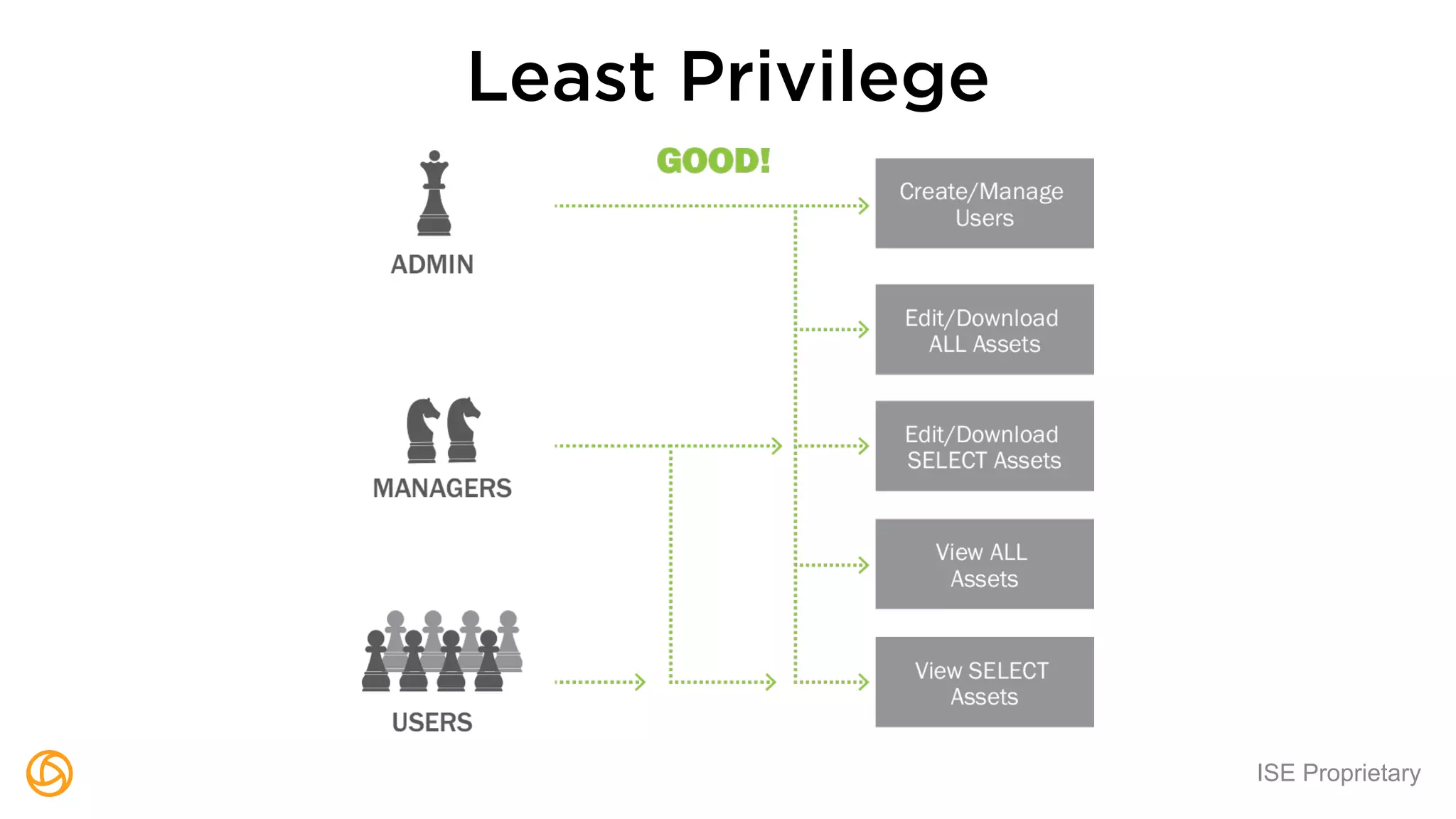
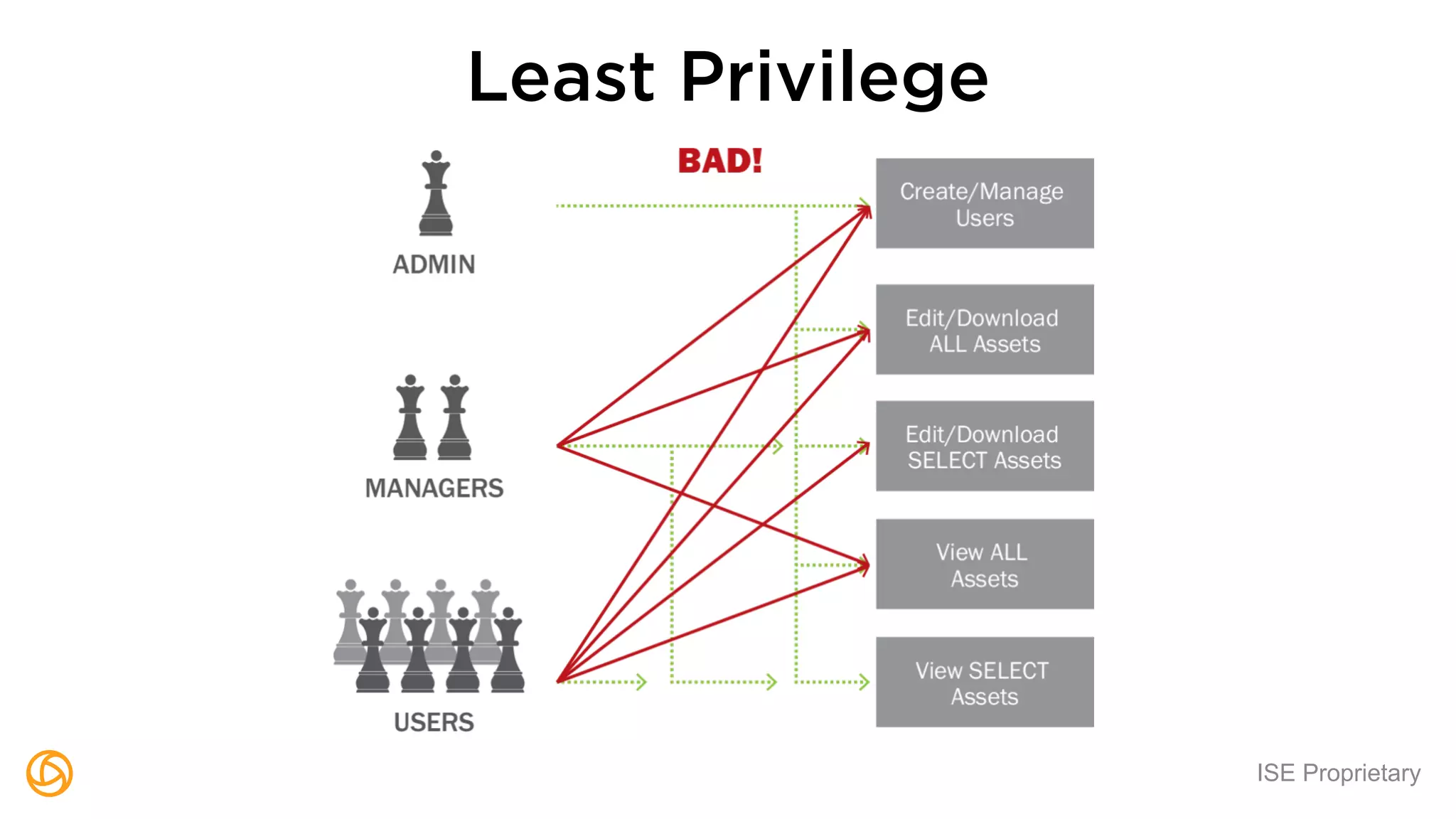
