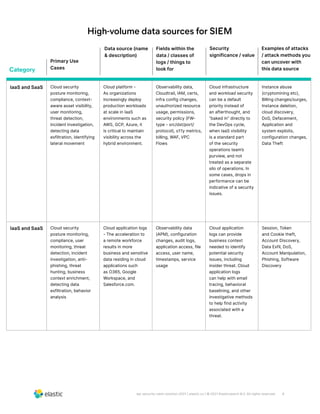
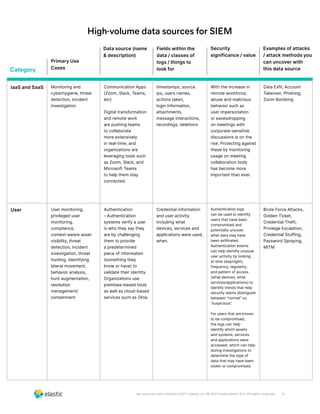
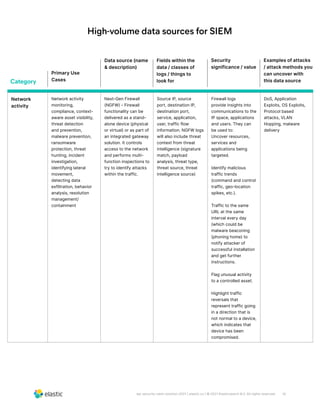
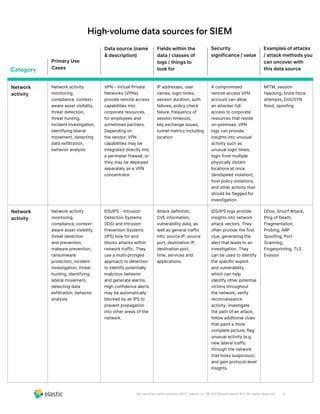
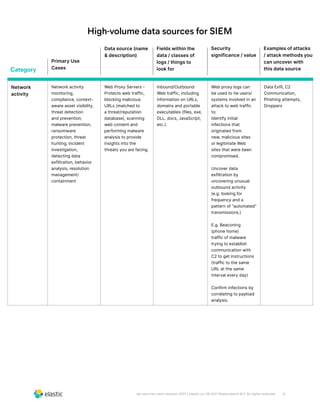
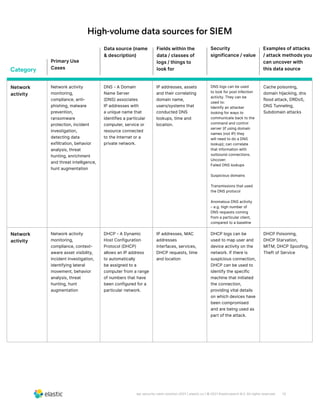
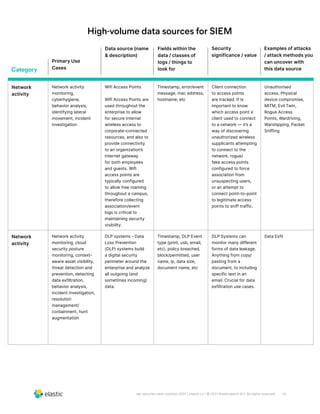
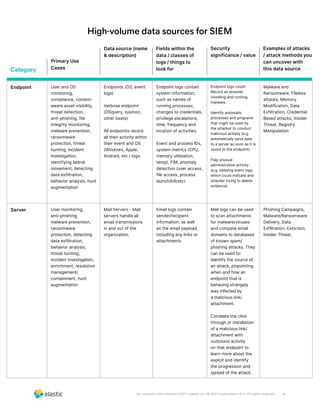
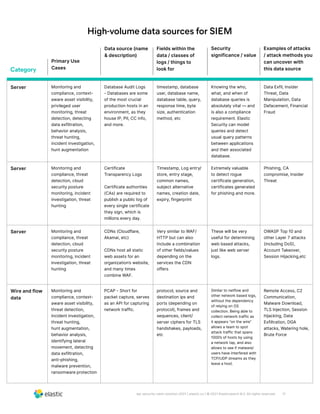
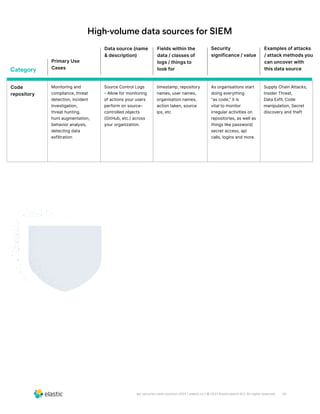
The document discusses the need for security teams to have access to more data from a variety of sources to address evolving security challenges. As adversaries become more motivated by lucrative opportunities and employ more evasive and patient attack methods, security teams need more context from diverse data sources to identify unknown threats, investigate long dwell times, and combat evasion techniques. Both basic attacks exploiting misconfigurations and advanced attacks require security teams to maintain visibility across on-premises and cloud environments and access security-relevant data for detections, investigations, and responses. High-profile examples that illustrate the need for more data include cloud-based data breaches, sophisticated supply chain attacks, and evolving ICS/SCADA and IoT attacks.