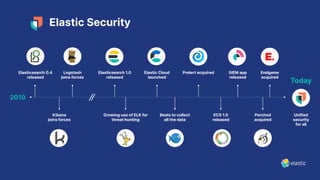
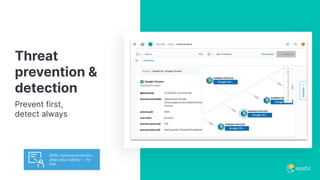
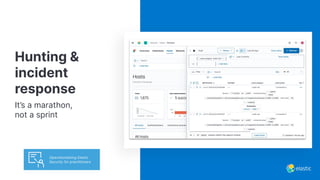
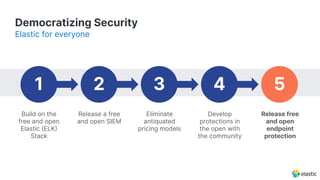
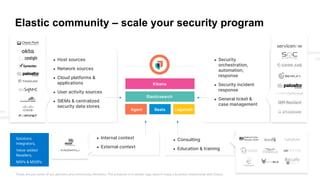
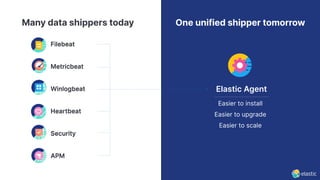
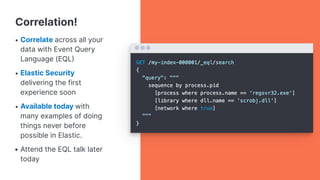
The presentation discusses the forward-looking statements related to Elastic's security offerings and their business outlook, emphasizing that actual outcomes may differ due to various risks and uncertainties. It highlights the evolution of Elastic Security, aiming to democratize security through a free and open SIEM, and discusses collaborative efforts with the security community to enhance protection. The document also emphasizes the importance of integrating diverse data sources for comprehensive security monitoring and incident response.