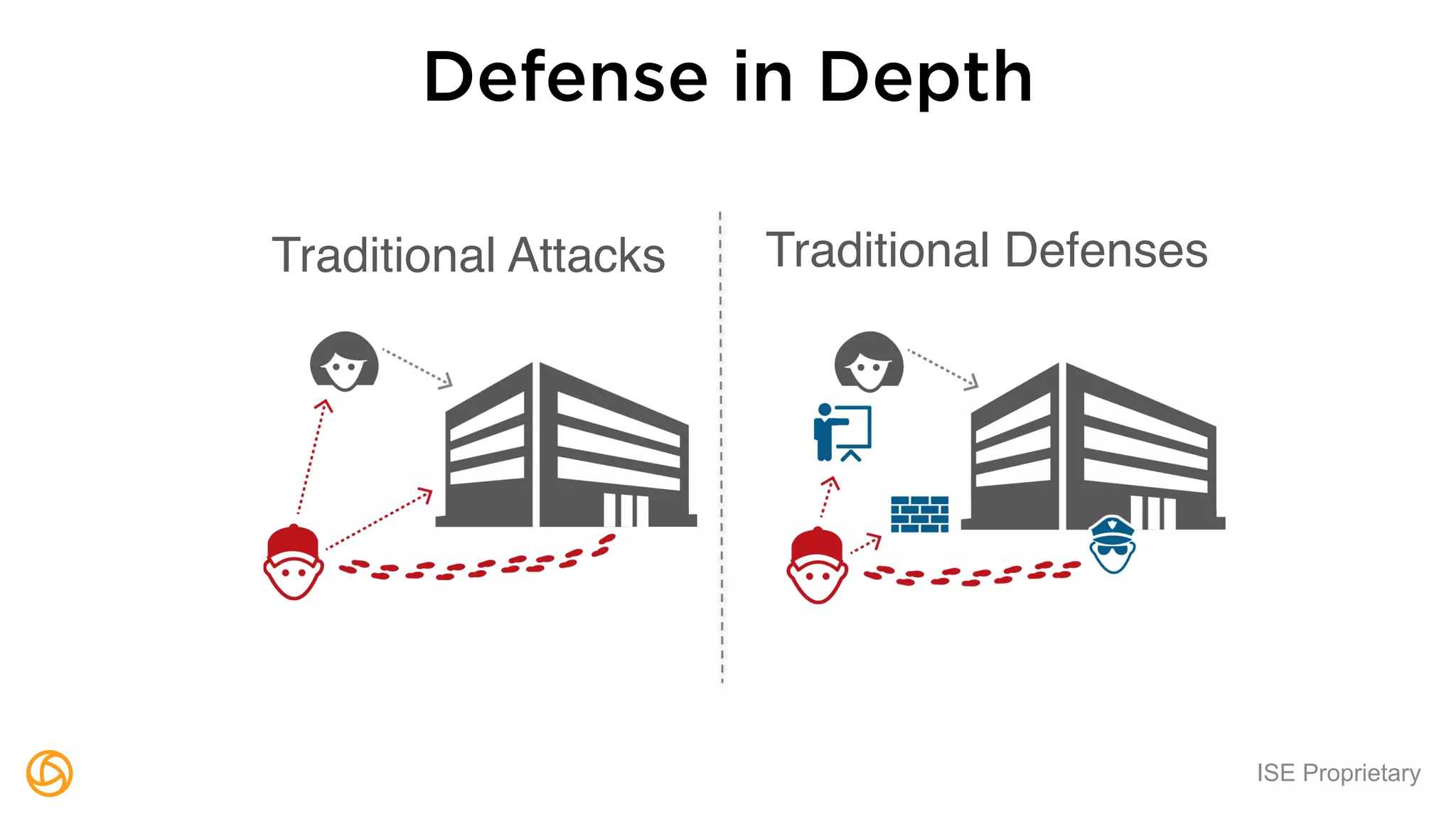
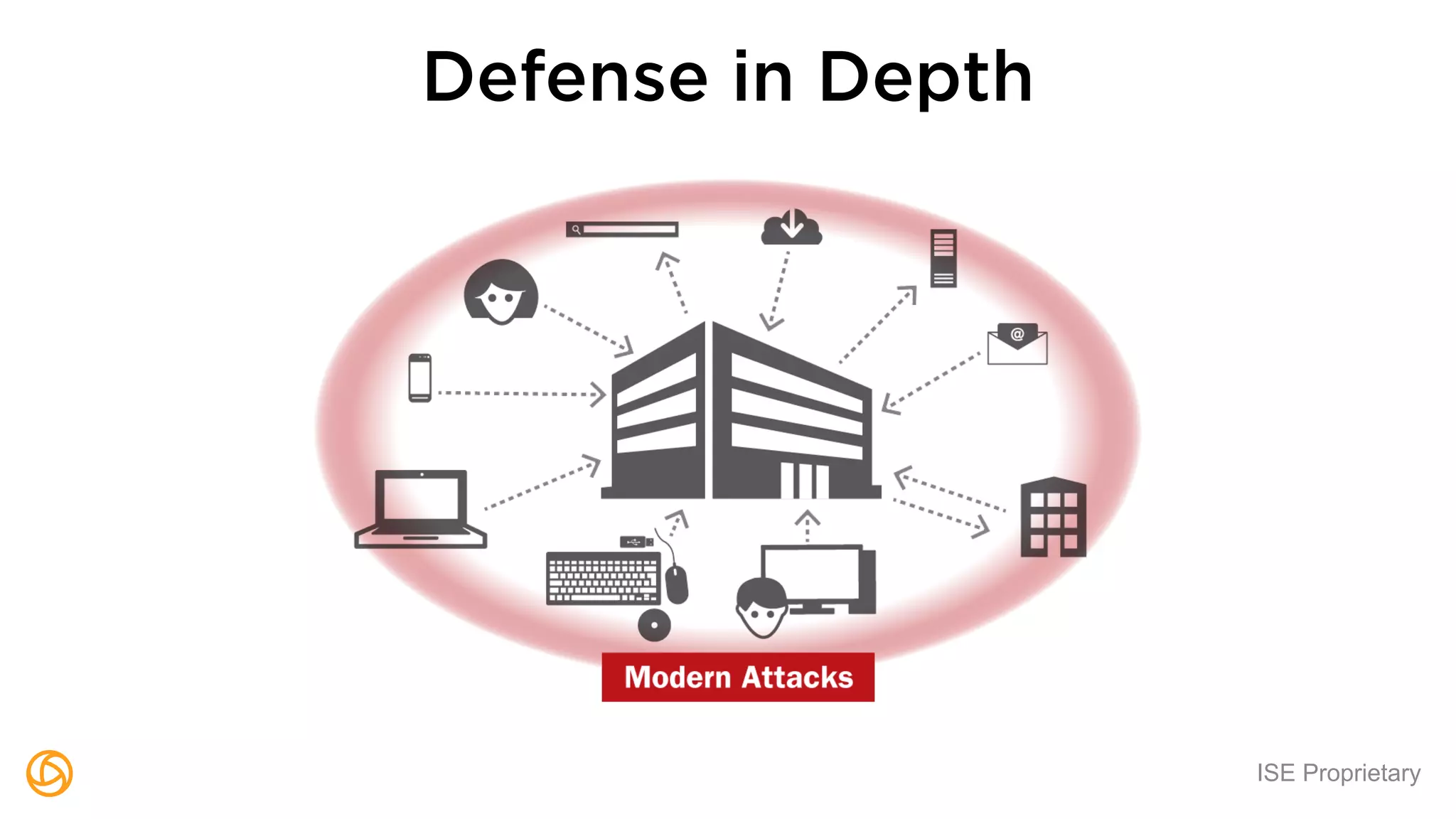
