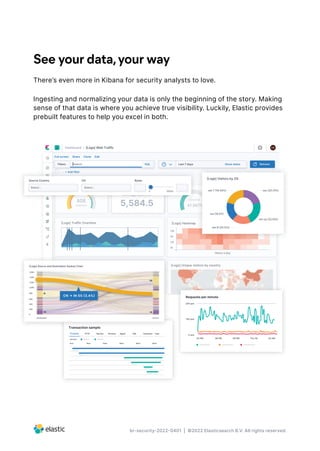
Elastic Security provides security teams with a unified platform to prevent, detect, and respond to cyber threats at scale. It allows teams to search across petabytes of data in seconds, gain visibility across cloud, network, and endpoint data through one-click integrations, and accelerate investigations and incident response through built-in case management and collaboration tools. Elastic Security offers capabilities for threat prevention and detection, hunting and investigation, continuous monitoring, and analytics on large volumes of security data.