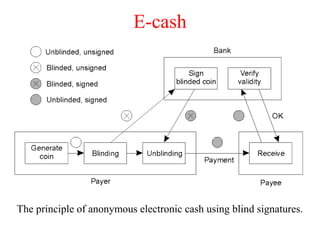
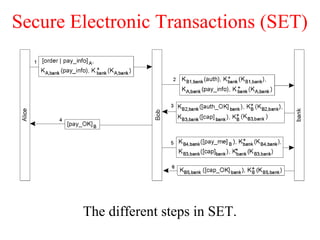
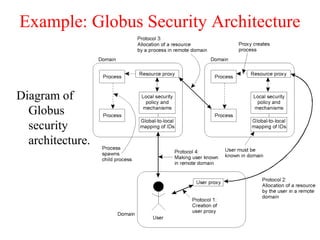
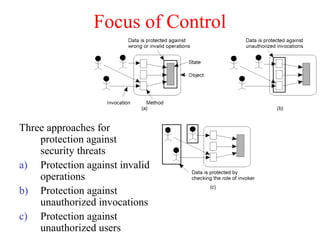
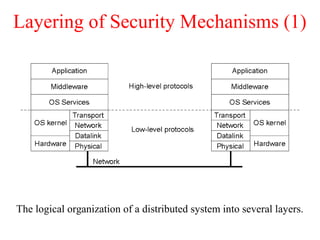
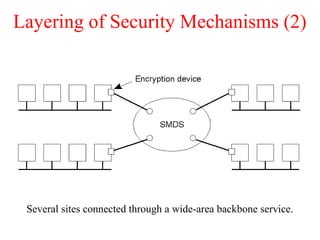
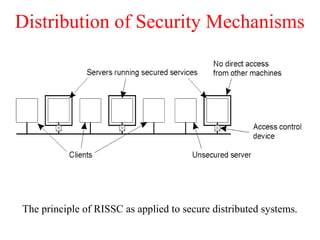
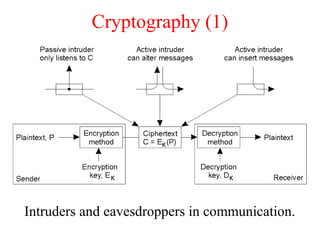
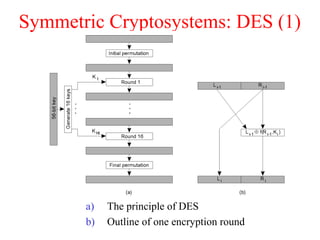
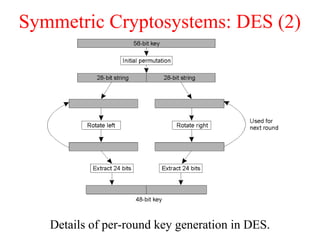
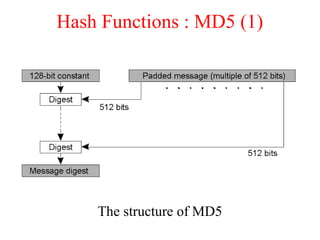
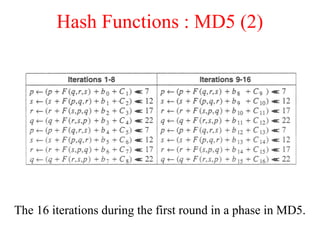
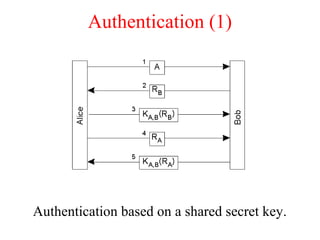
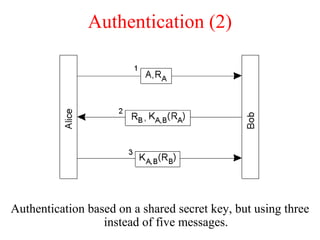
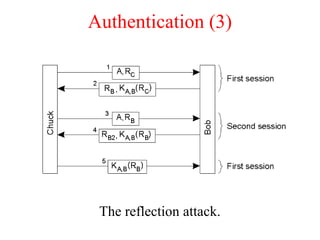
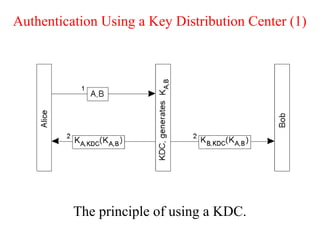
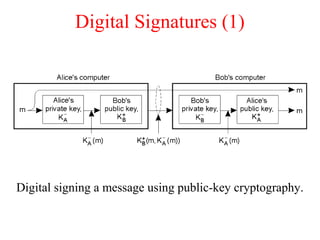
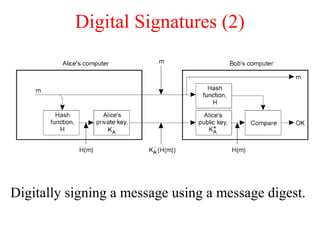
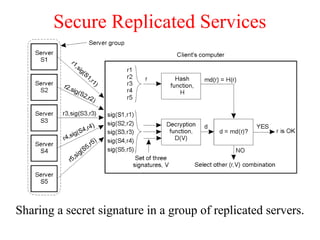