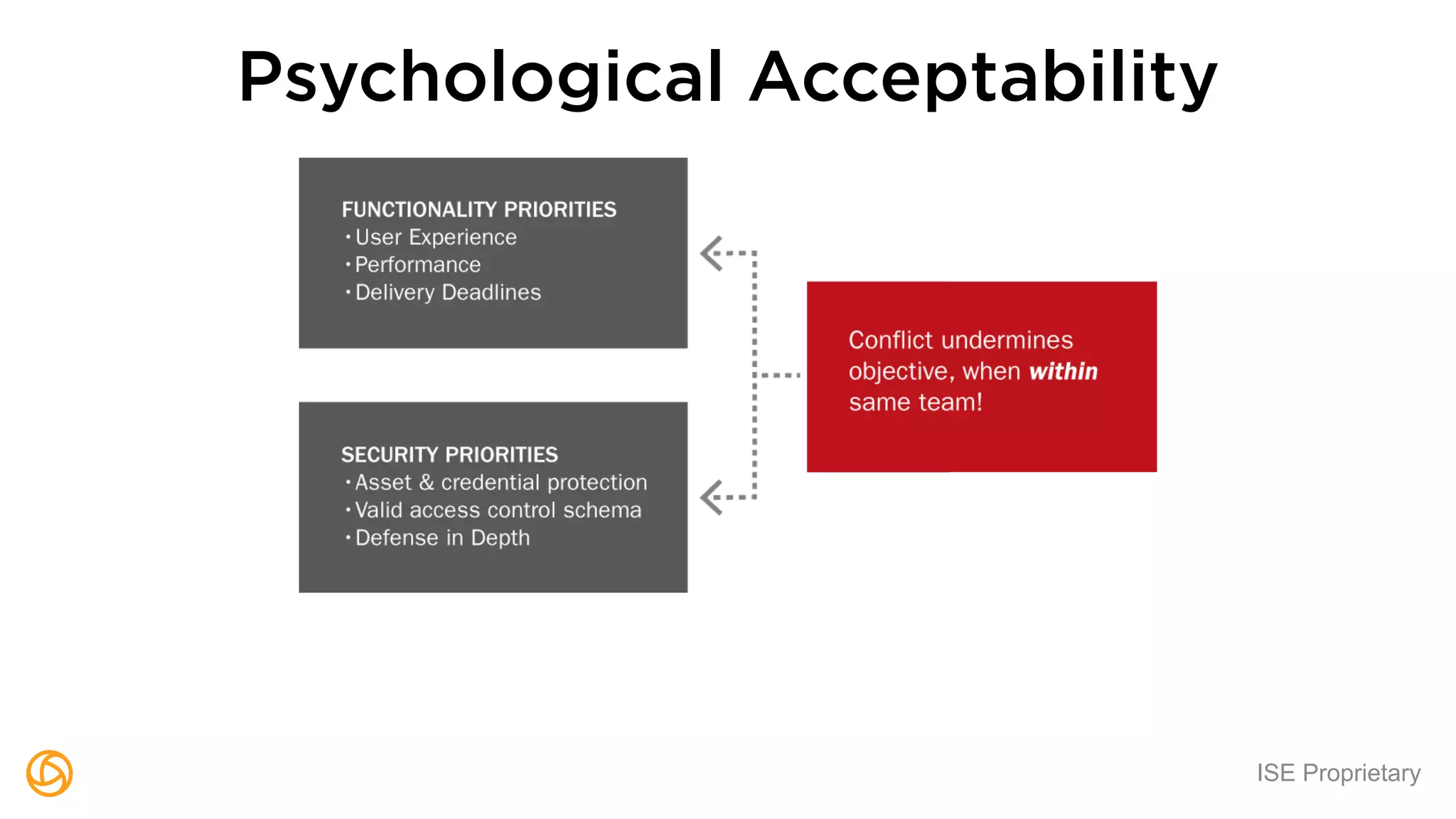
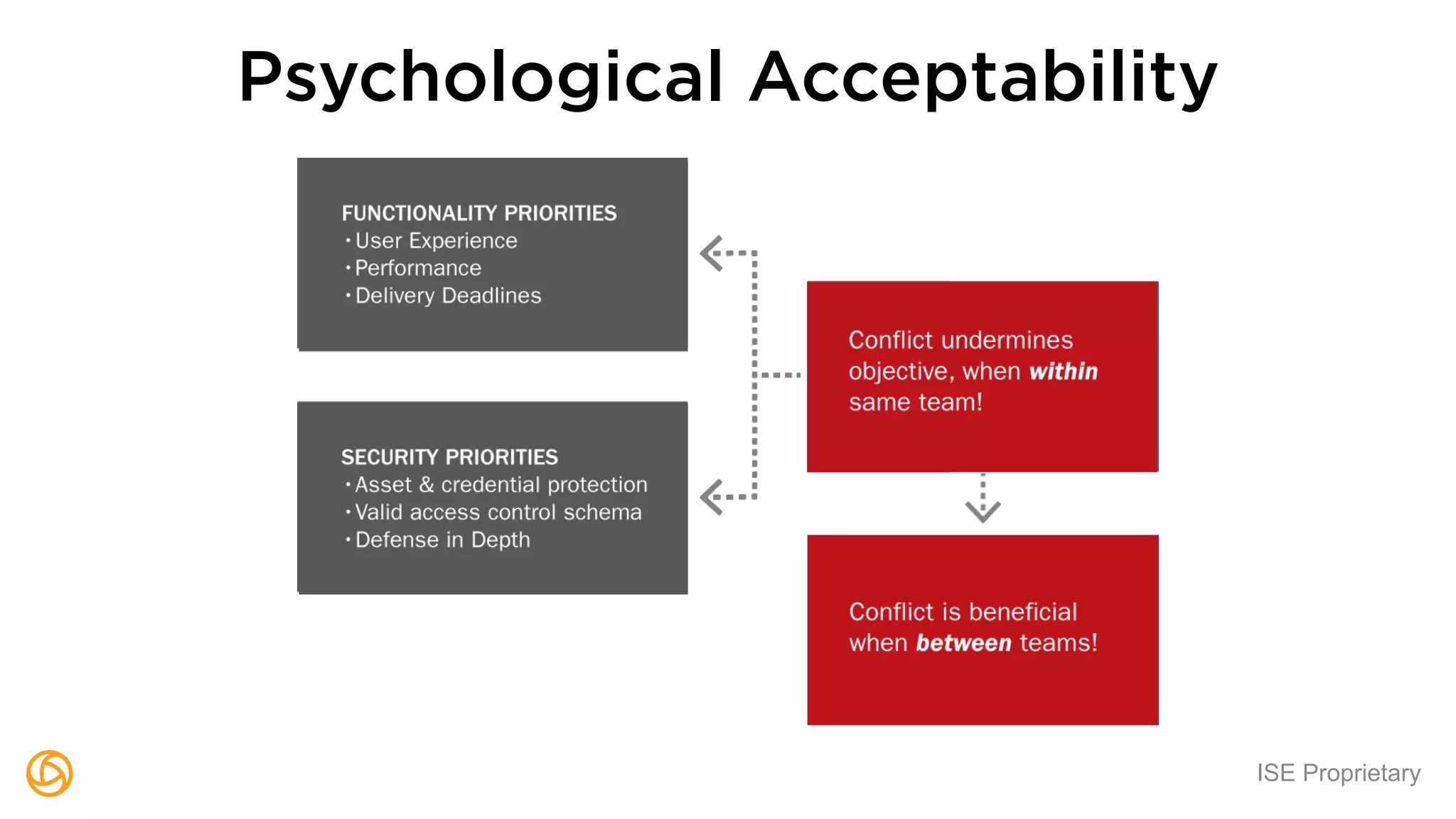
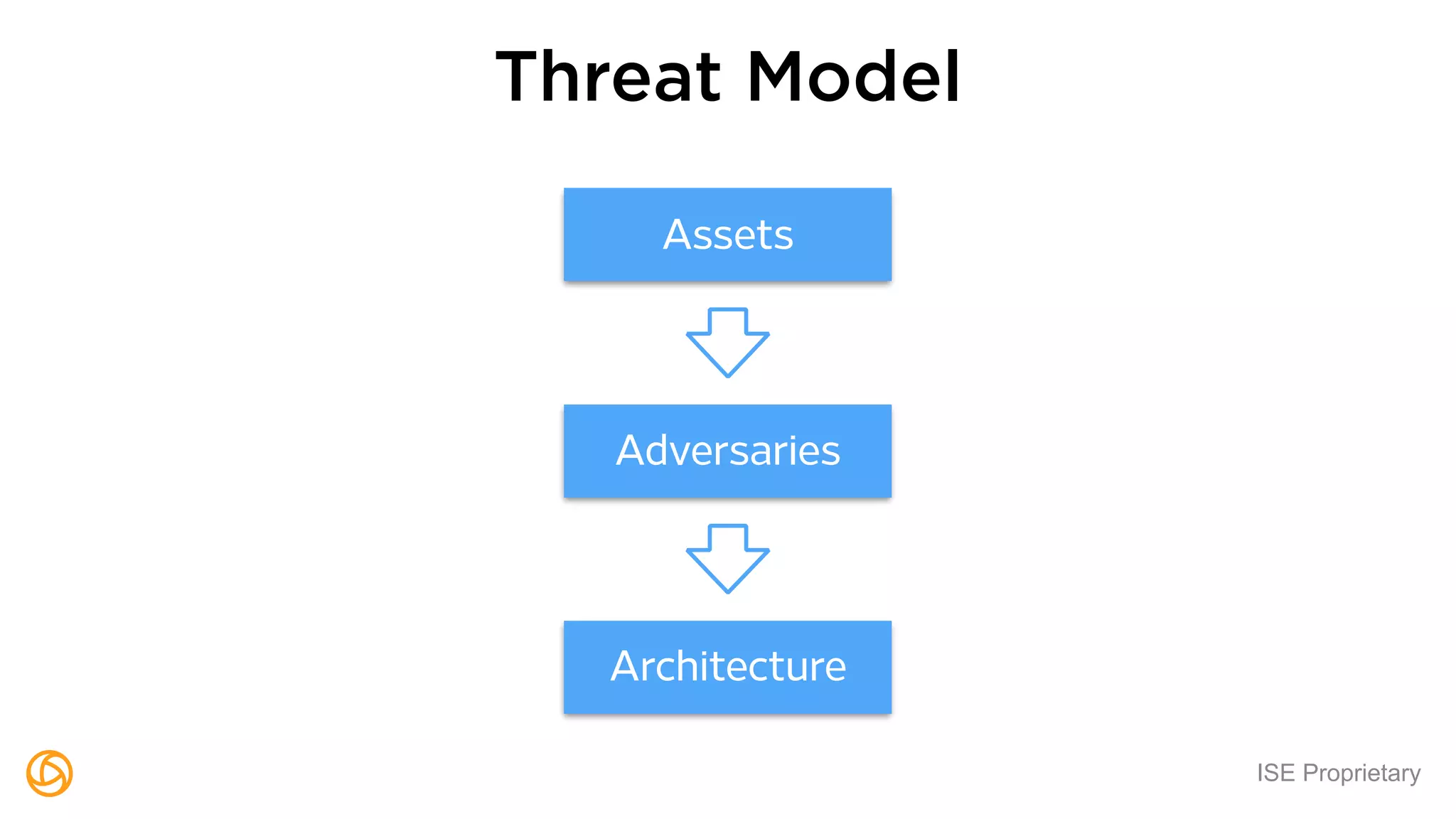
