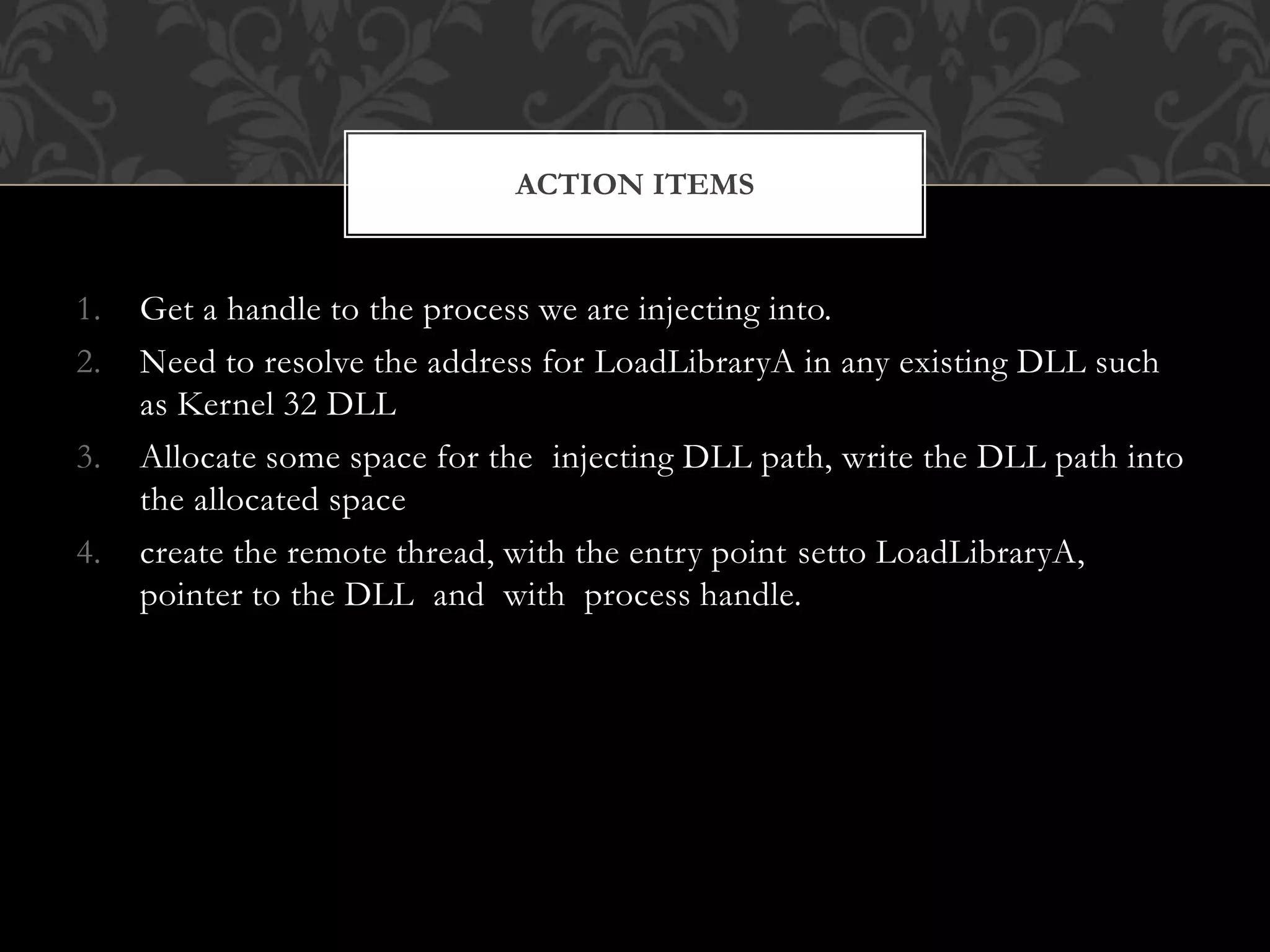
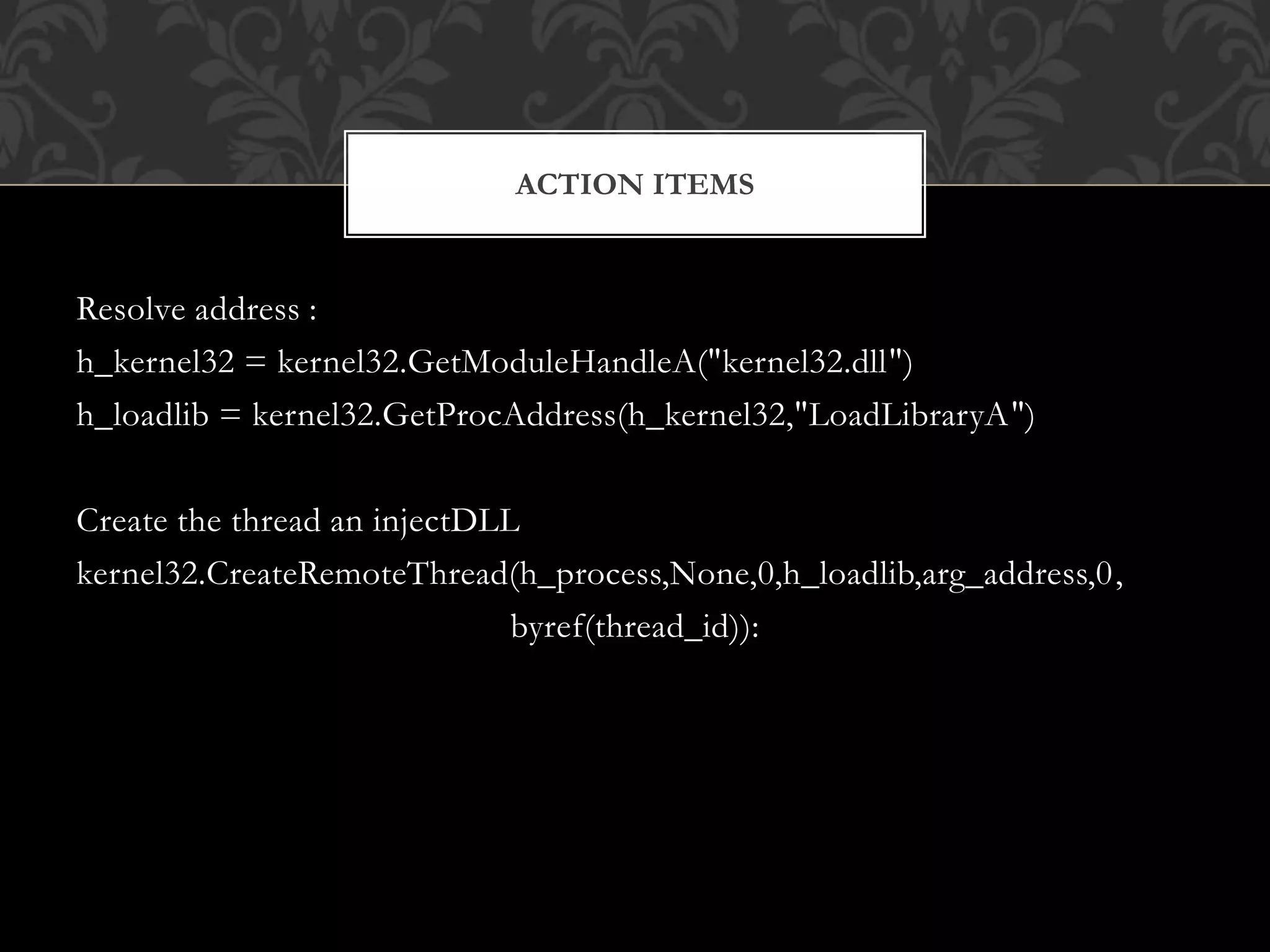
DLL injection involves loading a dynamic link library file into another running process's address space without the target process's cooperation or knowledge. The summarizes the key steps for DLL injection:
1. Get a handle to the target process using its process ID.
2. Allocate memory in the target process to store the path to the DLL.
3. Write the DLL path to the allocated memory.
4. Resolve the address of LoadLibraryA in kernel32.dll and create a remote thread in the target process using this entry point to load the DLL.