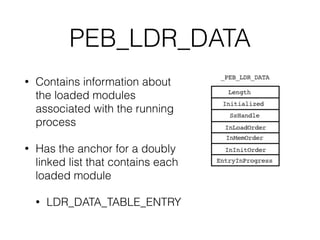
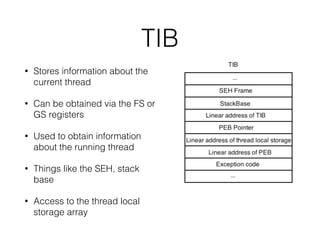
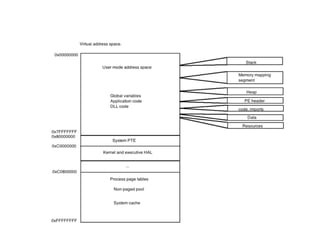
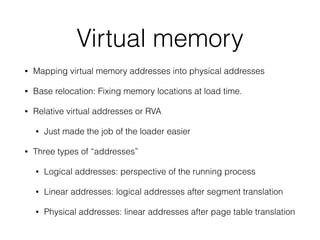
The document provides an overview of process injection techniques, specifically focusing on DLL injection and process replacement within the Windows operating system. It explains how these methods enable malware to execute code invisibly by manipulating the memory and behavior of legitimate processes. Key concepts covered include the structure of Windows processes, the mechanics of DLL injection, and the steps involved in process replacement, highlighting the potential risks and detection methods associated with these techniques.