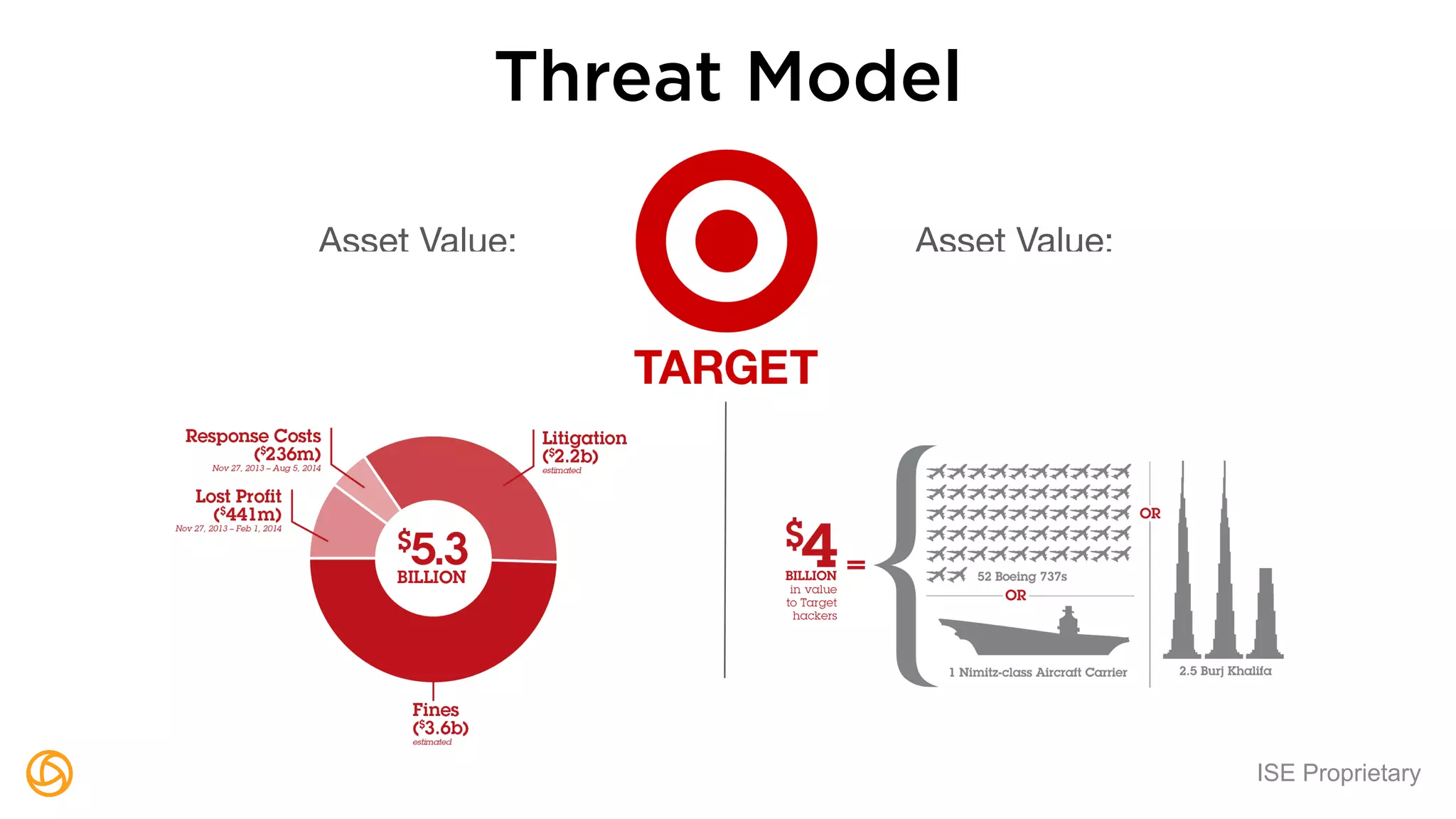
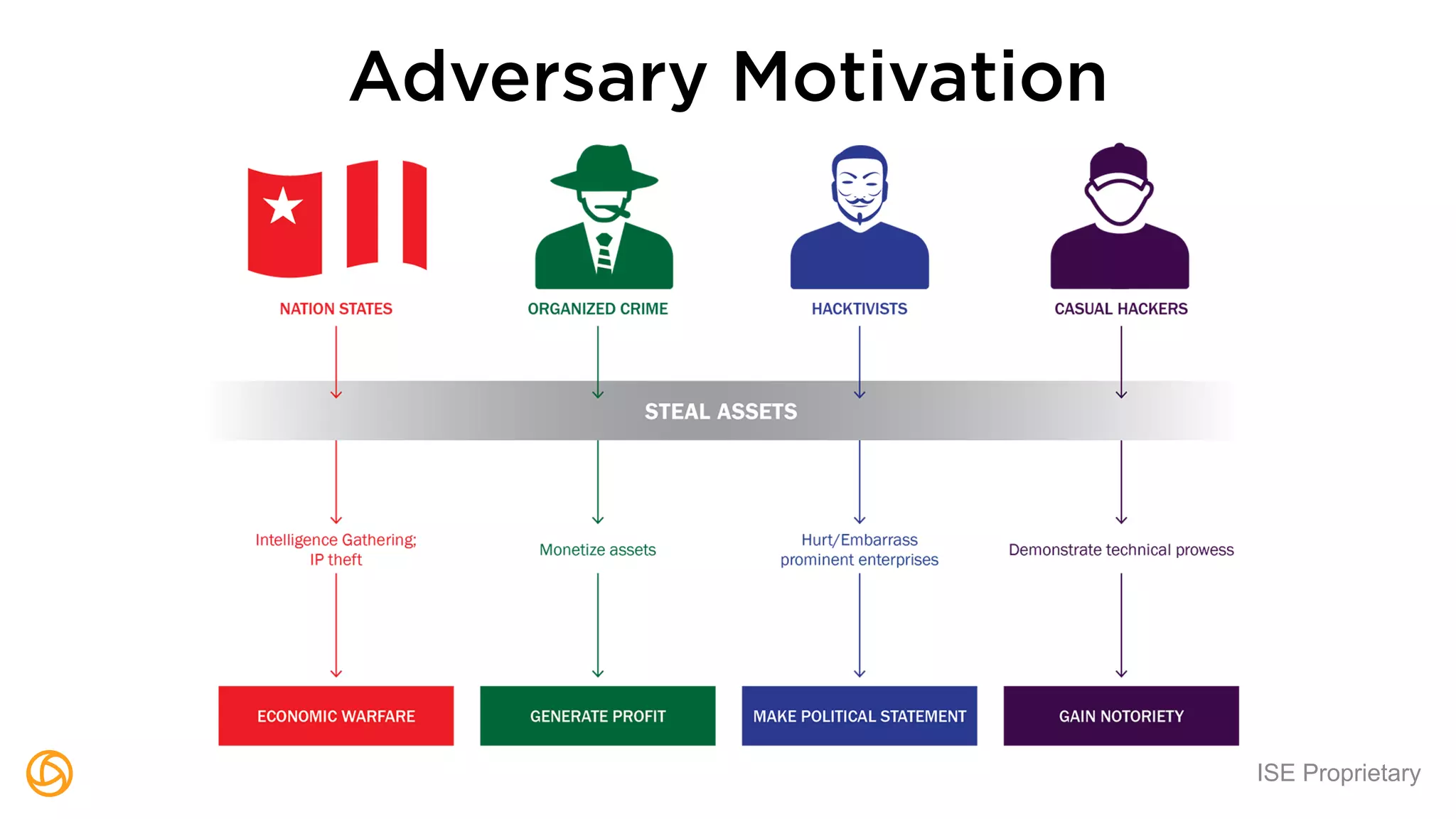
