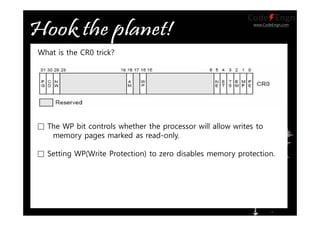
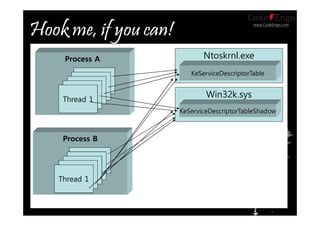
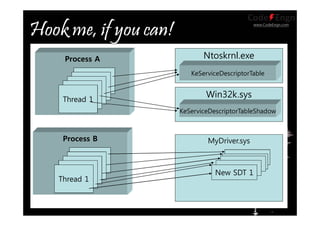
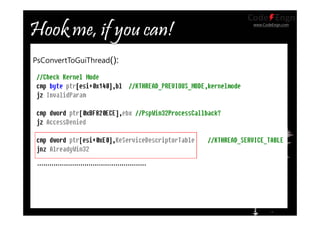
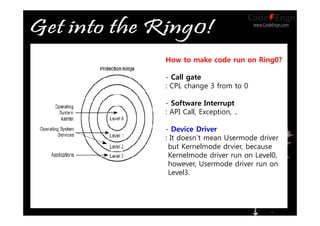
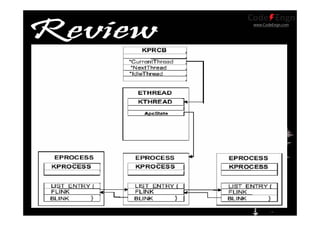
This document contains information about various techniques for hooking functions in the Windows kernel, including kernel hooks, SSDT hooking, IDT hooking, one-byte hooking, and blind hooking using debug registers. It discusses the motivations, concepts, and demonstrations of each technique. The document also contains information on kernel structures like EPROCESS, ETHREAD, KPCR, TEB, and PEB. It provides code samples and explanations for techniques like modifying the SSDT, hooking interrupts, and using debug registers to dynamically hook functions without directly patching memory or tables.





















![www.CodeEngn.com
MOV EAX,DWORD PTR FS:[18]
MOV EAX,DWORD PTR DS:[EAX+30]
MOVZX EAX,BYTE PTR DS:[EAX+2]
Original IsDebuggerPresent() code:
Modifed IsDebuggerPresent() code:
MOV EAX , KUSER_SHARED_DATA+0x8
JMP EAX](https://image.slidesharecdn.com/20071stcodeengndual5651hooktheplanet-130527105710-phpapp02/85/2007-CodeEngn-Conference-01-dual5651-Windows-27-320.jpg)
![www.CodeEngn.com
PAYLOAD:
DLL loading code :
pushad
pushfd
push KSD + 0x8 + sizeof(DLL load
code)
call [KUSER_SHARED_DATA]
popfd
popad
jmp [KUSER_SHARED_DATA+0x4]](https://image.slidesharecdn.com/20071stcodeengndual5651hooktheplanet-130527105710-phpapp02/85/2007-CodeEngn-Conference-01-dual5651-Windows-28-320.jpg)



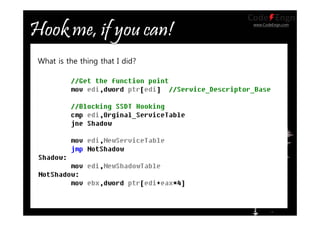
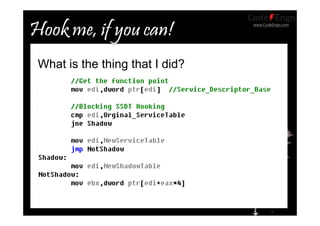
![www.CodeEngn.com
1. Build the function that has same prototype with Native API to
hook.
2. Get the index number of Native API.
3. Get address of SSDT by referencing KeServiceDescriptorTable.
4. Make SSDT memory area writeable.
5. KeServiceDescriptorTable->ServiceTableBase[index] =
HookFunction;
Process](https://image.slidesharecdn.com/20071stcodeengndual5651hooktheplanet-130527105710-phpapp02/85/2007-CodeEngn-Conference-01-dual5651-Windows-32-320.jpg)