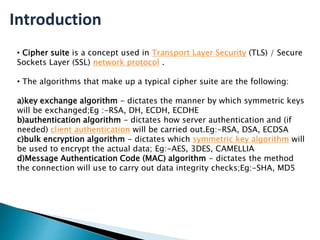
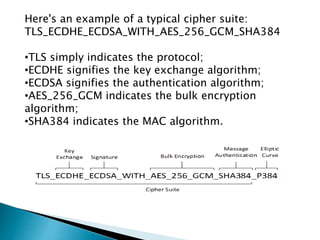
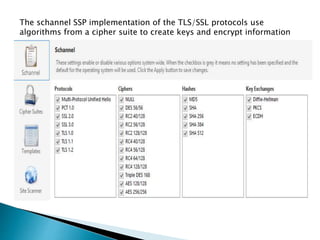
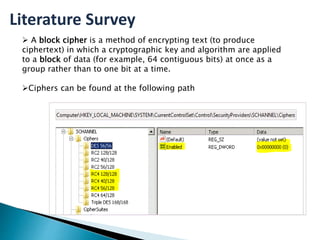
This document provides an introduction to cipher suites used in TLS/SSL network protocols. It discusses the key components of a cipher suite, including the key exchange algorithm, authentication algorithm, bulk encryption algorithm, and message authentication code algorithm. An example cipher suite is provided to illustrate these components. Vulnerabilities related to cipher suites like SWEET32, POODLE, and BEAST are also mentioned. The document concludes by stating the importance of understanding SSL and TLS to prevent server vulnerabilities from being exploited.