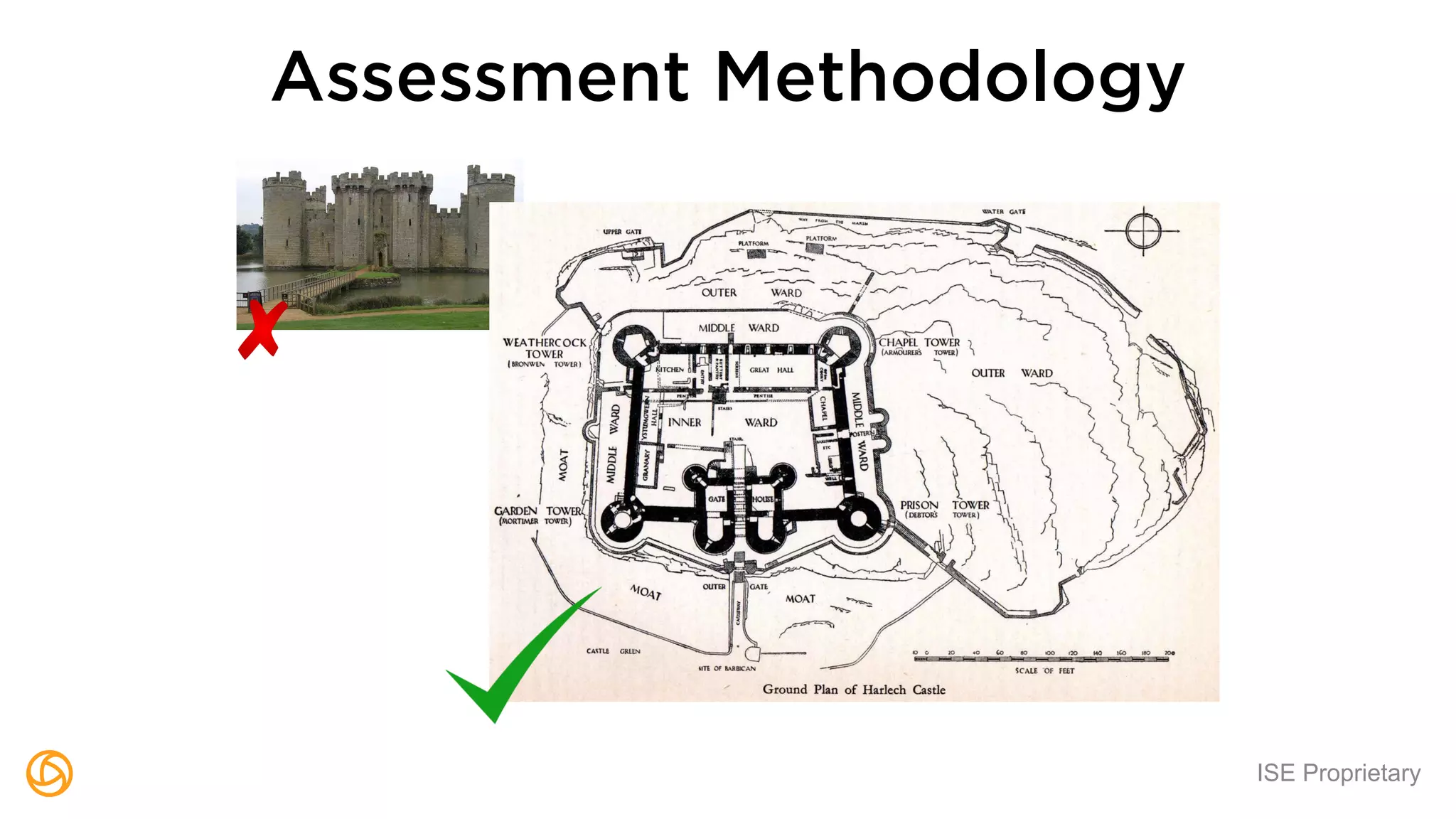
The document outlines a webinar hosted by Globaledit featuring Matt Glueckert and Ted Harrington, focusing on enterprise application security. Key topics include secure design principles, threat modeling, and defense strategies against traditional attacks. The session is scheduled for February 10th at 2 PM ET.