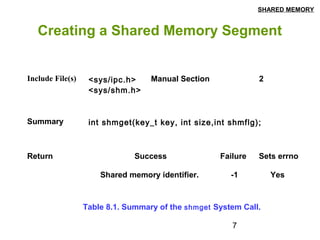
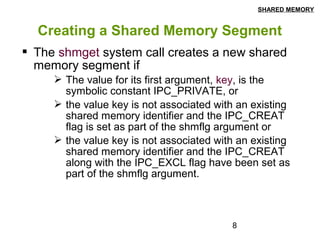
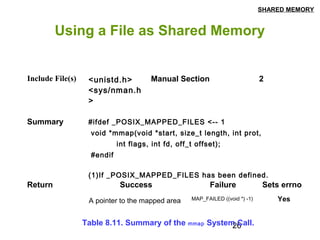
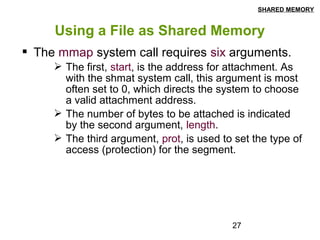
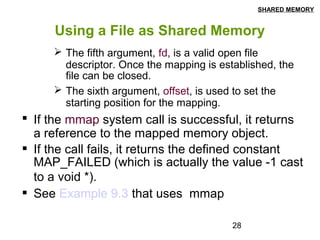
This document discusses shared memory in Linux, including creating shared memory segments using shmget, attaching and detaching shared memory using shmat and shmdt, controlling shared memory segments using shmctl, and using mmap to map files to shared memory. It provides details on the system calls used for shared memory and examples of creating and using shared memory between processes.