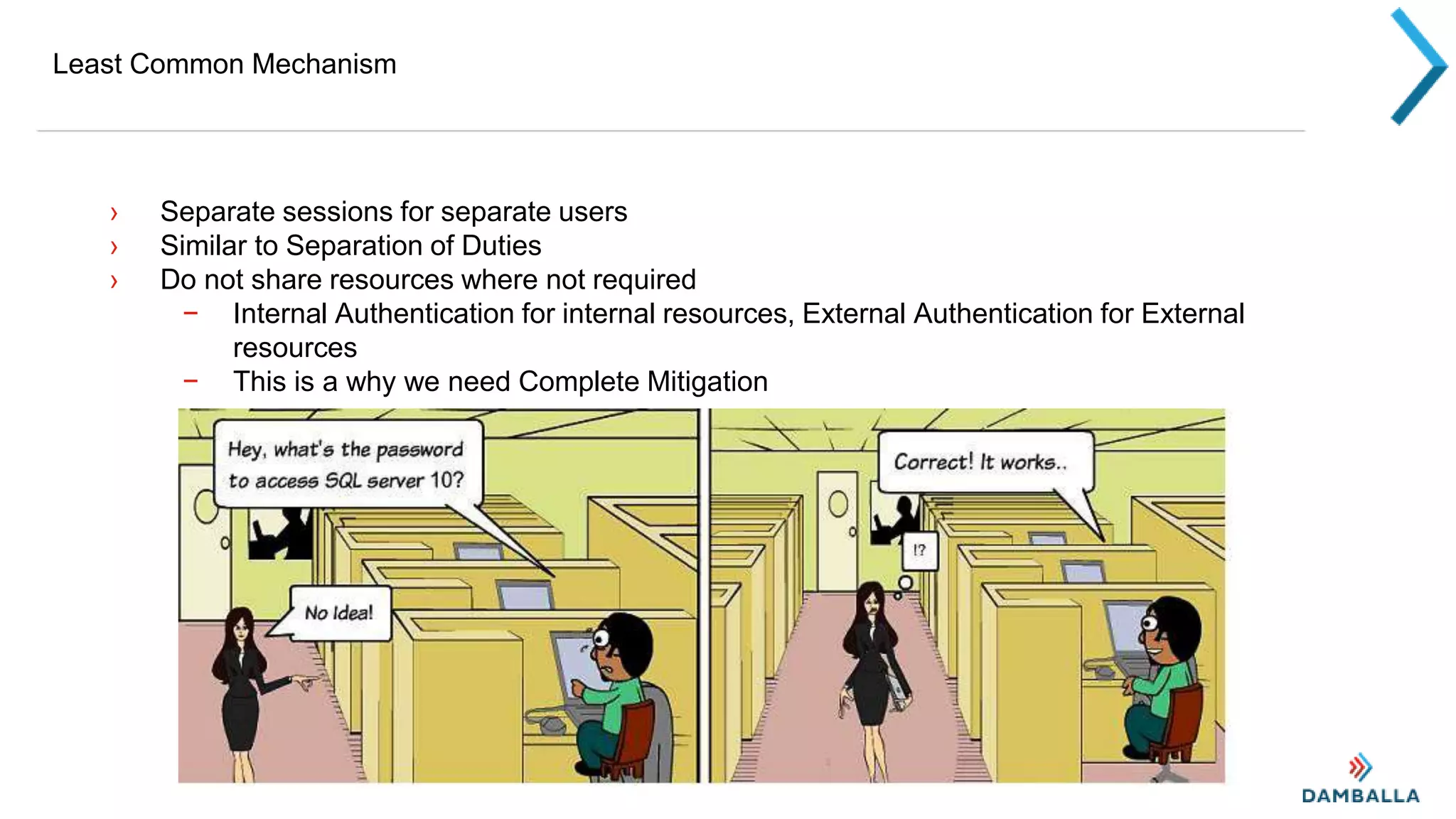
This document outlines principles of secure system design, beginning with assumptions that secrets are not safe, the network is untrusted, and help should be sought. It then describes 9 primary design principles: principle of least authority, failing securely, keeping it simple, mediating all access, open rather than obscure designs, separation of duties, least common mechanisms, psychological acceptability of security, and defense in depth. Examples are provided for each principle. The document notes some additional considerations like password management and two-factor authentication.