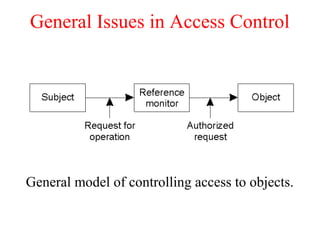
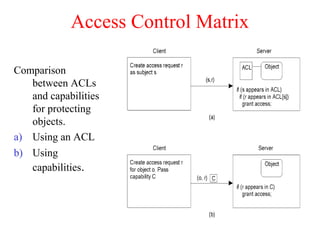
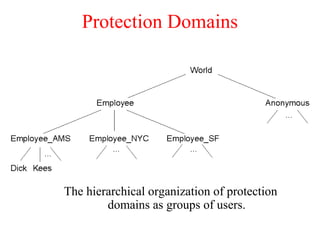
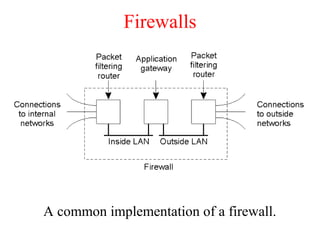
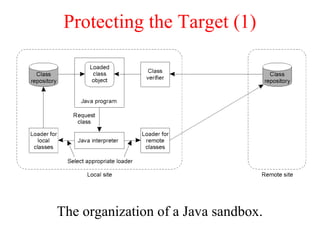
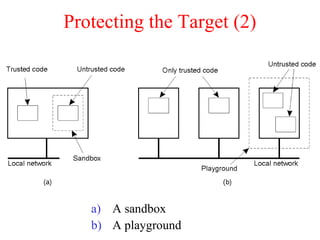
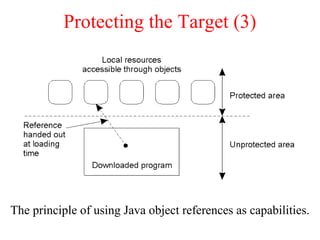
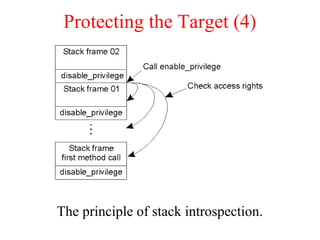
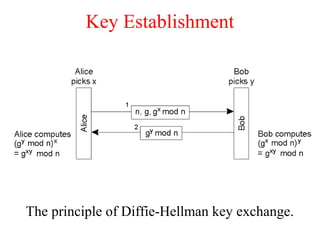
This document discusses various security concepts including types of threats, security mechanisms, authentication methods, access control, and electronic payment systems. It provides examples of security architectures like Globus and protocols like Kerberos. Key topics covered include encryption, digital signatures, firewalls, capabilities, and privacy in electronic payment systems.





