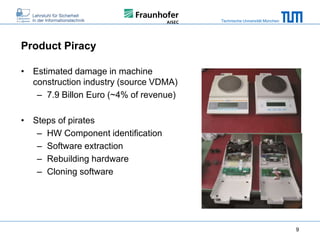
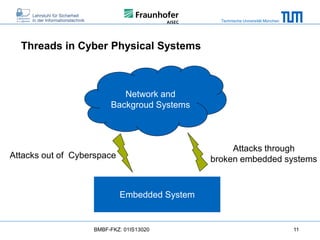
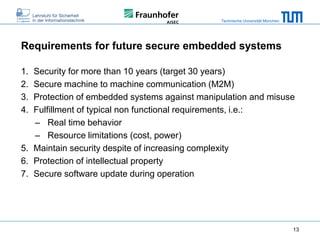
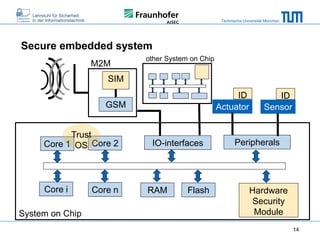
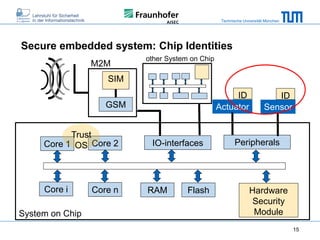
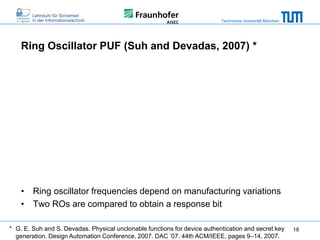
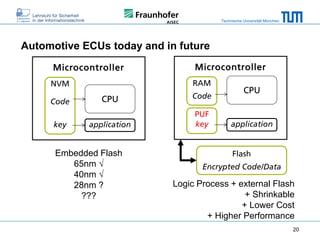
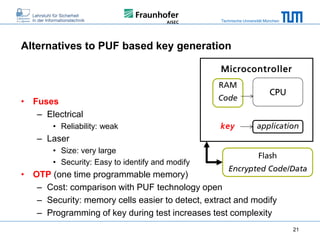
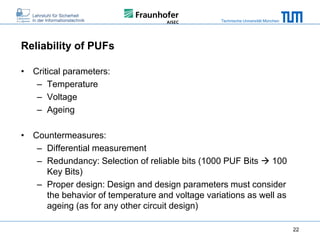
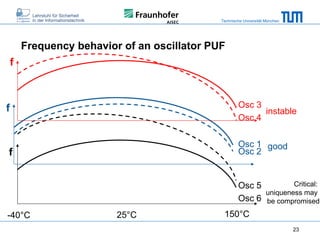
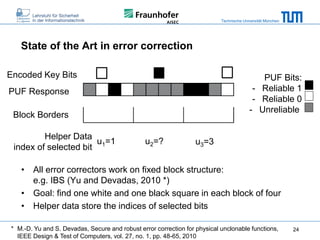
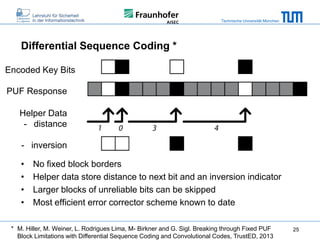
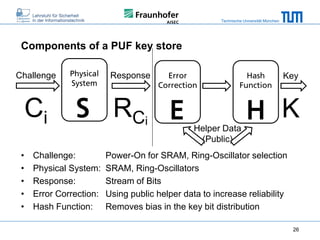
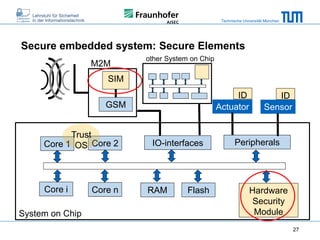
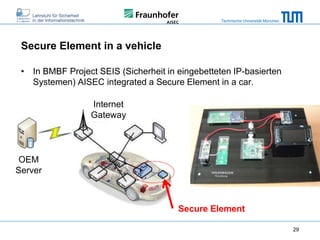
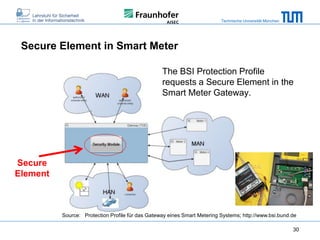
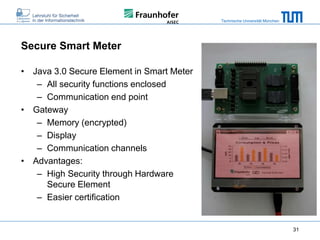
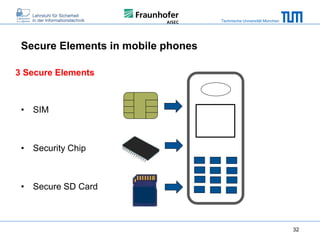
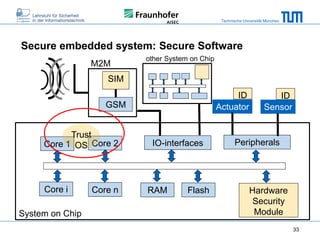
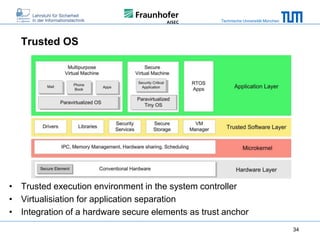
The document discusses secure embedded systems as a requirement for cyber physical systems and the internet of things. It begins by providing examples of attacks on modern embedded systems like cars, industrial control systems, smart grids, and medical devices. It then discusses trends increasing security risks for embedded systems like network connectivity and standardization. Finally, it outlines requirements for future secure embedded systems and describes techniques like hardware security modules, secure elements, physical unclonable functions, and trusted operating systems to provide security in embedded systems going forward.