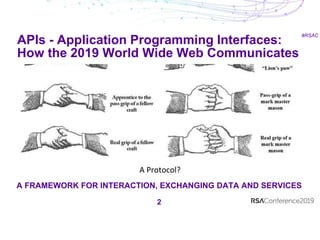
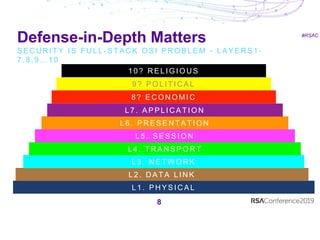
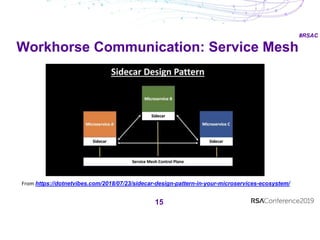
The document discusses security best practices for APIs and containers. It recommends establishing guardrails for authentication, data lifecycle, integration, deployment, changes, and testing. Guidelines should allow flexibility in tools and methods while ensuring consistency. Security must be integrated throughout the development process, and anomalies should be monitored to detect issues. While new technologies enable agility, responsibility is needed to ensure security is not compromised.