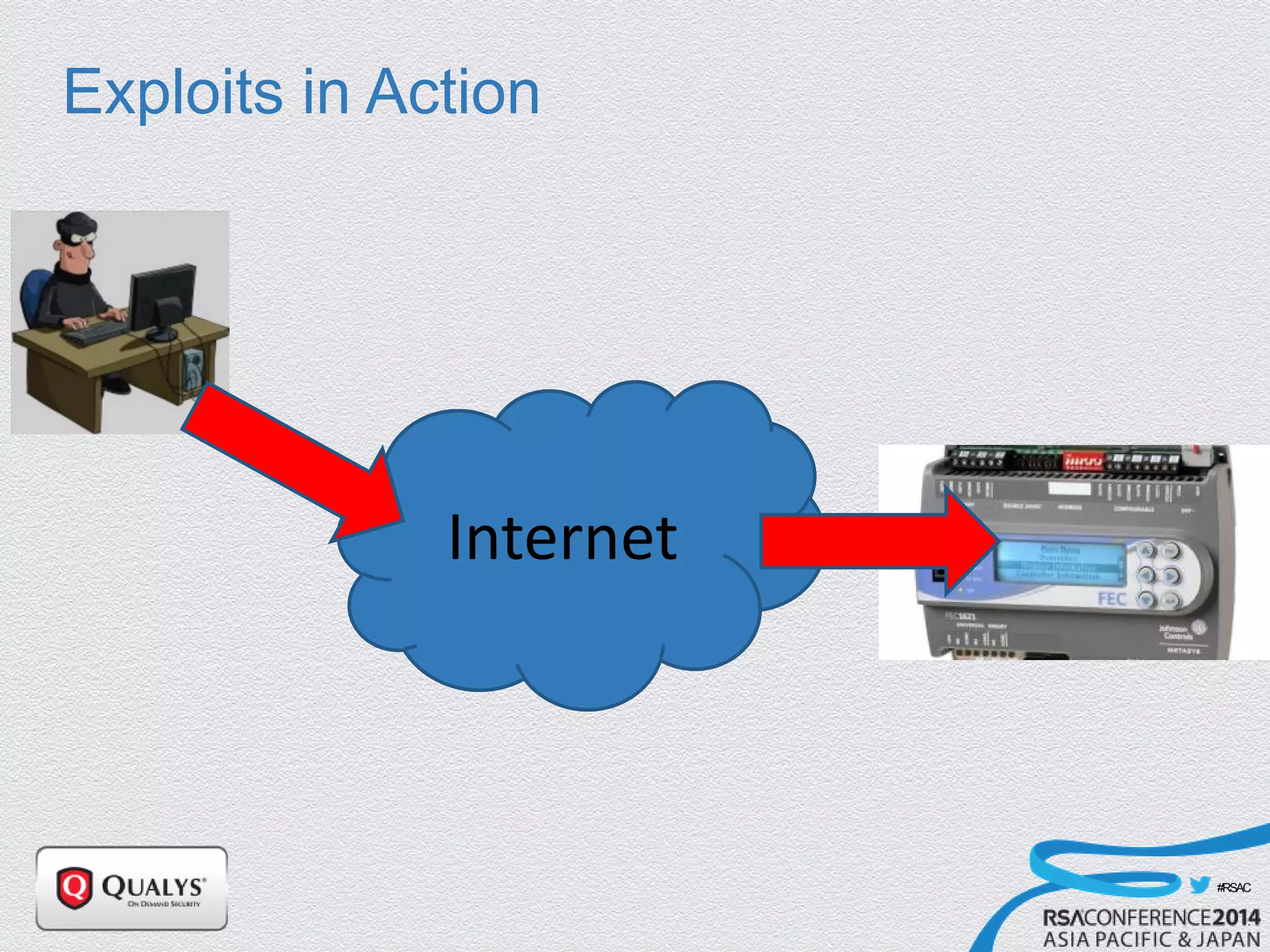
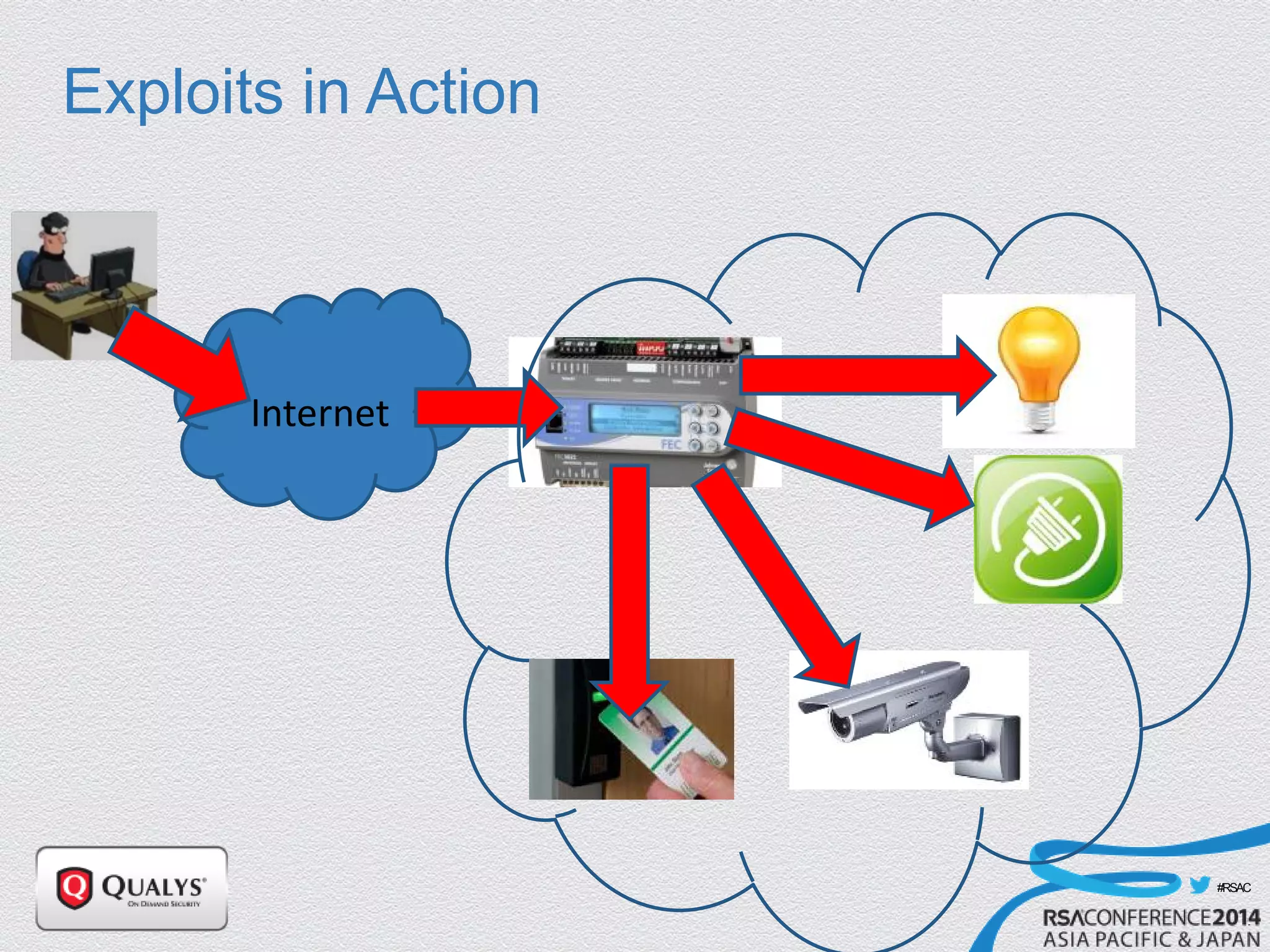
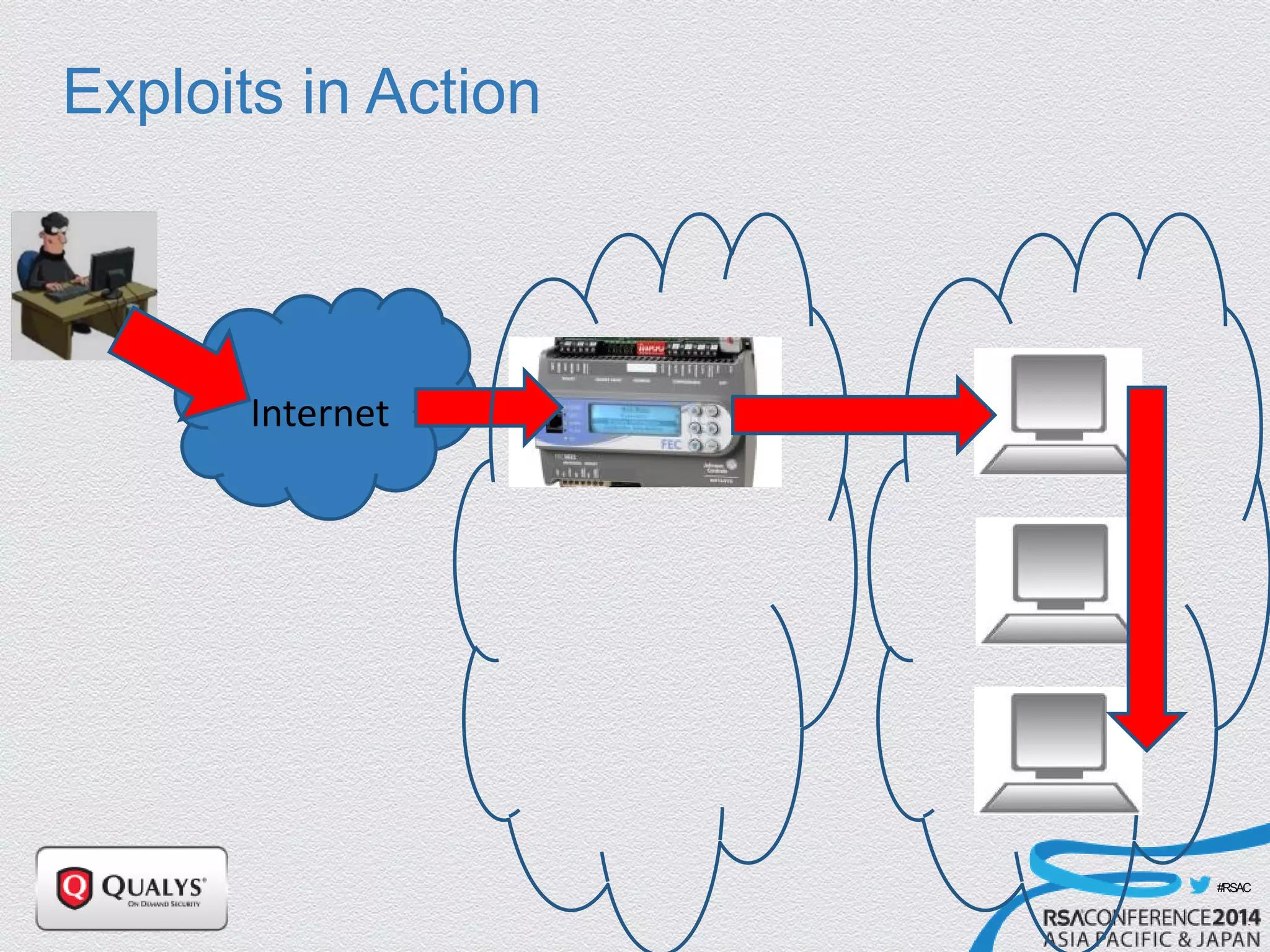
The document details a presentation on IoT security, highlighting vulnerabilities in smart devices and the potential for exploitation, particularly in building automation systems. It discusses past incidents, including a notable attack involving over 750,000 malicious emails and compromised medical devices. Key recommendations emphasize the importance of assessing remote management practices, engaging security teams early in device acquisition, and monitoring network traffic to mitigate risks.