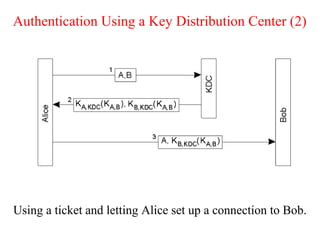
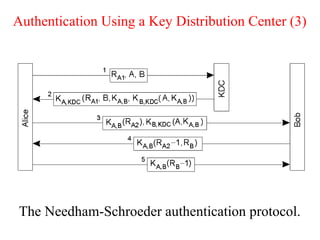
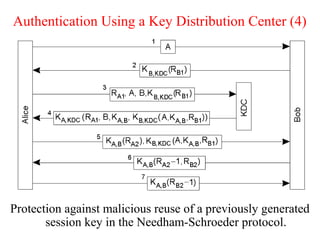
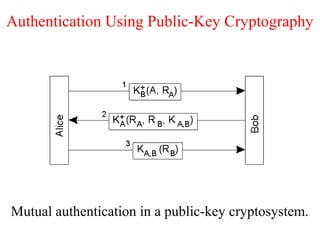
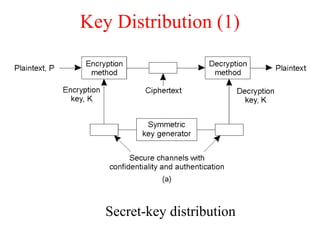
![Key Distribution (2)
Public-key distribution (see also [menezes.a96]).](https://image.slidesharecdn.com/chap-08-180727105055/85/Distributed-System-by-Pratik-Tambekar-37-320.jpg)
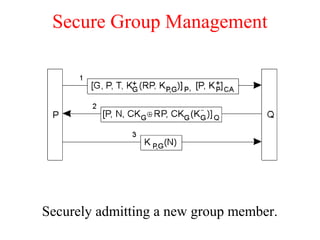

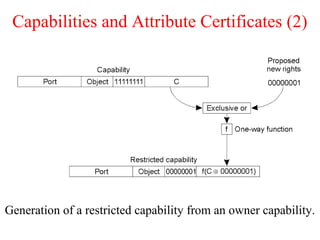
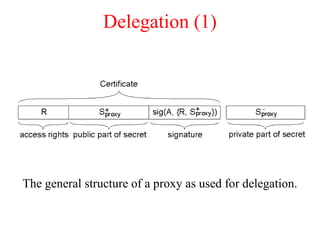
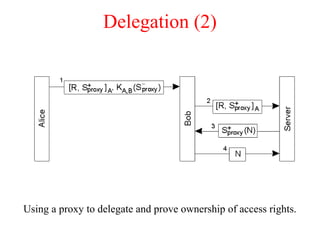
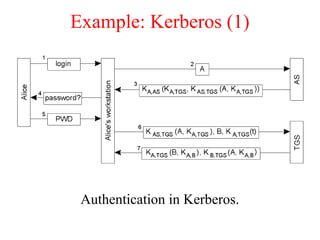
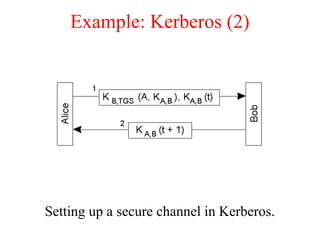
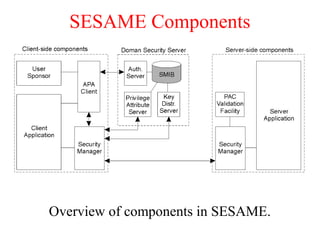

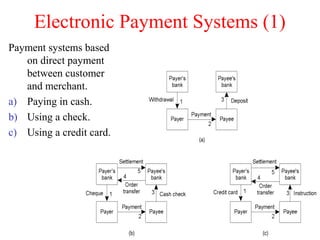
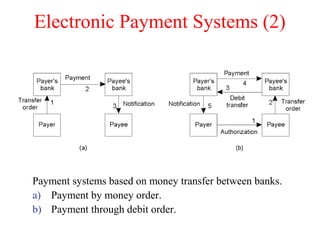
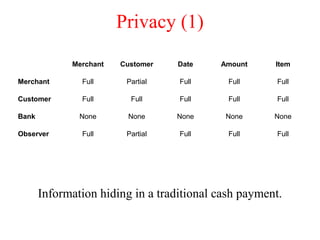
![Privacy (2)
Information hiding in a traditional credit-card system (see also [camp.lj96a])
Merchant Customer Date Amount Item
Merchant Full Full Full Full Full
Customer Full Full Full Full Full
Bank Full Full Full Full None
Observer Full Partial Full Full Full
Party
Information](https://image.slidesharecdn.com/chap-08-180727105055/85/Distributed-System-by-Pratik-Tambekar-50-320.jpg)