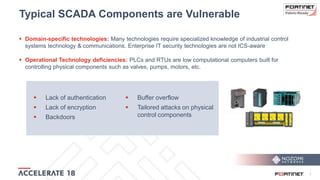
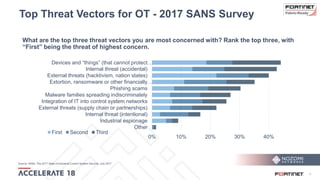
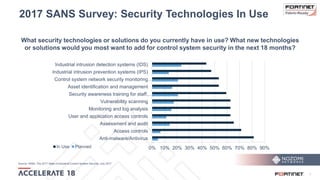
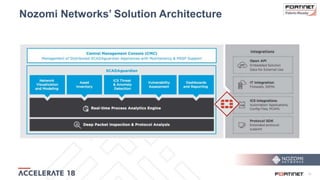
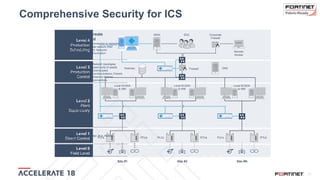
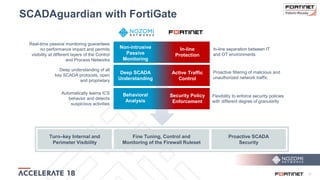
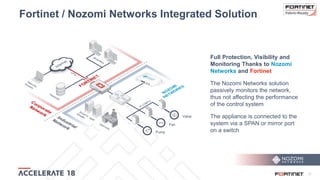
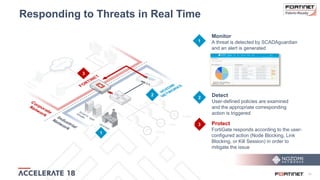
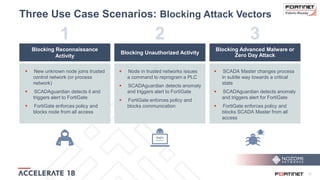
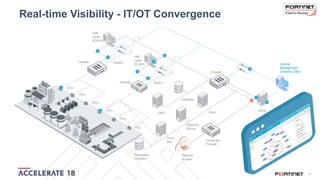
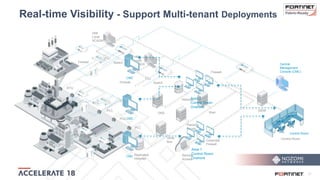
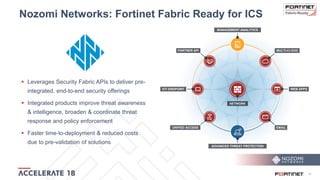
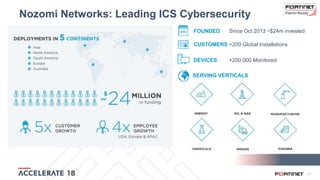
The document discusses the convergence of IT and operational technology (OT), highlighting the vulnerabilities of industrial control systems (ICS) and the increasing threats from cyber attacks such as Stuxnet and Industroyer. It emphasizes the need for integrated cybersecurity solutions tailored for ICS, showcasing Fortinet and Nozomi Networks' products that monitor and protect against various threats while ensuring system performance. The document also includes insights from a SANS survey on threat vectors and security technologies in use within the ICS environment.