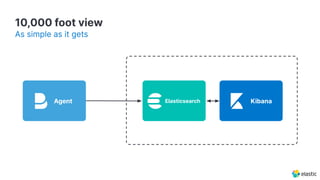
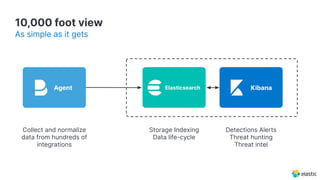
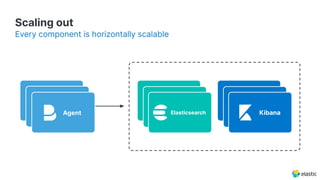
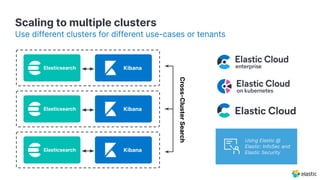
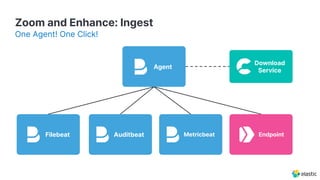
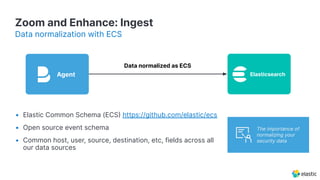
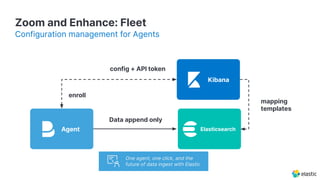
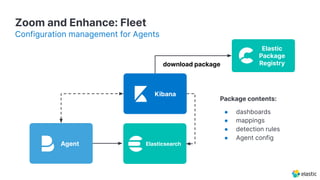
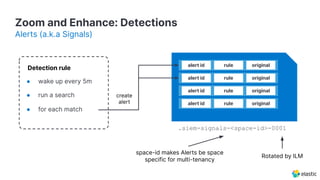
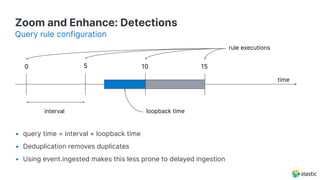
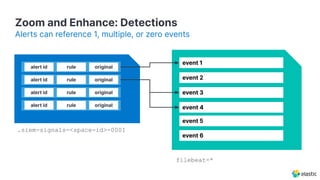
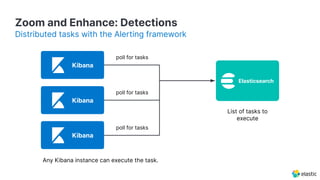
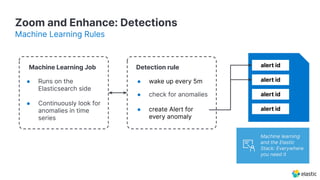
The document presents an overview of Elastic Security's features, including data ingestion, threat detection, and agent management within the Elastic Stack. It emphasizes the importance of normalizing security data using the Elastic Common Schema (ECS) and discusses the scalability of components like agents and Elasticsearch clusters. Additionally, it includes forward-looking statements regarding the company's future offerings and potential risks associated with uncertainties and market conditions.