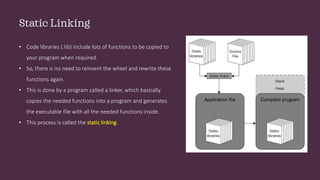
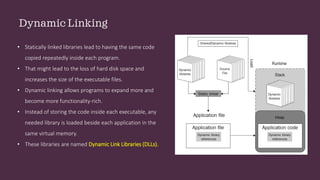
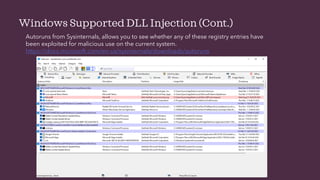
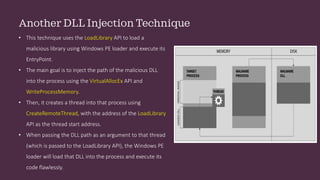
This document discusses static and dynamic linking of libraries in Windows. It explains how dynamic linking loads libraries into memory alongside applications rather than copying code into each executable. It then covers dynamic link libraries (DLLs) and how their exported functions can be accessed via name or index number. The document focuses on DLL injection techniques used by malware to manipulate process execution, including loading a malicious DLL via the LoadLibrary and GetProcAddress APIs or modifying registry entries.