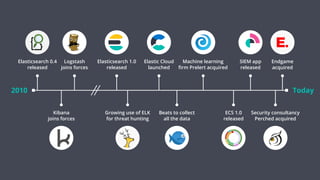
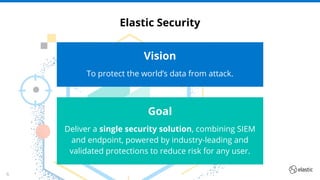
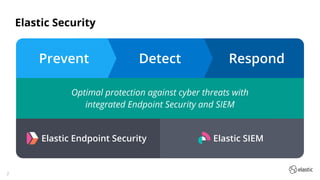
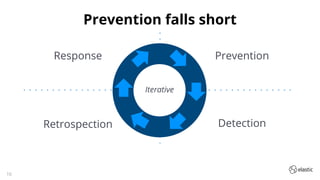
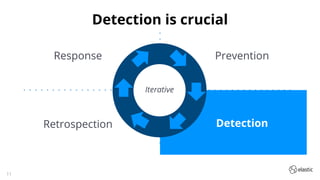
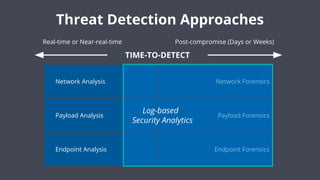
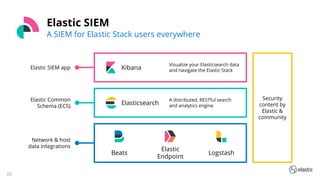
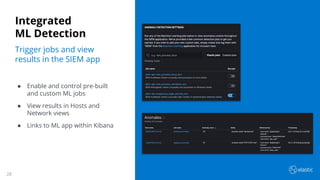
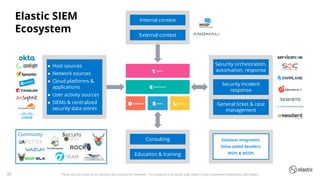
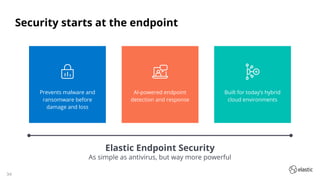
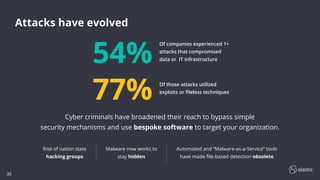
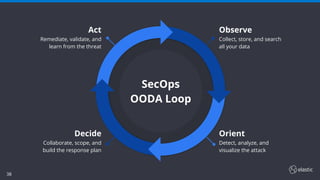
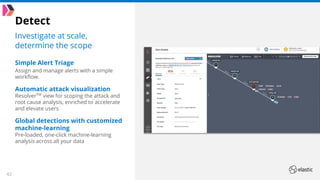
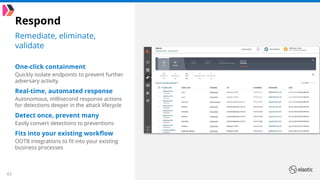
The document outlines the capabilities and offerings of Elastic Security, which combines SIEM and endpoint protection to safeguard organizations from cyber threats. It highlights the growth and evolution of the Elastic Stack, emphasizing features like real-time data processing, threat detection, and customizable security solutions through a zero-trust approach. Additionally, it includes a discussion of the challenges posed by modern attacks and the need for advanced security measures to protect against evolving cyber threats.